In the realm of secure remote access and data transfer, SSH (Secure Shell) reigns supreme. SSH UDP (User Datagram Protocol) extends the capabilities of SSH, offering a specialized protocol for efficient and secure UDP-based communication. This comprehensive guide delves into the world of SSH UDP, exploring its custom configuration, tunneling, port forwarding, proxy capabilities, and various applications.
We will uncover the benefits, security considerations, performance optimization techniques, and best practices for harnessing the power of SSH UDP.
SSH UDP is particularly advantageous in scenarios where UDP’s connectionless and low-latency nature is crucial. Its versatility extends to a wide range of applications, including secure remote desktop access, file transfers, and even gaming. As we navigate this guide, you will gain a deep understanding of SSH UDP, empowering you to leverage its capabilities effectively and securely.
SSH UDP Custom Port Configuration
Using a custom UDP port for SSH offers several benefits. It enhances security by reducing the likelihood of brute-force attacks targeting the default SSH port (TCP 22). Additionally, it provides greater flexibility in network configuration, allowing administrators to allocate ports more efficiently and avoid conflicts with other services.
To configure a custom UDP port for SSH, follow these steps:
Linux and macOS
- Edit the SSH configuration file (/etc/ssh/sshd_config).
- Add or modify the following lines:
Port [Custom UDP Port]ListenAddress [IP Address]
Windows
- Open the Registry Editor (regedit).
- Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sshd.
- Create or modify the following registry values:
PortNumber (DWORD): [Custom UDP Port]ListenAddress (REG_SZ): [IP Address]
Security Implications
While using a custom UDP port for SSH enhances security, it’s important to consider the following implications:
- Administrators must ensure that the chosen port is not already in use by other services.
- Firewall rules must be updated to allow traffic on the custom port.
- Clients must be configured to connect to the custom port.
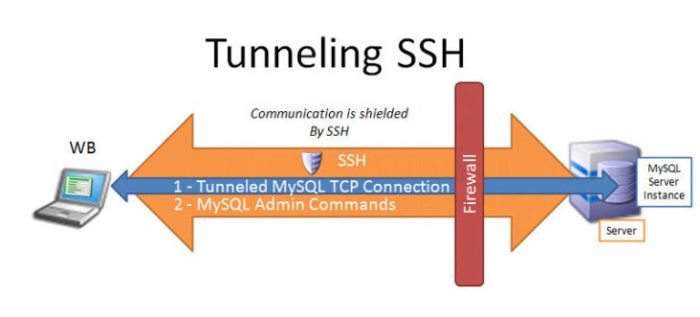
SSH UDP Tunneling
SSH UDP tunneling is a technique that allows UDP traffic to be encapsulated within an SSH connection. This can be useful for bypassing firewalls or other network restrictions that block UDP traffic.SSH UDP tunneling works by creating a virtual network interface on the client machine.
This interface is then used to send and receive UDP traffic. The traffic is encapsulated within SSH packets, which are then sent over the SSH connection to the server. The server then decapsulates the traffic and sends it to the appropriate destination.
Advantages and Disadvantages
SSH UDP tunneling has several advantages, including:
- It can bypass firewalls and other network restrictions that block UDP traffic.
- It is relatively easy to set up and use.
- It is secure, as the traffic is encrypted by the SSH connection.
However, SSH UDP tunneling also has some disadvantages, including:
- It can be slow, as the traffic is encapsulated within SSH packets.
- It can be difficult to troubleshoot, as the traffic is not visible to the network administrator.
SSH UDP Port Forwarding
SSH UDP port forwarding allows you to create a UDP tunnel from a remote host to your local machine. This is different from SSH UDP tunneling, which creates a UDP tunnel between two remote hosts. SSH UDP port forwarding is useful for accessing UDP-based services on a remote host that are not accessible directly.
Setting Up SSH UDP Port Forwarding
- Connect to the remote host using SSH.
- Use the following command to create a UDP port forward from the remote host to your local machine:
ssh -L local_port : local_address : remote_port user @ remote_host
- For example, to create a UDP port forward from port 5000 on the remote host to port 6000 on your local machine, you would use the following command:
ssh -L 6000:localhost:5000 user@remote_host
Use Cases for SSH UDP Port Forwarding
- Accessing UDP-based services on a remote host that are not accessible directly
- Testing UDP-based applications on a remote host
- Debugging UDP-based network issues
SSH UDP Proxy
SSH UDP proxy is a method of using SSH to forward UDP traffic over a secure SSH connection.
This can be useful for bypassing firewalls or accessing UDP-based services that are not normally accessible over SSH.
To use SSH as a UDP proxy, you will need to use the -D option when connecting to the SSH server. The -D option specifies the port that the SSH client will listen on for UDP traffic.
For example, the following command would create a UDP proxy on port 1080:
ssh -D 1080 [email protected]
Once the SSH connection is established, you can use any UDP-based application to connect to the proxy port. For example, the following command would use the netcat utility to connect to a UDP server on port 10000:
nc -u 127.0.0.1 1080 10000
SSH UDP proxy can be used in a variety of scenarios. For example, it can be used to bypass firewalls that block UDP traffic, or to access UDP-based services that are not normally accessible over SSH.
There are several advantages to using SSH UDP proxy. First, it is a secure way to forward UDP traffic. Second, it is relatively easy to set up and use. Third, it can be used to bypass firewalls and access UDP-based services that are not normally accessible over SSH.
However, there are also some disadvantages to using SSH UDP proxy. First, it can be slow, especially if the SSH connection is slow. Second, it can be difficult to troubleshoot if there are problems with the SSH connection.
SSH UDP Security
SSH UDP, while offering speed and efficiency, also introduces certain security risks that need to be addressed. Understanding these risks and implementing appropriate mitigation strategies is crucial for ensuring the secure use of SSH UDP.Encryption plays a vital role in SSH UDP security.
SSH UDP utilizes strong encryption algorithms to protect data transmitted over the network, ensuring confidentiality and integrity. By encrypting data, it becomes extremely difficult for unauthorized individuals to intercept and decipher sensitive information.
Mitigating Security Risks
To mitigate the security risks associated with SSH UDP, several recommendations should be followed:
- Use strong encryption algorithms: SSH UDP supports a range of encryption algorithms, including AES-256, which provides robust protection against unauthorized access.
- Enable authentication: Implement strong authentication mechanisms, such as two-factor authentication or public-key cryptography, to prevent unauthorized access to SSH UDP connections.
- Limit access: Restrict access to SSH UDP services to authorized users and devices only. Implement firewalls and access control lists (ACLs) to prevent unauthorized access.
- Monitor and audit logs: Regularly monitor SSH UDP logs for suspicious activities or unauthorized access attempts. Implement intrusion detection and prevention systems (IDS/IPS) to detect and respond to security breaches.
- Keep software up to date: Regularly update SSH UDP software and related components to patch security vulnerabilities and ensure the latest security measures are in place.
SSH UDP Performance
SSH UDP and SSH TCP are two different protocols for tunneling data over an SSH connection. SSH UDP is generally faster than SSH TCP, but it is also less reliable. The factors that affect the performance of SSH UDP include the network latency, the bandwidth, and the packet size.
Tips for Optimizing SSH UDP Performance
- Use a low latency network.
- Use a high bandwidth network.
- Use a small packet size.
- Use a UDP-friendly application.
SSH UDP Tools
SSH UDP connections can be managed using various tools. Each tool offers unique features and advantages, making it suitable for different scenarios. Here are some commonly used SSH UDP tools:
SSH Command-line Tool
The SSH command-line tool is a versatile tool that allows users to establish and manage SSH UDP connections from the command line. It provides a wide range of options for configuring and controlling the connection, including port forwarding, tunneling, and security settings.To
use the SSH command-line tool, open a terminal window and enter the following command:“`ssh
p [port] [user]@[host]
“`Replace [port] with the UDP port you want to connect to, [user] with your username, and [host] with the hostname or IP address of the remote server.
PuTTY
PuTTY is a popular SSH client that supports UDP connections. It provides a graphical user interface (GUI) that makes it easy to configure and manage SSH connections. PuTTY allows users to create and save connection profiles, specify port forwarding rules, and configure security settings.To
use PuTTY, download and install the application from the official website. Once installed, launch PuTTY and enter the hostname or IP address of the remote server in the “Host Name (or IP address)” field. Select “SSH” as the connection type and enter the UDP port in the “Port” field.
Click the “Open” button to establish the connection.
MobaXterm
MobaXterm is a powerful SSH client that includes a range of features for managing SSH UDP connections. It provides a tabbed interface that allows users to manage multiple connections simultaneously. MobaXterm supports port forwarding, tunneling, and a built-in terminal emulator.To
use MobaXterm, download and install the application from the official website. Once installed, launch MobaXterm and click on the “Session” menu. Select “SSH” as the connection type and enter the hostname or IP address of the remote server. Enter the UDP port in the “Port” field and click the “OK” button to establish the connection.
SSH UDP Applications
SSH UDP is a versatile tool that finds applications in various real-world scenarios. It offers a secure and efficient way to transmit data over UDP, making it suitable for applications that require low latency and high throughput.One of the most common applications of SSH UDP is in remote desktop access.
SSH UDP can be used to establish a secure connection to a remote computer and access its desktop environment. This allows users to remotely control the computer as if they were sitting in front of it.Another application of SSH UDP is in file transfer.
SSH UDP can be used to transfer files between two computers securely and efficiently. This is particularly useful for transferring large files or files that need to be transferred quickly.SSH UDP can also be used for tunneling other protocols over UDP.
For example, SSH UDP can be used to tunnel TCP traffic over UDP, allowing applications that rely on TCP to be used over UDP. This can be useful for bypassing firewalls or other network restrictions.Integrating SSH UDP into existing systems is relatively straightforward.
Most SSH clients and servers support SSH UDP out of the box. To use SSH UDP, simply specify the UDP port that you want to use when connecting to the remote computer.SSH UDP offers several benefits over other methods of data transmission.
First, SSH UDP is secure. It uses strong encryption to protect data from eavesdropping and tampering. Second, SSH UDP is efficient. It uses a lightweight protocol that minimizes overhead and maximizes throughput. Third, SSH UDP is flexible.
It can be used to transmit a variety of data types, including text, files, and even audio and video.
SSH UDP Best Practices
To ensure secure and effective use of SSH UDP, it’s crucial to follow established best practices. These guidelines help mitigate risks and enhance the overall user experience.
When utilizing SSH UDP, several potential pitfalls should be considered:
- Insufficient port protection: Leaving UDP ports exposed without proper security measures can lead to unauthorized access and potential exploitation.
- Unrestricted access: Granting excessive access to users or services can create vulnerabilities and compromise the security of the system.
- Outdated software: Running outdated SSH software versions can introduce security flaws and increase the risk of attacks.
Troubleshooting SSH UDP Issues
Resolving SSH UDP issues requires a systematic approach to identify and address the underlying cause. Some common troubleshooting steps include:
- Verifying port configuration: Ensure that the SSH UDP port is correctly configured on both the client and server.
- Checking firewall settings: Confirm that the firewall allows UDP traffic on the designated port.
- Examining SSH logs: Review SSH logs for any error messages or indications of connection problems.
- Testing with alternative clients: Attempt to connect using a different SSH client to eliminate potential client-specific issues.
- Seeking expert assistance: If troubleshooting efforts prove unsuccessful, consider reaching out to a qualified network administrator or SSH expert for guidance.
SSH UDP Future
SSH UDP, as a reliable and secure tunneling protocol, is poised for continued evolution and widespread adoption in the years to come. Several key trends and developments will shape its future:
Growing Adoption in Cloud and Virtualization Environments: As cloud computing and virtualization become increasingly prevalent, SSH UDP will play a crucial role in providing secure remote access and data transfer between cloud-based resources and on-premises systems.
Enhanced Security Features
SSH UDP will incorporate advanced security features to address emerging threats and maintain its position as a highly secure tunneling protocol. These features may include:
- Improved encryption algorithms to protect data from unauthorized access
- Multi-factor authentication to enhance user authentication and prevent unauthorized access
- Support for IPv6 to ensure compatibility with the latest networking technologies
Increased Performance and Scalability
To meet the demands of modern applications and large-scale deployments, SSH UDP will focus on improving performance and scalability. Key developments in this area include:
- Optimized network protocols to reduce latency and increase data transfer speeds
- Support for multiplexing to allow multiple connections over a single UDP port
- Load balancing techniques to distribute traffic across multiple servers, improving overall scalability
Integration with Emerging Technologies
SSH UDP will continue to integrate with emerging technologies to enhance its functionality and usability. These integrations may include:
- Support for software-defined networking (SDN) to provide greater flexibility and control over network resources
- Integration with cloud-based security services to enhance threat detection and response capabilities
- Compatibility with modern operating systems and applications to ensure seamless integration with existing IT environments
In summary, SSH UDP’s future is bright, with continued advancements in security, performance, scalability, and integration with emerging technologies. As organizations increasingly rely on remote access and data transfer, SSH UDP will remain a critical tool for maintaining secure and reliable connectivity.