In the realm of secure remote access, SSH (Secure Shell) stands as a pillar of reliability. However, by harnessing the power of custom UDP ports, you can unlock a new dimension of SSH connectivity, enhancing security, performance, and flexibility.
This guide will delve into the intricacies of SSH UDP custom configurations, empowering you with the knowledge to optimize your remote access experience. From firewall rules to client compatibility, we will cover every aspect to ensure a seamless and secure connection.
SSH UDP Custom Port Configuration
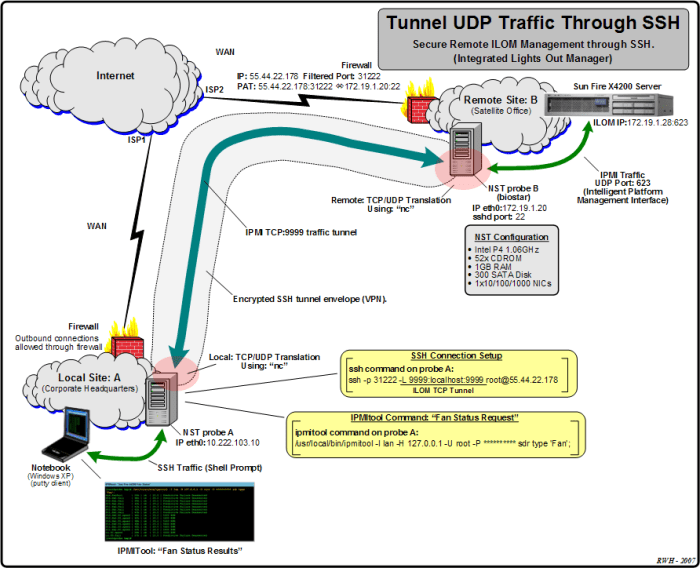
Configuring a custom UDP port for SSH connections allows you to enhance security and potentially bypass firewalls or network restrictions. This guide will explain the process, provide examples, and discuss the security implications of using a custom UDP port for SSH.
Valid Custom UDP Port Numbers
When selecting a custom UDP port for SSH, it’s crucial to choose a port number that is not commonly used by other services or applications. This helps prevent conflicts and ensures that your SSH connection is less likely to be blocked or interfered with.
Valid custom UDP port numbers typically fall within the range of 49152 to 65535.
Security Implications
Using a custom UDP port for SSH can enhance security by making it more difficult for attackers to identify and target your SSH server. However, it’s important to note that changing the UDP port alone does not guarantee complete protection.
Additional security measures, such as strong encryption and firewall rules, should be implemented to ensure the overall security of your SSH connections.
SSH UDP Custom Firewall Rules
SSH connections typically use TCP port 22 by default, but you can configure SSH to use a custom UDP port for added security or flexibility. To allow SSH connections over a custom UDP port, you’ll need to configure firewall rules to permit traffic on that port.
Firewall Rule Configuration
Firewall rules vary depending on the operating system you’re using. Here’s how to configure firewall rules for different operating systems: Linux:
Use the `ufw` command to add a firewall rule
“`sudo ufw allow “`
Example
To allow SSH connections on UDP port 2222, run:“`sudo ufw allow 2222“` Windows:
Use the `netsh` command to add a firewall rule
“`netsh advfirewall firewall add rule name=”SSH UDP Custom” dir=in action=allow protocol=UDP localport= “`
Example
To allow SSH connections on UDP port 2222, run:“`netsh advfirewall firewall add rule name=”SSH UDP Custom” dir=in action=allow protocol=UDP localport=2222“` macOS:
Use the `pfctl` command to add a firewall rule
“`sudo pfctl
- a nat on lo0 from any to any port 22
- > 127.0.0.1 port
“`
Example
To allow SSH connections on UDP port 2222, run:“`sudo pfctl
- a nat on lo0 from any to any port 22
- > 127.0.0.1 port 2222
“`
Benefits of Using SSH UDP Custom
Employing a custom UDP port for SSH connections offers several advantages, enhancing both security and performance.
In terms of security, using a non-standard UDP port can help mitigate the risk of unauthorized access to SSH services. By deviating from the default port, potential attackers are less likely to target the system, as they may not be aware of the custom port being used.
Moreover, a custom UDP port can improve performance by optimizing network traffic. By using a dedicated port for SSH traffic, it is possible to prioritize and route SSH packets more efficiently, reducing latency and improving overall connectivity.
Real-World Examples
Custom UDP ports have been successfully implemented in various scenarios to enhance SSH connectivity.
- In enterprise environments, organizations have used custom UDP ports to segment SSH traffic from other network traffic, ensuring reliable and secure remote access for employees.
- In cloud computing, cloud providers have adopted custom UDP ports for SSH connections to provide improved performance and isolation for their customers’ virtual machines.
- For remote access to industrial control systems, custom UDP ports have been used to establish secure and reliable SSH connections, ensuring the integrity and availability of critical infrastructure.
Troubleshooting SSH UDP Custom Issues
Using a custom UDP port for SSH can occasionally lead to various problems. This section will highlight some common issues and provide solutions to help you troubleshoot and resolve them effectively.
Diagnosing and resolving SSH UDP custom connection errors require a systematic approach. The first step is to identify the root cause of the problem. This can be done by checking the SSH server logs and examining the error messages. Once the cause has been identified, you can then proceed with the appropriate solution.
Firewall Rules
One of the most common problems when using a custom UDP port for SSH is related to firewall rules. Ensure that the firewall is configured to allow UDP traffic on the custom port. Check the firewall settings and make sure that the rules are configured correctly.
Port Forwarding
If you are using port forwarding to access the SSH server, make sure that the port forwarding rules are set up correctly. Check the configuration of the port forwarding rules and ensure that they are pointing to the correct IP address and port.
SSH Server Configuration
Another potential issue is related to the SSH server configuration. Make sure that the SSH server is configured to listen on the custom UDP port. Check the SSH server configuration file and verify that the port is set correctly.
SSH UDP Custom with Different SSH Clients
Different SSH clients may vary in their support for custom UDP ports. Here’s a discussion on the compatibility and configuration of SSH clients for custom UDP ports:
OpenSSH
OpenSSH, widely used on Linux and macOS systems, supports custom UDP ports. To configure OpenSSH to use a custom UDP port, add the following line to the SSH configuration file (/etc/ssh/sshd_config on Linux or /etc/ssh_config on macOS):
Port 2222
Replace 2222 with the desired custom UDP port number.
PuTTY
PuTTY, a popular SSH client for Windows, also supports custom UDP ports. To configure PuTTY, go to the “Connection” settings, select “SSH”, and then click on the “Tunnels” tab. Under “Destination”, enter the custom UDP port number in the “Port” field.
Other SSH Clients
The compatibility of other SSH clients with custom UDP ports may vary. Consult the documentation or support forums of the specific client for more information.
SSH UDP Custom Port Forwarding
SSH UDP Custom Port Forwarding allows you to forward SSH connections over a custom UDP port. This can be useful if you want to use a non-standard port for SSH traffic, or if you want to improve the performance of SSH over UDP.
To forward SSH connections over a custom UDP port, you need to use the -p option when starting the SSH server. For example, the following command will start the SSH server on UDP port 5000:
“`ssh
p 5000
“`
You can also use the -o option to specify the port that SSH will listen on. For example, the following command will start the SSH server on UDP port 5000 and listen on port 22:
“`ssh
- o Port=22
- p 5000
“`
Once you have started the SSH server on a custom UDP port, you can connect to it using the -p option when starting the SSH client. For example, the following command will connect to the SSH server on UDP port 5000:
“`ssh
p 5000 user@host
“`
Port forwarding over a custom UDP port can improve the performance of SSH, as UDP is a faster and more efficient protocol than TCP. However, it is important to note that UDP is not as reliable as TCP, so you may experience some data loss if you use SSH over UDP.
Security Considerations
There are some security considerations to keep in mind when using SSH UDP Custom Port Forwarding:
- UDP is not as secure as TCP, so you may be more vulnerable to attacks if you use SSH over UDP.
- Using a non-standard port for SSH traffic can make it more difficult for attackers to find and exploit vulnerabilities in your SSH server.
- You should always use a strong password or passphrase when connecting to an SSH server over UDP.
SSH UDP Custom with Two-Factor Authentication
SSH UDP custom port configuration allows for the utilization of two-factor authentication (2FA) to enhance security. 2FA adds an extra layer of protection by requiring users to provide two different forms of identification when logging in. This helps prevent unauthorized access even if a user’s password is compromised.
Benefits of Using 2FA for SSH
*
-*Increased Security
2FA makes it significantly harder for attackers to gain access to a system, even if they have obtained a user’s password.
-
- -*Compliance with Regulations
Many industries and organizations have regulations that require the use of 2FA for remote access to sensitive systems.
- -*Compliance with Regulations
-*Peace of Mind
Users can have greater confidence that their SSH connections are secure, reducing the risk of data breaches and unauthorized access.
Configuring 2FA for SSH with a Custom UDP Port
There are several methods for configuring 2FA for SSH over a custom UDP port.
One common approach is to use a third-party authentication server, such as Google Authenticator or Duo Security. These services provide mobile applications that generate one-time passcodes (OTPs) that users can enter during the SSH login process.To configure 2FA with a third-party authentication server:*
-*Install the authentication server
Install the server software on the host system where SSH is running.
-
- -*Configure the SSH server
Modify the SSH configuration file to enable 2FA and specify the authentication server to use.
- -*Configure the SSH server
-*Set up user accounts
Create user accounts on the authentication server and configure them to use 2FA.
-*Enable 2FA for users
Instruct users to install the authentication app on their mobile devices and link it to their SSH accounts.
Once 2FA is configured, users will be prompted to enter their OTPs when logging in via SSH over the custom UDP port.
This provides an additional layer of security and helps protect against unauthorized access.
SSH UDP Custom with Public Key Authentication
Public key authentication provides a secure and convenient way to authenticate to an SSH server without using a password. When using public key authentication, you generate a pair of keys: a public key and a private key. The public key is stored on the server, while the private key is kept secret on your local machine.
When you connect to the server, the server will use your public key to verify your identity. If the verification is successful, you will be granted access to the server without having to enter a password.There are several benefits to using public key authentication for SSH:*
-*Increased security
Public key authentication is more secure than password authentication because it is not susceptible to brute-force attacks.
-
- -*Convenience
Public key authentication is more convenient than password authentication because you do not have to remember and enter a password each time you connect to a server.
- -*Convenience
-*Automation
Public key authentication can be used to automate SSH connections, such as when setting up a continuous integration/continuous delivery (CI/CD) pipeline.
To configure public key authentication for SSH with a custom UDP port, you will need to generate a pair of keys and then add your public key to the server’s authorized_keys file.
Generate a Key Pair
To generate a key pair, use the following command:“`ssh-keygen
- t ed25519
- C “[email protected]”
“`This command will generate a pair of keys and store them in the files ~/.ssh/id_ed25519.pub and ~/.ssh/id_ed25519.
Add Your Public Key to the Server’s Authorized_keys File
Once you have generated a key pair, you will need to add your public key to the server’s authorized_keys file. To do this, use the following command:“`ssh-copy-id
i ~/.ssh/id_ed25519.pub [email protected]
“`This command will add your public key to the file ~/.ssh/authorized_keys on the server.Once you have added your public key to the server’s authorized_keys file, you will be able to connect to the server using public key authentication. To do this, use the following command:“`ssh
- p 12345
- i ~/.ssh/id_ed25519 [email protected]
“`Replace 12345 with the custom UDP port that you are using.You will not be prompted for a password when you connect to the server using public key authentication.
SSH UDP Custom with Compression
SSH over UDP can be configured to use compression, which can improve performance by reducing the amount of data that needs to be transferred. Compression can be enabled on both the client and server side.There are two main benefits to using compression with SSH:*
-*Reduced bandwidth usage
Compression can significantly reduce the amount of bandwidth required for SSH traffic. This can be especially beneficial for connections over slow or expensive links.
-*Improved performance
Compression can improve the performance of SSH by reducing the amount of time it takes to transfer data. This can be especially noticeable for large file transfers or when using SSH over a high-latency connection.To configure compression for SSH with a custom UDP port, you will need to add the following options to your SSH configuration file:“`Compression yesPort 2222“`You will also need to ensure that the SSH server is configured to allow compression.
This can be done by adding the following option to the SSH server configuration file:“`Compression yes“`Once you have configured compression for SSH, you can start using it by connecting to the SSH server on the custom UDP port. You can use the following command to connect to the SSH server:“`ssh
p 2222 user@server
“`You should now be able to use SSH over UDP with compression.
SSH UDP Custom with SOCKS Proxy
A SOCKS proxy allows you to establish a secure connection to another network or server. You can use a SOCKS proxy with SSH over a custom UDP port to add an extra layer of security and privacy to your connection.
Benefits of Using a SOCKS Proxy for SSH
Using a SOCKS proxy with SSH offers several benefits, including:
-
- -*Increased security
The SOCKS proxy acts as an intermediary between your computer and the SSH server, providing an additional layer of protection against eavesdropping and other attacks.
- -*Increased security
-*Improved privacy
The SOCKS proxy hides your real IP address from the SSH server, making it more difficult for your online activities to be tracked.
-*Access to restricted networks
Some SOCKS proxies allow you to bypass firewalls and other network restrictions, giving you access to websites and services that may be otherwise inaccessible.
Configuring a SOCKS Proxy for SSH with a Custom UDP Port
To configure a SOCKS proxy for SSH with a custom UDP port, you will need to:
-
- Choose a SOCKS proxy service. There are many different SOCKS proxy services available, both free and paid. Choose a service that is reputable and offers the features you need.
- Configure your SSH client to use the SOCKS proxy. The specific instructions will vary depending on your SSH client. However, most SSH clients will allow you to specify the SOCKS proxy server and port in the client’s configuration settings.
- Connect to the SSH server using the custom UDP port. Once you have configured your SSH client to use the SOCKS proxy, you can connect to the SSH server using the custom UDP port.
Final Thoughts
By embracing the versatility of SSH UDP custom configurations, you can tailor your remote access to meet your unique requirements. Whether it’s bolstering security, optimizing performance, or seamlessly integrating with other tools, SSH UDP custom is the key to unlocking a world of enhanced connectivity.