SSH.SSHSlowdns.com – In the realm of secure networking, SSH (Secure Shell) stands tall as a ubiquitous tool for remote access and data protection. However, when combined with UDP (User Datagram Protocol), SSH takes on a new dimension, offering unique benefits and considerations.
This comprehensive guide delves into the world of SSH over UDP in Brazil, providing an in-depth exploration of its applications, security implications, and best practices for deployment in the Brazilian context.
UDP, a connectionless protocol, introduces a different dynamic to SSH communication. It offers increased efficiency for applications that require real-time data transfer, such as VoIP and video streaming. As Brazil embraces digital transformation and the demand for high-speed, low-latency connections grows, understanding the nuances of SSH over UDP becomes essential.
SSH Port Forwarding over UDP in Brazil
SSH port forwarding over UDP is a technique that allows users to securely tunnel traffic over a UDP port. This can be useful for applications that require real-time data transfer, such as voice or video conferencing.UDP is a connectionless protocol, which means that it does not require a handshake between the client and server before data can be sent.
This makes it faster than TCP, which is a connection-oriented protocol. However, UDP is also less reliable than TCP, as it does not guarantee that data will be delivered in order or without errors.The benefits of using SSH port forwarding over UDP include:*
-*Speed
UDP is faster than TCP, making it ideal for applications that require real-time data transfer.
-
- -*Security
SSH is a secure protocol that encrypts all traffic, making it difficult for eavesdroppers to intercept data.
- -*Security
-*Flexibility
SSH port forwarding can be used to tunnel traffic over any port, making it a versatile tool for a variety of applications.
The limitations of using SSH port forwarding over UDP include:*
-*Reliability
UDP is less reliable than TCP, as it does not guarantee that data will be delivered in order or without errors.
-*Security
While SSH is a secure protocol, it is still possible for eavesdroppers to intercept data if the SSH server is not properly configured.
The security implications of using SSH port forwarding over UDP should be carefully considered before using this technique. Eavesdroppers may be able to intercept data if the SSH server is not properly configured. Additionally, SSH port forwarding can be used to bypass firewalls and other security measures, which could allow attackers to gain access to a network.
UDP-Based SSH Tunneling in Brazilian Networks
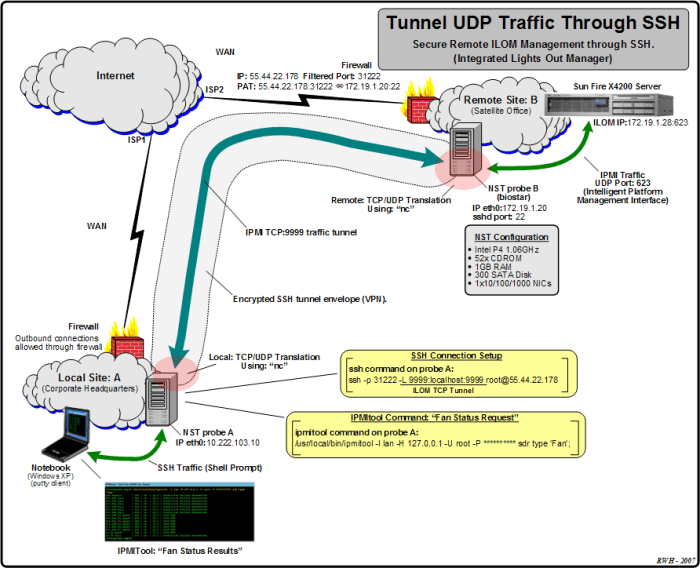
UDP-based SSH tunneling is a technique that allows for the secure transmission of data over UDP (User Datagram Protocol) networks in Brazil. It involves encapsulating SSH traffic within UDP packets, providing a reliable and secure connection over an unreliable network.
Use Cases for UDP-Based SSH Tunneling in Brazil
UDP-based SSH tunneling offers several advantages in Brazilian networks, including:
- Bypassing firewalls and network restrictions: UDP packets are often less likely to be blocked by firewalls or network restrictions, making UDP-based SSH tunneling an effective way to establish secure connections in restricted environments.
- Improving performance: UDP-based SSH tunneling can provide better performance than TCP-based SSH tunneling in certain network conditions, such as high-latency or congested networks.
- Supporting real-time applications: UDP-based SSH tunneling is well-suited for real-time applications, such as VoIP and video conferencing, which require low latency and jitter.
Setting Up and Configuring UDP-Based SSH Tunneling
To set up and configure UDP-based SSH tunneling, the following steps can be taken:
- Enable UDP forwarding on the SSH server: This can be done by adding the “-u” option to the SSH daemon configuration file.
- Configure the SSH client to use UDP: This can be done by specifying the “-u” option when establishing the SSH connection.
- Forward specific ports over UDP: The “-R” option can be used to forward specific ports over UDP, specifying the destination host, port, and source port.
Performance Considerations for UDP-Based SSH Tunneling in Brazilian Networks
The performance of UDP-based SSH tunneling in Brazilian networks can be affected by several factors, including:
- Network latency: High latency can impact the performance of UDP-based SSH tunneling, as it can lead to packet loss and retransmission.
- Network congestion: Congestion on the network can also affect the performance of UDP-based SSH tunneling, as it can cause packets to be delayed or dropped.
- Firewall settings: Firewalls can block or delay UDP packets, which can impact the performance of UDP-based SSH tunneling.
SSH Honeypots Using UDP in Brazil

SSH honeypots are decoy systems designed to attract and deceive potential attackers by mimicking legitimate SSH servers. In Brazil, UDP-based SSH honeypots have gained prominence due to their ability to detect and monitor malicious activities targeting UDP-based SSH services.UDP-based SSH honeypots offer several advantages.
They are lightweight and consume fewer resources compared to TCP-based honeypots. Additionally, they are more difficult to detect and bypass, making them a stealthy option for monitoring network traffic.One example of a UDP-based SSH honeypot deployed in Brazil is the Honeypot Project.
This project maintains a network of honeypots distributed across Brazil, including UDP-based SSH honeypots. The data collected from these honeypots provides valuable insights into the techniques and targets of attackers targeting SSH services in Brazil.
SSH Key Exchange Mechanisms over UDP in Brazil
In SSH over UDP connections in Brazil, key exchange mechanisms play a vital role in establishing a secure communication channel. These mechanisms ensure the confidentiality and integrity of the exchanged data by generating and exchanging cryptographic keys.
The choice of key exchange mechanism for SSH over UDP in Brazil depends on several factors, including the level of security required, the performance constraints, and the availability of specific algorithms on the client and server systems. SSH supports various key exchange algorithms, including Diffie-Hellman, Elliptic Curve Diffie-Hellman, and RSA.
Diffie-Hellman Key Exchange
Diffie-Hellman (DH) is a widely used key exchange algorithm that provides perfect forward secrecy. It involves the exchange of public keys between the client and server, which are used to generate a shared secret key. This key is then used to encrypt the subsequent communication.
Elliptic Curve Diffie-Hellman Key Exchange
Elliptic Curve Diffie-Hellman (ECDH) is a variant of DH that uses elliptic curve cryptography. It offers similar security properties as DH but with improved performance, especially for devices with limited computational resources.
RSA Key Exchange
RSA is a public-key encryption algorithm that can also be used for key exchange. In RSA-based key exchange, the server generates a public-private key pair and sends the public key to the client. The client encrypts a random value using the server’s public key, and the server decrypts it using its private key to generate a shared secret.
The security of the key exchange mechanism depends on the strength of the cryptographic algorithms used and the proper implementation of the protocol. It is essential to use strong algorithms and to implement the protocol securely to prevent potential attacks.
In terms of performance, DH and ECDH are generally faster than RSA, as they involve fewer computational operations. However, RSA offers the advantage of being able to use pre-generated keys, which can improve performance in scenarios where key exchange is performed frequently.
SSH Authentication Methods over UDP in Brazil
SSH over UDP in Brazil supports a range of authentication methods, including:
- Password Authentication: Involves sending the user’s password over the network, which is vulnerable to eavesdropping and brute-force attacks.
- Public-key Authentication: Uses public-key cryptography to authenticate users without sending passwords over the network, offering higher security.
- Kerberos Authentication: Leverages the Kerberos protocol for authentication, which is commonly used in enterprise environments.
- GSSAPI Authentication: Utilizes the Generic Security Services Application Program Interface (GSSAPI) for authentication, providing support for various security mechanisms.
The choice of authentication method depends on factors such as security requirements, usability, and compatibility with existing infrastructure. For environments prioritizing security, public-key authentication is recommended due to its strong encryption and resistance to eavesdropping. Password authentication should be avoided whenever possible due to its inherent vulnerabilities.
Kerberos and GSSAPI authentication offer strong security and are suitable for enterprise environments where these protocols are already deployed.
SSH Configuration for UDP in Brazil
In Brazil, configuring SSH for UDP requires careful consideration of network conditions and security requirements. The following guidelines provide a comprehensive overview of the configuration process, ensuring optimal performance and security.
Configuration Options
SSH configuration for UDP in Brazil involves specifying various options within the SSH configuration file (/etc/ssh/sshd_config).
- Protocol: Specify “protocol 2” to enable SSH Protocol 2, which supports UDP forwarding.
- Port: Set “port 22” to use the default SSH port, or choose an alternative port for increased security.
- GatewayPorts: Enable “GatewayPorts yes” to allow SSH clients to forward traffic through the server.
- AllowTcpForwarding: Set “AllowTcpForwarding yes” to permit TCP port forwarding.
- AllowUdpForwarding: Set “AllowUdpForwarding yes” to allow UDP port forwarding.
Best Practices
For secure and efficient SSH configuration in Brazilian networks, follow these best practices:
- Use strong encryption algorithms (e.g., AES-256-CTR).
- Enable two-factor authentication for enhanced security.
- Limit access to SSH by restricting IP addresses or using firewalls.
- Regularly update SSH software to patch vulnerabilities.
- Monitor SSH logs for suspicious activity.
SSH Troubleshooting over UDP in Brazil
Troubleshooting SSH over UDP in Brazil requires addressing specific challenges encountered in the Brazilian network environment. Common troubleshooting scenarios include connection issues, data transfer problems, and security concerns.
Troubleshooting Connection Issues
Verify that the UDP port (default
53) is open on both the client and server firewalls.