ssh.sshslowdns.com – In the realm of remote access and secure communication, SSH UDP accounts have emerged as a powerful tool.
This guide will delve into the intricacies of SSH UDP accounts, exploring their purpose, advantages, configuration, security considerations, management techniques, troubleshooting tips, and alternative solutions.
Through real-world case studies and insights into future trends, we aim to provide a comprehensive understanding of this essential technology.
SSH UDP accounts leverage the User Datagram Protocol (UDP) to establish secure connections over unreliable networks. This protocol’s inherent speed and efficiency make it ideal for applications such as remote desktop access, file transfers, and network management.
However, understanding the nuances of SSH UDP account configuration, security, and management is crucial for maximizing their benefits.
SSH UDP Account Overview

An SSH UDP account utilizes the User Datagram Protocol (UDP) to establish a secure connection between two hosts. Unlike TCP, UDP is a connectionless protocol, making it faster and more efficient for certain applications, particularly those involving real-time data transmission.
SSH UDP accounts are commonly employed in scenarios requiring low latency and high performance, such as:
- Remote desktop access with minimal lag
- Real-time audio and video streaming
- Online gaming with reduced ping
Advantages of using SSH UDP accounts include:
- Faster connection speeds due to the connectionless nature of UDP
- Lower latency, minimizing delays in data transmission
- Reduced overhead compared to TCP
However, there are also disadvantages to consider:
- Unreliable data delivery as UDP does not guarantee packet delivery
- Limited error handling and recovery mechanisms
- Potential security risks if not properly configured
SSH UDP Account Configuration
Configuring an SSH UDP account enables secure remote access and data transfer over UDP protocol. Here’s a step-by-step guide for setting up SSH UDP accounts on different operating systems:
Windows
- Install an SSH client like PuTTY or OpenSSH.
- Generate an SSH key pair using PuTTYgen or OpenSSH’s ssh-keygen command.
- Copy the public key to the remote server using PuTTY or ssh-copy-id command.
- Configure the SSH client to use UDP protocol by adding “-u” flag to the command line.
Linux
- Install OpenSSH package using your distribution’s package manager.
- Generate an SSH key pair using ssh-keygen command.
- Copy the public key to the remote server using ssh-copy-id command.
- Edit the SSH configuration file (/etc/ssh/sshd_config) and set “Protocol 2” and “UseDNS no”.
- Restart the SSH service.
macOS
- Open Terminal and install OpenSSH if not already installed.
- Generate an SSH key pair using ssh-keygen command.
- Copy the public key to the remote server using ssh-copy-id command.
- Edit the SSH configuration file (~/.ssh/config) and add “Protocol 2” and “UseDNS no”.
- Restart the SSH service.
Tips and Troubleshooting
- Ensure the remote server is listening on UDP port 22.
- Verify that the SSH client and server are using compatible SSH versions.
- Disable firewall rules that may block UDP traffic.
SSH UDP Account Security
SSH UDP accounts, while convenient, come with inherent security considerations that require careful attention. Understanding these risks and implementing robust security measures is crucial for safeguarding access and protecting sensitive data.
Potential vulnerabilities associated with SSH UDP accounts include:
- UDP Spoofing: UDP’s connectionless nature makes it susceptible to spoofing attacks, where malicious actors can impersonate legitimate users or services.
- Eavesdropping: UDP packets are sent in plaintext, allowing eavesdroppers to intercept and potentially decipher sensitive information.
- Port Scanning: UDP ports are often used for port scanning, making it easier for attackers to identify and target vulnerable systems.
Best Practices for Securing SSH UDP Accounts
To mitigate these risks and enhance SSH UDP account security, follow these best practices:
- Encryption: Use strong encryption algorithms like AES-256 or ChaCha20 to protect data in transit.
- Authentication: Implement two-factor authentication or public-key authentication to prevent unauthorized access.
- Firewall Rules: Configure firewall rules to restrict access to SSH UDP ports from only trusted sources.
- Monitor Activity: Regularly monitor SSH UDP account activity for suspicious behavior or unauthorized login attempts.
SSH UDP Account Management
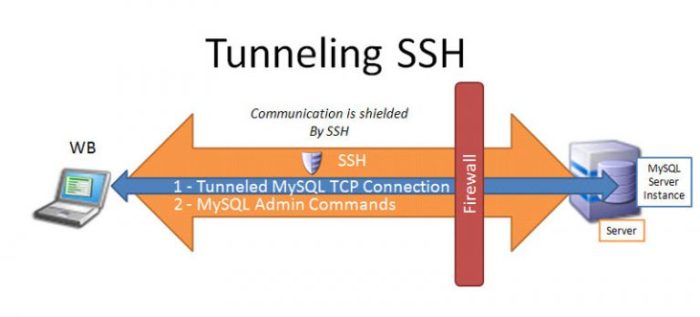
Managing SSH UDP accounts involves tasks like creating, modifying, and deleting accounts, as well as managing user permissions and access controls. Effective management ensures secure and efficient use of SSH UDP services.
Creating SSH UDP Accounts
- Assign a unique username and password to the new account.
- Specify the host or hosts that the account can access.
- Configure the account’s permissions and access controls.
Modifying SSH UDP Accounts
- Change the account’s username, password, or host access.
- Update the account’s permissions and access controls.
- Enable or disable the account as needed.
Deleting SSH UDP Accounts
- Remove the account’s access to all hosts.
- Revoke the account’s permissions and access controls.
- Delete the account from the system.
Managing User Permissions and Access Controls
- Set permissions for individual users or groups.
- Restrict access to specific commands or directories.
- Implement two-factor authentication or other security measures.
SSH UDP Account Troubleshooting
Troubleshooting SSH UDP account issues involves diagnosing and resolving connection errors, authentication failures, and other problems. This guide provides comprehensive steps to identify and address common SSH UDP account issues.
Connection Errors
If you encounter connection errors when accessing your SSH UDP account, consider the following steps:
- Verify that the SSH UDP port (typically port 22) is open on the server and your local machine.
- Check if the SSH UDP service is running on the server.
- Ensure that your firewall settings allow SSH UDP traffic.
- If connecting from a remote location, check if your network connection is stable.
Authentication Failures
If you experience authentication failures, try the following:
- Confirm that you are using the correct username and password.
- Check if two-factor authentication is enabled and complete the necessary steps.
- Verify that the SSH key you are using is authorized on the server.
- If using a password, ensure that password authentication is enabled on the server.
Other Problems
Other potential issues include:
- Permission denied errors: Verify that you have the necessary permissions to access the server.
- Slow connection speeds: Check your network connection and consider optimizing SSH UDP settings.
- Timeouts: Increase the SSH UDP timeout values if you experience frequent timeouts.
SSH UDP Account Tools
Managing SSH UDP accounts effectively requires a set of specialized tools. These tools provide comprehensive functionalities for creating, configuring, troubleshooting, and securing SSH UDP accounts, enhancing efficiency and ensuring a secure remote access environment.
Open-Source Tools
- OpenSSH: A versatile open-source SSH implementation that supports UDP connections. It offers robust features for managing SSH keys, configuring access controls, and enabling UDP forwarding.
- SSH-Config: A command-line tool for managing SSH configuration files. It simplifies the process of defining and editing SSH settings, including those related to UDP accounts.
- SFTP: A file transfer protocol built on SSH. It allows for secure file transfers over UDP connections, providing an efficient and reliable way to manage files on remote servers.
Commercial Tools
- SecureCRT: A commercial SSH client with advanced features for managing and securing SSH UDP accounts. It provides a user-friendly interface, customizable session profiles, and robust encryption options.
- Royal TSX: A multi-protocol remote access tool that supports SSH UDP connections. It offers session management, credential management, and audit capabilities, enhancing security and simplifying administration.
- MobaXterm: A comprehensive SSH client with built-in tools for network analysis, X11 forwarding, and file transfer. It supports SSH UDP connections and provides advanced features for troubleshooting and debugging.
These tools empower users to manage SSH UDP accounts efficiently, ensuring secure and reliable remote access. By leveraging these tools, administrators can simplify account creation, enforce access policies, troubleshoot connectivity issues, and protect against unauthorized access.
SSH UDP Account Alternatives
SSH UDP accounts provide secure remote access, but alternative methods exist. Understanding the strengths and weaknesses of each option helps determine the best solution for specific needs.
SSH TCP
SSH TCP uses TCP, a reliable and ordered protocol. It offers strong security and is widely supported. However, TCP’s connection-oriented nature can result in higher latency and lower performance in certain situations.
HTTPS
HTTPS uses HTTP over TLS/SSL encryption. It is widely used for web browsing and offers secure communication. However, HTTPS may not be suitable for all remote access scenarios, such as managing servers or executing commands.
VPNs
VPNs create a secure tunnel between two networks, allowing remote access as if directly connected to the local network. VPNs offer comprehensive security and can be configured for various protocols. However, they may introduce additional overhead and complexity.
Choosing the Right Solution
The best alternative to SSH UDP accounts depends on the specific requirements:
-
- -*Reliability and Performance SSH TCP is suitable for scenarios requiring reliable and low-latency connections.
-*Wide Compatibility
SSH TCP and HTTPS are widely supported across different platforms and devices.
-*Security
SSH TCP, HTTPS, and VPNs provide robust security measures.
-*Ease of Use
SSH TCP and HTTPS are relatively easy to set up and use, while VPNs may require more configuration.
-*Use Case
SSH TCP is ideal for remote server management, while HTTPS is suitable for secure web access. VPNs are versatile and can be used for various remote access scenarios.
SSH UDP Account Case Studies
SSH UDP accounts have been widely adopted by organizations across various industries, leading to significant improvements in security, efficiency, and remote access capabilities.
Let’s explore real-world case studies that showcase the benefits and lessons learned from practical implementations.
Enhanced Security in Financial Institutions
- A global investment bank implemented SSH UDP accounts to strengthen remote access security for their traders and analysts. The UDP protocol’s connectionless nature reduced the attack surface, making it more challenging for attackers to exploit vulnerabilities. Additionally, the bank implemented two-factor authentication and role-based access controls to further enhance security.
Improved Efficiency for Remote Workforce
- A technology company enabled SSH UDP accounts for its distributed workforce, allowing employees to securely access corporate resources from anywhere. The UDP protocol’s low latency and high performance provided a seamless remote work experience, boosting productivity and collaboration.
Case Study: Remote Access for Offshore Oil Rigs
An oil and gas company operating offshore oil rigs implemented SSH UDP accounts to provide secure and reliable remote access for maintenance engineers and technicians. The UDP protocol’s ability to traverse unstable and intermittent network connections ensured uninterrupted access to critical systems, minimizing downtime and improving operational efficiency.
SSH UDP Account Trends and Future
The future of SSH UDP accounts is promising, with emerging trends and advancements shaping their evolution. SSH UDP accounts are poised to become more secure, efficient, and versatile, enabling enhanced remote access and network security.
New Features and Protocols
SSH UDP accounts are incorporating advanced encryption algorithms and authentication protocols to enhance security. The adoption of modern protocols like SSHv2 and OpenSSH ensures stronger encryption and improved resistance against brute-force attacks. Additionally, features like two-factor authentication and key-based authentication provide additional layers of protection.
Cloud Integration
SSH UDP accounts are seamlessly integrating with cloud computing platforms, allowing users to securely access and manage cloud resources. This integration enables remote access to virtual machines, containers, and other cloud services, facilitating efficient cloud management and enhanced security.
Mobile Device Support
The growing prevalence of mobile devices is driving the development of SSH UDP clients for smartphones and tablets. These clients allow users to securely access remote servers and applications from anywhere, enhancing mobility and convenience.
Automated Management
SSH UDP accounts are becoming increasingly automated, with tools and scripts available for managing multiple accounts and configurations. This automation simplifies administration, reduces errors, and improves overall efficiency.
Increased Adoption
SSH UDP accounts are gaining wider adoption across various industries, including finance, healthcare, and IT. The growing need for secure remote access and network security is driving the demand for SSH UDP solutions.
SSH UDP Account Resources
Enhance your understanding of SSH UDP accounts by exploring the following valuable resources:
Official Documentation
Tutorials
Articles
Community Forums