In the realm of cybersecurity, SSH (Secure Shell) has emerged as a cornerstone technology for secure remote access and data transfer. Its versatility and robust security features have made it an indispensable tool for system administrators, developers, and anyone seeking to establish secure connections over untrusted networks.
This comprehensive guide delves into the intricacies of SSH, with a particular focus on the advantages and applications of UDP-based SSH connections. We will explore the nuances of SSH account management, port forwarding, and tunneling, empowering you with the knowledge to leverage SSH effectively for secure remote access and data management.
SSH Overview
SSH, short for Secure Shell, is a network protocol that allows secure remote access and data transfer between two devices. It provides a secure channel over an insecure network, enabling users to connect to remote systems, execute commands, and transfer files securely.SSH
plays a crucial role in secure remote administration, allowing system administrators to manage and troubleshoot remote servers without compromising security. It also facilitates secure file transfers, preventing unauthorized access and data interception.
Functionality
SSH operates on a client-server model, where the SSH client connects to an SSH server running on the remote host. The client initiates a secure connection by exchanging cryptographic keys with the server. Once the connection is established, the client can authenticate using various methods, including password-based or public-key authentication.After
successful authentication, the client gains access to the remote host and can execute commands, transfer files, and perform other administrative tasks as permitted by the server’s configuration. SSH supports various encryption algorithms, ensuring the confidentiality and integrity of data transmitted over the network.
SSH UDP Protocol
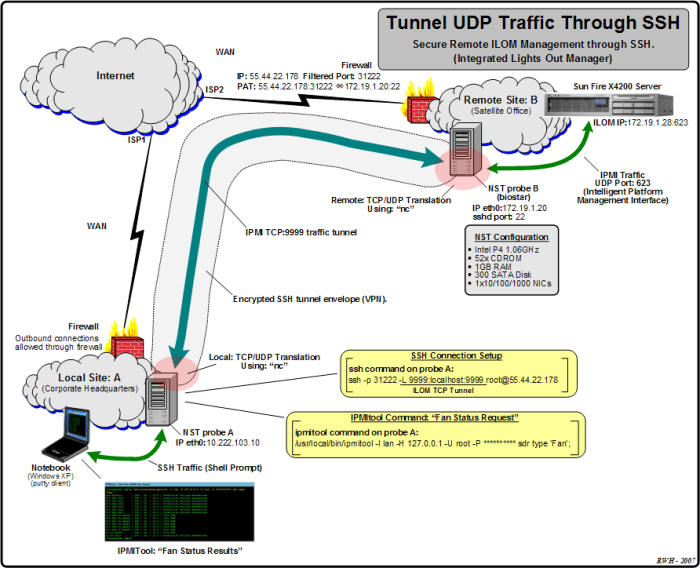
SSH (Secure Shell) protocol can utilize the UDP (User Datagram Protocol) for data transmission, offering certain advantages and characteristics compared to the traditional TCP (Transmission Control Protocol).
Comparison of UDP-based SSH with TCP-based SSH
The main differences between UDP-based SSH and TCP-based SSH lie in their performance and security aspects:
- Performance: UDP is a connectionless protocol, which means it does not establish a dedicated connection between the client and server. This can result in faster initial connection times and lower overhead, making UDP-based SSH more suitable for applications that require low latency and high throughput.
- Security: TCP provides built-in mechanisms for error detection and correction, ensuring reliable data transmission. UDP, on the other hand, does not have these mechanisms, making it more susceptible to data loss or corruption. However, SSH employs encryption and other security measures to mitigate these risks.
Ultimately, the choice between UDP-based SSH and TCP-based SSH depends on the specific requirements of the application. UDP-based SSH offers advantages in performance and latency, while TCP-based SSH provides greater reliability and security.
SSH Account Management
Effective SSH account management is crucial for maintaining the security of your systems. This involves creating, managing, and deleting SSH accounts securely and efficiently.
Strong Password Policies
Strong password policies are essential for preventing unauthorized access to SSH accounts. These policies should enforce the use of complex passwords that are difficult to guess or brute force.
- Minimum password length
- Use of uppercase, lowercase, numbers, and special characters
- Prohibition of common passwords and dictionary words
Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security to SSH accounts by requiring users to provide multiple forms of identification. This makes it more difficult for attackers to gain access to accounts, even if they have obtained the user’s password.
- One-time passwords (OTP)
- Security keys
- Biometric authentication
SSH Port Forwarding
SSH port forwarding is a technique that allows you to securely access a remote server’s services through a local port on your own computer. It’s a powerful feature that provides secure access to services that may be blocked by firewalls or network restrictions.
SSH port forwarding works by creating a secure tunnel between your local computer and the remote server. Data sent through this tunnel is encrypted, ensuring privacy and security. You can configure port forwarding for specific applications or services, allowing you to access them remotely as if they were running on your local machine.
Configuring Port Forwarding
To configure SSH port forwarding, you can use the following command:
ssh -L <local_port>:<remote_host>:<remote_port> <username>@<remote_host>
For example, to forward port 8080 on your local machine to port 80 on the remote server, you would use the following command:
ssh -L 8080:remote_host:80 username@remote_host
Once the port forwarding is configured, you can access the remote service on your local machine using the specified local port (in this case, 8080).
SSH Tunneling
SSH tunneling is a technique that allows you to create a secure, encrypted channel between two computers over an unsecured network. This can be useful for securely accessing remote networks or bypassing firewalls.To create an SSH tunnel, you first need to establish an SSH connection to the remote computer.
Once the connection is established, you can use the SSH tunnel to forward traffic from your local computer to the remote computer. The traffic will be encrypted by the SSH tunnel, so it will be secure from eavesdropping.There are many different ways to use SSH tunnels.
Here are a few examples:* You can use an SSH tunnel to securely access a remote network. This can be useful if you need to access a work network from home, or if you want to access a private network from a public Wi-Fi network.
- You can use an SSH tunnel to bypass a firewall. This can be useful if you need to access a website or service that is blocked by a firewall.
- You can use an SSH tunnel to create a secure connection between two computers. This can be useful if you need to transfer files between two computers securely, or if you want to use a remote computer as a proxy server.
SSH tunneling is a powerful tool that can be used to improve the security and privacy of your network communications.
Setting Up an SSH Tunnel
To set up an SSH tunnel, you will need to use an SSH client. There are many different SSH clients available, so you can choose one that is compatible with your operating system.Once you have an SSH client installed, you can follow these steps to set up an SSH tunnel:
- Open the SSH client and connect to the remote computer.
- Once the connection is established, you can use the following command to create an SSH tunnel:
“`ssh
-L [local port]
[remote host]:[remote port] [user]@[remote host]“`For example, the following command would create an SSH tunnel that forwards traffic from port 8080 on your local computer to port 80 on the remote computer:“`ssh-L 8080
remotehost.com:80 [email protected]“`Once the SSH tunnel is created, you can use your local port to access the remote port. For example, you could use a web browser to access the remote website on port 80 by visiting the following URL:“`http://localhost:8080“`The traffic between your local computer and the remote computer will be encrypted by the SSH tunnel, so it will be secure from eavesdropping.
SSH Configuration
Configuring SSH servers and clients securely and efficiently is crucial for maintaining a secure and performant remote access environment.
Best practices for SSH configuration include:
Disabling Insecure Protocols
Disable weak protocols like SSH version 1 (SSHv1) and insecure ciphers (e.g., CBC, MD5) to prevent attackers from exploiting vulnerabilities.
Limiting Login Attempts
Implement measures to limit failed login attempts (e.g., fail2ban, PAM modules) to prevent brute-force attacks.
Key-Based Authentication
Configure SSH to use public-key cryptography for authentication instead of passwords, which are susceptible to brute-force attacks and phishing.
SSH Troubleshooting

Troubleshooting SSH issues can be a time-consuming and frustrating process, but it’s essential to ensure a secure and reliable connection. This guide provides a comprehensive overview of common SSH problems and their solutions, covering connectivity, authentication, and data transfer issues.
To effectively troubleshoot SSH issues, it’s crucial to have a thorough understanding of the SSH protocol, its components, and potential points of failure. This guide will delve into the various aspects of SSH, providing practical solutions and best practices to resolve common problems.
Connectivity Issues
- Unable to establish a connection: Verify that the SSH server is running on the remote host and that the specified port is open on the firewall. Check the network connectivity and ensure that there are no physical or logical barriers between the client and server.
- Connection refused: This error typically indicates that the SSH server is not listening on the specified port. Ensure that the SSH service is enabled and configured to listen on the correct port.
- Connection timed out: This error occurs when the client fails to receive a response from the server within a specified timeout period. Increase the timeout value or check for network latency or congestion.
Authentication Issues
- Invalid username or password: Ensure that the username and password are correct and that the user account is authorized to access the SSH server.
- Permission denied (publickey): This error occurs when the client attempts to authenticate using a public key that is not authorized on the server. Check the authorized_keys file on the server and ensure that the client’s public key is included.
- Authentication failure: This error can indicate a variety of issues, including incorrect authentication methods, misconfigured SSH settings, or a compromised server. Investigate the SSH logs and configuration files to identify the specific cause.
Data Transfer Issues
- File transfer errors: These errors can occur due to insufficient permissions, disk space limitations, or network issues. Check the file permissions and ensure that the user has the necessary access rights. Verify that there is sufficient disk space on both the client and server.
- Slow file transfers: Slow data transfer speeds can be caused by network congestion, inefficient SSH settings, or hardware limitations. Optimize the SSH configuration by adjusting the compression and encryption algorithms. Consider upgrading the network infrastructure or using a faster SSH implementation.
- Connection dropped during file transfer: This issue can be caused by unstable network connections, firewall interruptions, or server-side issues. Check the network connectivity and ensure that the firewall rules are not blocking the SSH traffic. Monitor the server logs for any errors or warnings that may indicate a problem.
SSH Security Considerations
SSH, while secure, is not immune to potential security risks. It is crucial to understand these risks and implement appropriate mitigation measures to safeguard your systems.
One significant risk is the exploitation of vulnerabilities in SSH software. Attackers can exploit these vulnerabilities to gain unauthorized access to systems or escalate privileges.
Patching Vulnerabilities
Regularly patching SSH software is essential to mitigate this risk. Patches address known vulnerabilities and improve the overall security of the software.
Monitoring SSH logs can provide valuable insights into suspicious activities or attempted attacks. By analyzing log files, system administrators can identify potential threats and take appropriate action.
Monitoring Logs
In addition to patching and monitoring, implementing intrusion detection systems (IDS) can further enhance SSH security. IDS can detect and alert on suspicious activities or attempted attacks, enabling timely response and containment.
Intrusion Detection Systems
By implementing these security measures, organizations can significantly reduce the risks associated with SSH and ensure the integrity and confidentiality of their systems.
SSH Tools and Utilities
SSH offers various tools and utilities to enhance its functionality and security. These tools include SSH clients, key generators, and port scanners, each serving a specific purpose in SSH management.
SSH Clients
SSH clients are essential for establishing secure remote connections to SSH servers. They provide a command-line interface or graphical user interface (GUI) to execute commands on the remote host. Some popular SSH clients include OpenSSH, PuTTY, and Bitvise SSH Client.
Key Generators
Key generators are used to create and manage SSH keys, which are cryptographic keys used for authentication and encryption. They generate public and private key pairs that are used to establish secure connections without the need for passwords. Common key generators include ssh-keygen and PuTTYgen.
Port Scanners
Port scanners are used to identify open ports on a network, including SSH ports. They help in detecting potential vulnerabilities and unauthorized access attempts. By scanning for open SSH ports, administrators can take proactive measures to secure their systems. Some popular port scanners include Nmap and Netcat.
SSH Advanced Topics
SSH offers advanced features that enhance its functionality and cater to specific use cases. These include multiplexing, compression, and X11 forwarding.
Multiplexing
Multiplexing enables multiple SSH sessions to share a single TCP connection. This improves efficiency and reduces latency, especially in high-traffic environments. For instance, system administrators can simultaneously manage multiple servers using a single SSH connection, reducing network overhead and streamlining their workflow.
Compression
SSH supports data compression algorithms, such as zlib, to reduce the size of data transmitted over the network. This can significantly improve performance, particularly when transferring large files or working with bandwidth-constrained connections. Compression is especially beneficial for slow or unstable network environments, as it minimizes data loss and ensures efficient data transfer.
X11 Forwarding
X11 forwarding allows users to remotely display graphical applications running on the server on their local machine. This is useful for accessing graphical user interfaces (GUIs) of remote servers, enabling tasks like software development, remote desktop access, and running graphical applications from anywhere with an internet connection.
Closure
SSH, with its inherent security mechanisms and flexibility, continues to be a vital tool in the modern cybersecurity landscape. By understanding the concepts and techniques Artikeld in this guide, you can harness the power of SSH to establish secure remote connections, manage user accounts effectively, and safeguard your data from unauthorized access.
Whether you are a seasoned system administrator or a novice user, this guide will provide you with the knowledge and insights necessary to leverage SSH to its full potential.