SSH.SSHSlowdns.com – In the realm of secure network communication, SSH (Secure Shell) has emerged as a cornerstone protocol, offering a robust and versatile means of establishing encrypted connections. SSH’s ability to seamlessly traverse firewalls and NAT devices has made it a ubiquitous tool for remote administration, secure file transfers, and tunneling applications.
This article delves into the intricacies of SSH UDP, exploring its unique characteristics, advantages, and use cases, while also addressing security considerations and troubleshooting techniques.
UDP (User Datagram Protocol), known for its low overhead and connectionless nature, plays a pivotal role in SSH communication, enabling efficient data transfer without the burden of establishing and maintaining network connections. This guide will shed light on the advantages and potential drawbacks of using UDP for SSH, providing a comprehensive understanding of its implementation and configuration across various operating systems and network environments.
SSH Protocol and UDP Port 30
The Secure Shell (SSH) protocol enables secure remote login and command execution over an unsecured network. It establishes a secure channel for data transmission between two computers, allowing users to access and control remote systems as if they were physically present.UDP
port 30 plays a crucial role in SSH communication. It is the default port used for establishing the initial connection between the SSH client and server. During this connection phase, key exchange and authentication take place. Once the secure channel is established, the actual data transfer occurs over a different port, typically TCP port 22.Using
UDP for SSH offers several advantages. UDP is a connectionless protocol, which means it does not require the establishment of a persistent connection. This makes it faster and more efficient for establishing the initial connection, especially in situations where network latency or packet loss may be an issue.
Additionally, UDP is less susceptible to certain types of network attacks, such as SYN floods, which can be beneficial for maintaining secure connections.However, UDP also has some disadvantages. Since it is a connectionless protocol, it does not provide the same level of reliability as TCP.
Data packets may be lost or corrupted during transmission, which can lead to potential issues during the authentication and key exchange process. Furthermore, UDP does not support flow control mechanisms, which can result in congestion or data loss if the network is heavily loaded.
SSH UDP Tunneling
SSH UDP tunneling is a technique that allows you to establish a secure, encrypted tunnel over a UDP port. This can be useful for bypassing firewalls or other network restrictions that block UDP traffic.
To create an SSH UDP tunnel, you will need to use the -L option of the SSH command. The following command will create a tunnel from your local port 10000 to the remote host’s port 30000:
ssh
-L 10000
remote_host:30000 user@remote_host
Once the tunnel is established, you can send UDP traffic to your local port 10000 and it will be forwarded to the remote host’s port 30000.
Use Cases
SSH UDP tunneling can be used for a variety of purposes, including:
- Bypassing firewalls or other network restrictions that block UDP traffic
- Creating a secure, encrypted connection between two hosts
- Tunneling UDP-based applications through a firewall
Security Considerations
Utilizing SSH over UDP introduces certain security considerations that warrant attention.
One primary concern is the potential for amplification attacks , where malicious actors leverage SSH UDP to amplify the impact of DDoS attacks by spoofing source IP addresses. This can result in significant network traffic oversubscription and service disruptions.
Vulnerabilities and Attack Vectors
SSH UDP presents several potential vulnerabilities that attackers may exploit:
- IP spoofing: Attackers can spoof IP addresses to launch amplification attacks or bypass network access controls.
- Port scanning: UDP ports are easily scannable, allowing attackers to identify and target SSH UDP servers.
- Denial-of-service (DoS) attacks: Malicious actors can flood SSH UDP servers with excessive traffic, leading to service interruptions.
Securing SSH UDP Connections
To mitigate security risks associated with SSH UDP, several measures can be implemented:
- Disable SSH UDP: If SSH UDP is not essential, it is advisable to disable it to reduce the attack surface.
- Configure firewall rules: Restrict access to SSH UDP ports only from trusted IP addresses.
- Use strong encryption: Implement strong encryption algorithms to protect data transmitted over SSH UDP.
- Monitor network traffic: Regularly monitor network traffic for suspicious activity and implement intrusion detection systems.
- Keep software updated: Ensure SSH software is up-to-date with the latest security patches.
Troubleshooting SSH UDP Issues
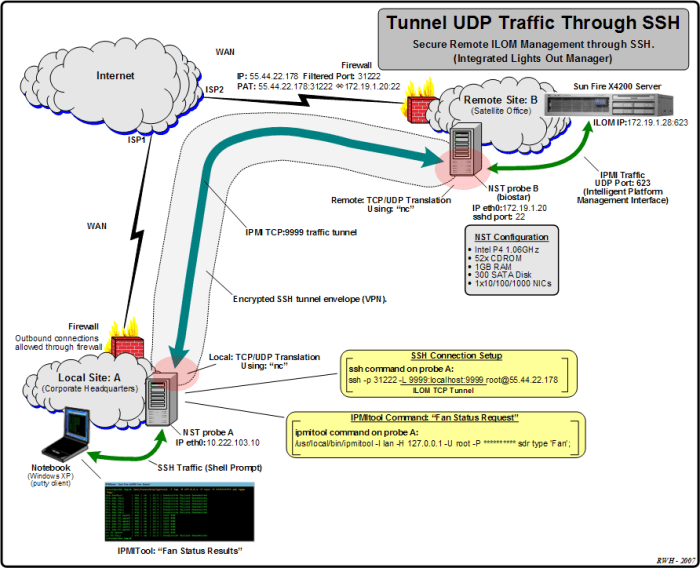
Troubleshooting SSH UDP connections involves identifying common problems and implementing effective solutions. This section explores typical issues and provides guidance for resolving them, ensuring optimal performance and reliability.
Error Messages
SSH UDP connections may encounter error messages, indicating underlying issues. Some common errors include:
“Connection refused”
The remote host is not accepting SSH UDP connections. Verify that the SSH service is enabled and configured to allow UDP connections.
“Permission denied”
The user does not have sufficient permissions to establish an SSH UDP connection. Ensure that the user has the necessary privileges.
“Invalid argument”
The SSH client or server encountered an invalid argument in the connection request. Check the configuration parameters and ensure they are valid.
Troubleshooting Steps
To troubleshoot SSH UDP issues, follow these steps:
- Verify that the SSH service is enabled and configured to allow UDP connections.
- Check the firewall settings on both the client and server to ensure that UDP port 30 is open.
- Ensure that the user has the necessary permissions to establish an SSH UDP connection.
- Review the SSH configuration files for any errors or misconfigurations.
- Consider using a packet analyzer to monitor the network traffic and identify any issues.
Performance Optimization
To optimize SSH UDP performance, consider the following tips:
- Use a high-performance UDP stack.
- Configure the SSH server to use a large UDP buffer size.
- Enable SSH compression to reduce the size of data packets.
- Avoid unnecessary data transfers.
SSH UDP in Different Operating Systems
SSH UDP is supported in various operating systems, each with its unique implementation and configuration. Understanding these differences is crucial for effective SSH UDP management.
Linux
- SSH UDP is enabled by default on most Linux distributions.
- To manage SSH UDP connections, use the ‘ss’ command, e.g., ‘ss
-tunlp | grep udp’. - Platform-specific considerations include firewall settings and kernel support for UDP tunneling.
Windows
- SSH UDP support requires the installation of an SSH server with UDP tunneling capabilities, such as OpenSSH for Windows.
- Configuration is typically done through the SSH server’s configuration file, e.g., ‘sshd_config’.
- Windows Firewall may need to be configured to allow UDP traffic on port 30.
macOS
-
- SSH UDP is supported natively in macOS.
- To manage SSH UDP connections, use the ‘netstat’ command, e.g., ‘netstat
-ltup | grep udp’.
li>Platform-specific considerations include system preferences and keychain management.
SSH UDP and Network Configurations
Network configurations play a crucial role in determining the performance and reliability of SSH UDP connections. Several factors, including firewalls, network address translation (NAT), and routing policies, can impact the functionality and efficiency of SSH UDP.
Firewalls
Firewalls can restrict or block SSH UDP traffic, resulting in connection failures or performance issues. To ensure seamless SSH UDP connections, it is essential to configure firewall rules that allow UDP traffic on port 30. Additionally, firewalls should be configured to allow incoming and outgoing traffic from the SSH server and client, respectively.
Network Address Translation (NAT)
NAT can introduce challenges for SSH UDP connections, as it can alter the source and destination IP addresses of packets. To mitigate these issues, it is recommended to use a NAT traversal mechanism, such as UDP hole punching or STUN, to establish and maintain SSH UDP connections through NAT devices.
Routing Policies
Routing policies can also affect SSH UDP performance. Optimal routing paths should be established to minimize latency and packet loss. Additionally, load balancing techniques can be employed to distribute SSH UDP traffic across multiple paths, improving overall network resilience.
SSH UDP and Proxy Servers
Proxy servers act as intermediaries between SSH UDP clients and servers, enhancing security and flexibility. They can mask the client’s IP address, providing anonymity and protecting against eavesdropping. Proxy servers also enable access to SSH UDP services that may be blocked by firewalls or network restrictions.
Advantages of Using Proxy Servers with SSH UDP
- Increased security and privacy
- Bypassing firewalls and network restrictions
- Load balancing and failover capabilities
Disadvantages of Using Proxy Servers with SSH UDP
- Potential performance overhead
- Additional configuration and maintenance requirements
- Security concerns if the proxy server is compromised
Example Proxy Server Configurations for SSH UDP
SOCKS5 proxy
This is a widely supported proxy protocol that provides authentication and encryption.
HTTP proxy
This is a versatile proxy protocol that can be used for both web browsing and SSH UDP tunneling.
SSH proxy
This is a specialized proxy protocol designed specifically for SSH traffic, offering enhanced security and performance.
SSH UDP and Port Forwarding
Port forwarding in SSH allows users to establish a secure connection between two remote systems through an SSH tunnel. This feature enables access to services or resources on a remote host that may not be accessible directly due to firewall restrictions or network configurations.SSH
UDP port forwarding operates similarly to TCP port forwarding but utilizes the UDP protocol. It involves creating a UDP tunnel between the local and remote systems, allowing UDP-based applications and services to communicate securely.
Use Cases for SSH UDP Port Forwarding
SSH UDP port forwarding finds applications in various scenarios:
-
- -*Remote Gaming
UDP is commonly used in online gaming. SSH UDP port forwarding enables gamers to access game servers that may be restricted by firewalls or network configurations.
- -*Remote Gaming
-*VoIP Applications
Voice over IP (VoIP) applications like Skype and Discord rely on UDP for real-time communication. SSH UDP port forwarding allows users to bypass firewalls and access VoIP services.
-*DNS Tunneling
SSH UDP port forwarding can be employed to tunnel DNS traffic, providing secure access to DNS servers and bypassing internet censorship or filtering.
-*Media Streaming
UDP is often used for streaming media content. SSH UDP port forwarding allows users to securely stream audio and video content from remote servers.
SSH UDP and VPNs
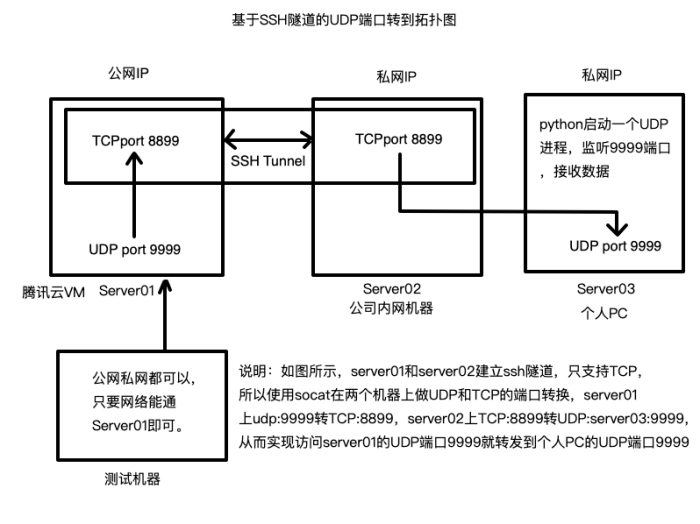
SSH UDP can be used to create VPN tunnels, providing a secure and encrypted connection between two remote networks.
This can be useful for connecting remote offices or employees to a central network, or for accessing resources on a private network from a public network.There are several advantages to using SSH UDP for VPN connections:
-
- -*Security
SSH UDP uses strong encryption to protect data in transit, making it difficult for eavesdroppers to intercept and decrypt the traffic.
- -*Security
-*Flexibility
SSH UDP can be used to create VPN tunnels over any type of network, including the Internet, private networks, and even cellular networks.
-*Cost-effectiveness
SSH UDP is a free and open-source protocol, making it an affordable option for creating VPN connections.
However, there are also some disadvantages to using SSH UDP for VPN connections:
-
- -*Performance
SSH UDP can be slower than other VPN protocols, such as OpenVPN or IPSec.
- -*Performance
-*Complexity
SSH UDP can be more complex to configure than other VPN protocols.
Overall, SSH UDP is a viable option for creating VPN tunnels, but it is important to weigh the advantages and disadvantages before deciding whether to use it.
Example
To create a VPN tunnel using SSH UDP, you can use the following steps:
- On the server, install the SSH server software and configure it to listen on UDP port 30.
- On the client, install the SSH client software and configure it to connect to the server using UDP port 30.
- Establish a SSH connection between the client and the server.
- Use the SSH tunnel to route traffic between the client and the server.
SSH UDP and Cloud Environments
SSH UDP can be utilized in cloud computing environments to facilitate secure communication between cloud instances, on-premises infrastructure, and remote users. It provides a reliable and efficient method for data transfer and remote management in the cloud.One of the primary benefits of using SSH UDP in the cloud is its ability to establish secure connections over UDP, a connectionless protocol.
This can be particularly advantageous in cloud environments where bandwidth is limited or latency is a concern, as UDP does not require acknowledgment of every packet received, reducing overhead and improving performance.However, it is important to note that SSH UDP connections may be more susceptible to packet loss and reordering compared to TCP-based SSH connections.
Therefore, it is crucial to carefully consider the specific requirements and limitations of the cloud environment when determining whether to use SSH UDP.
Best Practices for Managing SSH UDP Connections in the Cloud
-
- -*Configure firewalls and security groups
Implement appropriate firewall rules and security group configurations to restrict access to SSH UDP 30 ports only from authorized sources.
- -*Configure firewalls and security groups
-*Use strong encryption algorithms
Employ robust encryption algorithms such as AES-256 or ChaCha20 to protect data transmitted over SSH UDP 30 connections.
-*Limit access to privileged accounts
Restrict access to privileged accounts and use role-based access control (RBAC) mechanisms to minimize the risk of unauthorized access.
-*Monitor and audit connections
Regularly monitor SSH UDP 30 connections and audit logs to detect any suspicious activity or potential security breaches.
-*Consider using a VPN
Utilize a virtual private network (VPN) to establish a secure tunnel for SSH UDP 30 traffic, providing an additional layer of protection.