SSH (Secure Shell) is a critical tool for secure remote access and management of systems. While TCP is the default transport protocol for SSH, UDP (User Datagram Protocol) can also be used, offering certain advantages. This comprehensive guide delves into the world of SSH UDP, exploring its purpose, vulnerabilities, best practices, performance, applications, configuration, troubleshooting, case studies, and resources.
SSH UDP connections utilize port 3074, providing an alternative to traditional TCP-based SSH. UDP’s connectionless nature and low overhead make it suitable for specific use cases, such as remote desktop sharing and real-time applications. However, it also introduces unique security considerations that need to be addressed.
SSH UDP Port 3074
SSH UDP port 3074 is a port that is used by SSH (Secure Shell) for sending and receiving UDP (User Datagram Protocol) traffic. It is used to establish and maintain SSH connections over UDP, providing an alternative to the more commonly used TCP (Transmission Control Protocol).UDP
is a connectionless protocol, which means that it does not establish a reliable connection between two endpoints. This makes it faster and more efficient than TCP, but also less reliable. UDP is often used for applications that require fast and real-time data transfer, such as online gaming and video streaming.
Benefits of using UDP for SSH connections
There are several benefits to using UDP for SSH connections:
- Speed: UDP is a faster protocol than TCP, as it does not establish a reliable connection between two endpoints.
- Efficiency: UDP is more efficient than TCP, as it does not have to maintain a connection state.
- Low overhead: UDP has a lower overhead than TCP, as it does not have to send and receive acknowledgment packets.
Limitations of using UDP for SSH connections
There are also some limitations to using UDP for SSH connections:
- Unreliability: UDP is an unreliable protocol, which means that it does not guarantee that packets will be delivered in order or without errors.
- Security: UDP is less secure than TCP, as it does not provide any built-in encryption or authentication mechanisms.
- Compatibility: UDP is not as widely supported as TCP, so it may not be available on all devices.
SSH UDP Vulnerabilities
SSH UDP connections, while less common than TCP connections, can still be vulnerable to certain types of attacks. These vulnerabilities arise due to the nature of UDP, which is a connectionless protocol that does not provide the same level of security as TCP.
One common vulnerability associated with SSH UDP is the lack of authentication. Unlike TCP connections, UDP connections do not require the client to authenticate before establishing a connection. This makes it possible for attackers to impersonate legitimate clients and gain access to the target system.
Another vulnerability associated with SSH UDP is the lack of encryption. UDP packets are not encrypted by default, which means that attackers can eavesdrop on the traffic and potentially steal sensitive information, such as passwords or session keys.
Examples of Attacks
There are several different types of attacks that can exploit the vulnerabilities associated with SSH UDP connections. One common attack is the man-in-the-middle attack. In this attack, the attacker intercepts the traffic between the client and the server and impersonates one of the parties.
This allows the attacker to eavesdrop on the traffic and potentially steal sensitive information.
Another common attack is the denial-of-service attack. In this attack, the attacker sends a large number of UDP packets to the target system, which can overwhelm the system and cause it to crash.
SSH UDP Security Best Practices
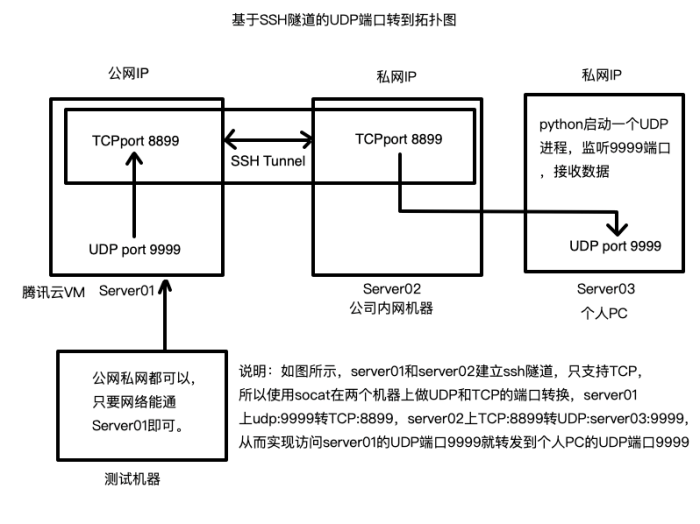
To safeguard SSH UDP connections, implementing robust security measures is paramount. This involves employing port filtering techniques to restrict access to the UDP port 3074 and deploying intrusion detection systems to monitor network traffic for suspicious activities.
Additionally, mitigating the risks associated with SSH UDP vulnerabilities requires proactive strategies. These include regularly updating SSH software to patch known vulnerabilities, using strong passwords and encryption algorithms, and limiting the number of failed login attempts to prevent brute force attacks.
Port Filtering
- Configure firewalls to block incoming traffic on UDP port 3074 from untrusted sources.
- Only allow traffic from authorized IP addresses or subnets.
- Consider using a dedicated SSH bastion host to further restrict access.
Intrusion Detection
- Deploy intrusion detection systems (IDS) to monitor network traffic for malicious activity.
- Configure IDS to detect and alert on suspicious patterns, such as repeated login attempts or port scans.
- Use IDS to block or quarantine traffic that exhibits malicious behavior.
SSH UDP Logging and Monitoring
Logging and monitoring SSH UDP traffic are essential for maintaining network security and detecting potential threats. By capturing and analyzing SSH UDP logs, organizations can gain visibility into SSH UDP connections, identify suspicious activities, and respond promptly to security incidents.
To establish an effective logging and monitoring system for SSH UDP connections, organizations should consider the following steps:
Log Collection
- Configure SSH UDP servers to log all SSH UDP connections, including successful and failed attempts.
- Centralize SSH UDP logs in a secure location for easy access and analysis.
- Use log management tools to collect, aggregate, and normalize SSH UDP logs from various sources.
Log Analysis
- Establish baselines for normal SSH UDP traffic patterns to identify deviations that may indicate suspicious activities.
- Monitor for anomalous events, such as unusual source or destination IP addresses, excessive connection attempts, or failed logins.
- Use intrusion detection systems (IDS) or security information and event management (SIEM) tools to analyze SSH UDP logs for known attack patterns and vulnerabilities.
Incident Response
- Define clear incident response procedures for SSH UDP security incidents.
- Establish communication channels to alert relevant teams and stakeholders in case of suspicious activities.
- Investigate SSH UDP security incidents promptly, identify the root cause, and implement appropriate mitigation measures.
SSH UDP Performance
When comparing SSH UDP connections to SSH TCP connections, UDP offers certain performance advantages. Due to its connectionless nature, UDP establishes sessions more quickly than TCP, reducing latency. Additionally, UDP does not require acknowledgment of received packets, further minimizing latency and improving overall performance.
Factors Affecting SSH UDP Performance
Several factors can impact the performance of SSH UDP connections:
- Network latency: High latency can lead to significant delays in packet transmission and reception, affecting overall performance.
- Packet loss: Packet loss can result in data being dropped during transmission, requiring retransmission and potentially causing performance degradation.
SSH UDP Applications
SSH UDP connections are commonly used for various applications, including:
Port forwarding
SSH UDP can be used to forward UDP traffic from one host to another, allowing applications that rely on UDP to communicate securely over an SSH connection.
DNS tunneling
SSH UDP can be used to tunnel DNS traffic over an SSH connection, allowing users to access DNS services securely and bypass censorship or firewalls.
Remote desktop
SSH UDP can be used for remote desktop applications, allowing users to access and control a remote computer’s graphical user interface (GUI) over an SSH connection.
File transfer
SSH UDP can be used for file transfer applications, allowing users to securely transfer files between two hosts over an SSH connection. Advantages of using SSH UDP for these applications include:
Security
SSH UDP connections are encrypted, providing a secure channel for data transmission.
Reliability
SSH UDP connections are reliable, ensuring that data is transmitted without errors or loss.
Flexibility
SSH UDP connections can be used for a wide range of applications, making it a versatile tool for network administrators. Disadvantages of using SSH UDP for these applications include:
Performance
SSH UDP connections can be slower than TCP connections, especially for high-bandwidth applications.
Complexity
SSH UDP connections can be more complex to configure than TCP connections, requiring additional knowledge and expertise.
SSH UDP Configuration
SSH UDP connections can be configured on various operating systems by modifying the SSH configuration file. This file typically resides in the /etc/ssh directory.
Configuration File Options
The SSH configuration file contains several options that can be used to configure SSH UDP connections. Some of the most common options include:
-
- -*Port This option specifies the UDP port that SSH will listen on. The default port is 3074.
-*AddressFamily
This option specifies the address family that SSH will use. The default is “any”, which allows SSH to listen on both IPv4 and IPv6 addresses.
-*ListenAddress
This option specifies the IP address that SSH will listen on. The default is “0.0.0.0”, which allows SSH to listen on all IP addresses.
-*PermitRootLogin
This option specifies whether root login is allowed over SSH UDP. The default is “no”.
Example Configuration File
The following is an example SSH configuration file that enables SSH UDP connections on port 3074:“`# SSH configuration file# Listen on UDP port 3074Port 3074# Listen on all IP addressesListenAddress 0.0.0.0# Allow root login over SSH UDPPermitRootLogin yes“`
SSH UDP Troubleshooting
Troubleshooting SSH UDP connections involves identifying and resolving common problems that may arise during establishment or maintenance of the connection. These issues can range from network configuration errors to software misconfigurations or external factors affecting the connection.
Common Problems and Solutions
- Connection Refused: Occurs when the SSH server is not listening on UDP port 3074. Verify that the SSH server is configured to accept UDP connections and that the firewall is not blocking traffic on port 3074.
- Connection Timeout: Indicates that the SSH server is not responding within the expected timeframe. Check the network connection, ensure that the SSH server is running, and verify that there are no network latency issues.
- Authentication Failure: Occurs when the provided credentials are incorrect or the SSH server is not configured to accept UDP-based authentication. Double-check the credentials and ensure that the SSH server is configured for UDP authentication.
- Data Corruption: UDP connections are inherently unreliable, and data corruption can occur during transmission. Implement error detection and correction mechanisms, such as checksums or sequence numbers, to mitigate data corruption.
SSH UDP Case Studies
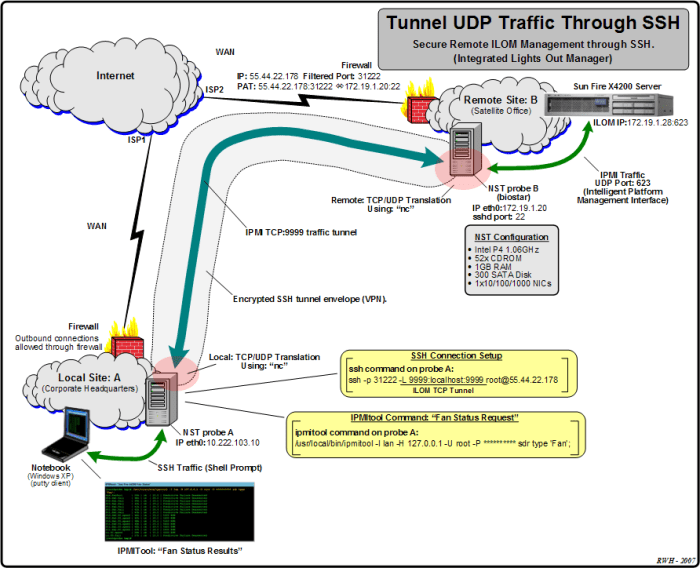
SSH UDP is gaining popularity in various real-world deployments, offering benefits like reduced latency and improved performance.
Challenges
Deploying SSH UDP can present challenges, such as:
Firewall configuration
Firewalls need to be configured to allow UDP traffic on port 3074.
Network latency
UDP is a connectionless protocol, making it susceptible to network latency issues.
Security concerns
SSH UDP may be vulnerable to spoofing attacks, as UDP packets do not contain source IP address validation.
Benefits
Despite these challenges, SSH UDP offers significant benefits:
Reduced latency
UDP’s connectionless nature reduces latency, making it ideal for interactive applications.
Improved performance
UDP’s simplified packet structure improves performance, especially for applications that require high throughput.
Scalability
UDP’s lightweight nature makes it scalable for large-scale deployments.
Example: Remote Management of IoT Devices
SSH UDP is widely used for remote management of IoT devices, where low latency and high throughput are critical. It enables secure and efficient communication between the management console and the IoT devices, facilitating real-time monitoring and control.
Example: Cloud Gaming
SSH UDP is also employed in cloud gaming platforms to provide a responsive and immersive gaming experience. The low latency and high throughput of UDP ensure smooth and uninterrupted gameplay, even over long distances.
SSH UDP Resources
A wealth of resources is available to assist you in delving deeper into the intricacies of SSH UDP. These resources, ranging from comprehensive articles to practical tools, are meticulously categorized to expedite your research endeavors.
Within each category, you will find a curated collection of resources that delve into specific aspects of SSH UDP, providing valuable insights and actionable guidance.
Articles and Documentation
- SSH UDP: A Comprehensive Guide
– An in-depth overview of SSH UDP, covering its benefits, limitations, and best practices. - Configuring SSH UDP on Linux and Windows
– Step-by-step instructions for setting up SSH UDP on different operating systems. - Troubleshooting SSH UDP Connectivity Issues
– A practical guide to diagnosing and resolving common SSH UDP connectivity problems.
Tools
- SSH UDP Port Scanner
– A tool for identifying open SSH UDP ports on remote systems. - SSH UDP Vulnerability Scanner
– A tool for assessing the security of SSH UDP configurations. - SSH UDP Performance Monitor
– A tool for monitoring the performance of SSH UDP connections.
Case Studies
- SSH UDP Deployment in a Large Enterprise
– A case study showcasing the successful implementation of SSH UDP in a complex enterprise environment. - SSH UDP for Remote Access in a Healthcare Setting
– A case study highlighting the use of SSH UDP for secure remote access to medical devices. - SSH UDP for Industrial Automation
– A case study demonstrating the benefits of SSH UDP for managing and monitoring industrial automation systems.
Outcome Summary
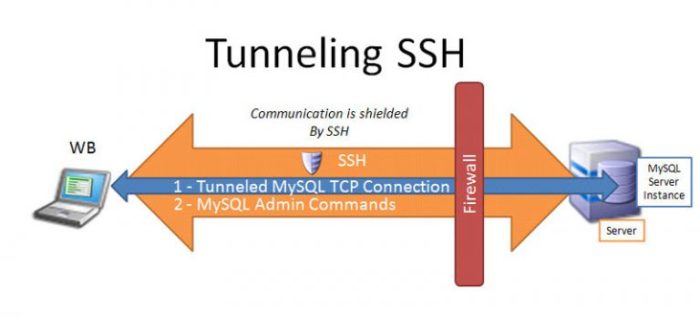
Understanding and implementing SSH UDP security best practices is crucial for organizations seeking to leverage its benefits while mitigating potential risks. By following the guidelines Artikeld in this guide, IT professionals can effectively secure their SSH UDP connections, ensuring the integrity and confidentiality of sensitive data and systems.