ssh.sshslowdns.com – In the realm of secure remote access, the Secure Shell (SSH) protocol reigns supreme, offering a robust and versatile means of establishing encrypted connections over various transport protocols. Among these protocols, UDP stands out as an intriguing option, presenting both advantages and challenges.
This comprehensive guide delves into the intricacies of SSH over UDP, exploring its role in SSH, comparing it to TCP, examining its applications, and unraveling its security implications. Furthermore, we will delve into SSH UDP tunneling and port forwarding, providing practical insights and troubleshooting tips to ensure optimal performance and security.
SSH UDP Protocol

SSH (Secure Shell) is a network protocol that provides secure remote access to a computer system. It uses UDP (User Datagram Protocol) as an alternative transport protocol to TCP (Transmission Control Protocol).
UDP is a connectionless protocol, which means that it does not establish a dedicated connection between the client and the server. Instead, it sends packets of data without any guarantee of delivery or order.
Advantages of Using UDP in SSH
- Speed: UDP is faster than TCP because it does not have to establish a connection before sending data.
- Efficiency: UDP is more efficient than TCP because it does not have to maintain a connection state.
- Low overhead: UDP has a lower overhead than TCP because it does not have to send acknowledgment packets.
Disadvantages of Using UDP in SSH
- Unreliable: UDP is an unreliable protocol, which means that it does not guarantee delivery of packets.
- Unordered: UDP does not guarantee that packets will be delivered in the order they were sent.
Comparison of SSH UDP with SSH TCP
| Feature | SSH UDP | SSH TCP |
|---|---|---|
| Transport protocol | UDP | TCP |
| Connection-oriented | No | Yes |
| Reliability | No | Yes |
| Speed | Faster | Slower |
| Efficiency | More efficient | Less efficient |
| Overhead | Lower | Higher |
SSH UDP Port
SSH, by default, utilizes a specific UDP port for its operations. Understanding this port’s purpose and the implications of altering it is crucial for maintaining a secure SSH environment.
Default UDP Port
SSH typically employs port 53 by default for UDP communication. This port is primarily used for DNS (Domain Name System) queries, which are essential for resolving domain names to IP addresses.
Purpose of UDP Port
SSH leverages UDP port 53 for specific tasks, including:
- DNS Lookups: SSH utilizes UDP port 53 to perform DNS lookups, resolving hostnames to IP addresses.
- Connectivity Checks: SSH employs UDP port 53 to conduct connectivity checks, ensuring that the remote host is reachable.
Security Implications of Non-Default UDP Port
While SSH primarily uses UDP port 53, it is possible to configure a non-default port for UDP communication. However, this practice may introduce security risks:
- Port Scanning: Non-default UDP ports can attract the attention of attackers who scan for open ports on a network.
- Increased Attack Surface: Using a non-default UDP port expands the attack surface, providing additional potential entry points for malicious actors.
SSH UDP Applications
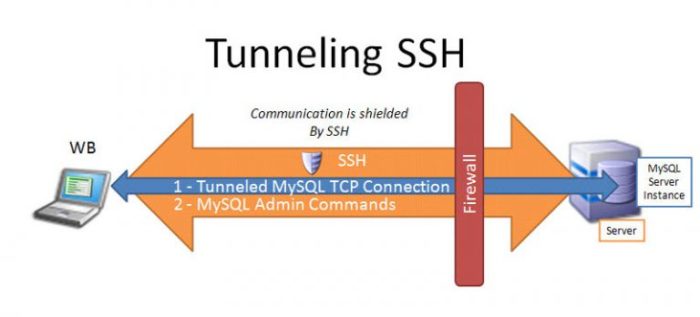
SSH UDP is used in various applications to enhance their performance and security. Some common applications include:
Network Management
SSH UDP is widely used for network management tasks, such as remote monitoring, configuration, and troubleshooting. It provides a secure and efficient way to access and manage network devices, even across firewalls and NAT devices.
Data Transfer
SSH UDP can be used for secure data transfer between two hosts. It is particularly useful for transferring sensitive data, as it encrypts the data in transit and prevents unauthorized access.
Virtual Private Networks (VPNs)
SSH UDP is a popular choice for establishing VPN connections. It provides a secure and encrypted tunnel between two hosts, allowing them to communicate securely over an untrusted network.
Remote Desktop Access
SSH UDP can be used for remote desktop access, allowing users to securely connect to and control a remote computer. It provides a secure and encrypted connection, ensuring the confidentiality and integrity of the data being transferred.
SSH UDP Security
SSH UDP, while offering performance benefits, also presents certain security risks that need to be addressed to ensure the integrity and confidentiality of data transmitted over the network. Let’s delve into these risks and explore measures to mitigate them, ensuring the secure use of SSH UDP connections.
One of the primary security risks associated with SSH UDP is the potential for eavesdropping and interception of data. Since UDP is a connectionless protocol, it does not establish a secure channel for communication, making it susceptible to man-in-the-middle attacks.
An attacker could potentially intercept and manipulate the data being transmitted, leading to data breaches or unauthorized access to systems.
Mitigating Security Risks
To mitigate these risks and enhance the security of SSH UDP connections, several measures can be implemented:
- Use Strong Encryption Algorithms: Employing robust encryption algorithms, such as AES-256 or ChaCha20-Poly1305, ensures that data is securely encrypted during transmission, minimizing the risk of eavesdropping and data interception.
- Enable IP Spoofing Protection: Configure firewalls or network security devices to prevent IP spoofing attacks. This prevents attackers from impersonating legitimate hosts and gaining unauthorized access to the network.
- Limit Access to SSH UDP Ports: Restrict access to SSH UDP ports only to authorized users and devices. Implement access control lists (ACLs) or firewalls to block unauthorized access attempts.
- Use SSH Key-Based Authentication: Instead of relying on passwords, which can be compromised, utilize SSH key-based authentication. This provides a more secure method of authenticating users and prevents unauthorized access.
- Monitor Network Traffic: Regularly monitor network traffic for suspicious activities or unauthorized access attempts. Use intrusion detection systems (IDS) or security information and event management (SIEM) tools to detect and respond to potential threats.
By implementing these best practices, organizations can significantly enhance the security of SSH UDP connections, protecting data integrity and confidentiality while leveraging the performance benefits offered by UDP.
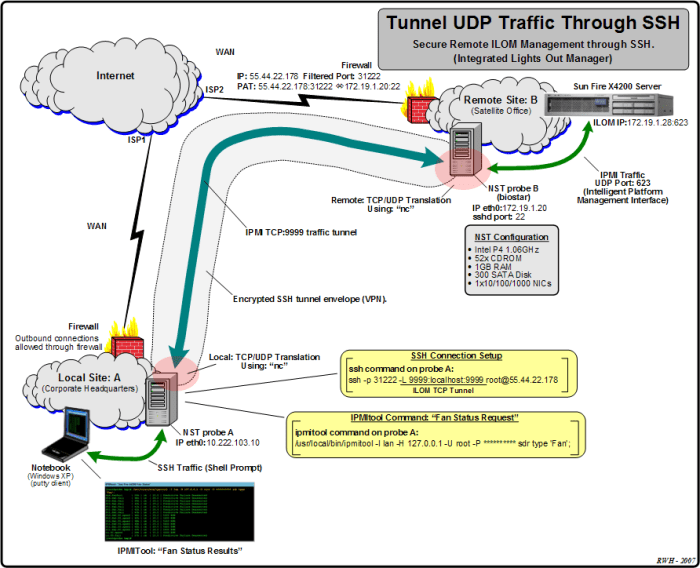
SSH UDP Tunneling
SSH UDP tunneling is a technique that allows users to securely forward UDP traffic over an SSH connection. This can be useful for a variety of purposes, such as accessing UDP-based services that are blocked by a firewall or accessing remote devices that are only accessible via UDP.SSH
UDP tunneling works by encapsulating UDP packets within SSH packets. This allows the UDP packets to be transmitted over the SSH connection, even if the underlying network does not support UDP. The SSH server then decapsulates the UDP packets and forwards them to the appropriate destination.There
are several benefits to using SSH UDP tunneling. First, it is a secure way to forward UDP traffic. SSH uses strong encryption to protect the data that is transmitted over the connection, so it is not possible for eavesdroppers to intercept the UDP packets.
Second, SSH UDP tunneling is relatively easy to set up. It only requires a few simple commands to establish a tunnel. Third, SSH UDP tunneling is compatible with a wide range of operating systems and devices.Here are some examples of how SSH UDP tunneling can be used:* To access UDP-based services that are blocked by a firewall.
- To access remote devices that are only accessible via UDP.
- To create a secure tunnel for gaming or other UDP-based applications.
SSH UDP Port Forwarding
SSH UDP port forwarding allows you to establish a secure connection between two hosts over a UDP network, typically used for applications that require real-time data transfer.
Benefits of SSH UDP Port Forwarding
SSH UDP port forwarding provides several benefits:
-
- -*Secure data transmission Encrypts data transmitted over the UDP connection, ensuring confidentiality and integrity.
-*Firewall traversal
Allows applications to bypass firewalls by tunneling traffic through an SSH connection.
-*Remote access
Enables access to UDP services on a remote host from a local computer.
Examples of SSH UDP Port Forwarding
SSH UDP port forwarding can be used in various scenarios:
-
- -*Gaming Allows gamers to connect to online games that use UDP protocols, even behind firewalls.
-*VoIP
Facilitates secure voice and video calls over UDP-based VoIP applications.
-*DNS tunneling
Enables DNS queries to be sent over an SSH connection, bypassing DNS filtering or censorship.
SSH UDP Performance
SSH UDP performance can vary depending on several factors, including network conditions, encryption algorithms, and hardware capabilities.Optimizing
SSH UDP performance involves finding the right balance between security and speed. Stronger encryption algorithms provide better security but can impact performance. Similarly, faster hardware can improve performance but may be more expensive.
Factors Affecting SSH UDP Performance
- Network conditions: High latency and packet loss can significantly impact SSH UDP performance.
- Encryption algorithms: Stronger encryption algorithms, such as AES-256, require more computational power and can slow down performance.
- Hardware capabilities: Faster CPUs and network adapters can improve SSH UDP performance.
- SSH server configuration: Properly configuring the SSH server, such as setting appropriate packet sizes and compression algorithms, can optimize performance.
- Client configuration: Optimizing the SSH client settings, such as disabling unnecessary features and adjusting buffer sizes, can also improve performance.
Tips for Optimizing SSH UDP Performance
- Use a strong encryption algorithm that balances security and performance.
- Upgrade to faster hardware if possible.
- Optimize the SSH server configuration by setting appropriate packet sizes and compression algorithms.
- Disable unnecessary SSH client features and adjust buffer sizes for optimal performance.
- Monitor SSH UDP performance regularly and make adjustments as needed.
SSH UDP Troubleshooting
SSH UDP troubleshooting involves identifying and resolving issues that may arise when using SSH over UDP. Common problems include connection failures, slow performance, and security vulnerabilities.
To diagnose and resolve these issues, it is important to understand the underlying causes and have a systematic approach to troubleshooting.
Identifying Common SSH UDP Issues
- Connection failures: SSH UDP connections may fail due to incorrect configuration, firewall blocking, or network connectivity issues.
- Slow performance: SSH UDP performance can be affected by network latency, congestion, or server load.
- Security vulnerabilities: SSH UDP can be susceptible to security vulnerabilities, such as spoofing attacks or eavesdropping.
Troubleshooting Guide for SSH UDP
- Check connectivity: Verify that the SSH server is reachable over UDP and that there are no firewall or network issues.
- Inspect configuration: Ensure that the SSH client and server are configured correctly for UDP transport, including the correct port number and protocol version.
- Monitor performance: Use tools like tcpdump or Wireshark to monitor SSH UDP traffic and identify any performance bottlenecks or packet loss.
- Check security settings: Review SSH UDP security settings, such as encryption algorithms and key exchange methods, to ensure they are secure and appropriate for the intended use case.
SSH UDP Tools
SSH UDP tools enable administrators and users to effectively manage and monitor SSH UDP connections, providing valuable insights into network performance, security, and troubleshooting. These tools offer a range of features, including connection monitoring, packet analysis, and tunneling management.
SSH UDP Connection Monitoring Tools
- Tcpdump: A powerful command-line tool for capturing and analyzing network traffic, including SSH UDP packets. It allows administrators to monitor connection status, packet size, and transmission time.
- Wireshark: A graphical network analyzer that provides detailed analysis of SSH UDP traffic. It enables users to inspect packet headers, payloads, and timestamps, facilitating in-depth troubleshooting and security audits.
SSH UDP Packet Analysis Tools
- Nmap: A comprehensive network scanner that includes UDP scanning capabilities. Nmap can detect open SSH UDP ports, identify version information, and perform security audits.
- Metasploit: A penetration testing framework that includes modules for exploiting SSH UDP vulnerabilities. It enables security professionals to assess the security posture of SSH UDP servers and identify potential attack vectors.
SSH UDP Tunneling Management Tools
- OpenSSH: A popular SSH implementation that supports UDP tunneling. OpenSSH allows users to establish secure UDP tunnels through SSH connections, enabling the transmission of data over UDP-based applications.
- SSHuttle: A dedicated SSH tunneling tool that simplifies the process of creating and managing UDP tunnels. SSHuttle provides a user-friendly interface and supports multiple tunneling modes, making it suitable for various applications.
Comparison of SSH UDP Tools
| Tool | Features | Benefits ||—|—|—|| Tcpdump | Packet capture and analysis | In-depth network monitoring and troubleshooting || Wireshark | Graphical network analyzer | Intuitive visualization and analysis of SSH UDP traffic || Nmap | UDP scanning and security audits | Comprehensive network reconnaissance and vulnerability assessment || Metasploit | SSH UDP exploitation modules | Advanced security testing and vulnerability identification || OpenSSH | UDP tunneling support | Secure and reliable UDP tunneling for various applications || SSHuttle | Dedicated SSH tunneling tool | Easy-to-use interface and support for multiple tunneling modes |
SSH UDP Best Practices
To ensure the secure and efficient use of SSH UDP, it is essential to adhere to a set of best practices. These practices aim to mitigate potential risks and enhance the overall effectiveness of SSH UDP.
Neglecting these best practices can lead to compromised security, reduced performance, and increased vulnerability to attacks. Therefore, it is paramount to implement and follow these guidelines diligently.