SSH UDP is a powerful protocol that offers secure remote access to servers and devices. It is a lightweight and efficient alternative to SSH TCP, making it ideal for applications that require low latency and high performance. In this comprehensive guide, we will explore the benefits, configuration, security implications, performance considerations, and use cases of SSH UDP.
We will also provide a comparison to other protocols, troubleshooting tips, and best practices to ensure secure and efficient use.
SSH UDP leverages the User Datagram Protocol (UDP) to establish a secure channel between two hosts. UDP is a connectionless protocol that provides faster transmission speeds compared to TCP, which is connection-oriented. This makes SSH UDP particularly suitable for applications that require real-time data transfer, such as remote desktop access, audio/video streaming, and gaming.
Overview of SSH UDP
SSH UDP is a secure remote access protocol that utilizes the User Datagram Protocol (UDP) for data transmission, offering an alternative to the commonly used SSH over TCP.
SSH UDP is designed to enhance performance in scenarios where latency is a critical factor, such as interactive remote desktop sessions or real-time data transfer. UDP’s connectionless nature allows for faster transmission and reduced overhead, making it a suitable choice for applications that prioritize speed over reliability.
Benefits of SSH UDP
- Lower latency: UDP’s connectionless nature eliminates the need for handshakes and acknowledgments, resulting in faster data transmission.
- Improved performance: UDP’s reduced overhead and connectionless nature can significantly enhance performance in latency-sensitive applications.
Limitations of SSH UDP
- Unreliable delivery: UDP does not guarantee the delivery of packets, which can lead to data loss or corruption.
- Vulnerability to packet loss: UDP’s lack of error correction and flow control makes it susceptible to packet loss, especially in congested networks.
Configuration of SSH UDP
Configuring SSH UDP involves modifying the server and client configurations to enable UDP-based SSH connections.
On the server side, the sshd_config file needs to be edited. Find the line Protocol 2 and uncomment it by removing the leading # character. Additionally, add the line Port 2222 to specify the UDP port for SSH connections.
For example:
“`# Allow SSH connections over UDPProtocol 2Port 2222“`
On the client side, the ssh_config file needs to be edited. Add the following line to enable UDP connections:
“`# Enable SSH UDP connectionsEnableSSHUDP yes“`
Additionally, the UDP port can be specified using the -p flag when connecting to the server:
“`ssh
p 2222 [email protected]
“`
Security Implications of SSH UDP
SSH UDP, while offering performance advantages, comes with certain security implications that must be carefully considered before deployment.
One of the main concerns with SSH UDP is its increased exposure to denial-of-service (DoS) attacks. UDP is a connectionless protocol, meaning that it does not establish a persistent connection between the client and the server. As a result, attackers can easily send large volumes of UDP packets to a target SSH server, overwhelming its resources and causing it to become unresponsive.
Mitigating DoS Attacks
To mitigate DoS attacks against SSH UDP, several strategies can be employed:
- Rate Limiting: Implement rate limiting mechanisms to restrict the number of UDP packets that can be received by the SSH server within a given time frame.
- IP Filtering: Block incoming UDP packets from suspicious or known malicious IP addresses.
- Firewall Rules: Configure firewall rules to drop UDP packets that do not originate from trusted sources.
- UDP Flood Detection: Use intrusion detection systems (IDS) or other tools to detect and block UDP flood attacks.
In addition to DoS attacks, SSH UDP may also be vulnerable to man-in-the-middle (MitM) attacks. MitM attacks occur when an attacker intercepts the communication between the client and the server and impersonates one of them. In the case of SSH UDP, an attacker could intercept UDP packets and inject malicious data into the communication stream.
Mitigating MitM Attacks
To mitigate MitM attacks against SSH UDP, the following measures can be taken:
- IPsec: Implement IPsec encryption and authentication to protect the UDP packets from eavesdropping and tampering.
- SSH Key Exchange: Use strong SSH key exchange algorithms to generate unique session keys for each connection, making it difficult for an attacker to impersonate the client or the server.
- Multi-factor Authentication: Require multiple factors of authentication, such as a password and a one-time password (OTP), to make it more difficult for an attacker to gain access to the SSH server.
Performance Considerations of SSH UDP
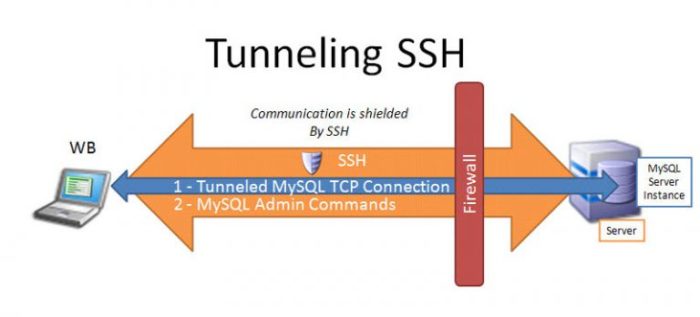
SSH UDP offers distinct performance characteristics compared to its TCP counterpart. UDP’s connectionless nature eliminates the need for handshaking and session maintenance, resulting in lower overhead and potentially faster initial connection establishment. However, UDP lacks built-in error correction and flow control mechanisms, which can impact performance under certain network conditions.
Factors Affecting Performance
Several factors can influence the performance of SSH UDP:
-
- -*Network latency
High latency can hinder UDP’s efficiency, as it increases the time required for packets to be transmitted and received.
- -*Network latency
-*Packet loss
UDP does not provide guaranteed delivery, so packet loss can occur. Excessive packet loss can degrade performance and lead to data corruption.
-*Network congestion
In congested networks, UDP packets may be dropped due to buffer overflow, affecting performance and reliability.
-*Server load
Heavily loaded servers can experience performance issues, especially with UDP connections that require more processing resources than TCP connections.
Optimization Techniques
To optimize SSH UDP performance, consider the following techniques:
-
- -*Use a reliable network
Minimize latency and packet loss by utilizing a stable and low-latency network infrastructure.
- -*Use a reliable network
-*Implement error handling
Employ mechanisms to handle packet loss and ensure data integrity.
-*Configure UDP buffer sizes
Adjust UDP buffer sizes to optimize packet transmission and reception under varying network conditions.
-*Limit the number of concurrent UDP connections
Control the number of simultaneous UDP connections to avoid overloading the server and affecting performance.
Use Cases for SSH UDP
SSH UDP offers several advantages over SSH TCP, making it suitable for specific use cases.
Its primary benefit lies in its ability to traverse network firewalls and NAT devices more easily than SSH TCP.
Penetration Testing
SSH UDP is often used in penetration testing to bypass firewalls and gain access to remote systems. By leveraging UDP’s ability to pass through restrictive network configurations, testers can establish a secure connection to the target system and perform vulnerability assessments.
Remote Management of Devices Behind Firewalls
In environments where devices are located behind firewalls, SSH UDP can provide a reliable means of remote management. It allows administrators to securely access and configure devices without having to reconfigure the firewall to allow SSH TCP traffic.
Data Exfiltration
Due to its ability to bypass firewalls, SSH UDP can be used for data exfiltration purposes. Attackers may leverage this capability to stealthily transfer sensitive data out of a network by tunneling it through SSH UDP connections.
Secure Communication in Unstable Networks
In networks with unreliable or intermittent connectivity, SSH UDP can provide a more stable connection than SSH TCP. UDP’s connectionless nature makes it less susceptible to packet loss and network disruptions, ensuring a reliable communication channel.
Comparison of SSH UDP to Other Protocols
SSH UDP is a variant of the Secure Shell (SSH) protocol that uses the User Datagram Protocol (UDP) instead of the Transmission Control Protocol (TCP). This makes SSH UDP faster and more efficient for certain applications, but it also makes it less secure.
Here is a comparison of SSH UDP to other common file transfer protocols:
OpenSSH
- OpenSSH is the most popular SSH implementation. It is a free and open-source software that is available for a variety of platforms.
- OpenSSH is a secure and reliable protocol that supports a wide range of features, including file transfer, remote command execution, and port forwarding.
- OpenSSH is slower than SSH UDP, but it is more secure.
SFTP
- SFTP is a file transfer protocol that is built on top of SSH. It is a secure and reliable protocol that supports a wide range of features, including file transfer, directory listing, and file permissions.
- SFTP is slower than SSH UDP, but it is more secure.
- SFTP is a good choice for transferring files over a secure network.
FTPS
- FTPS is a file transfer protocol that is built on top of TLS/SSL. It is a secure and reliable protocol that supports a wide range of features, including file transfer, directory listing, and file permissions.
- FTPS is slower than SSH UDP, but it is more secure.
- FTPS is a good choice for transferring files over a secure network.
Troubleshooting SSH UDP Issues
SSH UDP can encounter various issues that require troubleshooting. Here’s a guide to help resolve common problems:
Connection Failures
- Check if the UDP port (default 53) is open on both the client and server firewalls.
- Ensure the client and server are using the same UDP port.
- Verify the client and server IP addresses are correct.
Slow Performance
- Check for network congestion or packet loss.
- Ensure the client and server are physically close or connected via a high-bandwidth network.
- Consider using a different UDP port to avoid potential network congestion.
Authentication Failures
- Check if the client has the correct credentials (username and password) to access the server.
- Verify that the server has public key authentication enabled if using SSH keys.
- Ensure the client is using the correct key file if using SSH keys.
Data Corruption
- Check for network errors or packet loss.
- Consider increasing the UDP packet size to reduce fragmentation.
- Use error-correcting codes (ECC) to detect and correct errors.
Other Issues
- If SSH UDP is not working, try using SSH TCP instead.
- Check if the server is running the SSH daemon (sshd).
- Ensure the client is using a compatible SSH version with the server.
Best Practices for SSH UDP
To ensure secure and efficient usage of SSH UDP, adhering to best practices is crucial. This involves implementing recommended configurations and following operational guidelines.
Recommended Configurations
- Use Strong Encryption: Employ robust encryption algorithms such as AES-256 or ChaCha20-Poly1305 for data protection.
- Enable Authentication: Configure SSH UDP to require authentication, utilizing methods like public-key cryptography or passwords.
- Limit Access: Restrict access to SSH UDP services by implementing firewalls and access control lists (ACLs).
Operational Guidelines
- Regular Updates: Regularly update SSH UDP software and firmware to patch vulnerabilities and enhance security.
- Monitor Logs: Monitor SSH UDP logs for suspicious activities and potential security breaches.
- Educate Users: Inform users about the importance of SSH UDP security and provide guidance on best practices.
Future Developments in SSH UDP
The future of SSH UDP is promising, with ongoing developments and research exploring new frontiers in secure remote access and data transfer. These advancements aim to enhance the protocol’s capabilities, improve performance, and address emerging security challenges.
Emerging Trends and Research Directions
- Enhanced Encryption Algorithms: Research focuses on developing stronger encryption algorithms to safeguard data transmissions against advanced cryptanalytic techniques.
- Improved Key Management: New key management techniques are being explored to simplify key distribution and rotation, ensuring robust security and preventing unauthorized access.
- Performance Optimizations: Ongoing research aims to optimize SSH UDP’s performance, reducing latency and increasing throughput for demanding applications.
- Integration with Cloud Services: SSH UDP is being integrated with cloud platforms, enabling secure remote access and data management across distributed environments.
- Quantum-Safe Implementations: With the advent of quantum computing, research is exploring quantum-safe implementations of SSH UDP to mitigate potential security risks posed by quantum attacks.
Design a table summarizing the key features and benefits of SSH UDP.
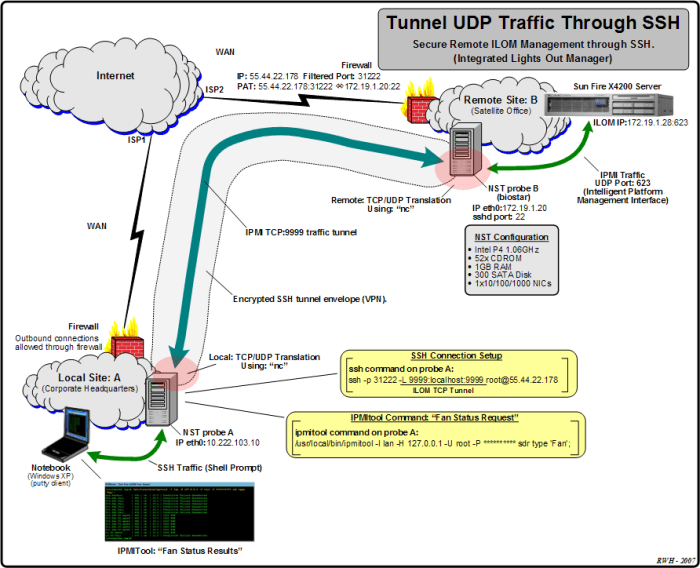
SSH UDP offers several key features and benefits that make it a valuable tool for secure remote access and data transfer.
The following table summarizes the key features and benefits of SSH UDP:
| Feature | Description | Benefit |
|---|---|---|
| Secure remote access | SSH UDP provides a secure channel for remote access to servers and other devices over UDP. | Allows for secure remote management and administration of systems. |
| Port forwarding | SSH UDP supports port forwarding, which allows users to securely access services running on a remote host through a local port. | Enables access to remote services without having to open firewall ports on the remote host. |
| Performance | SSH UDP can provide improved performance over SSH TCP, especially for applications that require low latency and high bandwidth. | Faster data transfer and improved responsiveness for applications. |
Final Summary
In conclusion, SSH UDP is a versatile and powerful protocol that provides secure remote access with low latency and high performance. Its flexibility and ease of configuration make it a valuable tool for system administrators, IT professionals, and anyone who requires secure and efficient remote access to servers and devices.
As technology continues to evolve, we can expect further advancements in SSH UDP, making it an even more indispensable tool for remote connectivity.