SSH.SSHSlowdns.com – In the realm of digital communication, the need for secure and reliable connections has become paramount. Enter SSH tunnel websocket, a powerful tool that enables the establishment of encrypted and private channels over the internet. By leveraging the strengths of both SSH tunneling and websockets, this technology empowers users to bypass restrictions, enhance security, and gain remote access with unparalleled efficiency.
SSH tunnel websocket seamlessly integrates the robust encryption and authentication mechanisms of SSH with the real-time and bidirectional communication capabilities of websockets. This combination opens up a world of possibilities for secure data transfer, remote desktop access, and seamless integration with web applications.
SSH Tunnel Websocket Overview
SSH tunneling is a technique that allows you to establish a secure connection between two computers over an insecure network. It works by creating an encrypted tunnel through which all traffic between the two computers is passed. This makes it possible to bypass firewalls and other restrictions that may be in place on the network.
Websockets are a technology that allows you to establish a real-time connection between a web browser and a server. This makes it possible to create interactive web applications that can send and receive data in real time. By combining SSH tunneling with websockets, it is possible to create secure, real-time web applications that can bypass firewalls and other restrictions.
Benefits of SSH Tunneling with Websockets
- Increased security: SSH tunneling encrypts all traffic between the two computers, making it impossible for eavesdroppers to intercept or read the data.
- Bypassing restrictions: SSH tunneling can be used to bypass firewalls and other restrictions that may be in place on the network. This makes it possible to access websites and other resources that would otherwise be blocked.
- Improved performance: SSH tunneling can improve the performance of web applications by reducing latency and jitter.
Benefits of Using SSH Tunnel Websocket
SSH tunneling over websockets offers several advantages that enhance security, privacy, and remote access capabilities. These benefits make it a valuable tool for various applications.
Increased Security
SSH tunneling establishes a secure channel between the client and server, encrypting all data transmitted over the connection. This prevents eavesdropping or unauthorized access to sensitive information, even when using untrusted networks like public Wi-Fi.
Data Encryption
The encryption provided by SSH tunneling ensures that data is protected from interception and unauthorized access. This is particularly crucial for transmitting sensitive data, such as financial information, personal data, or intellectual property, across public networks.
Remote Access
SSH tunneling allows users to securely access remote resources, such as servers or applications, from anywhere with an internet connection. This enables remote work, system administration, and file sharing without compromising security.
Setting Up an SSH Tunnel Websocket
Setting up an SSH tunnel websocket involves establishing a secure connection between a client and a server over an insecure network. Here’s a step-by-step guide to configure both the server and client:
Server Configuration
- Generate an SSH key pair on the server using the command `ssh-keygen
- t rsa`.
- Copy the public key to the client using `ssh-copy-id
- i ~/.ssh/id_rsa.pub username@client_address`.
- Start an SSH server on the server with `sudo service ssh start`.
Client Configuration
-
- On the client, establish a tunnel using a tool like PuTTY or OpenSSH.
- In PuTTY, navigate to “Connection” > “SSH” > “Tunnels” and enter the server’s address, port, and the local port to bind to.
- In OpenSSH, use the command `ssh
-L local_port
localhost:server_port username@server_address`.
- Test the connection by accessing the local port from the client.
SSH Tunneling Tools
-
- -*PuTTY
A free and open-source SSH client for Windows.
- -*PuTTY
-*OpenSSH
A popular SSH client available on most Linux and macOS systems.
-*AutoSSH
A tool that automatically restarts an SSH tunnel if it disconnects.
-*SSHGuard
A tool that protects SSH servers from brute-force attacks.
Security Considerations for SSH Tunnel Websocket
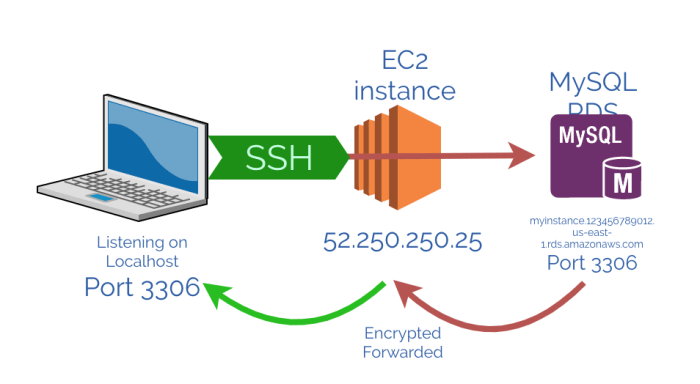
While SSH tunneling over websockets offers numerous advantages, it also introduces certain security implications that need to be addressed to ensure the confidentiality, integrity, and availability of the connection.
Understanding these potential vulnerabilities and implementing appropriate mitigation strategies is crucial for maintaining a secure SSH tunnel websocket connection.
Potential Vulnerabilities
One potential vulnerability lies in the fact that websockets operate over HTTP, which is an unencrypted protocol. This means that any data transmitted over an SSH tunnel websocket connection could be intercepted and read by a malicious third party if the connection is not properly secured.Another
vulnerability arises from the use of websockets, which are designed to be persistent connections. This means that an attacker who gains access to the websocket connection could potentially maintain that connection indefinitely, allowing them to eavesdrop on all traffic passing through the tunnel.
Mitigation Strategies
To mitigate these vulnerabilities, several strategies can be employed:
Use strong encryption algorithms
SSH tunneling supports a variety of encryption algorithms, including AES-256 and ChaCha20-Poly1305. It is important to use strong encryption algorithms to protect the data transmitted over the tunnel from eavesdropping.
Implement authentication and authorization mechanisms
Authentication and authorization mechanisms can be used to restrict access to the SSH tunnel websocket connection to authorized users only. This can be achieved using methods such as SSH key-based authentication or password authentication.
Use a secure websocket library
When implementing an SSH tunnel websocket connection, it is important to use a secure websocket library that supports features such as TLS encryption and certificate validation. This will help to protect the connection from eavesdropping and man-in-the-middle attacks.
Best Practices
In addition to implementing mitigation strategies, there are several best practices that can be followed to further enhance the security of SSH tunnel websocket connections:
Use a dedicated SSH server
It is recommended to use a dedicated SSH server for SSH tunneling, rather than using an SSH server that is also used for other purposes. This will help to reduce the risk of the SSH server being compromised and the SSH tunnel websocket connection being exploited.
Regularly update SSH software
SSH software should be regularly updated to the latest version to ensure that the latest security patches are applied. This will help to protect against known vulnerabilities in the SSH software that could be exploited to compromise the SSH tunnel websocket connection.
Monitor SSH tunnel websocket connections
It is important to monitor SSH tunnel websocket connections for any suspicious activity. This can be done using tools such as log analysis and intrusion detection systems. Any suspicious activity should be investigated promptly to determine the cause and take appropriate action.
Troubleshooting SSH Tunnel Websocket Issues
SSH tunneling over websockets offers reliable and secure connections, but it can sometimes encounter issues. This section explores common problems and provides troubleshooting tips to resolve them.
Identifying Common Problems
Several factors can lead to issues with SSH tunnel websockets, including:
- Firewall or network configuration blocking traffic
- Incorrect SSH configuration or key management
- Issues with the websocket server or client
- Intermittent network connectivity or latency
- Server-side limitations or restrictions
Troubleshooting Tips
To troubleshoot SSH tunnel websocket issues, consider the following steps:
| Issue | Troubleshooting Tips |
|---|---|
| Firewall or network configuration blocking traffic | Check firewall settings and network configurations to ensure that the necessary ports and IP addresses are allowed. |
| Incorrect SSH configuration or key management | Verify SSH configuration files and ensure that the correct keys are used for authentication. |
| Issues with the websocket server or client | Check the websocket server and client logs for errors or connection issues. |
| Intermittent network connectivity or latency | Monitor network connectivity and identify any potential sources of latency or packet loss. |
| Server-side limitations or restrictions | Consult with the server administrator to verify that the server supports SSH tunneling over websockets and that there are no restrictions in place. |
Advanced Techniques for SSH Tunnel Websocket
Multiplexing
Multiplexing enables multiple websocket connections to be established over a single SSH tunnel. This technique improves efficiency and reduces resource utilization, especially when managing numerous connections.
To implement multiplexing, the websocket server should be configured to accept multiple connections on the same port. The SSH client can then establish multiple websocket connections to the server through the tunnel, allowing for simultaneous data transfer.
Compression
Compression can significantly reduce the bandwidth required for SSH tunnel websocket connections. By compressing data before sending it through the tunnel, the amount of data transferred is minimized, resulting in improved performance and reduced latency.
Various compression algorithms can be employed, such as zlib or lz4. The choice of algorithm depends on the specific requirements and trade-offs between compression efficiency and computational overhead.
Load Balancing
Load balancing distributes incoming websocket connections across multiple SSH tunnels, ensuring optimal resource utilization and preventing any single tunnel from becoming overloaded.
A load balancer can be implemented using a software tool or a hardware appliance. The load balancer monitors the traffic load on each tunnel and dynamically redirects incoming connections to the least loaded tunnel, ensuring efficient and reliable operation.
Comparison with Other Tunneling Protocols
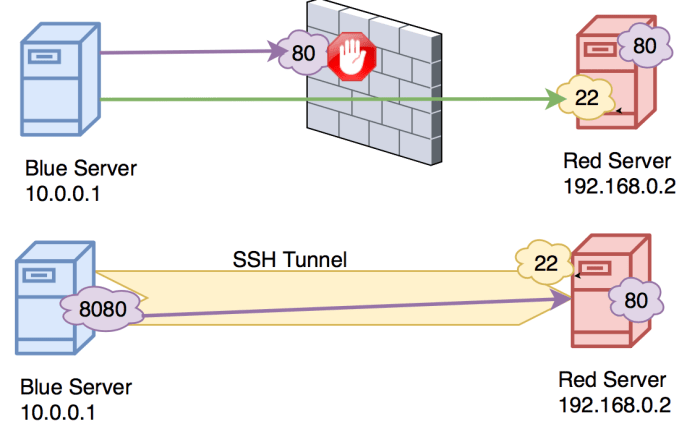
SSH tunneling over websockets offers unique advantages compared to alternative tunneling protocols like VPNs and HTTP tunnels. Let’s compare their strengths and weaknesses in a tabular format for clarity:
Tunneling Protocol
| Feature | SSH Tunneling over Websockets | VPN | HTTP Tunnel |
|---|---|---|---|
| Security | High: Encrypted with SSH and websockets | High: Encrypted with VPN protocols | Medium: Encrypted only by HTTP |
| Performance | Good: Efficient over high-latency connections | Variable: Can be slower due to VPN overhead | Poor: Slow over high-latency connections |
| Flexibility | High: Can tunnel any type of traffic | High: Supports various protocols and applications | Low: Limited to HTTP traffic |
| Setup Complexity | Medium: Requires SSH server and websocket proxy | High: Requires VPN client and server configuration | Low: Simple setup with web browsers |
| Cost | Free: Uses open-source software | Varies: Commercial VPNs can be expensive | Free: Can be used with free HTTP proxy servers |
Use Cases for SSH Tunnel Websocket
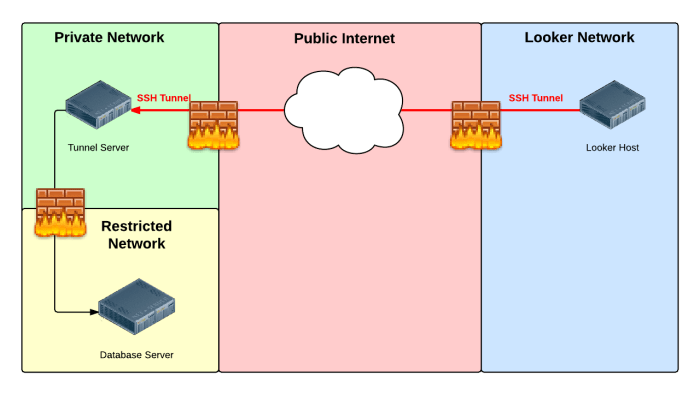
SSH tunneling over websockets finds practical applications in various industries and scenarios, offering secure and efficient remote access to resources.
Remote Desktop Access
SSH tunneling allows users to securely access remote desktops over the internet, enabling remote work, technical support, and administration tasks. This is particularly useful for accessing systems that are not directly accessible through public networks.
Secure File Transfer
SSH tunneling provides a secure channel for file transfer, protecting sensitive data from interception. It is commonly used for transferring files between remote servers or between a remote server and a local machine.
Database Access
SSH tunneling enables secure access to databases located on remote servers, allowing developers and administrators to manage and query data remotely. This ensures data confidentiality and integrity during transmission.
Web Application Testing
SSH tunneling can be used to test web applications by simulating different network conditions and access patterns. It allows testers to access the application from various locations and configurations, helping identify potential vulnerabilities.
Network Monitoring
SSH tunneling can be used to monitor network traffic and identify security threats. By establishing a secure tunnel to a remote network device, administrators can monitor traffic patterns, detect anomalies, and respond to potential attacks.
Future Trends in SSH Tunnel Websocket
The future of SSH tunnel websocket holds immense promise, with advancements in technology and emerging applications driving its evolution. Here are some key trends to watch out for:
Enhanced Security
SSH tunneling over websockets is continuously evolving to enhance security measures. The adoption of modern encryption algorithms, such as AES-256 and ChaCha20, ensures the confidentiality and integrity of data transmitted over the tunnel. Additionally, the use of multi-factor authentication adds an extra layer of protection against unauthorized access.
Increased Scalability
As the demand for remote access and data transfer grows, SSH tunnel websockets are being optimized for scalability. The implementation of load balancing techniques and the adoption of cloud-based infrastructure enable seamless handling of multiple concurrent connections, ensuring high availability and performance.
Integration with Cloud Services
The integration of SSH tunnel websockets with cloud services is gaining traction. By leveraging cloud platforms, organizations can easily establish secure connections to their cloud-based resources, such as virtual machines, databases, and storage services. This integration simplifies remote access and streamlines cloud management tasks.
Expanded Use Cases
The versatility of SSH tunnel websockets is expanding, leading to its adoption in various domains. In the healthcare sector, it enables secure access to patient data, while in the financial industry, it facilitates secure transactions and compliance with regulatory requirements.
Additionally, SSH tunnel websockets are being used for remote debugging, DevOps automation, and secure access to legacy systems.
Improved User Experience
User experience is a key focus in the development of SSH tunnel websockets. The introduction of user-friendly interfaces and simplified configuration processes makes it easier for users to establish and manage secure connections. Additionally, the integration of automation tools and support for multiple platforms enhances the overall user experience.
Conclusion
In conclusion, SSH tunneling over websockets provides a secure and versatile method for establishing encrypted connections between remote systems. It offers several advantages, including increased security, enhanced privacy, and improved network performance. By leveraging the capabilities of both SSH and websockets, this technique has emerged as a valuable tool for various applications, such as remote desktop access, web scraping, and secure data transfer.As
technology continues to evolve, SSH tunneling over websockets is expected to play an even more significant role in the future. The increasing adoption of cloud computing and the growing need for secure remote access will drive the demand for this technology.
Additionally, advancements in encryption algorithms and websocket protocols will further enhance the security and efficiency of SSH tunneling. By embracing these advancements, organizations and individuals can reap the benefits of this powerful technique to establish secure and reliable connections in a rapidly evolving digital landscape.