SSH.SSHSlowdns.com – In the realm of secure remote access, SSH stands as a beacon of reliability and versatility. Utilizing both TCP and UDP protocols, SSH enables seamless communication and data transfer across networks. This guide delves into the intricacies of SSH, empowering you to harness its capabilities for secure and efficient remote connections.
From understanding the nuances of SSH versions and authentication methods to mastering key management, tunneling, and port forwarding techniques, this comprehensive resource provides a thorough understanding of SSH’s multifaceted functionality. Dive into the depths of SSH configuration, explore potential security considerations, and uncover troubleshooting strategies to ensure seamless remote access.
SSH Protocol Versions
SSH (Secure Shell) is a network protocol that allows for secure remote access and command execution over an unsecured network. There are two main versions of the SSH protocol: SSHv1 and SSHv2.SSHv1 was released in 1995 and is now considered insecure due to several known vulnerabilities.
SSHv2 was released in 2006 and is the current recommended version of the SSH protocol. SSHv2 includes a number of security improvements over SSHv1, including:
- Stronger encryption algorithms
- Improved authentication methods
- Better session management
Security Implications of Using Outdated SSH Versions
Using an outdated version of SSH can have serious security implications. Outdated versions of SSH may be vulnerable to attacks that allow attackers to gain unauthorized access to your system. For example, the Heartbleed bug, which was discovered in 2014, allowed attackers to steal sensitive information from servers that were running outdated versions of OpenSSL.It
is important to keep your SSH server up to date with the latest security patches. This will help to protect your system from attacks that exploit vulnerabilities in outdated versions of SSH.
SSH Authentication Methods
SSH provides various authentication methods, allowing users to connect securely to remote systems. These methods include:
- Password Authentication: The most basic method, where users provide their username and password to access the system.
- Public Key Authentication: A more secure method that uses a pair of public and private keys. The public key is stored on the remote system, while the private key is kept secret on the client system.
- Kerberos Authentication: A network authentication protocol that allows users to access services on a network without having to enter their password multiple times.
- Certificate Authentication: Similar to public key authentication, but uses certificates issued by a trusted certificate authority (CA) to verify the user’s identity.
Example: Using Public Key Authentication To use public key authentication, you first need to generate a public and private key pair on your local system using the ssh-keygen command. Once generated, copy the public key to the remote system using the ssh-copy-id command.
When you connect to the remote system, SSH will automatically use the public key to authenticate your identity.
SSH Key Management
SSH keys are cryptographic key pairs used for secure authentication and data encryption in SSH connections. They provide an alternative to password-based authentication, enhancing security and convenience.
Generating an SSH key pair involves using a key generation tool like ssh-keygen. It creates a public key and a private key. The public key is shared with the remote server, while the private key is kept secret on the client machine.
Best Practices for SSH Key Security
To ensure the security of SSH keys, it’s crucial to follow best practices:
- Strong Passphrases: Use strong passphrases to protect private keys. Avoid using common words or phrases that can be easily guessed.
- Regular Key Rotation: Regularly generate new key pairs to prevent compromise. This mitigates the risk of key theft or exposure.
- Restrict Access to Private Keys: Limit access to private keys to authorized users only. Use file permissions and secure storage mechanisms to prevent unauthorized access.
- Monitor Key Usage: Monitor SSH key usage to detect any suspicious activity. Use tools like log analysis or intrusion detection systems to identify unauthorized access attempts.
- Use Key Management Tools: Utilize key management tools to simplify key generation, storage, and rotation. These tools can help ensure key security and compliance with best practices.
SSH Tunneling
SSH tunneling is a technique that allows you to create a secure, encrypted connection between two remote hosts over an insecure network. It works by using the SSH protocol to establish a secure channel between the two hosts, and then tunneling other traffic through that channel.
This allows you to securely access services on the remote host, even if the network between you and the host is not secure.There are many different ways to use SSH tunneling. Some common examples include:*
-*Securely accessing a web server
You can use SSH tunneling to securely access a web server on a remote host, even if the web server is not configured to use HTTPS. This is useful if you need to access a web server that is behind a firewall, or if you want to protect your traffic from eavesdropping.
-
- -*Securely accessing a database server
You can use SSH tunneling to securely access a database server on a remote host, even if the database server is not configured to use SSL. This is useful if you need to access a database server that is behind a firewall, or if you want to protect your traffic from eavesdropping.
- -*Securely accessing a database server
-*Securely accessing a file server
You can use SSH tunneling to securely access a file server on a remote host, even if the file server is not configured to use SFTP. This is useful if you need to access a file server that is behind a firewall, or if you want to protect your traffic from eavesdropping.
SSH tunneling is a powerful tool that can be used to securely access a wide variety of services on remote hosts. It is a simple and easy-to-use technique that can help you to protect your traffic from eavesdropping and other security threats.
Creating an SSH Tunnel
To create an SSH tunnel, you will need to use an SSH client. There are many different SSH clients available, including PuTTY, OpenSSH, and SSH.exe.Once you have an SSH client, you can follow these steps to create an SSH tunnel:
- Open the SSH client and connect to the remote host.
- Once you are connected to the remote host, you can use the following command to create an SSH tunnel:
“`ssh
-L local_port
remote_host:remote_port user@remote_host“`where:* `local_port` is the port number that you want to use on your local computer to access the remote service.
- `remote_host` is the hostname or IP address of the remote host.
- `remote_port` is the port number of the service that you want to access on the remote host.
- `user` is the username that you want to use to log in to the remote host.
For example, the following command would create an SSH tunnel that allows you to access a web server on the remote host at port 8080:“`ssh
-L 8080
remote_host:80 user@remote_host“`Once you have created an SSH tunnel, you can use it to access the remote service by connecting to the local port that you specified in the `-L` option. For example, if you created an SSH tunnel to access a web server on port 8080, you could connect to the web server by visiting the following URL in your web browser:“`http://localhost:8080“`SSH tunneling is a powerful tool that can be used to securely access a wide variety of services on remote hosts.
It is a simple and easy-to-use technique that can help you to protect your traffic from eavesdropping and other security threats.
SSH Port Forwarding
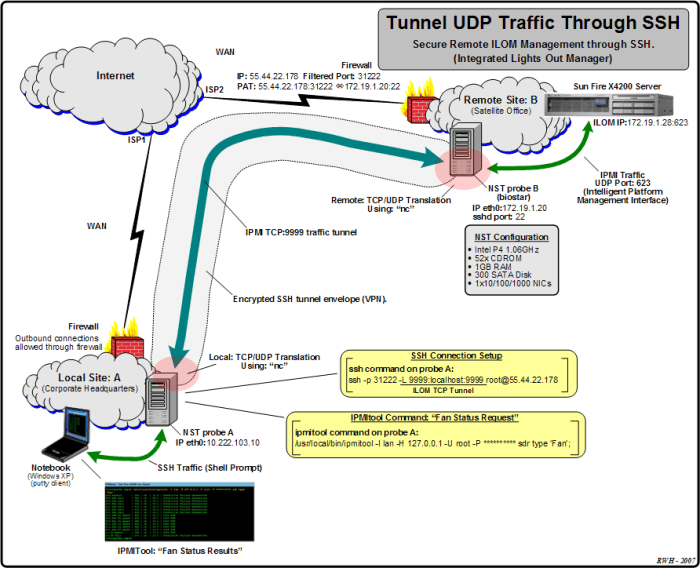
SSH port forwarding is a technique that allows you to create a secure tunnel between two computers over an insecure network. This can be used to access services that are normally not accessible from the outside world, such as web servers, email servers, and databases.There
are two types of SSH port forwarding: local and remote. Local port forwarding creates a tunnel from a port on your local computer to a port on the remote computer. Remote port forwarding creates a tunnel from a port on the remote computer to a port on your local computer.Local
port forwarding is typically used to access services that are running on the remote computer. For example, you could use local port forwarding to access a web server that is running on the remote computer from your local computer.Remote port forwarding is typically used to access services that are running on your local computer from the remote computer.
For example, you could use remote port forwarding to access a database that is running on your local computer from the remote computer.SSH port forwarding is a powerful tool that can be used to securely access services that are normally not accessible from the outside world.
SSH Configuration
SSH configuration allows you to customize the behavior of the SSH server and client. The configuration file is typically located at /etc/ssh/sshd_config on the server and ~/.ssh/config on the client.
There are many different SSH configuration options available, including:
- Port: The port number that the SSH server listens on. The default port is 22.
- ListenAddress: The IP address that the SSH server listens on. The default is to listen on all IP addresses.
- Protocol: The SSH protocol version to use. The default is 2.
- HostKey: The path to the SSH host key file. The default is to generate a new key on startup.
- PermitRootLogin: Whether or not to allow root logins. The default is to disable root logins.
- PasswordAuthentication: Whether or not to allow password authentication. The default is to disable password authentication.
- ChallengeResponseAuthentication: Whether or not to allow challenge-response authentication. The default is to disable challenge-response authentication.
- GSSAPIAuthentication: Whether or not to allow GSSAPI authentication. The default is to disable GSSAPI authentication.
- PermitEmptyPasswords: Whether or not to allow empty passwords. The default is to disable empty passwords.
- PermitUserEnvironment: Whether or not to allow users to set environment variables. The default is to disable user environment variables.
- X11Forwarding: Whether or not to allow X11 forwarding. The default is to disable X11 forwarding.
- Compression: Whether or not to use compression. The default is to enable compression.
- LogLevel: The level of logging to use. The default is to use the INFO level.
Here are some examples of how to configure SSH for different purposes:
Disable Password Authentication
To disable password authentication, set the PasswordAuthentication option to no in the SSH configuration file.
PasswordAuthentication no
Enable Key-Based Authentication
To enable key-based authentication, generate an SSH key pair and add the public key to the authorized_keys file on the server.
ssh-keygen
t rsa
cat ~/.ssh/id_rsa.pub >> ~/.ssh/authorized_keys
Enable Port Forwarding
To enable port forwarding, set the GatewayPorts option to yes in the SSH configuration file.
GatewayPorts yes
SSH Security Considerations
SSH, while secure, is not immune to potential security risks. Understanding these risks and implementing appropriate mitigation strategies is crucial for maintaining the security of SSH connections.
One significant risk is unauthorized access to SSH servers. Attackers may attempt to exploit vulnerabilities in SSH implementations or use brute-force attacks to guess weak passwords. To mitigate this risk, it is essential to use strong passwords, enable two-factor authentication, and regularly patch SSH servers to address any known vulnerabilities.
Vulnerability Assessment and Penetration Testing
Conducting regular vulnerability assessments and penetration testing helps identify potential weaknesses in SSH configurations and implementations. These tests simulate real-world attacks to uncover exploitable vulnerabilities that could be leveraged by malicious actors.
SSH Troubleshooting
SSH troubleshooting involves identifying common problems and applying appropriate solutions. It requires understanding the underlying issues and following systematic steps to resolve them.
Common SSH problems include connection failures, authentication errors, and permission issues. Connection failures can result from incorrect IP addresses, port numbers, or firewall restrictions. Authentication errors occur due to invalid credentials, disabled accounts, or incorrect key configurations. Permission issues arise when users lack the necessary privileges to access resources.
Troubleshooting Steps
- Verify Network Connectivity: Check if the SSH server is reachable using tools like ping or traceroute. Ensure that the firewall is not blocking SSH traffic.
- Confirm Credentials: Verify the username and password or SSH key used for authentication. Ensure that the account is active and has the appropriate permissions.
- Check SSH Configuration: Review the SSH configuration files (e.g., /etc/ssh/sshd_config) to ensure that the settings are correct, such as the port number and authentication methods.
- Examine SSH Logs: Check the SSH server logs (e.g., /var/log/auth.log) for error messages that can provide insights into the issue.
- Use SSH Debugging: Enable SSH debugging using the
- v or
- vv options to capture detailed information about the SSH connection process.
- Contact System Administrator: If the issue persists, contact the system administrator for assistance with advanced troubleshooting.
SSH Best Practices
To ensure the secure and efficient use of SSH, it is essential to adhere to established best practices. These guidelines provide a framework for configuring, managing, and utilizing SSH to mitigate potential risks and optimize performance.
Implementing these best practices involves a combination of technical measures and administrative controls. By following these recommendations, organizations and individuals can significantly enhance the security and effectiveness of their SSH deployments.
Key Management
- Use strong passphrases: Create complex and unique passphrases for SSH keys to prevent unauthorized access.
- Store keys securely: Keep private keys confidential and protected from unauthorized disclosure or theft.
- Rotate keys regularly: Periodically generate new SSH key pairs to reduce the risk of compromise.
- Revoke compromised keys: Immediately invalidate any SSH keys suspected of being compromised.
Configuration
- Disable unused services: Turn off unnecessary SSH services, such as password authentication, to reduce attack surface.
- Limit access: Restrict SSH access to authorized users and IP addresses using firewall rules and host-based access controls.
- Use strong encryption algorithms: Configure SSH to use robust encryption algorithms, such as AES-256-CBC, to protect data in transit.
- Enable logging and monitoring: Set up logging and monitoring systems to detect and respond to suspicious SSH activity.
Security Considerations
- Be aware of social engineering attacks: Exercise caution when receiving unsolicited SSH login requests or suspicious emails.
- Use two-factor authentication: Implement two-factor authentication mechanisms to add an extra layer of security.
- Patch regularly: Keep SSH software up to date with the latest security patches to address vulnerabilities.
- Educate users: Train users on SSH security best practices and potential risks to enhance overall awareness and vigilance.
SSH Tools
SSH provides a secure and efficient way to manage remote systems. Several tools are available to enhance the functionality and usability of SSH.
Popular SSH tools include: