In the realm of secure remote access, SSH (Secure Shell) stands as a cornerstone technology, facilitating encrypted communication over insecure networks. At its core, SSH leverages two primary transport protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). Understanding the distinctions between these protocols is crucial for optimizing SSH performance and security.
This comprehensive guide delves into the intricacies of SSH over TCP and UDP, exploring their unique characteristics, advantages, and use cases. We will delve into the technical nuances, providing practical examples and insights to empower you with a deep understanding of this essential technology.
SSH Protocol Versions
SSH, short for Secure Shell, is a cryptographic network protocol that provides secure communication over insecure networks. SSH is widely used for remote login and secure file transfer.
There are two major versions of the SSH protocol: SSHv1 and SSHv2. SSHv2 is the more recent and secure version, and it is recommended to use SSHv2 whenever possible.
Differences between SSHv1 and SSHv2
- SSHv2 uses a stronger encryption algorithm than SSHv1, making it more difficult to break.
- SSHv2 supports a wider range of authentication methods than SSHv1, making it more flexible and secure.
- SSHv2 includes a number of security improvements over SSHv1, such as support for message authentication codes (MACs) and public-key cryptography.
Examples of SSH clients and servers that support both versions
- OpenSSH
- PuTTY
- WinSCP
SSH Authentication Methods
SSH supports a range of authentication methods, providing flexibility and security in establishing remote connections. These methods include password-based authentication, public-key authentication, and Kerberos authentication.
Public-Key Authentication
Public-key authentication is a widely used method that enhances security by utilizing a pair of cryptographic keys, a public key and a private key. The public key is shared with the remote server, while the private key remains securely stored on the client machine.
During the authentication process, the server sends a challenge to the client, which is encrypted using the public key. The client then decrypts the challenge using its private key, demonstrating possession of the private key and proving its identity to the server.
To set up SSH key-based authentication, follow these steps:
- Generate an SSH key pair on the client machine using the “ssh-keygen” command.
- Copy the public key to the remote server using the “ssh-copy-id” command.
- Configure the server to accept public-key authentication by modifying the “/etc/ssh/sshd_config” file.
- Restart the SSH service on the server to apply the changes.
SSH Tunneling
SSH tunneling is a technique that allows you to create a secure, encrypted connection between two remote computers over an untrusted network, such as the Internet. It works by encapsulating data within an SSH connection, making it appear as if the data is originating from the SSH server rather than the client.
There are two main types of SSH tunnels: local and remote. Local tunnels allow you to access a remote computer as if it were a local resource. Remote tunnels allow you to access a local resource from a remote computer.
Local Tunnels
Local tunnels are created using the -L option of the ssh command. The following command creates a local tunnel from port 8080 on the local computer to port 80 on the remote computer:
“`ssh
-L 8080
remote_host:80 user@remote_host“`
Once the tunnel is created, you can access the remote computer’s web server by pointing your browser to http://localhost:8080.
Remote Tunnels
Remote tunnels are created using the -R option of the ssh command. The following command creates a remote tunnel from port 80 on the remote computer to port 8080 on the local computer:
“`ssh
-R 80
localhost:8080 user@remote_host“`
Once the tunnel is created, you can access the local computer’s web server by pointing your browser to http://remote_host:80.
Benefits of SSH Tunneling
SSH tunneling offers a number of benefits, including:
- Secure remote access: SSH tunneling provides a secure way to access remote computers and resources over untrusted networks.
- Port forwarding: SSH tunneling can be used to forward ports between different computers, allowing you to access resources that would otherwise be inaccessible.
- Anonymity: SSH tunneling can be used to hide your IP address and location, making it more difficult for others to track your online activity.
SSH Port Forwarding
SSH port forwarding allows you to create a secure tunnel between two computers over an insecure network. This can be useful for accessing remote services that are not normally accessible from the internet, or for securely transferring files between two computers.There
are two types of SSH port forwarding: local and remote.
Local Port Forwarding
Local port forwarding creates a tunnel from a port on the local computer to a port on the remote computer. This allows you to access the remote port as if it were a local port.For example, if you have a web server running on port 80 on a remote computer, you can use local port forwarding to access the web server on port 8080 on your local computer.
To do this, you would use the following command:“`ssh
-L 8080
remote_host:80 user@remote_host“`This command will create a tunnel from port 8080 on your local computer to port 80 on the remote computer. You can then access the web server by pointing your browser to http://localhost:8080.
Remote Port Forwarding
Remote port forwarding creates a tunnel from a port on the remote computer to a port on the local computer. This allows you to access the local port as if it were a remote port.For example, if you have a database server running on port 3306 on your local computer, you can use remote port forwarding to access the database server on port 3307 on the remote computer.
To do this, you would use the following command:“`ssh
-R 3307
localhost:3306 user@remote_host“`This command will create a tunnel from port 3307 on the remote computer to port 3306 on your local computer. You can then access the database server by connecting to port 3307 on the remote computer.
SSH Port Forwarding for Network Troubleshooting
SSH port forwarding can be used to troubleshoot network problems. For example, if you are unable to access a remote service, you can use SSH port forwarding to create a tunnel to the service and test if the problem is with the network or with the service itself.To
use SSH port forwarding for network troubleshooting, you can use the following steps:
- Connect to the remote computer using SSH.
- Create a tunnel to the service you want to troubleshoot.
- Test if you can access the service through the tunnel.
- If you can access the service through the tunnel, then the problem is with the network.
- If you cannot access the service through the tunnel, then the problem is with the service itself.
SSH Configuration
SSH configuration involves modifying SSH server and client settings to enhance security, performance, and functionality. It allows customization of various parameters, including authentication methods, encryption algorithms, port forwarding options, and logging levels.
SSH Configuration Options
SSH configuration is typically managed through the SSH configuration file, often named ‘sshd_config’ on servers and ‘.ssh/config’ on clients. This file contains directives that control various aspects of SSH behavior, such as:
Authentication
Setting authentication methods, such as password, public key, or multi-factor authentication.
Encryption
Configuring encryption algorithms for data protection, including ciphers and key exchange methods.
Port Forwarding
Enabling and configuring port forwarding, which allows remote access to services running on the server.
Logging
Specifying the level of logging for SSH events, such as authentication attempts and session activity.
Connection Limits
Controlling the maximum number of concurrent SSH connections and the rate of connection attempts.
Security Settings
Implementing security measures, such as disabling weak encryption algorithms, limiting access to specific users, and setting up intrusion detection systems.
Configuring SSH for Security and Performance
To configure SSH for optimal security and performance, consider the following guidelines:
-
- -*Use Strong Encryption Algorithms
Choose robust encryption algorithms, such as AES-256-CTR or ChaCha20-Poly1305, for data protection.
- -*Use Strong Encryption Algorithms
-*Enable Two-Factor Authentication
Implement two-factor authentication to enhance security by requiring additional verification, such as a one-time password or hardware token.
-*Limit SSH Access
Restrict SSH access to specific users and IP addresses to prevent unauthorized connections.
-*Disable Unused Authentication Methods
Disable weak or insecure authentication methods, such as password-based authentication, if not necessary.
-*Enable Intrusion Detection
Implement intrusion detection systems to monitor SSH activity for suspicious behavior and respond accordingly.
-*Optimize Network Settings
Adjust network settings, such as TCP keepalives and packet size, to improve SSH performance over different network conditions.
Common SSH Configuration Settings
Some common SSH configuration settings include:
-
- -*Port
Specifies the TCP port on which SSH listens for connections (default: 22).
- -*Port
-*Protocol
Sets the SSH protocol version to use (default: 2).
-*Ciphers
Lists the encryption algorithms to use for data protection.
-*MACs
Specifies the message authentication codes to use for data integrity.
-*KexAlgorithms
Configures the key exchange algorithms to use for session establishment.
-*HostKey
Specifies the path to the host key file, which is used for server authentication.
-*LogLevel
Sets the logging level for SSH events (default: INFO).
SSH Security Best Practices
Securing SSH connections is crucial for protecting sensitive data and systems. Here are some best practices to enhance SSH security:
Strong Passwords and Encryption
Use strong, complex passwords with a combination of uppercase, lowercase, numbers, and special characters. Additionally, enable strong encryption algorithms like AES-256-CBC or ChaCha20-Poly1305 for secure data transmission.
Harden SSH Servers
Harden SSH servers by disabling unused services, such as password authentication and X11 forwarding. Configure firewall rules to restrict access to the SSH port only from trusted IP addresses. Enable key-based authentication and disable root login.
Monitor SSH Activity
Monitor SSH activity regularly for suspicious behavior, such as failed login attempts, brute-force attacks, or unauthorized access. Use tools like fail2ban to automatically ban IP addresses after a certain number of failed login attempts.
Use SSH Keys
Generate SSH keys for strong authentication. SSH keys are more secure than passwords as they are not stored on the server and require a passphrase for decryption.
Disable Port Scanning
Disable port scanning on SSH servers to prevent attackers from discovering open ports. Configure firewall rules to block access to unused ports.
Use SSH Tunneling
Use SSH tunneling to securely access remote services over an encrypted connection. This prevents data from being intercepted by unauthorized parties.
Use SSH Port Forwarding
Use SSH port forwarding to forward traffic from one port to another, allowing access to services behind firewalls. This can be useful for accessing internal services from outside networks.
Configure SSH Configuration
Configure SSH settings to enhance security, such as setting a maximum number of failed login attempts, enabling TCPKeepAlive, and disabling SSH root login.
SSH over TCP and UDP
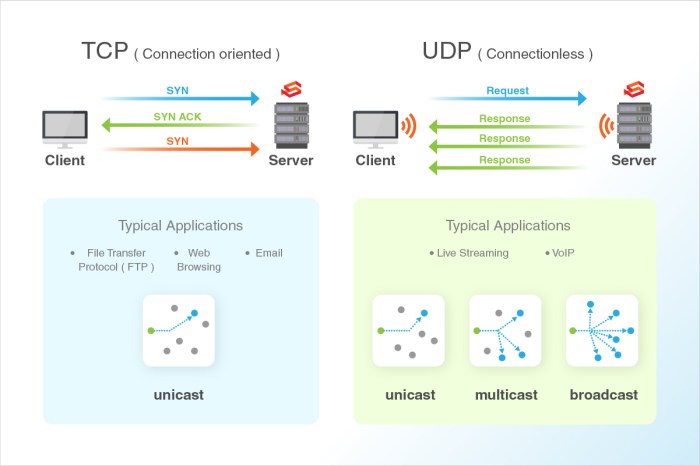
SSH (Secure Shell) is a network protocol that provides secure remote access to a computer. It can be used over both TCP and UDP.
TCP (Transmission Control Protocol) is a reliable, connection-oriented protocol. This means that it establishes a connection between the client and server before any data is transmitted. TCP also provides error checking and retransmission, which ensures that data is delivered reliably.
UDP (User Datagram Protocol) is a connectionless, unreliable protocol. This means that it does not establish a connection between the client and server before any data is transmitted. UDP also does not provide error checking or retransmission, which means that data may be lost or corrupted in transit.
Advantages and Disadvantages of SSH over TCP and UDP
SSH over TCP is more reliable than SSH over UDP, but it is also slower. SSH over UDP is faster than SSH over TCP, but it is less reliable.
Here is a table that summarizes the advantages and disadvantages of SSH over TCP and UDP:
| Protocol | Advantages | Disadvantages |
|---|---|---|
| TCP | Reliable | Slow |
| UDP | Fast | Unreliable |
When to Use SSH over TCP or UDP
SSH over TCP should be used when reliability is more important than speed. SSH over UDP should be used when speed is more important than reliability.
Here are some examples of when to use SSH over TCP or UDP:
- SSH over TCP should be used for remote administration tasks, such as managing files and running commands.
- SSH over UDP should be used for applications that require real-time data, such as video conferencing and online gaming.
SSH Tools
SSH provides a versatile set of tools for managing and troubleshooting remote systems.
SSH tools enable users to perform various tasks, including file transfer, command execution, and port forwarding.
Common SSH Tools
- ssh: Establishes an SSH connection to a remote host.
- scp: Securely copies files between local and remote hosts.
- sftp: Provides an interactive file transfer interface over SSH.
- ssh-keygen: Generates SSH key pairs for authentication.
- ssh-copy-id: Copies an SSH public key to a remote host for passwordless login.
These tools provide a powerful suite for remote system administration and troubleshooting.
SSH in the Cloud
SSH plays a crucial role in cloud computing, enabling secure management and access to cloud resources. It provides a secure channel for remote administration, file transfers, and other operations.
Using SSH in the cloud offers several benefits:
- Secure access: SSH establishes an encrypted connection, ensuring that data transmitted between the client and cloud resources remains confidential.
- Remote management: SSH allows administrators to manage cloud resources remotely, even when physical access is not feasible.
- File transfer: SSH supports secure file transfers between the client and cloud resources, facilitating data exchange.
Examples of SSH Use in the Cloud
Here are some common use cases of SSH in the cloud:
- Managing virtual machines: SSH is used to access and manage virtual machines (VMs) in the cloud, enabling administrators to perform tasks such as starting, stopping, and configuring VMs.
- Accessing cloud storage: SSH can be used to securely access and manage cloud storage services, allowing users to upload, download, and manage files.
- Troubleshooting: SSH provides a secure channel for troubleshooting issues with cloud resources, enabling administrators to diagnose and resolve problems remotely.
SSH Future Developments
SSH is constantly evolving to meet the changing needs of the IT industry. The latest versions of SSH include new features and enhancements that improve security, performance, and usability.
One of the most significant developments in SSH is the adoption of quantum-resistant cryptography. Quantum computers have the potential to break many of the encryption algorithms that are currently used to secure SSH connections. Quantum-resistant cryptography is a new type of cryptography that is designed to be resistant to attack by quantum computers.
Another major development in SSH is the introduction of support for multi-factor authentication. Multi-factor authentication requires users to provide multiple forms of identification before they can access a SSH server. This makes it much more difficult for attackers to gain unauthorized access to SSH servers.
In addition to these major developments, SSH is also being updated with a number of new features and enhancements that improve performance and usability. These include support for new ciphers and key exchange algorithms, as well as improvements to the SSH protocol itself.
Upcoming SSH Standards and Features
The SSH community is currently working on a number of new standards and features for SSH. These include:
- SSHv3: A new version of the SSH protocol that includes a number of new features and improvements.
- Quantum-resistant cryptography: Support for quantum-resistant cryptography algorithms.
- Multi-factor authentication: Support for multi-factor authentication methods.
- Improved performance: A number of improvements to the SSH protocol that improve performance.
- Improved usability: A number of improvements to the SSH protocol that improve usability.
Examples of How SSH Is Evolving to Meet Future Needs
SSH is evolving to meet the changing needs of the IT industry in a number of ways. These include:
- Support for new technologies: SSH is being updated to support new technologies, such as quantum-resistant cryptography and multi-factor authentication.
- Improved performance: SSH is being updated to improve performance, making it more efficient to use.
- Improved usability: SSH is being updated to improve usability, making it easier to use for both administrators and users.
SSH is a critical tool for IT professionals. It is used to manage servers, transfer files, and access remote systems. As the IT industry continues to evolve, SSH will continue to evolve to meet the changing needs of the industry.
Summary
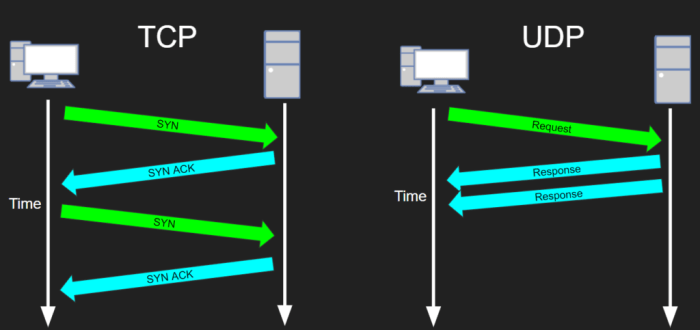
In conclusion, the choice between SSH over TCP or UDP hinges on the specific requirements of your application. TCP offers reliable, ordered delivery, making it ideal for interactive sessions and file transfers. UDP, on the other hand, prioritizes speed and efficiency, excelling in applications where latency is critical.
By comprehending the strengths and limitations of each protocol, you can harness the full potential of SSH for secure and efficient remote connectivity.