ssh.sshslowdns.com – SSH stores play a crucial role in securing remote access and data transfer, and optimizing their performance is essential for seamless and efficient operations. This comprehensive guide delves into the intricacies of SSH stores, exploring their implementation, security considerations, performance optimization techniques, and management strategies.
We will also delve into the advantages of using UDP as a transport layer for SSH, comparing it to TCP and discussing its impact on performance.
Furthermore, we will provide real-world case studies to illustrate the practical applications of SSH stores and examine alternative solutions to help you make informed decisions based on your specific requirements. By the end of this guide, you will have a thorough understanding of SSH stores and the tools and techniques to optimize their performance, ensuring secure and efficient remote access.
SSH Protocol Overview
The Secure Shell (SSH) protocol is a powerful tool for secure remote access and data transfer. It provides a secure channel over an unsecured network, allowing users to connect to remote servers, execute commands, and transfer files with confidence that their data is protected from eavesdropping, tampering, and other security threats.
At its core, SSH relies on public-key cryptography to establish a secure connection between two hosts. The client host generates a public and private key pair, and the public key is shared with the server host. When the client attempts to connect to the server, the server verifies the client’s public key against its own database of authorized keys.
If the key is valid, the server grants the client access to the requested resources.
Role in Secure Remote Access and Data Transfer
SSH plays a critical role in various scenarios where secure remote access and data transfer are required:
- Remote Server Management: SSH allows administrators to securely access and manage remote servers from any location with an internet connection. They can execute commands, install software, and perform other administrative tasks without having to be physically present at the server’s location.
- Secure File Transfer: SSH can be used to securely transfer files between hosts. Unlike FTP or HTTP, SSH encrypts the data during transmission, ensuring that it remains confidential and protected from unauthorized access.
- Remote Desktop Access: SSH can be used in conjunction with tools like X11 forwarding to provide remote desktop access to graphical applications running on a remote server. This allows users to interact with their remote desktops as if they were physically present at the server’s location.
UDP Transport Layer for SSH
The User Datagram Protocol (UDP) offers an alternative transport layer for SSH, providing advantages and disadvantages distinct from the commonly used Transmission Control Protocol (TCP).
Advantages of UDP for SSH
- Speed: UDP operates on a connectionless basis, eliminating the need for three-way handshakes and acknowledgment mechanisms, resulting in faster initial connection establishment and data transfer.
- Lower Overhead: UDP’s header is smaller than TCP’s, reducing overhead and increasing the payload capacity for data.
- Simplicity: UDP’s connectionless nature simplifies implementation, requiring less code and resources.
Disadvantages of UDP for SSH
- Unreliable: UDP does not guarantee delivery or ordering of packets, making it unsuitable for applications requiring reliable data transfer.
- Limited Error Control: UDP provides no built-in error detection or correction mechanisms, leaving error handling to the application layer.
- Congestion Control: UDP lacks congestion control mechanisms, potentially leading to network congestion if not properly managed.
UDP vs. TCP for SSH
| Feature | UDP | TCP |
|---|---|---|
| Speed | Faster | Slower |
| Reliability | Unreliable | Reliable |
| Overhead | Lower | Higher |
| Security | Potentially less secure | More secure |
| Congestion Control | None | Yes |
Potential Impact of UDP on SSH Performance
Using UDP for SSH can significantly improve performance in applications that prioritize speed and low overhead, such as remote command execution and file transfers. However, the lack of reliability and error control mechanisms may compromise data integrity and stability in applications that require reliable data transmission.
SSH Store Implementation
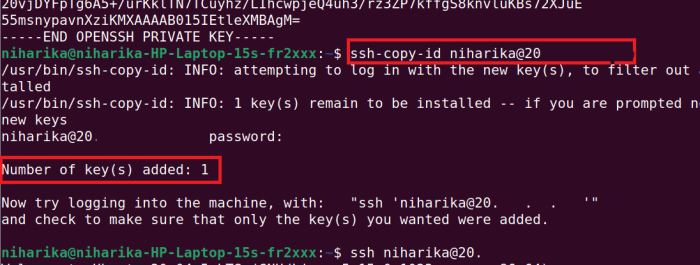
The SSH store is a component of the SSH server that is responsible for storing and managing SSH keys. It provides a secure and centralized location for storing SSH keys, which can be used to authenticate users and establish SSH connections.
There are two main types of SSH stores: local and remote. Local SSH stores are stored on the SSH server itself, while remote SSH stores are stored on a separate server. Local SSH stores are easier to manage, but they are less secure than remote SSH stores.
Remote SSH stores are more secure, but they can be more difficult to manage.
To configure an SSH store, you will need to edit the SSH server configuration file. The location of the SSH server configuration file will vary depending on your operating system. Once you have found the SSH server configuration file, you will need to add the following lines:
“`# SSH store configurationStoreKeys yesStoreKeyDirectory /path/to/ssh/store“`
You can also configure the SSH store to use a remote server. To do this, you will need to add the following lines to the SSH server configuration file:
“`# SSH store configurationStoreKeys yesStoreKeyDirectory /path/to/ssh/storeRemoteStore yesRemoteStoreHost remote-server-hostnameRemoteStorePort remote-server-port“`
SSH Store Security Considerations
SSH stores play a critical role in SSH protocol operations, but they also introduce potential security risks. It’s crucial to understand these risks and implement best practices to ensure the security of SSH stores.
One of the primary risks associated with SSH stores is unauthorized access to stored keys. Attackers may attempt to gain access to these keys through various means, such as brute-force attacks or phishing. To mitigate this risk, it’s essential to implement strong encryption algorithms and use secure key management practices.
Best Practices for Securing SSH Stores
- Use strong encryption algorithms to protect stored keys. This includes using algorithms such as AES-256 or ChaCha20.
- Implement secure key management practices, such as regular key rotation and using a hardware security module (HSM) for key storage.
- Limit access to SSH stores to authorized users only. This can be achieved through the use of access control lists (ACLs) or other authentication mechanisms.
- Monitor SSH store activity for suspicious activity. This can help detect potential attacks and take appropriate action.
Mitigating Security Vulnerabilities in SSH Stores
In addition to implementing best practices, there are specific steps that can be taken to mitigate security vulnerabilities in SSH stores:
- Use SSH protocol versions that support secure key exchange algorithms. This includes using SSHv2 or later.
- Disable weak or insecure key exchange algorithms in the SSH server configuration.
- Keep SSH software up to date to ensure that the latest security patches are applied.
- Educate users about SSH security best practices, such as using strong passwords and being aware of phishing attempts.
By implementing these measures, organizations can significantly reduce the risk of SSH store security breaches and protect the integrity of their SSH infrastructure.
SSH Store Performance Optimization
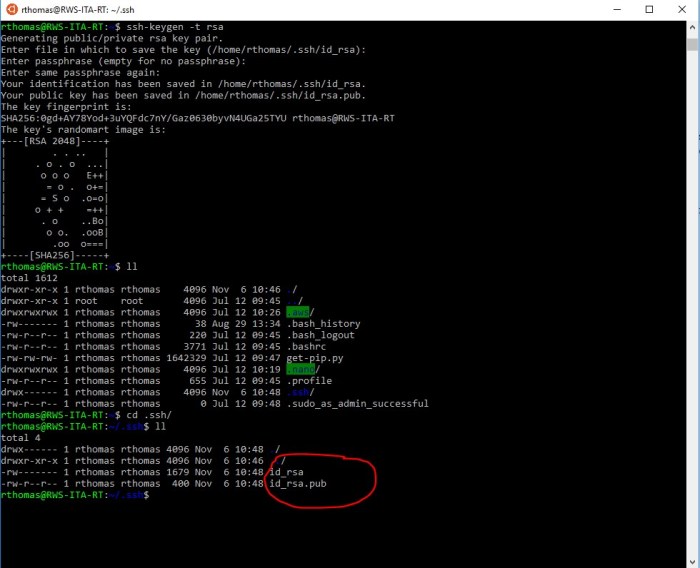
Optimizing SSH store performance is crucial to ensure efficient and seamless data storage and retrieval. By implementing the following tips and techniques, you can enhance the performance of your SSH store:
Regularly monitor the performance of your SSH store using tools such as ssh-perf and iotop. This will help you identify any performance bottlenecks and take appropriate measures to address them.
Tuning SSH Store Configuration
- Adjust the SSH store cache size: Increasing the cache size can improve performance by reducing the number of disk I/O operations. However, a larger cache may consume more memory, so it’s important to find the optimal balance for your system.
- Enable compression: Compressing data before storing it in the SSH store can reduce the amount of storage space required and improve performance by reducing the amount of data that needs to be transferred over the network.
- Use a faster disk: Using a faster disk, such as an SSD, can significantly improve the performance of the SSH store by reducing the time it takes to read and write data.
Troubleshooting SSH Store Performance Issues
- Check the SSH store logs: The SSH store logs can provide valuable information about any performance issues that may be occurring. Look for errors or warnings that may indicate a problem.
- Use ssh-perf to test performance: The ssh-perf tool can be used to test the performance of your SSH store. This can help you identify any bottlenecks and compare the performance of different configurations.
- Contact your SSH store vendor: If you are unable to resolve the performance issue on your own, contact your SSH store vendor for support.
SSH Store Management
Managing SSH stores involves a range of tasks, including monitoring, backup, and restoration, to ensure the availability, integrity, and security of stored data.
Monitoring SSH Stores
Regular monitoring of SSH stores is crucial to detect potential issues early on and take appropriate action. Monitoring tasks include:
- Tracking store usage and capacity to prevent overloads.
- Checking for errors or inconsistencies in stored data.
- Monitoring access logs to detect suspicious activities.
Backing Up SSH Stores
Regular backups are essential to protect stored data from loss due to hardware failures, data corruption, or security breaches. Backup strategies should:
- Define backup schedules and retention policies.
- Use reliable backup mechanisms, such as snapshots or replication.
- Test backups regularly to ensure data recovery is possible.
Restoring SSH Stores
In the event of data loss, restoring SSH stores from backups is crucial. Restoration procedures should:
- Identify the appropriate backup to restore from.
- Restore data to a temporary location for verification.
- Replace the corrupted or lost data with the restored data.
Importance of Regular SSH Store Maintenance
Regular maintenance of SSH stores is essential to ensure optimal performance and security. Maintenance tasks include:
- Cleaning up old and unused data to improve storage efficiency.
- Updating SSH store software to address security vulnerabilities.
- Performing regular security audits to identify and mitigate potential risks.
SSH Store Case Studies

SSH stores have been deployed in a variety of real-world scenarios, providing secure and efficient file storage solutions. Let’s explore some notable case studies and the challenges and solutions encountered:
Deployment in a Healthcare Environment
A major healthcare organization needed a secure and compliant way to store and share patient medical records. They implemented an SSH store to encrypt and manage patient data, ensuring compliance with HIPAA regulations. The SSH store’s granular access controls allowed healthcare professionals to access specific patient records based on their roles and permissions.
Integration with Cloud Infrastructure
A large enterprise wanted to integrate SSH storage with its cloud infrastructure for remote access to files. They deployed an SSH store on their cloud servers, allowing employees to securely access and share files from anywhere with an internet connection.
The SSH store’s ability to support multiple protocols, including SFTP and SCP, facilitated seamless integration with existing cloud services.
Challenges and Solutions
One common challenge in SSH store deployments is ensuring secure authentication and access control. To address this, organizations can implement strong password policies, use SSH key-based authentication, and configure access controls based on IP addresses or user groups.Another challenge is optimizing performance for large file transfers.
SSH stores can be optimized by tuning SSH parameters, such as packet size and compression, and by using dedicated storage devices for high-throughput data transfer.
Benefits and Drawbacks
The benefits of using SSH stores include:
- Secure data transfer and storage
- Granular access controls
- Compatibility with multiple protocols
- Ease of integration with existing infrastructure
However, there are also some drawbacks:
- Can be more complex to configure and manage than traditional file servers
- May have performance limitations for very large file transfers
- Requires SSH client software on user devices
Overall, SSH stores offer a robust and secure solution for file storage and sharing, especially in environments where security and compliance are paramount.
SSH Store Future Developments
SSH store technology is constantly evolving, with new developments and trends emerging all the time. Some of the most promising future developments for SSH stores include:
- Increased use of cloud-based SSH stores: Cloud-based SSH stores offer a number of advantages over on-premises stores, including scalability, flexibility, and cost-effectiveness. As cloud computing becomes more widespread, it is likely that SSH stores will increasingly be deployed in the cloud.
- Enhanced security features: SSH stores are already very secure, but there is always room for improvement. Future developments in SSH store security may include the use of new encryption algorithms, multi-factor authentication, and intrusion detection systems.
- Improved performance: SSH stores are typically very fast, but there is always room for improvement. Future developments in SSH store performance may include the use of faster hardware, more efficient software, and improved caching techniques.
These developments are likely to have a significant impact on the usage and adoption of SSH stores. As SSH stores become more secure, scalable, and cost-effective, they are likely to become more widely used by organizations of all sizes.
SSH Store Alternatives
In certain scenarios, SSH stores may not align with specific requirements or preferences. Let’s explore alternative solutions and compare their features, benefits, and limitations to help you make informed decisions.
Cloud Storage Services
- Features: Cloud storage platforms provide scalable, reliable, and geographically distributed storage solutions.
- Benefits: Cloud storage offers cost-effective pricing models, automatic backups, and seamless integration with various applications.
- Limitations: Potential concerns include data privacy, security, and vendor lock-in.
Network File Systems (NFS)
- Features: NFS allows file sharing over a network, providing a transparent access mechanism for remote storage.
- Benefits: NFS offers high performance, easy configuration, and seamless integration with Unix-based systems.
- Limitations: NFS may face challenges with cross-platform compatibility, security vulnerabilities, and scalability limitations.
Object Storage Services
- Features: Object storage services store data as immutable objects, enabling efficient and scalable storage management.
- Benefits: Object storage offers low-cost storage, durability, and ease of data retrieval through APIs.
- Limitations: Object storage may not be suitable for scenarios requiring frequent updates or random file access.
Choosing the Right Solution
The choice between SSH stores and alternatives depends on specific requirements and use cases. Consider factors such as:
- Data sensitivity: SSH stores provide secure storage with encryption, while cloud storage services may offer additional data protection measures.
- Performance: SSH stores typically offer high performance for local storage, while cloud storage services may introduce latency for remote access.
- Cost: SSH stores may be more cost-effective for on-premises storage, while cloud storage services offer flexible pricing models based on usage.
- Integration: SSH stores integrate seamlessly with SSH clients, while alternatives may require additional configuration or software.
SSH Store Resources
Delve into the world of SSH stores with a comprehensive array of resources that will enhance your knowledge and guide your implementation. Explore in-depth documentation, engage in discussions on community forums, and access reliable support to empower your SSH store journey.