In the realm of secure data storage and transmission, SSH Store UDP emerges as a formidable technology that seamlessly integrates the robust capabilities of SSH with the efficiency of UDP. SSH Store UDP has revolutionized the way businesses and individuals safeguard and share sensitive information, offering unparalleled security and performance.
With its cutting-edge encryption algorithms, SSH Store UDP establishes an impenetrable barrier against unauthorized access, ensuring that data remains confidential and intact throughout its journey. Its UDP-based architecture further optimizes data transfer, minimizing latency and maximizing speed, making it an ideal solution for real-time applications and large file transfers.
SSH Store UDP Overview
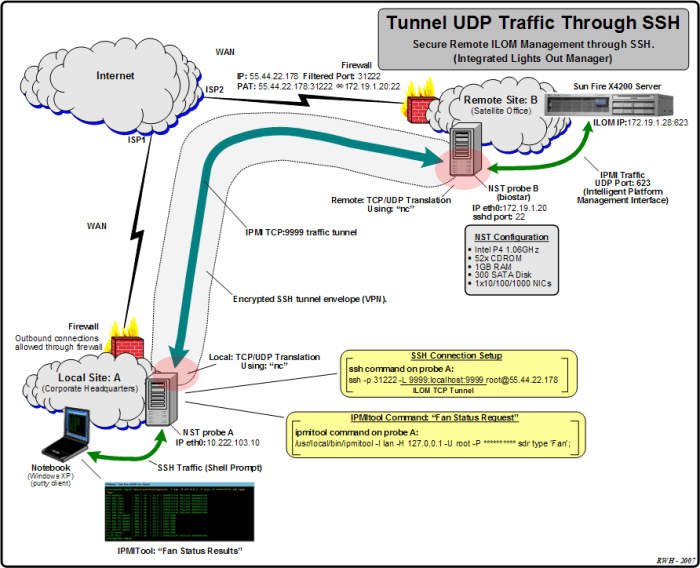
SSH Store UDP is a protocol that enables the secure transfer of data over UDP (User Datagram Protocol).
It combines the security features of SSH (Secure Shell) with the speed and efficiency of UDP, providing a reliable and secure way to transfer data between remote systems.
Benefits of SSH Store UDP
- Secure: SSH Store UDP uses strong encryption and authentication mechanisms to protect data from unauthorized access.
- Fast: UDP is a connectionless protocol, which makes it faster than TCP (Transmission Control Protocol) for transferring small amounts of data.
- Efficient: SSH Store UDP minimizes overhead and latency, making it suitable for real-time applications.
Use Cases of SSH Store UDP
- Securely transferring files between remote systems
- Establishing secure tunnels for remote access
- Providing a secure channel for streaming data
- Creating secure remote backups
Technical Specifications
SSH Store UDP is a lightweight, secure file transfer protocol that utilizes UDP as its transport layer. It offers various technical specifications that contribute to its efficiency and security:
Protocols
- SSH File Transfer Protocol (SFTP): Provides a secure file transfer mechanism over SSH connections.
- Universal Datagram Protocol (UDP): Facilitates fast and efficient data transmission over unreliable networks.
Ports
- Default UDP port: 10022
- Alternate UDP port (if port 10022 is blocked): 10023
Encryption Algorithms
- AES-128-CBC: Used for encrypting data in transit.
- AES-256-CBC: A stronger encryption algorithm that can be used for enhanced security.
- HMAC-SHA1: Employs a hash-based message authentication code for data integrity.
These technical specifications work in conjunction to provide a secure and reliable file transfer mechanism for SSH Store UDP.
Implementation and Configuration
Implementing and configuring SSH Store UDP involves installing the necessary software and configuring it to work with your SSH server. The specific steps will vary depending on your operating system and platform.
Configuration for Different Operating Systems
Here are the general steps for configuring SSH Store UDP on different operating systems:
-
- -*Linux Install the SSH Store UDP package and configure it using the `sshd_config` file.
-*macOS
Install SSH Store UDP using Homebrew and configure it using the `sshd_config` file.
-*Windows
Install SSH Store UDP using the Windows Subsystem for Linux (WSL) and configure it using the `sshd_config` file.
For detailed instructions on how to configure SSH Store UDP on your specific operating system, please refer to the official documentation or online tutorials.
Security Considerations
SSH Store UDP, while providing convenience and performance advantages, also introduces certain security considerations that must be taken into account.SSH Store UDP uses UDP, a connectionless protocol, which does not provide the same level of security as TCP. UDP does not guarantee message delivery or ordering, making it susceptible to spoofing and replay attacks.
To mitigate these risks, SSH Store UDP should be used only in trusted environments or with additional security measures, such as IPsec or TLS, in place.
Vulnerabilities and Mitigation Strategies
Spoofing Attacks: Attackers can send forged SSH Store UDP packets to impersonate legitimate clients or servers. To prevent spoofing, implement IP filtering or use IPsec or TLS to authenticate the source of packets.Replay Attacks: Attackers can capture and replay SSH Store UDP packets to gain unauthorized access or disrupt communication.
To mitigate replay attacks, use a sequence number or timestamp in SSH Store UDP packets to detect and discard replayed packets.Data Breaches: SSH Store UDP does not encrypt data by default, making it vulnerable to eavesdropping. To protect data, implement encryption using IPsec or TLS.Denial-of-Service
Attacks: Attackers can flood the network with SSH Store UDP packets to overwhelm servers and disrupt service. To mitigate DoS attacks, implement rate limiting or use a firewall to block excessive traffic.
Troubleshooting and Debugging
SSH Store UDP can encounter various issues during operation. This section provides troubleshooting tips to resolve common problems.
Connection Errors
Connection errors may occur due to incorrect IP addresses, port numbers, or firewall configurations. Verify that the IP address and port number are correct. Check firewall settings to ensure that UDP traffic is allowed on the specified port.
Authentication Failures
Authentication failures can arise from incorrect credentials, disabled accounts, or expired SSH keys. Double-check the username and password. Ensure that the account is enabled and not locked. Verify that the SSH key is valid and has not expired.
Data Transfer Problems
Data transfer problems may be caused by network congestion, packet loss, or buffer overflows. Check the network connection for stability and adequate bandwidth. Monitor packet loss and retransmission rates. Adjust buffer sizes as necessary to accommodate data volume.
Performance Optimization
Optimizing the performance of SSH Store UDP requires careful consideration of factors that affect speed and efficiency. Network conditions, configuration settings, and hardware resources all play a role in determining the performance of SSH Store UDP.
Network Conditions
Network conditions can significantly impact the performance of SSH Store UDP. High latency, packet loss, and congestion can all lead to decreased performance. It is important to ensure that the network infrastructure is optimized for UDP traffic and that there are no bottlenecks or congestion points.
Configuration Settings
The configuration settings of SSH Store UDP can also affect its performance. The following settings are particularly important:
- UDP Port: The UDP port used by SSH Store UDP should be carefully chosen to avoid conflicts with other applications or services.
- Buffer Size: The buffer size determines the amount of data that can be stored in the UDP buffer before it is sent. Increasing the buffer size can improve performance, but it can also increase latency.
- Timeout: The timeout setting determines how long SSH Store UDP will wait for a response from the server before resending a request. Increasing the timeout can improve reliability, but it can also decrease performance.
Hardware Resources
The hardware resources available to SSH Store UDP can also affect its performance. The following hardware resources are particularly important:
- CPU: The CPU is responsible for processing SSH Store UDP requests. A faster CPU can improve performance.
- Memory: Memory is used to store data that is being transferred over the network. Increasing the amount of memory available to SSH Store UDP can improve performance.
- Network Interface: The network interface is responsible for sending and receiving data over the network. A faster network interface can improve performance.
By carefully considering the factors that affect performance and optimizing the configuration settings and hardware resources, it is possible to achieve optimal performance from SSH Store UDP.
Integration with Other Services
SSH Store UDP can seamlessly integrate with various other services to enhance its functionality and cater to diverse use cases. Its interoperability with different protocols and applications opens up a wide range of possibilities for seamless data exchange and management.
One key aspect of SSH Store UDP’s integration capabilities lies in its support for different protocols. It can seamlessly communicate with services that utilize protocols such as HTTP, FTP, and SFTP. This allows for efficient data transfer between SSH Store UDP and other applications or systems that rely on these protocols.
Interoperability with Applications
SSH Store UDP’s interoperability extends beyond protocols, enabling it to integrate with a diverse range of applications. It can be seamlessly integrated with popular applications such as file managers, text editors, and database management systems. This integration allows for direct data access and manipulation within SSH Store UDP, enhancing productivity and streamlining workflows.
Use Cases and Applications

SSH Store UDP is a versatile tool that finds applications in diverse industries and scenarios.
Enterprise File Transfer
SSH Store UDP facilitates secure and efficient file transfer between remote servers and endpoints. It enables organizations to securely share sensitive data, such as financial records, confidential documents, and software updates, without exposing them to unauthorized access or interception.
Cloud Storage Access
SSH Store UDP serves as a secure gateway to access cloud storage services like Amazon S3 and Google Cloud Storage. It provides an encrypted channel for data transfer, ensuring the confidentiality and integrity of data during upload and download operations.
Remote Backup and Disaster Recovery
SSH Store UDP plays a crucial role in remote backup and disaster recovery strategies. It allows organizations to securely back up critical data to remote locations, ensuring data availability in case of hardware failures, natural disasters, or cyberattacks.
Remote Management and Monitoring
SSH Store UDP is used for remote management and monitoring of servers and network devices. It provides a secure and efficient way to access remote systems, execute commands, and monitor system performance from a centralized location.
Industrial Automation
In industrial automation, SSH Store UDP is used for secure communication between control systems and remote devices. It enables the transfer of configuration files, firmware updates, and diagnostic data, ensuring the smooth operation of industrial processes.
Comparison with Alternatives
SSH Store UDP stands out from other technologies with its unique features and capabilities. Let’s explore how it compares to some of its key alternatives.
One of the primary advantages of SSH Store UDP is its ability to securely transfer data over UDP. Unlike traditional SSH protocols that rely on TCP, UDP offers lower latency and faster transfer speeds, making SSH Store UDP ideal for applications that require real-time data transmission.
vs. SFTP
- SSH Store UDP provides faster data transfer speeds compared to SFTP, which uses TCP and has higher latency.
- SSH Store UDP is more efficient for transferring large files due to its use of UDP, which has lower overhead compared to TCP.
vs. SCP
- SSH Store UDP offers secure data transfer over UDP, while SCP uses TCP, which may be slower and less efficient.
- SSH Store UDP allows for more efficient file management and manipulation compared to SCP.
Future Developments
As SSH Store UDP continues to gain traction, several potential future developments and trends are worth considering. Emerging technologies, such as artificial intelligence (AI) and machine learning (ML), are expected to play a significant role in its evolution.
Integration with AI and ML
AI and ML algorithms can be leveraged to enhance the security and performance of SSH Store UDP. For instance, AI-powered intrusion detection systems can be integrated to detect and mitigate malicious activities, while ML algorithms can be employed to optimize data storage and retrieval operations, improving efficiency and reducing latency.
Closure
As the digital landscape continues to evolve, SSH Store UDP stands poised to play an increasingly pivotal role in safeguarding and facilitating data exchange. Its unparalleled security, coupled with its exceptional performance, makes it an indispensable tool for organizations seeking to protect their critical assets and empower their operations in the face of ever-changing technological challenges.