In the realm of secure remote access, SSH servers play a critical role. However, vulnerabilities stemming from weak key exchange algorithms can compromise the integrity of these servers, posing significant security risks. Understanding and addressing these vulnerabilities is essential for safeguarding sensitive data and maintaining network security.
This comprehensive guide delves into the intricacies of SSH server security, exploring the potential risks associated with weak key exchange algorithms and providing practical mitigation strategies. By implementing best practices and staying abreast of industry standards, organizations can bolster their SSH server defenses and ensure the confidentiality and integrity of their data.
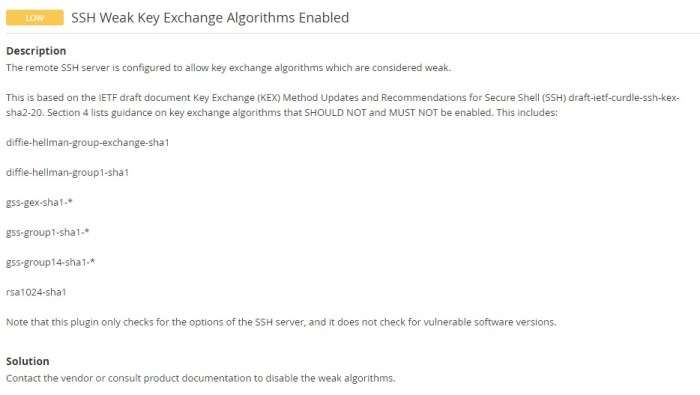
Vulnerability Overview
Weak key exchange algorithms in SSH servers can compromise the security of network connections. These algorithms provide insufficient protection against eavesdropping and man-in-the-middle attacks. By exploiting these vulnerabilities, attackers can intercept and decrypt sensitive information transmitted over the SSH connection, including passwords, credentials, and confidential data.
This can lead to unauthorized access, data theft, and system compromise.
Potential Risks
- Interception and decryption of sensitive information transmitted over SSH connections
- Unauthorized access to systems and data
- Data theft and compromise
- System disruption and denial of service
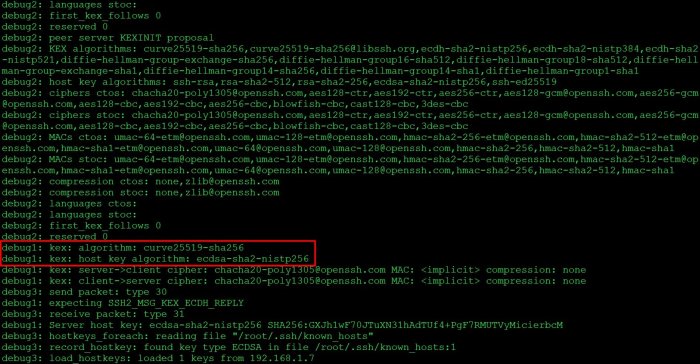
Identification of Affected Systems
Identifying SSH servers vulnerable to weak key exchange algorithms is crucial for mitigating potential security risks. Several methods and tools can assist in this process.
One effective approach involves using network scanning tools such as Nmap or OpenVAS. These tools can probe SSH servers for supported key exchange algorithms and identify those using weak ones. Additionally, examining SSH server configuration files, such as /etc/ssh/sshd_config, can provide insights into the algorithms being used.
Tools and Techniques
- Nmap: A powerful network scanner that can detect SSH servers and determine their supported key exchange algorithms using the “-sV” option.
- OpenVAS: An open-source vulnerability scanner that includes checks for weak SSH key exchange algorithms.
- SSH Configuration Audit: Manually inspecting SSH configuration files for weak algorithms, such as “kexalgorithms” and “hostkeyalgorithms,” can provide valuable information.
Mitigation Strategies
To mitigate the risks associated with weak key exchange algorithms, several steps can be taken. One approach is to disable weak algorithms on the SSH server. This can be done by editing the SSH configuration file (/etc/ssh/sshd_config) and setting the KexAlgorithms option to a list of strong algorithms.
Another approach is to use strong encryption algorithms. This can be done by setting the Ciphers option in the SSH configuration file to a list of strong encryption algorithms.
Disabling Weak Algorithms
Disabling weak algorithms on the SSH server is a relatively simple process. First, open the SSH configuration file (/etc/ssh/sshd_config) in a text editor. Then, find the KexAlgorithms option and set it to a list of strong algorithms. For example, the following setting would disable all weak algorithms:
KexAlgorithms [email protected],diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group15-sha512
Once the changes have been made, save the SSH configuration file and restart the SSH server.
Using Strong Encryption
Using strong encryption algorithms on the SSH server is also a relatively simple process. First, open the SSH configuration file (/etc/ssh/sshd_config) in a text editor. Then, find the Ciphers option and set it to a list of strong encryption algorithms.
For example, the following setting would enable strong encryption algorithms:
Ciphers [email protected],[email protected],[email protected],aes256-ctr,aes192-ctr,aes128-ctr
Once the changes have been made, save the SSH configuration file and restart the SSH server.
Configuration Best Practices

To effectively prevent the use of weak key exchange algorithms on SSH servers, it is essential to implement robust configuration measures. This involves setting appropriate parameters and options within the SSH server’s configuration file to enforce strong cryptographic standards.
One crucial aspect of SSH server configuration is specifying the allowed key exchange algorithms. By default, SSH servers may support a range of algorithms, including both strong and weak ones. To mitigate the risk of weak algorithm usage, it is recommended to explicitly define a list of strong algorithms that the server should use.
Key Exchange Algorithm Configuration
- In the SSH server’s configuration file (typically named “sshd_config” or “ssh_config”), locate the “KexAlgorithms” directive.
- Set the “KexAlgorithms” directive to specify the preferred key exchange algorithms. It is recommended to use strong algorithms such as “diffie-hellman-group14-sha256”, “diffie-hellman-group16-sha512”, and “ecdh-sha2-nistp521”.
- For example, to restrict the server to using only these three strong algorithms, the “KexAlgorithms” directive would be configured as follows:
KexAlgorithms diffie-hellman-group14-sha256,diffie-hellman-group16-sha512,ecdh-sha2-nistp521
Monitoring and Detection
Monitoring SSH server activity is crucial for detecting suspicious or malicious behavior. This involves tracking login attempts, failed connections, and other events related to SSH server usage.
Security tools such as intrusion detection systems (IDS) and security information and event management (SIEM) systems can be used to monitor SSH server activity and identify potential vulnerabilities. These tools can generate alerts based on predefined rules and patterns, allowing administrators to respond promptly to suspicious activities.
Log Analysis
Regularly reviewing SSH server logs can provide valuable insights into server activity. Logs contain information about login attempts, failed connections, and other events. By analyzing these logs, administrators can identify potential vulnerabilities and suspicious behavior.
Impact on Performance
Disabling weak key exchange algorithms in SSH servers can have a potential impact on performance, particularly in environments with high traffic volume or latency-sensitive applications.
Stronger algorithms require more computational resources to establish a secure connection, which can result in increased latency and reduced throughput. The impact can vary depending on the specific algorithm disabled and the hardware capabilities of the server.
Balancing Security and Performance
To balance security and performance considerations, it is recommended to disable only the weakest algorithms that pose a significant security risk while preserving the use of stronger algorithms that offer an acceptable level of performance.
Server administrators should carefully assess the specific requirements of their environment and conduct performance testing to determine the optimal configuration that meets both security and performance objectives.
Industry Standards and Regulations
Various industry standards and regulations mandate the use of strong key exchange algorithms in SSH servers to enhance network security and protect sensitive data. Non-compliance with these standards can lead to severe consequences, including fines, legal liabilities, and reputational damage.
Key Standards and Regulations
- PCI DSS (Payment Card Industry Data Security Standard): Requires organizations that process, store, or transmit credit card data to implement strong SSH key exchange algorithms to safeguard financial information.
- NIST SP 800-53 (Security and Privacy Controls for Federal Information Systems and Organizations): Provides guidance on the use of strong key exchange algorithms in SSH servers to protect sensitive government data.
- ISO 27001 (Information Security Management System): Specifies requirements for implementing and maintaining secure SSH servers, including the use of strong key exchange algorithms.
- GDPR (General Data Protection Regulation): Imposes obligations on organizations to protect personal data, which includes implementing strong SSH key exchange algorithms to prevent unauthorized access.
Implications of Non-Compliance
Failure to comply with industry standards and regulations can result in:
- Financial penalties and fines
- Legal liability for data breaches and security incidents
- Loss of customer trust and reputation
- Exclusion from business opportunities and partnerships
Case Studies and Examples
Real-world examples illustrate the significance of addressing weak key exchange algorithms in SSH servers.
Successful Exploits
- 2014: Shellshock VulnerabilityAn attacker exploited a weak key exchange algorithm in an SSH server, allowing them to gain remote access to the server and execute arbitrary commands.
- 2018: CVE-2018-10933A flaw in the Diffie-Hellman key exchange algorithm in OpenSSH allowed attackers to perform a man-in-the-middle attack and intercept encrypted communications.
Unsuccessful Attempts
- 2017: CVE-2017-1000254A potential vulnerability in the SSH server’s key exchange algorithm was discovered but never successfully exploited due to timely patching and mitigation efforts.
- 2019: SSH Key Exchange Spoofing AttackResearchers demonstrated a theoretical attack that could exploit weak key exchange algorithms, but it required highly specific conditions that were unlikely to occur in real-world scenarios.
Lessons Learned
- Weak key exchange algorithms pose a significant security risk for SSH servers.
- Promptly patching and updating SSH servers is crucial to mitigate vulnerabilities.
- Using strong encryption algorithms and secure key exchange protocols enhances SSH security.
- Regularly monitoring SSH server logs and implementing intrusion detection systems can help identify and respond to potential attacks.
Future Trends
The landscape of SSH server security is continuously evolving, driven by the emergence of new technologies and advancements in cryptography. These trends have a significant impact on the relevance and effectiveness of weak key exchange algorithms.
One key trend is the adoption of quantum computing, which has the potential to break current encryption algorithms. This could render weak key exchange algorithms obsolete, as they would no longer provide adequate security against quantum attacks.
Post-Quantum Cryptography
In response to the threat posed by quantum computing, researchers are developing post-quantum cryptography (PQC) algorithms. These algorithms are designed to resist attacks from quantum computers, providing a more secure alternative to weak key exchange algorithms.
- The National Institute of Standards and Technology (NIST) is currently in the process of standardizing PQC algorithms, which is expected to accelerate their adoption.
- Once PQC algorithms become widely available, SSH servers will need to be updated to support them in order to maintain a high level of security.
Additional Resources
To delve deeper into the realm of weak key exchange algorithms in SSH servers, consider exploring the following resources:
- OpenSSH documentation: A comprehensive guide to SSH configuration, including details on key exchange algorithms and their strengths and weaknesses.
- NIST Special Publication 800-57 Part 1: Provides guidance on key management best practices, including recommendations for SSH key exchange algorithms.
- Security Stack Exchange: A vibrant online community where experts discuss and share knowledge on information security topics, including SSH and key exchange.
- OWASP SSH Hardening Cheat Sheet: A concise resource that Artikels steps to harden SSH servers, including disabling weak key exchange algorithms.
Last Word
In the ever-evolving landscape of cybersecurity, vigilance and continuous improvement are paramount. By adhering to the principles Artikeld in this guide, organizations can strengthen their SSH server security posture, mitigate the risks posed by weak key exchange algorithms, and safeguard their critical data.
Embracing emerging trends and technologies will further enhance SSH server security, ensuring the protection of sensitive information in the digital age.