In the realm of cybersecurity, the Secure Shell (SSH) protocol plays a pivotal role in establishing secure remote connections. However, the effectiveness of SSH connections hinges on the robustness of the underlying key exchange algorithms. Weak key exchange algorithms can compromise the integrity of SSH connections, exposing systems to a myriad of security threats.
This comprehensive guide delves into the intricacies of weak key exchange algorithms in SSH connections, exploring their potential risks, detection methods, mitigation strategies, and best practices. By shedding light on this critical aspect of SSH security, we aim to empower system administrators and users alike to safeguard their networks and data.
Weak Key Exchange Algorithms

Key exchange algorithms are cryptographic protocols used to establish a shared secret key between two parties over an insecure channel. Weak key exchange algorithms are algorithms that are vulnerable to attack, allowing an attacker to compromise the shared secret key.The
use of weak key exchange algorithms poses significant risks to the security of a system. An attacker who can compromise the shared secret key can decrypt encrypted communications, impersonate legitimate users, and gain unauthorized access to sensitive data.Some examples of weak key exchange algorithms that should be avoided include:
- RSA with key sizes less than 2048 bits
- Diffie-Hellman with key sizes less than 2048 bits
- Elliptic Curve Diffie-Hellman with curves that are not considered secure
SSH Server Configuration
SSH servers can be configured to use weak key exchange algorithms, which can compromise the security of the server. It is important to check if an SSH server is using weak key exchange algorithms and disable them if necessary.
Checking for Weak Key Exchange Algorithms
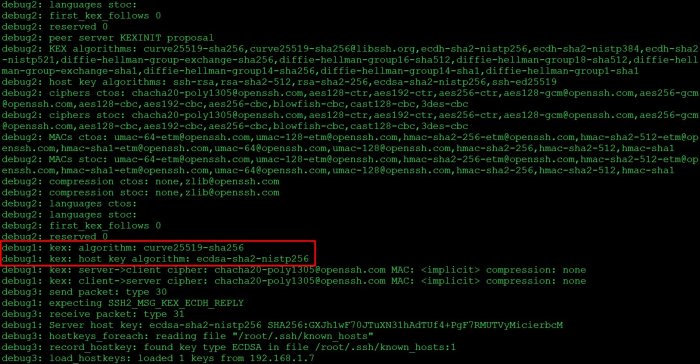
To check if an SSH server is using weak key exchange algorithms, you can use the following command:“`ssh
Q key-exchange-algorithms
“`This command will output a list of the key exchange algorithms that the SSH server supports. If any of the algorithms in the list are considered weak, then the server is vulnerable to attack.
Disabling Weak Key Exchange Algorithms
To disable weak key exchange algorithms on an SSH server, you can edit the SSH configuration file, which is typically located at /etc/ssh/sshd_config. Find the line that says “KexAlgorithms” and replace the list of algorithms with a list of strong algorithms, such as:“`KexAlgorithms curve25519-sha256,[email protected],ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256“`Once
you have made the changes, restart the SSH server for the changes to take effect.
Importance of Regular Updates
It is important to regularly update SSH server software to ensure that the latest security patches are applied. These patches can fix vulnerabilities that could be exploited by attackers to compromise the server. You can check for updates by running the following command:“`yum update ssh“`Or“`apt update && apt upgrade ssh“`If any updates are available, install them immediately.
SSH Client Configuration
SSH clients may also use weak key exchange algorithms that compromise the security of SSH connections. It’s essential to check if your SSH client supports weak key exchange algorithms and disable them for secure communication.
Checking SSH Client Configuration
To check if your SSH client uses weak key exchange algorithms, run the following command:“`ssh
Q key-exchange-algorithms
“`This command will display a list of key exchange algorithms supported by your SSH client. If you see any weak algorithms, such as “diffie-hellman-group1-sha1” or “diffie-hellman-group14-sha1,” you should disable them.
Disabling Weak Key Exchange Algorithms
To disable weak key exchange algorithms on your SSH client, edit the SSH configuration file, typically located at “~/.ssh/config”. Add the following line to the file:“`KexAlgorithms [email protected],diffie-hellman-group-exchange-sha256“`This line specifies that your SSH client should only use strong key exchange algorithms, such as “curve25519-sha256” and “diffie-hellman-group-exchange-sha256.”
Importance of Using a Secure SSH Client
Using a secure SSH client that supports strong key exchange algorithms is crucial for maintaining the security of SSH connections. Weak key exchange algorithms can be exploited by attackers to compromise SSH sessions, allowing them to gain unauthorized access to your system.
Therefore, it’s essential to ensure that your SSH client is configured to use strong key exchange algorithms to protect against potential attacks.
Best Practices for Secure SSH Connections
Secure Shell (SSH) is a vital tool for remote access and secure communication. However, if not configured and used correctly, SSH connections can be vulnerable to attacks. To ensure the security of SSH connections, it is essential to implement best practices for both server and client configuration.
Server Configuration
*
-*Use Strong Key Exchange Algorithms
SSH supports various key exchange algorithms. For secure connections, use algorithms such as ECDH (Elliptic Curve Diffie-Hellman) or Ed25519.
-
- -*Disable Weak Cipher Suites
Disable weak cipher suites like CBC (Cipher Block Chaining) and RC4. Use stronger suites like AES-GCM (Advanced Encryption Standard
- Galois/Counter Mode).
- -*Disable Weak Cipher Suites
-*Enforce Strong Password Policies
Require strong passwords for user accounts. Consider using password hashing algorithms like bcrypt or scrypt.
-*Enable Multi-Factor Authentication
Implement multi-factor authentication (MFA) to add an extra layer of security. MFA requires users to provide multiple forms of identification, making it harder for attackers to gain access.
-*Restrict Root Login
Disable direct root login and use a dedicated administrative account with limited privileges.
Client Configuration
*
-*Use Secure Key Exchange Algorithms
Similar to servers, clients should use strong key exchange algorithms like ECDH or Ed25519.
-
- -*Verify Server Certificates
Verify the server’s certificate to ensure you are connecting to the intended server and not an impostor.
- -*Verify Server Certificates
-*Use Strong Passwords or SSH Keys
Use strong passwords or SSH keys for authentication. Consider using a password manager or SSH key manager to generate and store secure credentials.
-*Enable Multi-Factor Authentication
If available, enable MFA on the client side as well. This provides an additional layer of security in case the client is compromised.
-*Keep Software Up-to-Date
Ensure that both the SSH server and client software are up-to-date with the latest security patches.
Checklist for Secure SSH Connections
* Use strong key exchange algorithms (ECDH, Ed25519).
- Disable weak cipher suites (CBC, RC4).
- Enforce strong password policies (bcrypt, scrypt).
- Enable multi-factor authentication (MFA).
- Restrict root login on the server.
- Verify server certificates on the client.
- Use strong passwords or SSH keys for authentication.
- Enable MFA on the client.
- Keep software up-to-date.
By implementing these best practices, organizations and individuals can significantly enhance the security of their SSH connections and protect sensitive data from unauthorized access.
Consequences of Weak Key Exchange Algorithms
Utilizing weak key exchange algorithms in SSH connections can lead to dire consequences for data security. These algorithms, responsible for establishing secure communication channels, are susceptible to exploitation by attackers.
Weak key exchange algorithms present a significant risk of data breaches. Attackers can exploit these algorithms to decrypt encrypted data transmitted over SSH connections, exposing sensitive information such as login credentials, financial data, and confidential business documents.
Unauthorized Access
Weak key exchange algorithms can also facilitate unauthorized access to systems and networks. By compromising the encryption mechanism, attackers can gain access to remote servers, execute malicious commands, and steal data.
Other Security Incidents
Beyond data breaches and unauthorized access, weak key exchange algorithms can contribute to various security incidents, including:
- Denial of service (DoS) attacks: Attackers can exploit weak key exchange algorithms to launch DoS attacks, disrupting SSH services and preventing legitimate users from accessing systems.
- Man-in-the-middle (MitM) attacks: Weak key exchange algorithms can allow attackers to intercept and manipulate SSH traffic, impersonating legitimate users and gaining access to sensitive data.
Real-World Incidents
Several real-world incidents have demonstrated the severe consequences of weak key exchange algorithms in SSH connections:
- 2014 OpenSSL Heartbleed bug: This vulnerability in the OpenSSL library, commonly used in SSH implementations, allowed attackers to exploit a weak key exchange algorithm and steal sensitive data from vulnerable servers.
- 2017 WannaCry ransomware attack: This global ransomware attack exploited a weak key exchange algorithm in SSH implementations, enabling attackers to encrypt and lock files on affected systems.
Alternative Key Exchange Algorithms
SSH connections can employ various key exchange algorithms to establish a secure connection. Some of the alternative algorithms include:
Diffie-Hellman Group Exchange (DH-GEX)
DH-GEX utilizes a Diffie-Hellman key exchange to generate a shared secret, which is then used to derive the session keys. It offers enhanced security compared to the traditional Diffie-Hellman key exchange by allowing the server to choose a different group for each session, mitigating potential vulnerabilities.
Elliptic Curve Diffie-Hellman (ECDH)
ECDH employs elliptic curve cryptography to establish a shared secret. It provides higher security than DH-GEX, as it utilizes smaller key sizes for equivalent levels of protection. Additionally, ECDH is less susceptible to certain types of attacks.
RSA-authenticated Diffie-Hellman (RSA-DH)
RSA-DH combines RSA authentication with Diffie-Hellman key exchange. It utilizes an RSA signature to authenticate the server, ensuring that the client is connecting to the intended server. This combination enhances security by preventing man-in-the-middle attacks.When selecting a key exchange algorithm, consider the following factors:
Security strength
The level of protection provided by the algorithm against various attacks.
Performance
The computational cost and latency associated with the algorithm.
Compatibility
The support for the algorithm by both the SSH client and server.For most applications, ECDH offers a balance of security, performance, and compatibility. However, in situations where maximum security is paramount, RSA-DH may be a more appropriate choice.
SSH Protocol Versions
The SSH protocol has evolved through several versions, each introducing new features and security enhancements. However, older versions of SSH may support weak key exchange algorithms that are vulnerable to compromise.Understanding the differences between SSH protocol versions and their support for weak key exchange algorithms is crucial for maintaining a secure SSH connection.
Security Implications of Using Older SSH Protocol Versions
Using older SSH protocol versions, such as SSH-1, can introduce security risks. SSH-1 is no longer considered secure due to its limited support for strong encryption algorithms and susceptibility to man-in-the-middle attacks.SSH-2, introduced in 1996, addressed many of the security weaknesses of SSH-1.
It introduced stronger encryption algorithms and improved authentication mechanisms. However, SSH-2 may still support weak key exchange algorithms, such as Diffie-Hellman Group 1 (DH Group 1), which are vulnerable to cryptanalysis.
Minimum SSH Protocol Version Recommendation
To mitigate the security risks associated with weak key exchange algorithms, it is recommended to use the latest version of the SSH protocol, SSH-2.1 or higher. SSH-2.1 introduced mandatory support for strong key exchange algorithms, ensuring that weak algorithms like DH Group 1 are not used.By
enforcing the use of strong key exchange algorithms, organizations can protect their SSH connections from compromise and maintain a secure communication channel.
Network Security Considerations
Network security devices play a crucial role in mitigating the risks associated with weak key exchange algorithms in SSH connections. These devices can be configured to monitor, detect, and block unauthorized SSH connections, enhancing the overall security of the network.
Firewalls, intrusion detection systems (IDSs), and other network security measures can be employed to protect SSH servers and clients from malicious activities.
Firewalls
Firewalls can be configured to restrict access to SSH ports, preventing unauthorized connections from outside the network. By blocking incoming connections from untrusted sources, firewalls help prevent attackers from exploiting weak key exchange algorithms to gain access to the network.
Intrusion Detection Systems
IDSs can monitor network traffic for suspicious activities, including attempts to exploit weak key exchange algorithms. By detecting and alerting on such attempts, IDSs can help administrators respond quickly and mitigate potential threats.
Other Network Security Measures
Other network security measures, such as access control lists (ACLs) and intrusion prevention systems (IPSs), can also be used to enhance SSH security. ACLs can be configured to restrict access to SSH servers based on IP addresses or other criteria, while IPSs can actively block attacks that exploit weak key exchange algorithms.
Monitoring and Auditing
Monitoring and auditing SSH connections are crucial for detecting potential security incidents and maintaining the integrity of your systems. By tracking SSH activity, you can identify suspicious connections and take appropriate actions to mitigate risks.
To set up a monitoring system for SSH connections, you should consider the following steps:
Monitoring Tools
- Install a log monitoring tool, such as Logwatch or Syslog-ng, to collect and analyze SSH logs.
- Configure your SSH server to log all connection attempts, successful and unsuccessful.
- Set up alerts to notify you of suspicious SSH activity, such as multiple failed login attempts from the same IP address.
Log Analysis
Regularly review SSH logs to identify potential security incidents. Look for patterns of unusual activity, such as:
- Repeated failed login attempts from different IP addresses.
- Successful logins from unexpected locations.
- Connections from known malicious IP addresses.
By monitoring and auditing SSH connections, you can stay informed about potential security threats and take proactive measures to protect your systems.
Security Standards and Compliance
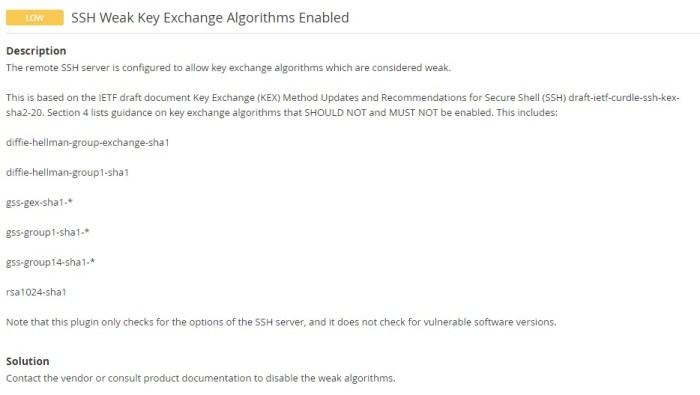
SSH connections are subject to various security standards and compliance requirements, including industry regulations and best practices.
Weak key exchange algorithms can compromise compliance by failing to meet the minimum security requirements set by these standards.
Implications for Compliance
- Violations of industry regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA).
- Failure to meet best practices guidelines, such as the National Institute of Standards and Technology (NIST) recommendations and the Center for Internet Security (CIS) benchmarks.
- Increased risk of data breaches and security incidents due to weak encryption.
Ensuring Compliance
- Use strong key exchange algorithms that meet or exceed industry standards.
- Regularly review and update SSH server configurations to ensure compliance with latest security requirements.
- Implement security controls, such as firewalls and intrusion detection systems, to protect SSH connections from external threats.
- Monitor and audit SSH connections to detect and respond to suspicious activity.
Outcome Summary
Securing SSH connections against weak key exchange algorithms requires a multifaceted approach that encompasses server and client configuration, regular software updates, and adherence to best practices. By implementing the measures Artikeld in this guide, organizations can significantly enhance their SSH security posture, minimizing the risks associated with weak key exchange algorithms and ensuring the confidentiality, integrity, and availability of their sensitive data.