Secure Shell (SSH) is a vital protocol for remote server management and secure data transfer. However, the security of SSH deployments can be compromised if weak key exchange algorithms are supported. This article explores the risks associated with weak key exchange algorithms in SSH, provides guidance on identifying vulnerable servers, and Artikels strategies for mitigation.
Weak key exchange algorithms can allow attackers to intercept and decrypt SSH traffic, leading to unauthorized access to sensitive data and systems. Understanding the vulnerabilities and implementing robust mitigation measures are essential for maintaining the integrity and security of SSH deployments.
SSH Weak Key Exchange Algorithms

SSH (Secure Shell) is a network protocol that enables secure remote access and command execution over insecure networks. SSH servers support various key exchange algorithms to establish secure communication channels between clients and servers. However, some of these algorithms are considered weak and vulnerable to attack.
Weak key exchange algorithms in SSH lack sufficient cryptographic strength to protect against brute-force attacks or advanced cryptanalytic techniques. This can compromise the confidentiality and integrity of the communication channel, allowing attackers to eavesdrop on or modify the transmitted data.
Common Weak Key Exchange Algorithms
Some common weak key exchange algorithms supported by SSH servers include:
- Diffie-Hellman Group 1 (DH Group 1)
- Diffie-Hellman Group 14 (DH Group 14)
- Elliptic Curve Diffie-Hellman (ECDH) over prime curves with less than 256 bits
These algorithms use small key sizes or weak mathematical groups, making them susceptible to brute-force attacks or cryptanalysis.
Risks and Consequences
Using weak key exchange algorithms in SSH deployments poses significant risks:
- Compromised Confidentiality: Attackers can intercept and decrypt sensitive data transmitted over the SSH connection.
- Compromised Integrity: Attackers can modify or forge data, potentially leading to unauthorized actions or system compromise.
- Session Hijacking: Attackers can impersonate legitimate users and gain unauthorized access to remote systems.
Identifying Vulnerable Servers
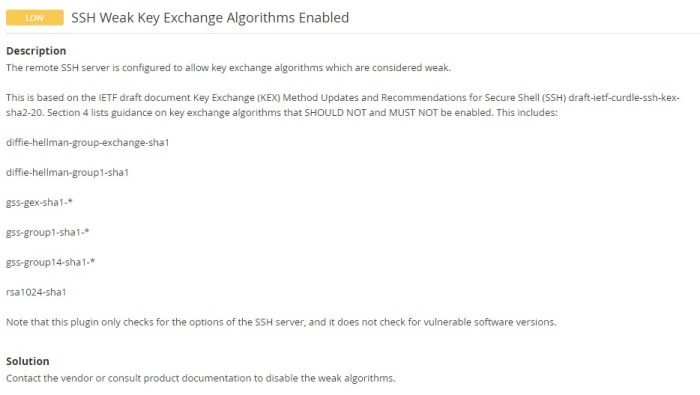
Identifying SSH servers that support weak key exchange algorithms is crucial for mitigating security risks. Several methods and tools are available for this purpose:
Manual Verification
Manually checking the SSH server configuration can reveal the supported key exchange algorithms. On Linux systems, the following command displays the configuration:“`sshd
T | grep KexAlgorithms
“`If weak algorithms like “diffie-hellman-group1-sha1” or “diffie-hellman-group14-sha1” appear, the server is vulnerable.
Scanning Tools
Various tools automate the scanning process for vulnerable SSH servers. Some popular options include:
- OpenSSL: The “openssl s_client
-connect” command can be used to connect to an SSH server and determine its supported algorithms. - Nmap: The “-sV” option in Nmap allows scanning for SSH servers and detecting weak key exchange algorithms.
- Nessus: This commercial tool provides comprehensive vulnerability scanning, including checks for weak SSH key exchange algorithms.
Best Practices for Keeping SSH Servers Updated
To minimize the risk of vulnerabilities, it’s essential to keep SSH servers updated with the latest security patches:
- Regularly Apply Updates: Install security updates as soon as they become available from the vendor.
- Use a Package Manager: Use a package manager like “apt” or “yum” to simplify the update process.
- Disable Unnecessary Services: Disable any SSH services that are not essential to reduce the attack surface.
By following these practices, organizations can effectively identify and mitigate vulnerabilities associated with weak SSH key exchange algorithms, ensuring the security of their SSH servers.
Mitigation Strategies
Mitigating the risks associated with weak key exchange algorithms in SSH involves a multifaceted approach that encompasses disabling or removing support for vulnerable algorithms, implementing strong algorithms, and adhering to industry best practices.
Disabling or removing weak algorithms from SSH servers is a crucial step in securing SSH connections. This can be achieved by modifying the server’s configuration file to specify the desired algorithms. For instance, in OpenSSH, the Ciphers and KexAlgorithms directives can be used to specify the allowed ciphers and key exchange algorithms, respectively.
Strong Key Exchange Algorithms
Employing strong key exchange algorithms is paramount for maintaining secure SSH connections. These algorithms provide robust protection against brute-force attacks and ensure the confidentiality and integrity of exchanged data. The recommended key exchange algorithms include ECDH (Elliptic Curve Diffie-Hellman), Diffie-Hellman Group 14 (DH Group 14), and Ed25519.
Industry Best Practices
Adhering to industry best practices is essential for comprehensive SSH security. These practices include regularly updating SSH software, monitoring SSH logs for suspicious activity, and enforcing strong password policies. Additionally, using a firewall to restrict access to SSH ports and implementing intrusion detection systems (IDS) can further enhance SSH security.
SSH Configuration Hardening
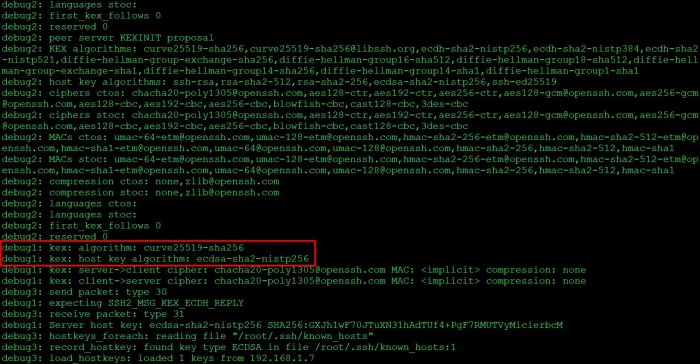
To prevent exploitation of weak key exchange algorithms, it’s crucial to harden SSH server configurations. SSH relies on key exchange algorithms to establish secure connections, ensuring data integrity and confidentiality during authentication and encryption processes.
Beyond key exchange algorithm selection, implementing additional security measures is essential. These include employing two-factor authentication to enhance user verification and limiting access to SSH services to authorized individuals or systems, minimizing the attack surface.
Additional Security Measures
- Two-Factor Authentication: Implement two-factor authentication to strengthen user verification. This adds an extra layer of security, requiring users to provide a second form of authentication beyond their password.
- Restrict Access to SSH Services: Limit access to SSH services to authorized individuals or systems. Configure SSH to restrict logins from specific IP addresses, subnets, or users. This reduces the potential attack surface and prevents unauthorized access.
Secure Key Exchange Algorithms
In SSH deployments, the selection of secure key exchange algorithms is crucial for establishing a robust and secure connection. Various algorithms offer different levels of security and performance, making it essential to understand their advantages and disadvantages.
Secure key exchange algorithms provide a means to securely establish a shared secret key between two parties, even when an eavesdropper is present. These algorithms are designed to resist various attacks, including man-in-the-middle attacks and replay attacks.
Recommended Key Exchange Algorithms
The following key exchange algorithms are highly recommended for use in SSH deployments due to their strong security and wide support:
- Elliptic Curve Diffie-Hellman (ECDH): ECDH is a modern and efficient algorithm that provides high levels of security and performance. It uses elliptic curve cryptography, which offers smaller key sizes compared to traditional Diffie-Hellman.
- Diffie-Hellman Group Exchange (DH-GEX): DH-GEX is a variant of the Diffie-Hellman algorithm that provides forward secrecy. It generates a new Diffie-Hellman group for each session, making it more resistant to eavesdropping attacks.
- RSA Key Exchange: RSA Key Exchange is a widely supported algorithm that uses RSA public-key cryptography. While it is less efficient than ECDH and DH-GEX, it remains a secure choice for many deployments.
Importance of Using Secure Algorithms
Using secure key exchange algorithms is paramount for several reasons:
- Resistance to Attacks: Secure algorithms are designed to withstand known attacks, including brute-force attacks and cryptanalytic attacks. This helps protect SSH connections from unauthorized access.
- Industry Standards: The recommended algorithms are widely accepted by industry standards and best practices. Using these algorithms ensures compliance with security guidelines and best practices.
- Data Protection: Secure key exchange algorithms help protect sensitive data transmitted over SSH connections. By establishing a secure shared secret key, data can be encrypted and protected from eavesdropping.
Impact on SSH Performance
Weak key exchange algorithms can significantly impact SSH performance, affecting connection speed, latency, and overall system efficiency.When using weak algorithms, the SSH client and server must perform more computations to establish a secure connection. This increased computational overhead can slow down the connection process and introduce noticeable latency.
Moreover, weak algorithms may require more frequent rekeying, which further adds to the computational load and can lead to performance degradation over time.The trade-off between security and performance should be carefully considered when selecting key exchange algorithms. While weak algorithms may offer faster performance, they compromise the security of the connection.
Strong algorithms, on the other hand, provide better security but may result in a slight performance penalty.
Factors Affecting Performance
Several factors can influence the performance impact of weak key exchange algorithms:
-
- -*Algorithm Complexity
The complexity of the algorithm directly affects the computational overhead required for key exchange. More complex algorithms typically take longer to compute, resulting in slower performance.
- -*Algorithm Complexity
-*Key Size
Larger key sizes provide stronger security but require more computational resources to generate and exchange. This can impact performance, especially for algorithms that rely on large keys for security.
-*Hardware Capabilities
The performance of SSH key exchange algorithms can vary depending on the hardware capabilities of the client and server. Slower hardware may experience more performance degradation when using weak algorithms.
-*Network Conditions
Network conditions, such as latency and bandwidth, can also affect the performance of SSH key exchange. High latency or low bandwidth can exacerbate the performance impact of weak algorithms.
Case Studies and Real-World Examples
Weak key exchange algorithms in SSH servers have led to numerous security breaches, compromising sensitive data and systems.
Here are two notable case studies:
2014 Yahoo Breach
In 2014, Yahoo experienced a massive data breach affecting over 500 million user accounts. The attackers exploited a vulnerability in Yahoo’s SSH server that allowed them to access private keys used for encrypting user data. The attackers used these keys to decrypt and steal sensitive user information, including names, email addresses, and passwords.
The breach highlighted the importance of using strong key exchange algorithms in SSH servers. Yahoo had configured their SSH server to use the weak Diffie-Hellman key exchange algorithm, which made it vulnerable to attack.
2017 Equifax Breach
In 2017, Equifax suffered a data breach that exposed the personal information of over 145 million Americans. The attackers exploited a vulnerability in Equifax’s SSH server that allowed them to gain unauthorized access to the server. The attackers then used the server to access and steal sensitive user data, including names, Social Security numbers, and credit card information.
Equifax had configured their SSH server to use the weak DSA key exchange algorithm, which made it vulnerable to attack. The attackers used a brute-force attack to crack the DSA key and gain access to the server.
Lessons Learned
These case studies illustrate the importance of using strong key exchange algorithms in SSH servers. Weak key exchange algorithms can compromise the security of SSH servers and lead to data breaches. Organizations should configure their SSH servers to use strong key exchange algorithms, such as ECDH or Ed25519, to protect against these types of attacks.
Industry Standards and Security
explanatory intro
Sub-title
- Industry standards and regulations like CIS Benchmark and NIST SP 800-53 define best practices for SSH key exchange.
- Adherence to these standards enhances security by ensuring strong key exchange algorithms and secure key management practices.
- Industry bodies like the Internet Engineering Task Force (IETF) and the Open Web Application Security Project (OWдить) contribute to SSH security by developing and promoting best practices.
Emerging Threats and Future Considerations
The evolving threat landscape necessitates constant vigilance and proactive measures to safeguard SSH infrastructure. Emerging threats and future considerations related to SSH key exchange algorithms must be addressed to ensure ongoing security and resilience.
Current algorithms may harbor potential vulnerabilities or weaknesses that could be exploited by malicious actors. Continuous monitoring and research are crucial to identify and mitigate these risks. Researchers and security experts are actively exploring novel approaches to enhance SSH security and minimize the impact of weak key exchange algorithms.
Potential Vulnerabilities and Mitigation Strategies
Potential vulnerabilities in current algorithms could arise from advancements in cryptanalysis techniques, increased computational power, or the discovery of new weaknesses. Mitigation strategies include:
- Regular algorithm updates to incorporate advancements and address vulnerabilities
- Enforcing strong key generation practices to reduce the likelihood of weak keys
- Deploying intrusion detection and prevention systems to monitor for suspicious activity and potential attacks
Research and Development Efforts
Ongoing research and development efforts aim to improve SSH security and mitigate risks associated with weak key exchange algorithms. These efforts include:
- Developing new key exchange algorithms with enhanced security and resistance to cryptanalysis
- Exploring post-quantum cryptography algorithms to address the threat posed by quantum computers
- Automating SSH configuration hardening to reduce the risk of misconfigurations and vulnerabilities
Best Practices for SSH Security
Ensuring SSH security is paramount for organizations and individuals alike. Here are some best practices to enhance SSH deployments, focusing on key exchange algorithms:
Organizations should implement a strict policy that prohibits the use of weak key exchange algorithms, such as DH, DH-GEX, and KEX. Instead, they should mandate the use of strong algorithms, such as ECDH-ECDSA and ECDH-RSA, which provide robust protection against brute-force attacks.
Key Exchange Algorithm Recommendations
- Disable weak key exchange algorithms, such as DH, DH-GEX, and KEX.
- Enable strong key exchange algorithms, such as ECDH-ECDSA and ECDH-RSA.
- Regularly review and update the list of supported key exchange algorithms based on industry standards and security best practices.
Regular Security Audits
Regular security audits are crucial for identifying vulnerabilities and ensuring SSH security. These audits should assess the configuration of SSH servers and clients, including the key exchange algorithms used. Organizations should engage qualified security professionals or use automated tools to conduct these audits regularly.
Patch Management
Timely application of security patches is essential for mitigating vulnerabilities in SSH software. Organizations should establish a patch management process that ensures SSH servers and clients are updated promptly with the latest security patches. This process should be regularly reviewed and updated to address emerging threats.
Ongoing Monitoring
Ongoing monitoring of SSH activity is critical for detecting suspicious behavior and preventing security breaches. Organizations should implement intrusion detection systems (IDS) and security information and event management (SIEM) tools to monitor SSH logs and identify any unauthorized access attempts or other suspicious activities.
Last Word
By adhering to industry best practices, organizations can effectively mitigate the risks associated with weak key exchange algorithms in SSH. Regular security audits, patch management, and continuous monitoring are crucial for maintaining SSH security. Embracing strong key exchange algorithms and implementing additional security measures, such as two-factor authentication and access control, further enhance SSH deployments.