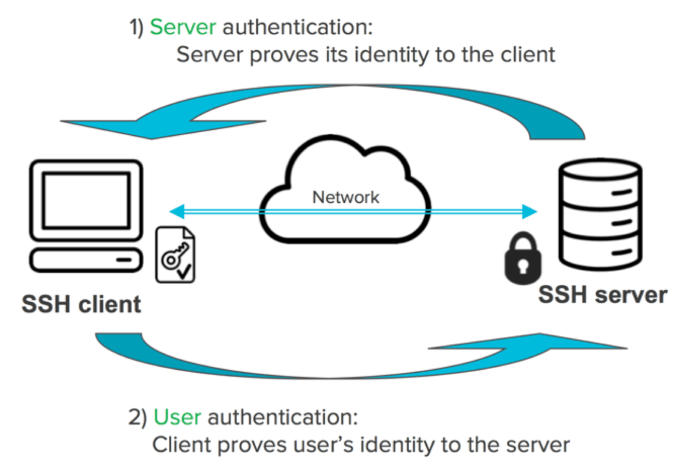
In the realm of secure remote access, the SSH protocol reigns supreme. At its core lies the public key infrastructure, where a key’s size plays a pivotal role. In this article, we delve into the critical implications of using an SSH server public key that is too small, exploring the security risks, best practices, and mitigation strategies.
A public key, the cornerstone of SSH authentication, serves as the gateway to your server. Its size directly impacts the strength of the encryption used to protect your data. A small public key, like a flimsy lock, can easily be compromised, leaving your server vulnerable to unauthorized access.
Public Key Size
In SSH server security, the size of the public key plays a crucial role in determining the level of protection against unauthorized access.
When a public key is too small, it becomes more vulnerable to brute-force attacks, where attackers attempt to guess the private key by trying out numerous possible combinations. A smaller key size reduces the number of possible combinations, making it easier for attackers to crack the key and gain access to the server.
Recommended Key Size
To ensure adequate security, it is recommended to use a public key size of at least 2048 bits. This key size provides a high level of protection against brute-force attacks and is considered industry best practice for SSH server security.
Security Implications
Using a small public key in SSH introduces significant security risks, as it can compromise the integrity of SSH connections. A small public key provides less entropy, making it easier for attackers to guess or brute-force the private key.
The reduced key size weakens the cryptographic algorithms used in SSH, making it more susceptible to attacks. This can lead to unauthorized access to the server, allowing attackers to gain control over the system and potentially steal sensitive data or launch further attacks.
Key Exhaustion Attacks
A key exhaustion attack is a type of brute-force attack that involves trying all possible combinations of a small public key to determine the corresponding private key. With a smaller public key, the number of possible combinations is significantly reduced, making it easier for attackers to exhaust all options and compromise the server.
Recommendation for Key Size
Determining an appropriate public key size for your SSH server is crucial for maintaining a balance between security and performance. Let’s delve into the industry standards and best practices to guide your decision.
The key size refers to the number of bits used to generate the public and private key pair. Larger key sizes provide enhanced security but may come at the cost of computational overhead.
Industry Standards and Best Practices
- NIST Recommendation: The National Institute of Standards and Technology (NIST) recommends a minimum key size of 2048 bits for SSH public keys.
- Industry Standard: Within the industry, key sizes ranging from 2048 to 4096 bits are commonly used, with 4096 bits being the preferred choice for high-security environments.
- Future-Proofing: While 2048 bits is currently considered secure, advancements in computing power may make it vulnerable in the future. Therefore, opting for a larger key size, such as 4096 bits, is recommended for long-term security.
Mitigation Strategies

To mitigate the risks associated with using a small public key, several strategies can be implemented.
One effective approach is to increase the key size to a more secure level, such as 4096 bits or higher. This significantly enhances the computational effort required to crack the key, making it more resilient to brute-force attacks.
Enhancing SSH Server Security
Beyond increasing the key size, additional measures can be taken to strengthen SSH server security without compromising functionality.
- Disable password authentication: Relying solely on public key authentication eliminates the risk of password-based attacks.
- Implement two-factor authentication (2FA): Adding an extra layer of security through 2FA provides an additional barrier against unauthorized access.
- Limit SSH access: Restricting SSH access to specific IP addresses or subnets reduces the attack surface and prevents unauthorized connections.
- Use strong ciphers and algorithms: Employing robust encryption algorithms, such as AES-256-GCM or ChaCha20-Poly1305, ensures data confidentiality and integrity.
- Enable security logging and monitoring: Logging and monitoring SSH activity helps detect suspicious behavior and facilitates timely response to security incidents.
Impact on SSH Protocol
The size of the public key in SSH plays a crucial role in determining the functionality and compatibility of the SSH protocol.
A small public key can limit the available cryptographic algorithms and key exchange methods that can be used during SSH sessions. This can lead to compatibility issues with older or less secure SSH clients and servers that do not support the newer, more secure algorithms.
Compatibility Limitations
- Restricted Algorithm Support: Smaller public keys may not support newer, more secure cryptographic algorithms, such as Elliptic Curve Cryptography (ECC) or Ed25519, which offer higher levels of security.
- Key Exchange Limitations: The size of the public key can also impact the choice of key exchange algorithms available. Smaller keys may not be suitable for certain key exchange methods, such as Diffie-Hellman, which require a minimum key size for secure operation.
- Legacy Client Compatibility: Some older SSH clients may not support public keys that are too large. Using a smaller public key can ensure compatibility with these legacy clients.
Common Misconceptions
Many individuals believe that longer public keys are always superior. However, this assumption overlooks the importance of considering the computational cost associated with using larger keys. While longer keys provide increased security, they can also lead to a significant performance penalty, especially on resource-constrained devices.Another
common misconception is that a larger key size automatically implies stronger security. While a larger key size does increase the difficulty of brute-force attacks, it is essential to recognize that other factors, such as the quality of the random number generator used to generate the key, also play a crucial role in determining the overall security of the SSH connection.
Best Practices for Key Management
Proper key management is crucial for SSH security. Here are some best practices:
Key Rotation
Regularly rotate SSH keys to mitigate the impact of key compromise. Establish a schedule for key rotation based on the organization’s security policy and risk assessment.
Secure Key Storage
Store SSH keys securely in a password-protected or encrypted file system. Use a dedicated key management system or a secure vault to store and manage keys centrally.
Key Distribution
Distribute SSH keys securely using a trusted channel. Consider using a key distribution system or a secure file transfer protocol.
Tools for Key Generation
When generating SSH public keys, several tools and techniques can be utilized. The choice of tool depends on factors such as the operating system, security requirements, and desired level of control over the key generation process.
Popular tools include the built-in SSH key generation utility (ssh-keygen), OpenSSL, and third-party tools like PuTTYgen. Each tool offers unique features and considerations:
ssh-keygen
- Comes pre-installed on most Linux and macOS systems.
- Generates keys in OpenSSH format, which is widely supported.
- Provides options for customizing key parameters, such as key size and type.
OpenSSL
- A versatile tool for generating keys in various formats, including SSH.
- Offers advanced options for controlling key generation algorithms and parameters.
- Requires manual configuration and may not be as user-friendly as other tools.
Third-Party Tools
- Provide user-friendly interfaces and additional features, such as key management and conversion.
- May be less widely supported than built-in tools.
- Example: PuTTYgen for Windows users.
Example of Key Generation
To generate an SSH public key using a recommended key size, follow these steps:
Using ssh-keygen
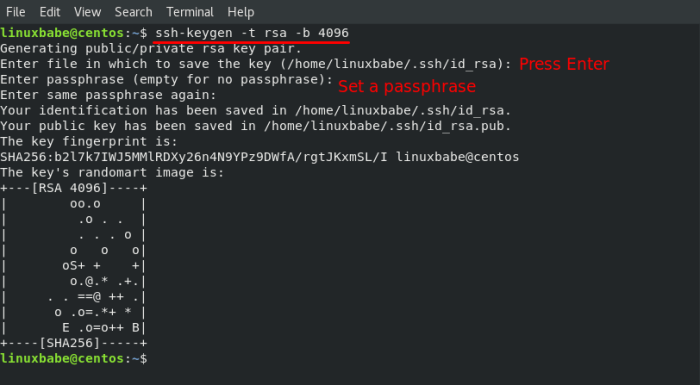
Use the ssh-keygen command with the -t option to specify the key type and the -b option to set the key size. For example, to generate a 4096-bit RSA key:
ssh-keygen -t rsa -b 4096
You will be prompted to enter a passphrase to protect the private key. Enter a strong passphrase and confirm it.
Using PuTTYgen (Windows)
Open PuTTYgen and select the “SSH-2 RSA” key type. In the “Number of bits in a generated key” field, enter the desired key size (e.g., 4096).
Click “Generate” and move the mouse cursor randomly over the blank area to generate entropy. Once the progress bar is complete, click “Save private key” to save the private key and “Save public key” to save the public key.
Conclusion
In summary, the appropriate public key size for an SSH server is crucial for maintaining robust security. Using a key that is too small can significantly compromise the security of your server, making it vulnerable to brute-force attacks and other malicious attempts.
It is essential to select a key size that balances security and computational efficiency. Following best practices for key management and utilizing tools for key generation can further enhance the security of your SSH server. Remember, a strong SSH server is a cornerstone of a secure network infrastructure.
Closing Summary
In conclusion, the size of your SSH server public key is a crucial factor in safeguarding your remote connections. By adhering to industry standards, implementing robust mitigation strategies, and practicing diligent key management, you can effectively mitigate the risks associated with small public keys.
Remember, a strong SSH infrastructure is the cornerstone of secure remote access, empowering you to confidently navigate the digital landscape.