In the realm of secure remote server access, SSH (Secure Shell) reigns supreme. Central to its security is the public key authentication mechanism, which hinges on the size of the public key. When an SSH server encounters a “Public Key Too Small” error, it raises concerns about the strength of the authentication process.
This comprehensive guide delves into the intricacies of SSH server public key size, empowering you to troubleshoot errors and enhance the security of your remote connections.
Public key size plays a crucial role in SSH security, as smaller keys are more susceptible to brute-force attacks. Understanding the recommended key sizes, potential error causes, and best practices for SSH public key management is paramount to ensuring robust server protection.
This guide will equip you with the knowledge and tools to effectively navigate the challenges of SSH public key authentication, safeguarding your servers from unauthorized access.
Understanding SSH Server Public Key Size Limitations
SSH public key size plays a crucial role in the security of SSH connections. A larger key size provides stronger encryption, making it more difficult for attackers to brute-force or decrypt the key. However, using an excessively large key can slow down the authentication process.
Recommended SSH Public Key Sizes
The minimum recommended key size for SSH servers is 2048 bits, which provides a good balance between security and performance. For even higher security, a key size of 4096 bits or higher is recommended, especially for critical servers or applications.
Common SSH Public Key Sizes and Their Strengths
Some common SSH public key sizes include:
1024 bits
This key size is considered insecure and should not be used.
2048 bits
This is the minimum recommended key size and provides a reasonable level of security.
4096 bits
This key size is stronger than 2048 bits and is recommended for high-security applications.
8192 bits
This key size is even stronger than 4096 bits, but it may slow down the authentication process.
Troubleshooting “Public Key Too Small” Errors
SSH servers impose size limitations on public keys for security reasons. Keys that fall below the minimum size may trigger a “Public Key Too Small” error, preventing successful authentication.
To resolve this issue, it is crucial to determine the root cause and take appropriate corrective actions.
Checking Public Key Size
- Use the following command to check the size of your public key:
ssh-keygen -l -f ~/.ssh/id_rsa.pub - Locate the “key_size” field in the output. A typical public key size is 2048 bits.
Generating a New SSH Public Key
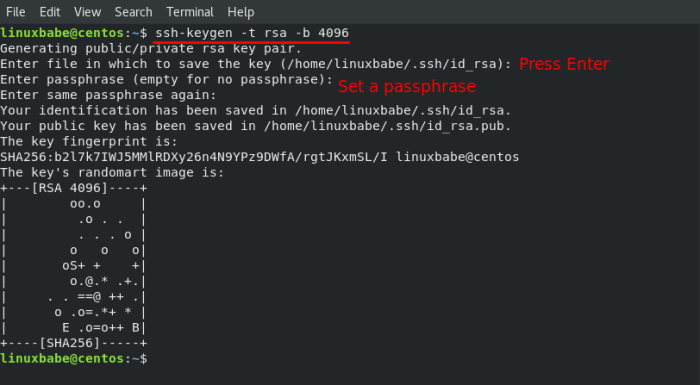
If your public key is too small, it is recommended to generate a new one with an appropriate size.
- Run the following command:
ssh-keygen -t rsa -b 4096 - Select a secure passphrase for your private key.
- Save the generated public and private key files in a secure location.
Best Practices for SSH Public Key Management
Implementing robust SSH public key management practices is crucial for maintaining a secure SSH environment. This involves utilizing strong and unique public keys, managing them through a centralized system, and securely storing and managing private keys.
Importance of Strong and Unique SSH Public Keys
Strong SSH public keys are essential to prevent brute-force attacks. Generating long and complex keys with sufficient entropy makes it computationally infeasible for attackers to guess or crack them. Additionally, using unique public keys for each server and user prevents attackers from compromising multiple systems with a single compromised key.
Benefits of Centralized SSH Key Management
Centralized key management systems provide a centralized repository for storing and managing SSH public keys. This simplifies key distribution, enables centralized access control, and facilitates key rotation and revocation. It also reduces the risk of unauthorized key additions or modifications.
Secure Storage and Management of SSH Private Keys
SSH private keys should be securely stored and managed to prevent unauthorized access. Best practices include storing keys in encrypted form, using strong passphrases, and limiting access to authorized users. Additionally, consider using hardware security modules (HSMs) or other secure key storage solutions to further enhance security.
4. Advanced SSH Configuration Options
To enhance the security and flexibility of SSH public key authentication, administrators can explore advanced configuration options available in SSH servers.
Configuring SSH Servers for Different Public Key Sizes
By default, SSH servers may have limitations on the size of public keys they accept. To accommodate keys of varying sizes, administrators can modify the MaxKeyBits option in the server configuration file (e.g., /etc/ssh/sshd_config ). Increasing this value allows the server to accept larger keys, while decreasing it restricts the size of accepted keys.
Using Wildcards and Key Restrictions
SSH servers support the use of wildcards in public key configuration. This enables administrators to define patterns for accepted keys, such as matching keys from a specific domain or organization. Additionally, key restrictions can be applied to further enhance security, such as limiting the number of keys allowed per user or enforcing specific key attributes.
5. Common SSH Tools and Utilities
SSH provides a range of tools and utilities to simplify the management of public keys. These tools offer intuitive and efficient ways to generate, manage, and utilize SSH keys, enhancing the security and convenience of remote access.
Key Generation and Management
- ssh-keygen: A versatile tool for generating SSH key pairs. It supports various key algorithms (e.g., RSA, DSA, ECDSA) and allows users to specify key size and other parameters.
- ssh-copy-id: Facilitates the secure copying of public keys to remote hosts. It prompts for the user’s password and automatically adds the public key to the authorized_keys file on the target server.
- ssh-add: Manages SSH keys stored in the local system’s SSH agent. It loads private keys into the agent’s memory, allowing users to access multiple remote servers without repeatedly entering passwords.
Practical Examples
- Generating a New SSH Key Pair:
“`
ssh-keygen
-t rsa
-b 4096
-C “[email protected]”
“` - Copying a Public Key to a Remote Server:
“`
ssh-copy-id [email protected]
“` - Loading a Private Key into the SSH Agent:
“`
ssh-add ~/.ssh/id_rsa
“`
6. Securing SSH Servers with Public Key Authentication
Public key authentication offers significant advantages over password-based authentication for SSH servers. It eliminates the risk of brute-force attacks and provides a more secure way to authenticate users.
Disabling Password-Based Authentication
To disable password-based authentication and configure SSH servers to rely solely on public key authentication, edit the SSH configuration file (usually located at /etc/ssh/sshd_config) and set the following options:
PasswordAuthentication noChallengeResponseAuthentication no
Recommendations for Protecting SSH Servers
In addition to disabling password-based authentication, consider the following recommendations to protect SSH servers from unauthorized access and potential attacks:
- Limit SSH Access: Restrict SSH access to authorized IP addresses or subnets using the
AllowUsersandDenyUsersdirectives in the SSH configuration file. - Use Strong Public Keys: Generate strong public keys using a key length of at least 2048 bits. Avoid using weak or compromised keys.
- Enable Two-Factor Authentication: Implement two-factor authentication mechanisms such as Google Authenticator or SMS-based OTPs to add an extra layer of security.
- Regularly Update SSH Software: Keep SSH software up-to-date to patch security vulnerabilities and prevent potential exploits.
7. Case Studies and Success Stories

SSH public key authentication has been widely adopted by organizations worldwide. Here are a few real-world examples of its successful implementation:
Google Cloud Platform
Google Cloud Platform (GCP) offers a managed SSH service that allows users to securely access their virtual machines (VMs) using public key authentication. GCP’s SSH service provides a number of benefits, including:
- Centralized key management
- Automatic key rotation
- Support for multiple key types
GCP’s SSH service has been used by a number of organizations to improve the security of their cloud infrastructure. For example, Dropbox uses GCP’s SSH service to manage access to its production VMs. Dropbox has found that GCP’s SSH service has helped them to reduce the risk of unauthorized access to their VMs and has improved their overall security posture.
Amazon Web Services
Amazon Web Services (AWS) also offers a managed SSH service that allows users to securely access their EC2 instances using public key authentication. AWS’s SSH service provides a number of benefits, including:
- Support for multiple key types
- Automatic key rotation
- Integration with AWS Identity and Access Management (IAM)
AWS’s SSH service has been used by a number of organizations to improve the security of their cloud infrastructure. For example, Netflix uses AWS’s SSH service to manage access to its production EC2 instances. Netflix has found that AWS’s SSH service has helped them to reduce the risk of unauthorized access to their EC2 instances and has improved their overall security posture.
Frequently Asked Questions (FAQs)
This section addresses common questions and concerns related to SSH server public key size and management, providing clear and concise answers.
Key Size Recommendations
- RSA keys: 4096 bits or higher
- DSA keys: 2048 bits or higher
- ECDSA keys: 256 bits or higher
Troubleshooting “Public Key Too Small” Errors
- Ensure that the public key being used meets the minimum size requirements.
- Check the SSH server configuration to verify the minimum key size allowed.
- Consider regenerating a new public key with an appropriate size.
Best Practices for SSH Public Key Management
- Use strong and unique passphrases to protect private keys.
- Store private keys securely, preferably in an encrypted password manager.
- Regularly review and update public keys to ensure they remain secure.
Additional Resources
- SSH.com: Public Key Authentication
- OpenSSL: ssh-keygen Manual
- DigitalOcean: How To Manage SSH Keys on a VPS
9. Glossary of Terms
To enhance understanding of SSH public key authentication, it’s essential to define and explain key terms and concepts. Here’s a comprehensive glossary to clarify the technical jargon and terminology:
Public Key
- A cryptographic key used to encrypt data that can only be decrypted by the corresponding private key.
- In SSH, public keys are used to authenticate users without requiring them to share their private keys.
Private Key
- A cryptographic key used to decrypt data that has been encrypted with the corresponding public key.
- Private keys must be kept secret and secure to prevent unauthorized access to accounts.
Key Pair
- A set of two mathematically linked keys consisting of a public key and a private key.
- The public key is shared with others, while the private key is kept secret.
SSH Agent
- A software component that manages SSH keys and provides them to SSH clients when needed.
- SSH agents allow users to avoid manually entering their private key passphrase for each authentication attempt.
SSH Key Manager
- A tool or service used to generate, manage, and store SSH keys securely.
- Key managers can simplify the process of creating and using SSH keys and provide additional security features.
Passphrase
- A secret phrase used to encrypt and decrypt a private key.
- Passphrases add an extra layer of security to SSH keys and should be chosen carefully.
SSH Config File
- A configuration file that specifies various settings for SSH clients and servers.
- The SSH config file can be used to set options such as the default SSH port, preferred authentication methods, and key locations.
SSH Key Fingerprint
- A unique identifier for an SSH public key that can be used to verify its authenticity.
- Key fingerprints are typically displayed in hexadecimal format.
SSH Certificate
- A digital certificate that binds an SSH public key to a specific user or host.
- SSH certificates provide additional assurance of the identity of the key holder.
Additional Resources

To further enhance your understanding of SSH public key authentication and best practices, we recommend exploring the following resources:
Online Articles and Tutorials
[SSH Public Key Authentication
A Comprehensive Guide](https://www.digitalocean.com/community/tutorials/ssh-public-key-authentication-a-comprehensive-guide)
[Troubleshooting SSH Public Key Errors](https
//www.ssh.com/academy/ssh/troubleshooting/public-key-errors)
[Best Practices for SSH Public Key Management](https
//www.unixmen.com/best-practices-for-ssh-public-key-management/)
Documentation and White Papers
[OpenSSH Public Key Authentication](https
//man.openbsd.org/OpenSSH_7.6p1/ssh-keygen.1)
[SSH Public Key Infrastructure (PKI)](https
//www.ietf.org/rfc/rfc4250.txt)
[SSH Public Key Authentication Best Practices](https
//www.cisco.com/c/en/us/td/docs/security/security_management/ssh/public_key_authentication_best_practices.html)
Community Forums and Support
[SSH Public Key Authentication on Unix & Linux Stack Exchange](https
//unix.stackexchange.com/questions/tagged/ssh-key)
[SSH Public Key Authentication on Server Fault](https
//serverfault.com/questions/tagged/ssh-key)
[SSH Public Key Authentication on Reddit](https
//www.reddit.com/r/linux/search?q=ssh+public+key&restrict_sr=on&sort=relevance&t=all)By exploring these resources, you can stay informed and expand your knowledge on SSH public key authentication, ensuring the security and efficiency of your remote connections.
Last Point
SSH public key authentication offers a robust and convenient method of securing remote server access. By adhering to recommended key sizes, implementing strong key management practices, and leveraging advanced SSH configuration options, you can effectively mitigate security risks and ensure the integrity of your servers.
Remember, the key to secure SSH connections lies in understanding the intricacies of public key authentication and implementing best practices. Embrace the knowledge imparted in this guide to empower yourself and safeguard your remote server infrastructure.