ssh.sshslowdns.com – Welcome to the realm of SSH (Secure Shell), a vital tool for secure remote access and server management. In this guide, we will embark on a journey to enable SSH server on Ubuntu 22.04, empowering you with the knowledge and skills to connect to your systems remotely, securely, and efficiently.
SSH is a powerful protocol that allows you to establish encrypted connections between two computers, enabling you to execute commands, transfer files, and manage systems from the comfort of your local machine. By enabling SSH on your Ubuntu 22.04 system, you unlock a world of possibilities for remote administration, troubleshooting, and collaboration.
Installing OpenSSH Server

OpenSSH is a powerful tool that allows you to securely connect to and manage your Ubuntu system remotely. It provides a secure channel for data transfer and remote command execution, making it essential for system administrators and developers.
Installing OpenSSH on Ubuntu 22.04 is a straightforward process. Here’s how you can do it:
Installation Steps
-
- Update your system’s package index:
sudo apt update -
- Install the OpenSSH server package:
sudo apt install openssh-server -
- Enable the SSH service to start automatically on boot:
sudo systemctl enable ssh -
- Start the SSH service:
sudo systemctl start ssh Configuring SSH Server
SSH (Secure Shell) is a protocol used for secure remote login and command execution over an unsecured network.
It provides a secure channel for data transmission, preventing unauthorized access and eavesdropping. To configure the SSH server, you can edit the SSH configuration file, typically located at /etc/ssh/sshd_config.
Securing SSH Configuration
Securing the SSH configuration is crucial to prevent unauthorized access and potential security breaches. Some important security considerations include:
- Use strong passwords or keys: Avoid using weak or easily guessable passwords. Instead, use strong passwords or SSH keys to authenticate users.
- Disable root login: By default, root login is enabled. Disable root login and create a separate user account with administrative privileges to enhance security.
- Limit access to specific users: Restrict SSH access to only authorized users or groups by specifying them in the configuration file.
- Configure firewall rules: Implement firewall rules to restrict SSH access to specific IP addresses or ranges, preventing unauthorized access from outside networks.
Common SSH Configuration Options
The SSH configuration file contains various options that control the behavior of the SSH server. Some common options include:
- Port: Specifies the port number on which the SSH server listens for incoming connections. The default port is 22.
- Protocol: Specifies the SSH protocol version to be used. SSHv2 is the recommended and more secure version.
- Ciphers: Defines the encryption algorithms used to protect data transmitted over the SSH connection.
- MACs: Specifies the message authentication code algorithms used to ensure the integrity of data transmitted over the SSH connection.
- PermitRootLogin: Controls whether root login is allowed. Setting it to “no” disables root login.
- AllowUsers: Restricts SSH access to specified users or groups.
By carefully configuring these options, you can enhance the security of your SSH server and protect against unauthorized access.
Enabling SSH Server
To enable the SSH server on Ubuntu 22.04, we’ll use the systemctl command, a powerful tool for managing system services.
Systemctl allows us to start, stop, enable, and disable services, including SSH. By enabling the SSH service, we ensure it automatically starts at boot time, allowing remote connections.
Enabling SSH Server
- Open a terminal window.
- Run the following command:
sudo systemctl enable ssh
- This command creates a symbolic link in the /etc/systemd/system/multi-user.target.wants/ directory, ensuring SSH is started automatically at boot time.
If you encounter any issues enabling SSH, try the following troubleshooting tips:
- Ensure you have superuser privileges (use sudo).
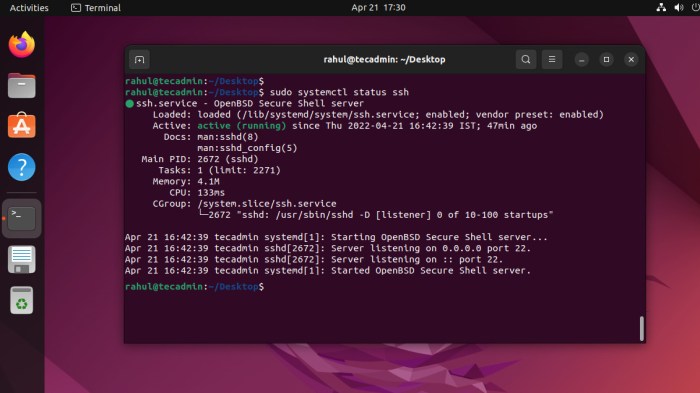
- Check if the SSH service is running: sudo systemctl status ssh
- If the service is not running, try starting it manually: sudo systemctl start ssh
Verifying SSH Server Status
Verifying the status of your SSH server is crucial for ensuring its proper functioning and maintaining security. SSH, or Secure Shell, is a protocol that allows secure remote access to a server over an encrypted connection. Monitoring the status of your SSH server helps you identify any issues or potential vulnerabilities, enabling you to take prompt action.
Using systemctl
The systemctl command provides a convenient way to check the status of SSH. Run the following command:“`systemctl status sshd“`This command will display the current status of the SSH server, including whether it is active, inactive, or disabled.
Using ss
The ss command can also be used to verify the status of SSH. Run the following command:“`ss
an | grep ssh
“`This command will list all active network connections, including those established by SSH. Look for the line that starts with “LISTEN” and has a port number of 22. If you see this line, it indicates that the SSH server is listening for incoming connections and is active.
Importance of Monitoring SSH Server Status
Monitoring the status of your SSH server is essential for several reasons:*
-*Security
SSH is a critical service that allows remote access to your server. By monitoring its status, you can quickly identify any unauthorized access attempts or security breaches.
-
- -*Maintenance
Knowing the status of your SSH server helps you plan for maintenance activities, such as software updates or hardware upgrades.
- -*Maintenance
-*Troubleshooting
If you encounter any issues with remote access or SSH connectivity, checking the status of the SSH server can help you identify the root cause and resolve the problem promptly.
Configuring Firewall for SSH
To enhance the security of your Ubuntu 22.04 system, it’s crucial to configure the firewall to allow SSH connections while restricting unauthorized access.
The firewall acts as a barrier, monitoring and controlling incoming and outgoing network traffic based on a set of rules.
Allowing SSH Traffic
By default, the firewall in Ubuntu 22.04 blocks all incoming connections, including SSH. To allow SSH traffic, you need to add a firewall rule that explicitly permits connections on port 22, the standard port for SSH.
Open the terminal and execute the following command:
sudo ufw allow 22
This command adds a rule to the firewall that allows incoming connections on port 22 from any IP address.
Restricting SSH Access
To further enhance security, you can restrict SSH access to specific IP addresses or subnets. This prevents unauthorized users from connecting to your system from unknown locations.
To restrict SSH access, add a rule that allows connections only from a specific IP address or subnet:
sudo ufw allow from 192.168.1.100 to any port 22
Replace “192.168.1.100” with the IP address or subnet you want to allow.
Managing SSH Keys
In the realm of secure remote access, SSH keys play a pivotal role in safeguarding connections between systems. These cryptographic keys provide a robust alternative to traditional password-based authentication, offering enhanced security and convenience.
SSH keys come in pairs: a public key and a private key. The public key is shared with the remote system, while the private key remains confidential on the local system. During an SSH connection, the remote system uses the public key to encrypt a message, which can only be decrypted using the corresponding private key.
This intricate mechanism ensures that only the holder of the private key can establish a connection, effectively thwarting unauthorized access.
Generating SSH Keys
Generating an SSH key pair is a straightforward process. On most Linux systems, you can use the ssh-keygen command. Simply run the command in a terminal and follow the prompts to specify the type of key (RSA or DSA), the key size (typically 2048 bits), and the location where the keys should be stored.
Once generated, the public key will be saved with a .pub extension, while the private key will have no extension. The public key can be shared with the remote system, while the private key should be kept secret.
Managing SSH Keys
Managing SSH keys involves keeping track of your public and private keys, revoking access to compromised keys, and adding new keys when necessary. To manage your keys, you can use the ssh-add and ssh-keygen commands. ssh-add allows you to add your private key to the SSH agent, which enables you to use the key without entering the passphrase each time you connect to a remote system.
To revoke access to a compromised key, you can use the ssh-keygen command with the -f option to remove the key from the system. To add a new key, simply follow the steps Artikeld in the “Generating SSH Keys” section.
Best Practices for Managing SSH Keys
- Use strong passphrases for your private keys.
- Keep your private keys secure and do not share them with anyone.
- Regularly check your SSH keys for any unauthorized changes.
- Revoke access to compromised keys immediately.
- Consider using a key management tool to simplify the process of managing multiple SSH keys.
Troubleshooting SSH Connection Issues
Encountering difficulties connecting to an SSH server? Here’s a comprehensive guide to troubleshoot common issues and establish a successful connection.
SSH connection failures can stem from various reasons, including incorrect configurations, firewall restrictions, or authentication problems. Understanding the underlying causes and implementing appropriate solutions can resolve these issues swiftly.
Identifying Common Error Messages
- “Connection refused”: The SSH server is not running or is not listening on the specified port.
- “Connection timed out”: The SSH client could not establish a connection within the specified timeout period.
- “Permission denied (publickey)”: The SSH client’s public key is not authorized to access the server.
- “Bad owner or permissions on ~/.ssh/authorized_keys”: The permissions or ownership of the authorized_keys file are incorrect.
Advanced SSH Configuration
To further customize and enhance the security of your SSH server, you can delve into advanced configuration options. These options allow you to fine-tune the server’s behavior, optimize performance, and implement additional security measures.
The primary configuration file for SSH is typically located at /etc/ssh/sshd_config. This file contains a comprehensive list of settings that control various aspects of the SSH server.
SSH Configuration File
The SSH configuration file is divided into sections, each representing a specific aspect of the server’s behavior. Some of the commonly used sections include:
- GlobalConfiguration: Contains global settings that apply to all SSH connections.
- Match: Allows you to specify configuration options based on specific criteria, such as the client’s IP address or username.
- Host: Defines settings specific to a particular host or group of hosts.
Advanced Configuration Options
Among the numerous advanced configuration options available, some of the most useful include:
- Port: Specifies the port on which the SSH server listens for incoming connections. Changing the default port can enhance security by making it harder for attackers to target the server.
- Protocol: Configures the SSH protocol version to be used. By default, SSHv2 is recommended for improved security and performance.
- Ciphers: Defines the encryption algorithms used to protect data transmitted over the SSH connection. Stronger ciphers provide higher levels of encryption, but may impact performance.
- MACs: Specifies the message authentication code algorithms used to ensure the integrity of data transmitted over the SSH connection.
- Key Exchange Algorithms: Configures the algorithms used to establish a secure connection between the client and server. Stronger algorithms provide better security, but may be computationally intensive.
Benefits of Advanced Configuration
Implementing advanced SSH configuration options can provide several benefits, including:
- Enhanced Security: By customizing SSH settings, you can strengthen the server’s security posture and mitigate potential vulnerabilities.
- Improved Performance: Fine-tuning SSH configuration can optimize performance by selecting appropriate algorithms and settings.
- Compliance: Advanced configuration allows you to align the SSH server with industry best practices and security standards.
Securing SSH Server
SSH, or Secure Shell, is a secure network protocol that allows for remote login and command execution. Securing the SSH server is crucial to protect against unauthorized access and potential attacks. Here are some best practices to enhance SSH security on Ubuntu 22.04:
Strong Passwords and Limiting Login Attempts
Use strong and unique passwords for SSH accounts. Consider implementing password policies that enforce minimum length, complexity, and expiration. Additionally, limit the number of failed login attempts to prevent brute-force attacks.
Two-Factor Authentication
Enable two-factor authentication (2FA) to add an extra layer of security. This requires users to provide a second form of verification, such as a one-time password or hardware token, in addition to their password.
Monitoring SSH Logs
Monitor SSH logs regularly to detect any suspicious activity. Review logs for failed login attempts, unusual commands, or any other anomalies. Consider using tools like Logwatch or Fail2ban to automate log monitoring and respond to suspicious events.
Intrusion Detection Systems
Implement an intrusion detection system (IDS) to detect and respond to potential threats. IDS can monitor network traffic, analyze logs, and identify patterns that may indicate an attack.
Disable Root Login
Disable root login via SSH to prevent attackers from exploiting potential vulnerabilities in the root account. Instead, create a separate user account with administrative privileges for SSH access.
Use SSH Keys
Utilize SSH keys for authentication instead of passwords. SSH keys provide a more secure and convenient way to log in without the need to enter a password. Generate a key pair, add the public key to the authorized_keys file on the server, and keep the private key secure.
Keep SSH Software Updated
Regularly update the SSH server software to address any security vulnerabilities or performance improvements. Install security patches and updates promptly to maintain a secure configuration.
SSH Best Practices
SSH offers a secure and versatile protocol for remote access. By implementing best practices, you can enhance the security and efficiency of your SSH connections.
Some key best practices for using SSH effectively include:
Using SSH Tunneling
SSH tunneling allows you to establish secure connections over insecure networks. It creates an encrypted channel through which data can be transmitted securely. SSH tunneling can be useful for accessing services that are only available on specific ports or for bypassing firewalls.
Port Forwarding
Port forwarding allows you to redirect traffic from one port to another. This can be useful for accessing services that are running on a different port than the default port.
Compression
SSH supports compression to reduce the size of data transmitted over the network. This can improve performance, especially over slow or unreliable networks.
Optimizing Performance
There are several ways to optimize SSH performance, including:
- Using a fast encryption algorithm (e.g., AES-256-GCM)
- Disabling unnecessary features (e.g., X11 forwarding)
- Tuning SSH configuration parameters (e.g., packet size)
Enhancing User Experience
There are several ways to enhance the user experience when using SSH, including: