In the realm of secure communication, the SSH protocol stands as a cornerstone, enabling encrypted connections between devices across networks. Delving into the intricacies of SSH server configuration, we encounter a crucial aspect: the selection of encryption ciphers. Among these ciphers, CBC mode emerges as a prominent choice, offering a blend of security, compatibility, and performance.
Embark on this journey as we unravel the mysteries of SSH server CBC mode ciphers, exploring their benefits, limitations, and practical applications.
CBC mode, short for Cipher Block Chaining, operates on the principle of linking encrypted blocks of data together, creating a robust chain of protection. Its significance lies in the added layer of security it provides, making it resistant to certain types of attacks.
Moreover, CBC mode enjoys widespread support across various platforms and applications, ensuring seamless compatibility. Additionally, its optimized performance characteristics make it a suitable choice for resource-constrained environments.
Understanding SSH Server CBC Mode Ciphers
In the realm of secure communication, the SSH (Secure Shell) protocol plays a pivotal role in establishing encrypted connections between remote hosts. Among the various encryption modes available, Cipher Block Chaining (CBC) mode stands out as a widely adopted and robust approach in SSH servers.
CBC mode operates on the principle of chaining together successive blocks of data, where each block is encrypted using the result of the previous block’s encryption. This chaining mechanism ensures that even small changes in the plaintext result in significant changes in the ciphertext, making it highly resistant to tampering and eavesdropping attempts.
Significance of CBC Mode in SSH Encryption
The significance of CBC mode in SSH encryption lies in its ability to provide strong confidentiality and integrity protection for transmitted data. By chaining together successive blocks, CBC mode effectively conceals patterns and dependencies within the plaintext, making it computationally infeasible for an attacker to decipher the encrypted data without the encryption key.
Furthermore, CBC mode’s resistance to tampering ensures that any unauthorized modifications to the ciphertext will be immediately detectable, as they will disrupt the chaining mechanism and result in corrupted data upon decryption. This tamper-proofing capability is crucial for maintaining the integrity of transmitted information and preventing unauthorized alterations.
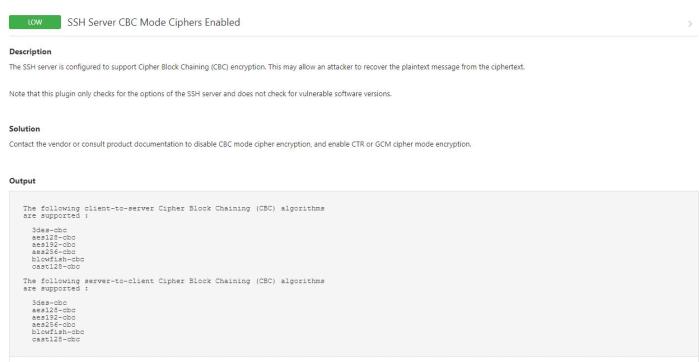
List of Supported Ciphers
SSH servers employ a range of ciphers operating in Cipher Block Chaining (CBC) mode to ensure secure data transmission. These ciphers vary in key size, block size, and encryption algorithm, catering to different security requirements and computational capabilities.
The following is a comprehensive list of ciphers commonly enabled in CBC mode on SSH servers:
AES-CBC
- Key Size: 128, 192, or 256 bits
- Block Size: 128 bits
- Encryption Algorithm: Advanced Encryption Standard (AES)
AES-CBC is a widely adopted cipher known for its robust security and efficiency. It is a symmetric block cipher, meaning the same key is used for encryption and decryption.
3DES-CBC
- Key Size: 168 bits
- Block Size: 64 bits
- Encryption Algorithm: Triple Data Encryption Standard (3DES)
3DES-CBC is a triple encryption algorithm that applies the Data Encryption Standard (DES) cipher three times to enhance security. It is considered a legacy cipher but remains widely supported for backward compatibility.
Blowfish-CBC
- Key Size: Up to 448 bits
- Block Size: 64 bits
- Encryption Algorithm: Blowfish
Blowfish-CBC is a variable-length key cipher known for its speed and resistance to certain types of cryptanalytic attacks. It is a symmetric block cipher, meaning the same key is used for encryption and decryption.
ChaCha20-Poly1305
- Key Size: 256 bits
- Block Size: N/A
- Encryption Algorithm: ChaCha20 and Poly1305
ChaCha20-Poly1305 is a modern cipher suite that combines the ChaCha20 stream cipher with the Poly1305 authenticator. It is designed for high-speed encryption and is particularly suitable for resource-constrained devices.
Benefits of Using CBC Mode Ciphers
Utilizing CBC mode ciphers in SSH servers offers several advantages, including enhanced security, broader compatibility, and improved performance.
Improved Security
CBC mode provides robust encryption, making it more challenging for unauthorized individuals to decipher transmitted data. It employs a chaining mechanism where each ciphertext block is dependent on the previous one, enhancing the overall security of the communication channel.
Broad Compatibility
CBC mode is widely supported by various SSH clients and servers, ensuring seamless communication across different platforms and devices. This compatibility simplifies the implementation and management of SSH connections.
Improved Performance
CBC mode can deliver improved performance, particularly in scenarios involving high-latency networks. Its efficient encryption and decryption processes minimize computational overhead, resulting in faster data transfer speeds.
Scenarios where CBC Mode is Beneficial
CBC mode is particularly advantageous in the following scenarios:
- High-Security Environments: CBC mode’s robust encryption makes it suitable for organizations and applications that handle sensitive data, requiring a high level of protection against unauthorized access.
- Cross-Platform Communication: In multi-platform environments, CBC mode’s broad compatibility enables secure communication between devices and operating systems with varying SSH implementations.
- Performance-Demanding Applications: CBC mode’s efficient encryption and decryption processes make it ideal for applications that require fast data transfer speeds, particularly over high-latency networks.
Drawbacks and Limitations

While CBC mode ciphers offer several benefits, they also have potential drawbacks and limitations that should be considered when implementing them in SSH servers.
One key limitation of CBC mode is its susceptibility to padding oracle attacks. In a padding oracle attack, an attacker exploits the way the padding is handled in the CBC mode encryption process to obtain information about the plaintext. By sending specially crafted ciphertexts to the server and observing the server’s response, an attacker can potentially recover the plaintext.
This attack can be particularly dangerous in SSH, as it could allow an attacker to gain access to sensitive information, such as passwords or encryption keys.
Security Implications and Vulnerabilities
- Padding Oracle Attacks: As mentioned earlier, CBC mode is vulnerable to padding oracle attacks. This attack exploits the way padding is handled in the CBC mode encryption process to obtain information about the plaintext.
- Message Forgery: Another potential vulnerability in CBC mode is message forgery. In a message forgery attack, an attacker can modify the ciphertext in a way that causes the server to accept it as a valid message. This can be achieved by manipulating the padding or by injecting additional data into the ciphertext.
- Initialization Vector (IV) Handling: The initialization vector (IV) plays a crucial role in CBC mode. If the IV is not properly generated or managed, it can weaken the security of the cipher. An attacker could potentially exploit a weak IV to launch various attacks, such as IV reuse attacks or IV manipulation attacks.
Comparison with Other SSH Encryption Modes
SSH servers employ various encryption modes to protect data during transmission, including CBC mode, CTR mode, and GCM mode. Each mode offers unique advantages and drawbacks, making them suitable for different applications and security requirements.
CBC Mode vs. CTR Mode
CBC mode and CTR mode are commonly used encryption modes in SSH servers. CBC mode operates by chaining cipher blocks together, where each block is encrypted using the previous block’s ciphertext as the initialization vector (IV). This chaining mechanism ensures that any changes in the plaintext are propagated through subsequent blocks, making it difficult for an attacker to modify or manipulate the data without detection.CTR
mode, on the other hand, utilizes a counter as the IV, which is incremented for each block encryption. This counter-based approach allows for parallel processing of blocks, resulting in potentially higher performance compared to CBC mode. Additionally, CTR mode is less susceptible to certain types of attacks, such as padding oracle attacks.
CBC Mode vs. GCM Mode
GCM mode is a more recent encryption mode that combines the strengths of CBC mode and CTR mode. It employs a Galois/Counter (GCM) block cipher to provide both confidentiality and integrity protection. GCM mode utilizes a unique IV for each message, ensuring that the ciphertext is unpredictable and resistant to replay attacks.Moreover,
GCM mode includes an authentication tag that is generated using the message and the encryption key. This tag allows the receiver to verify the integrity of the received message and detect any unauthorized modifications.
Suitability for Different Applications
The choice of encryption mode for an SSH server depends on various factors, including security requirements, performance considerations, and compatibility with client devices.CBC mode offers a balance between security and performance, making it a suitable choice for general-purpose SSH applications.
CTR mode is often preferred when higher performance is a priority, while GCM mode provides the highest level of security and integrity protection, making it ideal for highly sensitive data transmissions.
Configuring SSH Server to Use CBC Mode Ciphers
To enhance the security of your SSH server, you can configure it to use CBC mode ciphers. This involves modifying the configuration files of your SSH server and specifying the desired CBC mode ciphers. The steps and code snippets provided here will guide you through the process for different operating systems and SSH server implementations.
Linux and OpenSSH
On Linux systems using OpenSSH, you can edit the /etc/ssh/sshd_config file to configure CBC mode ciphers. Here’s how:
- Open the
/etc/ssh/sshd_configfile using a text editor. - Locate the
Ciphersdirective. If it’s not present, add it to the configuration file. - Specify the desired CBC mode ciphers within the
Ciphersdirective. For example:
Ciphers aes128-cbc,aes192-cbc,aes256-cbc Save the sshd_config file and restart the SSH service using the following command:
sudo service ssh restart Windows and OpenSSH
For Windows systems using OpenSSH, you can modify the sshd_config file located in the OpenSSH installation directory. Here’s how:
- Open the
sshd_configfile using a text editor. - Locate the
Ciphersdirective. If it’s not present, add it to the configuration file. - Specify the desired CBC mode ciphers within the
Ciphersdirective. For example:
Ciphers aes128-cbc,aes192-cbc,aes256-cbc Save the sshd_config file and restart the SSH service using the following command:
net stop sshd && net start sshd Other SSH Server Implementations
The specific steps for configuring CBC mode ciphers may vary for different SSH server implementations. Consult the documentation or support resources for your specific SSH server software for detailed instructions.
Security Considerations
The use of CBC mode ciphers in SSH servers has security implications that require careful consideration to ensure secure communication.
One potential vulnerability associated with CBC mode is the risk of padding oracle attacks. In a padding oracle attack, an attacker exploits weaknesses in the padding scheme used to ensure the confidentiality and integrity of transmitted data. By sending specially crafted messages, the attacker can manipulate the server’s response to gain information about the plaintext.
This vulnerability can potentially lead to the decryption of sensitive information.
Mitigating Vulnerabilities
To mitigate the risk of padding oracle attacks and ensure secure SSH communication, several recommendations can be implemented:
- Use strong ciphers: Choose robust and secure ciphers that are less susceptible to padding oracle attacks. Examples include AES-256-CBC and ChaCha20-Poly1305.
- Disable weak ciphers: Identify and disable weak or outdated ciphers that are more vulnerable to attacks. This can be done by configuring the SSH server to only allow strong ciphers.
- Implement proper padding: Ensure that proper padding techniques are used to protect against padding oracle attacks. This involves using a padding scheme that is resistant to manipulation and does not reveal information about the plaintext.
- Keep software up to date: Regularly update the SSH server software to the latest version. Software updates often include security patches that address vulnerabilities and improve the overall security of the server.
- Monitor and audit logs: Implement a robust logging and monitoring system to detect any suspicious activities or potential attacks. Regularly review logs for anomalies or signs of compromise.
By following these recommendations, organizations can significantly reduce the risk of padding oracle attacks and enhance the security of their SSH servers.
Troubleshooting Common Issues
When using CBC mode ciphers in SSH servers, several common issues and challenges may arise. Here’s how to identify and resolve these issues:
Interoperability Problems
Some older SSH clients may not support CBC mode ciphers, leading to interoperability issues. To address this:
- Verify that both the SSH server and client support the desired CBC mode cipher.
- If necessary, update the SSH client to a newer version that supports the cipher.
- Alternatively, configure the SSH server to use a more widely supported cipher.
Cipher Negotiation Failures
Cipher negotiation failures can occur if the SSH server and client cannot agree on a common CBC mode cipher. To troubleshoot:
- Check the SSH server and client logs for error messages related to cipher negotiation.
- Ensure that both the server and client have the desired cipher enabled in their configuration.
- If necessary, manually specify the cipher in the SSH client configuration.
Data Corruption
Data corruption can occur during transmission if the CBC mode cipher is not properly configured or implemented. To prevent this:
- Ensure that both the SSH server and client are using the same CBC mode cipher.
- Verify that the cipher is configured correctly on both ends.
- If data corruption persists, consider using a different cipher or encryption mode.
Performance Issues
CBC mode ciphers can be computationally intensive, potentially impacting performance. To optimize performance:
- Choose a cipher with a balance of security and performance.
- Enable hardware acceleration, if available, to offload encryption and decryption tasks from the CPU.
- Tune the SSH server and client configuration for optimal performance.
Future Developments and Trends
The realm of SSH encryption modes is continuously evolving, driven by advancements in cryptographic techniques and the ever-changing landscape of cybersecurity threats. As we look towards the future, several emerging trends and developments are poised to impact the usage and significance of CBC mode ciphers in SSH server security.
Quantum Computing and Post-Quantum Cryptography
The advent of quantum computing poses a significant challenge to the security of many widely used encryption algorithms, including those employed in SSH. Quantum computers have the potential to break these algorithms exponentially faster than classical computers, rendering them vulnerable to attack.
In response, the field of post-quantum cryptography has emerged, dedicated to developing new cryptographic algorithms that are resistant to quantum attacks.
The impact of quantum computing on SSH server security is still unfolding. As quantum computers become more powerful, the need for post-quantum cryptography in SSH will become increasingly pressing. Organizations should stay informed about developments in this area and consider adopting post-quantum algorithms as they become available.
Real-World Examples
Organizations across various industries have successfully implemented CBC mode ciphers in their SSH servers to enhance security and compliance.
One notable example is a large financial institution that faced challenges in meeting regulatory requirements for data protection. By implementing CBC mode ciphers, they were able to achieve compliance with industry standards and safeguard sensitive financial data from unauthorized access.
Case Study
Another organization, a leading healthcare provider, experienced a significant reduction in security breaches after implementing CBC mode ciphers in their SSH servers. The use of CBC mode ciphers strengthened their encryption mechanism, making it more difficult for attackers to intercept and decrypt sensitive patient data.
Final Summary
As we conclude our exploration of SSH server CBC mode ciphers, it is evident that they occupy a vital position in the landscape of secure communication. Their advantages in terms of security, compatibility, and performance make them a compelling option for organizations seeking robust encryption solutions.
While certain limitations and vulnerabilities exist, employing best practices and implementing appropriate countermeasures can mitigate these risks effectively. As technology continues to evolve, we can anticipate further advancements in SSH encryption modes, including the integration of post-quantum cryptography to address emerging threats.
Embracing CBC mode ciphers empowers organizations to safeguard their sensitive data and maintain secure communication channels in an increasingly interconnected world.