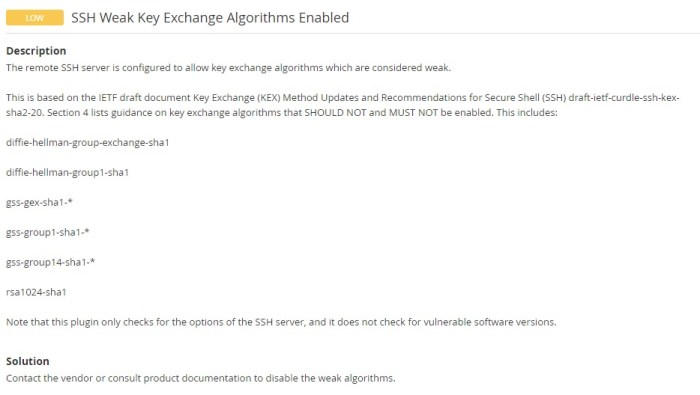
In the realm of secure remote access, SSH (Secure Shell) stands as a pivotal protocol. To further bolster its security posture, enabling CBC (Cipher Block Chaining) mode ciphers on SSH servers has emerged as a crucial practice. This article delves into the intricacies of SSH server CBC mode ciphers, exploring their benefits, implications, and best practices.
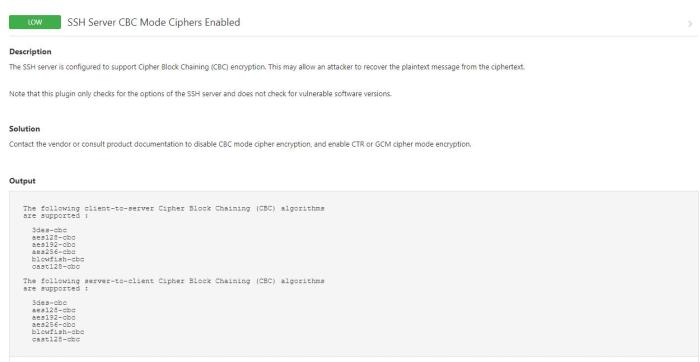
CBC mode ciphers provide an additional layer of protection by encrypting data in blocks, where each block is dependent on the previous one. This encryption technique enhances data confidentiality and integrity, making it more resistant to certain types of attacks.
SSH Server Configuration
SSH (Secure Shell) is a cryptographic network protocol that allows for secure data communication over an unsecured network. By default, SSH servers disable CBC mode ciphers due to security concerns. However, in certain scenarios, enabling CBC mode ciphers may be necessary to ensure compatibility with legacy clients or to support specific use cases.
To enable CBC mode ciphers on an SSH server, you can modify the server’s configuration file (typically named “sshd_config”) and add the following line:
Ciphers aes128-cbc,aes192-cbc,aes256-cbc
This line specifies that the server should allow the use of the AES-128, AES-192, and AES-256 ciphers in CBC mode. Once the configuration file is modified, the changes can be applied by restarting the SSH server.
Benefits of Using CBC Mode Ciphers in SSH
CBC (Cipher Block Chaining) mode is a block cipher mode of operation that provides confidentiality and integrity for data transmitted over a network. By using CBC mode, the server encrypts each block of data using a key and the previous block’s ciphertext, making it more difficult for an attacker to intercept and decipher the data.
Some of the benefits of using CBC mode ciphers in SSH include:
- Improved confidentiality: CBC mode provides stronger confidentiality compared to other modes of operation, such as ECB (Electronic Codebook Mode), as it encrypts each block of data using a unique key and the previous block’s ciphertext.
- Increased integrity: CBC mode also provides integrity protection for data, as any changes to the data will result in a different ciphertext, making it easier to detect tampering.
- Legacy compatibility: Enabling CBC mode ciphers can ensure compatibility with legacy SSH clients that may not support newer modes of operation.
Potential Security Implications of Enabling CBC Mode Ciphers
While CBC mode provides certain benefits, it also has some potential security implications that should be considered:
- Vulnerability to padding oracle attacks: CBC mode is vulnerable to padding oracle attacks, which can allow an attacker to recover plaintext data by exploiting the way the server handles padding in the ciphertext.
- Susceptibility to block size manipulation: CBC mode is susceptible to block size manipulation attacks, where an attacker can manipulate the block size to gain unauthorized access to data.
Due to these security concerns, it is generally recommended to use more secure modes of operation, such as GCM (Galois/Counter Mode), which provide stronger protection against these types of attacks.
Cipher Negotiation
In SSH, cipher negotiation is the process of establishing a mutually acceptable cipher algorithm to secure the communication channel. It involves a series of exchanges between the client and the server.
The server advertises a list of supported ciphers, and the client selects the strongest cipher that it also supports. CBC mode ciphers are commonly used in SSH due to their ability to protect against certain types of attacks, such as padding oracle attacks.
Common CBC Mode Ciphers in SSH
- AES-256-CBC
- AES-192-CBC
- AES-128-CBC
- 3DES-CBC
- Blowfish-CBC
Security Considerations
The use of CBC mode ciphers in SSH servers can introduce certain security risks that need to be considered.
CBC mode is a block cipher mode of operation that encrypts data by chaining together successive blocks of plaintext using a feedback mechanism. This chaining can create vulnerabilities that attackers can exploit.
Vulnerabilities in CBC Mode Ciphers
- Padding Oracle Attacks: Attackers can exploit weaknesses in the padding scheme used in CBC mode to recover plaintext data. This is particularly relevant when the padding scheme is predictable or uses a fixed pattern.
- Bit-Flipping Attacks: Attackers can manipulate specific bits in the ciphertext to modify the corresponding bits in the plaintext. This can be achieved by exploiting the predictable nature of the feedback mechanism in CBC mode.
- Truncation Attacks: Attackers can truncate the ciphertext to remove the last block. This can potentially allow them to decrypt the remaining plaintext blocks without knowing the encryption key.
Mitigation Recommendations
- Use Strong Padding Schemes: Implement robust padding schemes, such as PKCS#7 or OAEP, to mitigate padding oracle attacks.
- Enable Authentication: Ensure that SSH connections are authenticated using strong methods, such as public-key authentication or two-factor authentication, to prevent unauthorized access.
- Limit Ciphertext Exposure: Avoid exposing unnecessary ciphertext to potential attackers. Use secure protocols, such as TLS, to encrypt data in transit.
- Monitor and Update Regularly: Continuously monitor SSH server configurations and update software regularly to patch any vulnerabilities that may arise.
Performance Implications
Analyzing the performance impact of using CBC mode ciphers on SSH connections is essential to optimize SSH performance. By understanding the implications, system administrators can make informed decisions when configuring their SSH servers and clients.
CBC mode ciphers generally have higher latency compared to other cipher modes, such as CTR mode. This is because CBC mode requires the decryption of each block to depend on the previous block, leading to a sequential processing overhead.
Optimizing SSH Performance
To optimize SSH performance when using CBC mode ciphers, several strategies can be employed:
- Use faster ciphers: CBC mode ciphers with faster encryption and decryption algorithms, such as AES-256-CBC, can reduce latency.
- Enable hardware acceleration: If available, hardware acceleration can offload the encryption and decryption tasks from the CPU, improving performance.
- Increase the packet size: Larger packet sizes reduce the overhead of sending and receiving packets, as fewer packets are required to transmit the same amount of data.
- Tune the SSH server: Adjusting SSH server settings, such as the number of concurrent connections and the maximum packet size, can optimize performance for specific use cases.
Compatibility and Interoperability
CBC mode ciphers are widely supported by SSH clients and servers. Most modern SSH implementations support the use of CBC mode ciphers, including AES-128-CBC, AES-192-CBC, and AES-256-CBC. However, it is important to note that some older SSH clients and servers may not support CBC mode ciphers, so it is important to check the compatibility of your SSH client and server before using CBC mode ciphers.
One potential interoperability issue that may arise when using CBC mode ciphers is that some SSH clients and servers may not support the use of CBC mode ciphers with certain key sizes. For example, some SSH clients and servers may not support the use of CBC mode ciphers with a key size of 128 bits, so it is important to check the compatibility of your SSH client and server before using CBC mode ciphers with a key size of 128 bits.
To ensure compatibility and interoperability when using CBC mode ciphers, it is important to use a cipher that is supported by both the SSH client and server. It is also important to use a key size that is supported by both the SSH client and server.
Best Practices
To ensure the secure use of CBC mode ciphers on SSH servers, it is essential to adhere to best practices and avoid common pitfalls.
When configuring SSH servers for CBC mode ciphers, it is crucial to prioritize strong encryption algorithms, such as AES-256-CBC or AES-192-CBC, to provide robust protection against brute-force attacks.
Common Mistakes to Avoid
- Using weak or outdated encryption algorithms that are vulnerable to cryptanalysis.
- Enabling insecure protocols or ciphersuites that compromise server security.
- Neglecting regular security audits and updates to address emerging vulnerabilities.
Hardening SSH Servers
To enhance the resilience of SSH servers against attacks targeting CBC mode ciphers, consider implementing the following measures:
- Disable unused or insecure ciphersuites to reduce the attack surface.
- Enforce strong password policies and enable two-factor authentication for added security.
- Monitor server logs for suspicious activity and implement intrusion detection systems to detect and respond to potential attacks.
Alternative Cipher Modes
SSH supports various cipher modes beyond CBC mode. Each mode offers distinct advantages and disadvantages, influencing the security, performance, and compatibility of SSH connections. Understanding these alternatives enables informed decision-making when configuring SSH servers.
ECB Mode
Electronic Codebook (ECB) mode encrypts each data block independently, making it vulnerable to patterns and repetition attacks. However, it offers exceptional performance due to its simplicity.
CFB Mode
Cipher Feedback (CFB) mode uses a sliding window to encrypt data, providing better security than ECB mode. It strikes a balance between security and performance, making it suitable for scenarios where both factors are critical.
OFB Mode
Output Feedback (OFB) mode generates a keystream that is XORed with plaintext data to produce ciphertext. It offers stronger security than CFB mode but may introduce latency due to its stream-based nature.
CTR Mode
Counter (CTR) mode uses a counter to generate a unique keystream for each data block, providing high security and efficiency. It is often preferred for high-security applications.
Choosing the Right Cipher Mode
The appropriate cipher mode for an SSH deployment depends on specific requirements. For low-latency applications, ECB mode may suffice. For enhanced security, CFB or OFB mode is recommended. For applications demanding the highest security, CTR mode is the optimal choice.
Interoperability considerations may also influence the decision, as some SSH clients may not support all cipher modes.
SSH Protocol Evolution
The SSH protocol has evolved significantly over the years, and its cipher suite has been a key area of focus. In the early days of SSH, CBC mode ciphers were widely used. However, as security concerns emerged, the SSH protocol was updated to address these issues.
Addressing Security Concerns
One of the primary security concerns with CBC mode ciphers is that they are vulnerable to padding oracle attacks. These attacks allow an attacker to recover the plaintext of a message by manipulating the padding. To address this issue, the SSH protocol was updated to use authenticated encryption modes, such as AES-GCM.
These modes provide protection against padding oracle attacks and other security vulnerabilities.
Future Developments
The SSH protocol is constantly evolving, and the cipher suite is likely to continue to change in the future. One area of focus is the development of post-quantum cryptography algorithms. These algorithms are designed to be resistant to attack by quantum computers, which could potentially break current encryption methods.
As post-quantum cryptography algorithms mature, they are likely to be incorporated into the SSH protocol.
Real-World Case Studies
Numerous organizations have implemented CBC mode ciphers on their SSH servers, with varying degrees of success. Some have reported significant improvements in security, while others have encountered challenges.
Factors that contribute to the success or failure of CBC mode cipher implementations include:
- Server configuration: Ensuring that the server is configured correctly is crucial for the successful implementation of CBC mode ciphers.
- Cipher selection: Choosing the right cipher for the specific environment is important. Some ciphers are more resistant to certain types of attacks than others.
- Network conditions: The network conditions between the client and server can affect the performance of CBC mode ciphers.
- Client compatibility: Ensuring that the client is compatible with the CBC mode cipher being used is essential.
Case Study: Successful Implementation
A large financial institution successfully implemented CBC mode ciphers on its SSH servers. The organization reported a significant reduction in the number of successful brute-force attacks on its servers.
Factors that contributed to the success of this implementation included:
- Careful server configuration: The organization worked closely with its vendor to ensure that the server was configured correctly.
- Strong cipher selection: The organization chose a cipher that was known to be resistant to brute-force attacks.
- Optimal network conditions: The organization had a high-speed, low-latency network between its clients and servers.
- Client compatibility: The organization ensured that all of its clients were compatible with the CBC mode cipher being used.
Future Research Directions
Research in the field of CBC mode ciphers in SSH is an ongoing endeavor, with a focus on enhancing security and efficiency. Future research directions include:
Advanced Encryption Algorithms
Investigating the implementation of more robust and efficient encryption algorithms, such as AES-256-CBC or ChaCha20-Poly1305, to further strengthen SSH encryption.
Quantum-Resistant Cryptography
Exploring the integration of quantum-resistant cryptographic algorithms, such as post-quantum cryptography (PQC), to prepare for the potential threat posed by quantum computers.
Improved Cipher Negotiation
Developing more sophisticated cipher negotiation mechanisms to optimize cipher selection based on factors such as security requirements, performance, and compatibility.
Security Analysis and Vulnerability Assessment
Conducting thorough security analyses and vulnerability assessments of CBC mode ciphers in SSH to identify potential weaknesses and develop mitigation strategies.
Performance Optimization
Investigating techniques to improve the performance of CBC mode ciphers, such as optimizing key exchange and encryption/decryption algorithms, to enhance the overall efficiency of SSH connections.
Last Word
Understanding and implementing SSH server CBC mode ciphers is essential for system administrators seeking to maximize the security and performance of their remote access infrastructure. By carefully considering the factors discussed in this article, organizations can effectively mitigate risks, optimize performance, and ensure the integrity of their sensitive data.