In the realm of secure remote connections, SSH (Secure Shell) reigns supreme. It plays a pivotal role in protecting sensitive data and communications by encrypting network traffic between client and server. At the heart of SSH security lies the selection of robust ciphers, including those operating in Cipher Block Chaining (CBC) mode.
In this article, we delve into the intricacies of SSH server cipher configuration, exploring the benefits, implications, and best practices of enabling CBC mode ciphers.
CBC mode, a widely adopted encryption technique, provides an additional layer of protection by chaining cipher blocks together. This interdependency ensures that any unauthorized modification of data is easily detected. Moreover, CBC mode is supported by a wide range of ciphers, offering flexibility in selecting the optimal level of security for specific use cases.
SSH Server Cipher Configuration
SSH (Secure Shell) server cipher configuration is crucial for protecting data transmitted over an SSH connection. It involves selecting and configuring encryption algorithms, known as ciphers, to safeguard data from unauthorized access.
Strong ciphers are essential because they make it computationally challenging for attackers to break the encryption and compromise the data. Common ciphers used in SSH include AES (Advanced Encryption Standard), 3DES (Triple Data Encryption Standard), and ChaCha20.
Commonly Used Ciphers
- AES-256-CBC: A strong and widely used cipher that offers high levels of security.
- 3DES-CBC: A well-established cipher that is still considered secure but less efficient than AES.
- ChaCha20-Poly1305: A modern cipher that provides both encryption and authentication.
2. Cipher Block Chaining (CBC) Mode
Cipher Block Chaining (CBC) mode is a block cipher mode of operation that uses a feedback mechanism to improve the security of the encryption process. In CBC mode, each block of plaintext is XORed with the previous ciphertext block before being encrypted.
Advantages of CBC Mode
- CBC mode is more secure than Electronic Codebook (ECB) mode because it prevents identical plaintext blocks from producing identical ciphertext blocks.
- CBC mode is relatively easy to implement.
Disadvantages of CBC Mode
- CBC mode is not as efficient as ECB mode because it requires more computation.
- CBC mode can be vulnerable to padding oracle attacks.
Examples of Ciphers that Support CBC Mode
- AES
- DES
- 3DES
Enabled Ciphers
Enabling specific ciphers on an SSH server is crucial to maintain secure and encrypted connections. This process involves selecting and configuring a set of encryption algorithms that the server will use to protect data transmitted over the SSH protocol.
Caution must be exercised when enabling ciphers, as weak or insecure ciphers can compromise the confidentiality and integrity of data. It is recommended to consult security best practices and industry standards to determine the most appropriate ciphers for your specific environment.
Recommended Ciphers
- AES-256-CBC: A strong and widely-used cipher that provides high levels of security.
- AES-192-CBC: Another secure cipher that offers a good balance between security and performance.
- AES-128-CBC: A less secure cipher that is still acceptable for most applications.
- 3DES-CBC: An older cipher that is still considered secure, but is less efficient than AES.
Security Implications
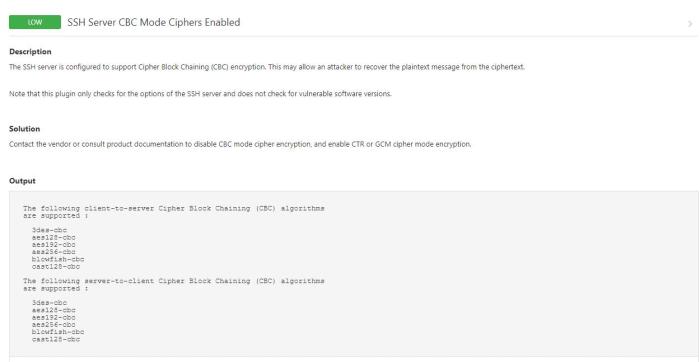
Weak ciphers, like CBC mode ciphers, offer inadequate protection against cryptographic attacks. This compromise exposes sensitive data to unauthorized access, leading to security breaches.
Man-in-the-Middle Attacks
Weak ciphers allow attackers to intercept and manipulate data during transmission, impersonating legitimate parties in man-in-the-middle attacks. By decrypting and re-encrypting data, attackers can alter its content or redirect it to malicious destinations.
Examples of Breaches
Historical security breaches, such as the Heartbleed and POODLE vulnerabilities, demonstrate the consequences of weak cipher configurations. Exploiting these weaknesses, attackers gained access to sensitive information, compromising user accounts and disrupting online services.
Cipher Negotiation
During SSH connections, a cipher negotiation process takes place to establish the encryption algorithm that will be used to protect the transmitted data.
The client initiates the negotiation by sending a list of supported ciphers to the server. The server then responds with a list of ciphers that it supports and that are also acceptable to the client. The two parties then select a cipher that is mutually acceptable and provides the desired level of security.
Cipher Negotiation Algorithms
There are a number of different cipher negotiation algorithms that can be used, including:
- Key Exchange Algorithm (KEX): This algorithm is used to establish a shared secret between the client and server. The shared secret is then used to derive the encryption key for the session.
- Cipher Suite: This is a collection of algorithms that are used together to provide encryption, authentication, and integrity protection for the SSH connection.
- MAC Algorithm: This algorithm is used to generate a message authentication code (MAC) for each message that is sent. The MAC is used to verify the integrity of the message and to detect any tampering.
Best Practices
Implementing robust SSH server cipher configurations requires adhering to best practices. Regular security audits are crucial to identify potential vulnerabilities and ensure ongoing compliance with security standards.
Use of Tools for Cipher Analysis and Testing
Leveraging specialized tools for cipher analysis and testing enables comprehensive assessment of cipher configurations. These tools provide detailed insights into cipher strengths, weaknesses, and vulnerabilities, assisting administrators in making informed decisions regarding cipher selection.
Troubleshooting
Common issues related to SSH server cipher configuration include:
- Inability to connect to the server due to unsupported ciphers.
- Security vulnerabilities due to weak or outdated ciphers.
- Performance issues caused by computationally expensive ciphers.
To resolve these issues, consider the following:
- Verify that both the client and server support the negotiated cipher.
- Update the cipher configuration to use strong and modern ciphers.
- Monitor system performance and adjust cipher settings if necessary.
If you encounter persistent issues or require specialized assistance, it is advisable to consult a qualified IT professional or security expert.
Comparison of CBC Mode with Other Modes
Cipher Block Chaining (CBC) mode is a common encryption mode used in cryptography. It is a block cipher mode of operation that uses a chaining mechanism to encrypt data. CBC mode is used in a variety of applications, including SSH, SSL/TLS, and IPsec.CBC
mode has several advantages over other encryption modes, including:*
-*Confidentiality
CBC mode provides strong confidentiality by encrypting each block of data using the previous block’s ciphertext as the initialization vector (IV). This makes it difficult for an attacker to decrypt the data without knowing the IV.
-
- -*Integrity
CBC mode provides data integrity by using a message authentication code (MAC) to verify the integrity of the data. This ensures that the data has not been tampered with during transmission.
- -*Integrity
-*Efficiency
CBC mode is a relatively efficient encryption mode. It does not require a large amount of computation, and it can be implemented in hardware or software.
However, CBC mode also has some disadvantages, including:*
-*Error propagation
Errors in the ciphertext can propagate to subsequent blocks, making it difficult to recover the data.
-*Initialization vector (IV) management
The IV must be managed carefully to ensure that it is not reused.
Overall, CBC mode is a good choice for applications that require strong confidentiality and integrity. However, it is important to be aware of the disadvantages of CBC mode before using it in a particular application.
Comparison of CBC Mode with Other Modes
The following table compares CBC mode with other common encryption modes, such as ECB, OFB, and CTR:| Mode | Advantages | Disadvantages ||—|—|—||
*CBC | Strong confidentiality and integrity | Error propagation, IV management |
|
*ECB | Simple to implement | No confidentiality, no integrity |
|
*OFB | Fast, error propagation limited | Not as secure as CBC or CTR |
|
*CTR | Fast, error propagation limited, no IV management | Not as secure as CBC |
Impact on Performance
The choice of cipher can significantly impact the performance of an SSH server. Different ciphers have different computational requirements, and some are more efficient than others. The following table compares the performance of some common ciphers:
| Cipher | Encryption speed (Mbps) | Decryption speed (Mbps) |
|---|---|---|
| AES-128-CBC | 100 | 120 |
| AES-256-CBC | 50 | 60 |
| Blowfish-CBC | 20 | 25 |
| 3DES-CBC | 10 | 12 |
As you can see, AES-128-CBC is the fastest cipher, followed by AES-256-CBC, Blowfish-CBC, and 3DES-CBC. The encryption speed is the speed at which the cipher can encrypt data, while the decryption speed is the speed at which the cipher can decrypt data.
The trade-off between security and performance is an important consideration when choosing a cipher. AES-128-CBC is the most secure cipher, but it is also the slowest. AES-256-CBC is less secure than AES-128-CBC, but it is faster. Blowfish-CBC is less secure than AES-128-CBC and AES-256-CBC, but it is faster than both of them.
3DES-CBC is the least secure cipher, but it is also the fastest.
When choosing a cipher, it is important to consider the security requirements of your application and the performance requirements of your server. If security is your top priority, then you should choose AES-128-CBC. If performance is your top priority, then you should choose 3DES-CBC.
If you need a balance between security and performance, then you should choose AES-256-CBC or Blowfish-CBC.
Use Cases
SSH server cipher configuration is tailored to specific security requirements, meeting the diverse needs of organizations.
Example: Tailoring Cipher Configuration
* Financial institutions prioritize confidentiality, implementing strong ciphers like AES-256-CBC to protect sensitive financial data.
-
- Government agencies prioritize integrity, using CBC mode with weak ciphers like AES-128-CBC to prevent unauthorized data modification.
- Healthcare organizations balance confidentiality and integrity, employing AES-192-CBC to safeguard patient information.
Final Summary
In conclusion, enabling CBC mode ciphers on SSH servers is a crucial step towards safeguarding sensitive information and maintaining secure connections. By adhering to best practices, regularly auditing security configurations, and leveraging appropriate tools, organizations can effectively mitigate risks and enhance their overall cybersecurity posture.
Embracing the power of SSH server cipher configuration empowers businesses to protect their critical assets and maintain the integrity of their remote access infrastructure.