ssh.sshslowdns.com – In the realm of secure remote connections, SSH (Secure Shell) reigns supreme. By leveraging the User Datagram Protocol (UDP), SSH can be further enhanced to optimize security and performance.
This comprehensive guide delves into the world of SSH over UDP, exploring custom ports, monitoring techniques, and best practices for safeguarding your network.
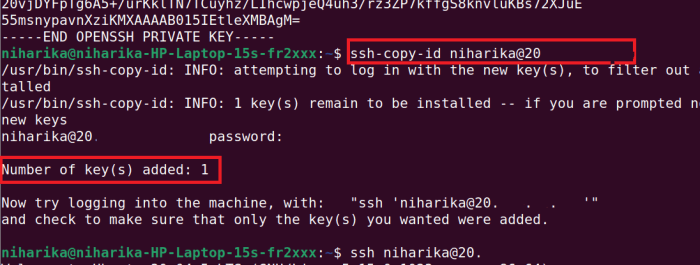
With a custom UDP port for SSH, you gain greater control over access to your systems. This guide will provide step-by-step instructions on how to configure a custom SSH UDP port, ensuring that your connections remain secure and protected from unauthorized access.
SSH (Secure Shell) Overview
SSH (Secure Shell) is a network protocol that provides secure remote access to a computer system over an unsecured network. It allows users to log into a remote machine and execute commands as if they were present locally. SSH encrypts all traffic, including passwords and data, making it difficult for eavesdroppers to intercept sensitive information.
SSH is widely used for system administration, remote file transfer, and secure shell access. It is a versatile tool that can be used for a variety of purposes, including:
Common SSH Uses
- Remote login: SSH allows users to log into a remote computer and execute commands as if they were present locally.
- Secure file transfer: SSH can be used to securely transfer files between two computers.
- Port forwarding: SSH can be used to forward ports between two computers, allowing users to access services that would otherwise be inaccessible.
- Secure shell access: SSH can be used to create a secure shell session between two computers, allowing users to execute commands on the remote computer as if they were present locally.
UDP (User Datagram Protocol)
UDP (User Datagram Protocol) is a connectionless protocol that operates at the transport layer of the TCP/IP model. It is designed for applications that require fast and efficient data transfer, with minimal overhead. UDP packets are known as datagrams and are transmitted without any error correction or flow control mechanisms.
Key Characteristics of UDP
-
- -*Connectionless UDP does not establish a connection between the sender and receiver before transmitting data. Each datagram is treated independently, making UDP suitable for applications that do not require reliable or ordered delivery.
-*Low Overhead
UDP headers are smaller compared to TCP headers, reducing the amount of overhead associated with data transmission. This makes UDP more efficient for applications that transmit short bursts of data.
-*Fast Data Transfer
UDP does not perform error correction or flow control, allowing for faster data transfer speeds. This is particularly beneficial for applications that require real-time data transmission, such as video streaming or online gaming.
Advantages of UDP
-
- -*Speed and Efficiency UDP’s connectionless nature and low overhead make it an efficient choice for applications that require fast data transfer.
-*Real-Time Applications
UDP is ideal for applications that need to transmit data in real time, without any delays caused by error correction or flow control mechanisms.
-*Simplicity
UDP’s simple header structure makes it easy to implement and integrate into applications.
Disadvantages of UDP
-
- -*Unreliable Delivery UDP does not guarantee that data will be delivered to the recipient, or that it will be delivered in the correct order. This can be a disadvantage for applications that require reliable data transmission.
-*No Flow Control
UDP does not implement flow control mechanisms, which can lead to network congestion and packet loss.
-*Security Concerns
UDP’s connectionless nature makes it vulnerable to certain types of security attacks, such as spoofing and denial-of-service attacks.
Examples of Applications that Utilize UDP
-
- -*Video Streaming UDP is used for streaming video content due to its ability to transmit data quickly and efficiently, with minimal buffering delays.
-*Online Gaming
UDP is preferred for online gaming due to its low latency and fast data transfer capabilities, which are crucial for real-time gaming experiences.
-*Voice over IP (VoIP)
UDP is used for transmitting voice data over the internet, as it provides real-time communication with minimal delays.
-*DNS (Domain Name System)
UDP is used for DNS lookups, as it is fast and efficient for resolving domain names to IP addresses.
Custom SSH UDP Port
Utilizing a custom UDP port for SSH enhances security by obscuring the standard port and making it more challenging for attackers to target.
Additionally, it allows for greater flexibility in network configurations and can help prevent port conflicts with other applications.
To configure a custom SSH UDP port, follow these steps:
Configuration
- Edit the SSH configuration file (/etc/ssh/sshd_config on Linux or /etc/ssh/sshd.conf on macOS).
- Add or modify the “Port” directive to specify the custom UDP port number, e.g., “Port 30000”.
- Restart the SSH service to apply the changes.
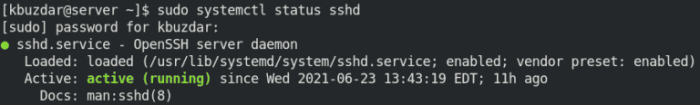
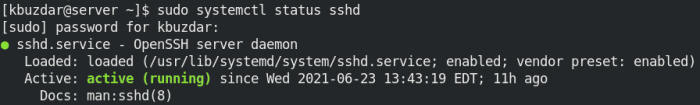
SSH Logs and Monitoring
Monitoring SSH logs is crucial for maintaining network security. SSH logs provide valuable insights into user activities, system events, and potential security threats.
To configure SSH logging, edit the SSH configuration file (usually /etc/ssh/sshd_config) and set the LogLevel parameter to a desired level (e.g., INFO, DEBUG). Additionally, consider using tools like syslog or logwatch to centralize and analyze SSH logs.
Identifying Security Threats
SSH logs can reveal potential security threats, such as:
- Unsuccessful login attempts (failed authentication)
- Suspicious user activity (e.g., accessing unauthorized files)
- Brute-force attacks (repeated login attempts with different credentials)
- Configuration errors (e.g., insecure settings or open ports)
Analyzing SSH Logs
To analyze SSH Over UDP logs effectively, focus on:
- Identifying patterns and anomalies in user behavior
- Checking for failed login attempts and suspicious activity
- Reviewing system events and configuration changes
- Correlating SSH logs with other security logs (e.g., firewall logs)
SSH Hardening Techniques
To enhance the security of SSH connections, implementing SSH hardening techniques is crucial. These techniques aim to mitigate potential vulnerabilities and strengthen the overall SSH configuration.
Some best practices for SSH hardening include:
Disabling Root Login
Disabling root login over SSH prevents attackers from directly targeting the root account, which has elevated privileges. Instead, create a non-root user with administrative privileges and use that account for SSH access.
Limiting Login Attempts
Limit the number of login attempts to prevent brute-force attacks. Configure SSH to lock out accounts after a certain number of failed login attempts within a specified time frame.
Using Strong Encryption Algorithms
Use strong encryption algorithms, such as AES-256 or ChaCha20-Poly1305, to protect SSH traffic from eavesdropping and man-in-the-middle attacks.
Additional Recommendations
- Use SSH key-based authentication instead of password-based authentication.
- Configure SSH to listen on a non-standard port to reduce the likelihood of automated attacks.
- Keep SSH software up-to-date with the latest security patches.
- Monitor SSH logs regularly for suspicious activity and take appropriate action.
SSH Authentication Methods
SSH provides various authentication methods to secure access to remote systems. Each method has its strengths and weaknesses, making it suitable for different scenarios.
Password Authentication
Password authentication is the simplest method, requiring users to provide a username and password. However, it is vulnerable to brute-force attacks and password theft.
Public Key Authentication
Public key authentication utilizes a pair of cryptographic keys: a public key and a private key. The public key is stored on the server, while the private key is kept secret by the user. This method is more secure than password authentication as it does not transmit the private key over the network.
Two-Factor Authentication
Two-factor authentication adds an extra layer of security by requiring users to provide two different authentication factors. This can be a combination of password and a one-time code sent to a mobile device or an authentication app.
Choosing the Most Appropriate Method
The choice of authentication method depends on the security requirements and convenience factors. Password authentication is easy to implement but less secure, while public key authentication is more secure but requires more setup. Two-factor authentication provides the highest level of security but may not be practical for all scenarios.
SSH Over UDP Tunneling
SSH tunneling is a technique that allows you to securely access remote networks by creating an encrypted tunnel over an insecure network. It establishes a secure connection between two remote hosts, enabling the secure transmission of data between them. SSH tunneling offers a versatile solution for various scenarios, including:
- Accessing Remote Networks: SSH tunneling can be used to securely access remote networks that may be behind firewalls or NAT (Network Address Translation) devices.
- Secure Data Transfer: SSH tunnels provide a secure channel for transferring sensitive data between two hosts, protecting it from eavesdropping or interception.
- Application-Specific Tunneling: SSH tunneling can be configured to forward specific applications or services through the secure tunnel, allowing for secure access to applications that may not support SSH natively.
Configuring SSH Tunnels
Configuring SSH tunnels involves establishing a secure connection between two hosts using the SSH protocol. The following steps Artikel the general process:
- Generate SSH Key Pair: Generate an SSH key pair on the client machine. This key pair will be used to authenticate the connection.
- Establish SSH Connection: Initiate an SSH connection to the remote host using the generated SSH key.
- Create Tunnel: Use the “sshL” command to create the SSH tunnel. Specify the local port on the client machine, the remote port on the remote host, and the destination host.
- Forward Traffic: Once the tunnel is established, traffic can be forwarded through it by accessing the local port on the client machine.
Examples of SSH Tunneling
SSH tunneling has numerous applications in various scenarios. Here are a few examples:
- Securely Accessing Web Servers: SSH tunneling can be used to securely access web servers that may be behind firewalls or NAT devices.
- Remote Database Access: SSH tunnels can be established to securely connect to remote databases, enabling secure data access and manipulation.
- Secure File Transfer: SSH tunneling can be used to securely transfer files between two hosts, ensuring data privacy and integrity.
SSH Port Forwarding
SSH port forwarding allows users to establish secure connections between two hosts through an SSH tunnel. It enables remote access to services and applications that may not be directly accessible due to network restrictions or security configurations. There are two main types of SSH port forwarding:
Local Port Forwarding
Local port forwarding creates a tunnel from a local port on the client machine to a remote port on the server. This allows the client to access the remote port as if it were a local port. It is useful for accessing services that are only available on the server, such as internal web servers or databases.
Remote Port Forwarding
Remote port forwarding creates a tunnel from a remote port on the server to a local port on the client machine. This allows the server to access the local port on the client as if it were a remote port.
It is useful for exposing local services, such as web servers or email servers, to the internet without opening ports directly on the client machine.
Benefits and Use Cases of SSH Port Forwarding
SSH port forwarding offers several benefits and use cases, including:
Secure access to remote services
SSH port forwarding provides a secure and encrypted channel for accessing remote services, even if they are not directly accessible due to firewalls or other network restrictions.
Remote administration
SSH port forwarding allows administrators to securely manage and configure remote servers from a local machine.
Exposing local services
SSH port forwarding can be used to expose local services to the internet without opening ports directly on the client machine, enhancing security and reducing the risk of unauthorized access.
Testing and debugging
SSH port forwarding can be used for testing and debugging network configurations and services by allowing access to ports that may be blocked or restricted in other ways.
Configuring and Using SSH Port Forwarding
To configure and use SSH port forwarding, follow these steps:
- Establish an SSH connection to the remote server.
- Use the
- L option for local port forwarding or the
- R option for remote port forwarding.
- Specify the local or remote port and the destination port on the server.
- Connect to the forwarded port on the local or remote machine as needed.
For example, to create a local port forwarding tunnel from port 8080 on the client machine to port 80 on the server, use the following command:“`ssh
-L 8080
localhost:80 username@server_address“`
SSH File Transfer
SSH provides a secure channel for transferring files between remote hosts. It supports multiple file transfer methods, including SCP (Secure Copy) and SFTP (SSH File Transfer Protocol).
SCP
SCP is a command-line tool that uses SSH to securely copy files between two hosts. It provides a simple and efficient way to transfer files without exposing them to eavesdropping or unauthorized access.
SFTP
SFTP is an interactive file transfer protocol that runs over SSH. It offers a more graphical and user-friendly interface compared to SCP, making it easier to navigate and manage remote files.
Best Practices for Secure File Handling
- Use strong passwords and SSH keys for authentication.
- Limit file access permissions to authorized users only.
- Transfer files over a secure network connection.
- Use file encryption to protect sensitive data during transfer.
- Regularly monitor SSH logs for suspicious activity.
SSH Troubleshooting
SSH troubleshooting involves identifying and resolving issues related to SSH connectivity, authentication, and performance. This section provides an overview of common SSH troubleshooting scenarios and techniques.
Diagnosing SSH Connection Problems
Connection problems can occur due to incorrect network configurations, firewall settings, or SSH server misconfigurations. To diagnose these issues, try the following:
- Verify that the SSH server is running and listening on the specified port.
- Check firewall settings to ensure SSH traffic is allowed.
- Use SSH debugging tools like `ssh
-v` to trace the connection process and identify any errors. - Review SSH server logs for any error messages or connection attempts.
Resolving Authentication Errors
Authentication errors can be caused by incorrect credentials, misconfigured SSH keys, or disabled authentication methods. To troubleshoot these issues:
- Double-check the username and password or SSH key.
- Verify that the SSH server allows the authentication method being used (e.g., password, key-based).
- Inspect SSH server logs for any authentication-related error messages.
Improving SSH Performance
SSH performance can be affected by factors such as network latency, encryption algorithms, and server load. To improve performance, consider the following: