In the realm of secure remote access, SSH (Secure Shell) stands tall as a ubiquitous protocol. While traditionally implemented over TCP, SSH over UDP has emerged as an alternative offering unique advantages and considerations. This guide delves into the intricacies of SSH over UDP, exploring its benefits, drawbacks, implementation, security implications, performance characteristics, and use cases.
By providing a comprehensive analysis, we aim to empower network administrators and security professionals with the knowledge to make informed decisions about adopting SSH over UDP in their environments.
SSH over UDP leverages the User Datagram Protocol (UDP) for data transmission, which differs from the Transmission Control Protocol (TCP) used in standard SSH implementations. This distinction brings forth both advantages and disadvantages, which we will thoroughly examine in the subsequent sections.
Additionally, we will provide practical guidance on implementing and configuring SSH over UDP on various platforms, ensuring a smooth transition for those seeking to harness its capabilities.
SSH over UDP Protocol
SSH over UDP is a secure shell protocol that uses the User Datagram Protocol (UDP) instead of the Transmission Control Protocol (TCP) for data transmission. This allows for faster and more efficient communication, especially in environments with high latency or packet loss.
Advantages of SSH over UDP
- Faster performance: UDP is a connectionless protocol, which means it does not establish a connection with the remote host before sending data. This eliminates the overhead associated with TCP connections, resulting in faster performance.
- Reduced latency: UDP does not require acknowledgment of data packets, which reduces the latency associated with TCP. This is particularly beneficial for applications that require real-time communication.
- Improved packet loss handling: UDP does not retransmit lost packets, which can improve performance in environments with high packet loss. This is because TCP’s retransmission mechanism can lead to congestion and further packet loss.
Disadvantages of SSH over UDP
- Unreliable data delivery: UDP does not guarantee the delivery of data packets, which can lead to data loss. This is a significant disadvantage for applications that require reliable data transmission.
- Limited error handling: UDP does not provide any built-in error handling mechanisms, which makes it difficult to detect and recover from errors. This can lead to problems with data integrity and application stability.
Comparison of SSH over UDP and SSH over TCP
| Feature | SSH over UDP | SSH over TCP |
|---|---|---|
| Connection type | Connectionless | Connection-oriented |
| Performance | Faster | Slower |
| Latency | Lower | Higher |
| Packet loss handling | Improved | Worse |
| Reliability | Unreliable | Reliable |
| Error handling | Limited | Extensive |
Implementation and Configuration
Implementing SSH over UDP involves a few key steps:
-
- -*Enable UDP forwarding on the server This allows SSH to accept UDP connections on a specific port.
-*Configure the SSH client to use UDP
The client must be configured to use the UDP protocol when connecting to the server.
-*Establish the SSH connection over UDP
The client initiates the connection using the UDP protocol, and the server responds with a UDP handshake.
Configuring SSH over UDP
Configuring SSH over UDP varies slightly across platforms:
-*Linux
Edit the `/etc/ssh/sshd_config` file and add
“` ListenAddress 0.0.0.0:2222 Port 2222 Protocol 2 “`
-
- Restart the SSH service.
-*Windows
Use the Windows Registry Editor to create a new key
“` HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sshd\Parameters “`
Add a DWORD value named “ListenAddress” and set it to “0.0.0.0
2222″.
-
- Restart the SSH service.
-*macOS
Edit the `/etc/ssh/sshd_config` file and add
“` ListenAddress 0.0.0.0:2222 Port 2222 Protocol 2 “`
Restart the SSH service.
Common Configuration Options for SSH over UDP
-
- -*ListenAddress The IP address and port on which the SSH server listens for UDP connections.
-*Port
The port number used for UDP connections.
-*Protocol
The SSH protocol version to use (e.g., 2 for SSHv2).
-*Ciphers
The encryption algorithms to use for UDP connections.
-*MACs
The message authentication codes to use for UDP connections.
-*KexAlgorithms
The key exchange algorithms to use for UDP connections.
Security Implications
While SSH over UDP offers performance benefits, it also introduces certain security implications that need to be considered.
One of the key concerns with SSH over UDP is that it can be more vulnerable to certain types of attacks compared to SSH over TCP. UDP is a connectionless protocol, which means that it does not establish a persistent connection between the client and the server.
This makes it more difficult to detect and prevent attacks such as spoofing, where an attacker impersonates a legitimate user or device.
Mitigation Techniques
To enhance security when using SSH over UDP, several mitigation techniques can be employed:
- Use strong encryption algorithms: Utilizing robust encryption algorithms such as AES-256 or ChaCha20-Poly1305 helps protect data from unauthorized access, even if it is intercepted.
- Implement rate limiting: Enforcing rate limits on UDP packets can help mitigate the impact of denial-of-service (DoS) attacks by limiting the number of requests that can be sent within a specific time frame.
- Enable IP filtering: Restricting access to SSH over UDP to specific IP addresses or ranges can prevent unauthorized users from accessing the service.
- Use a VPN: Establishing a VPN connection can provide an additional layer of security by encrypting all traffic, including SSH over UDP, making it more difficult for attackers to intercept and eavesdrop on data.
Performance Considerations
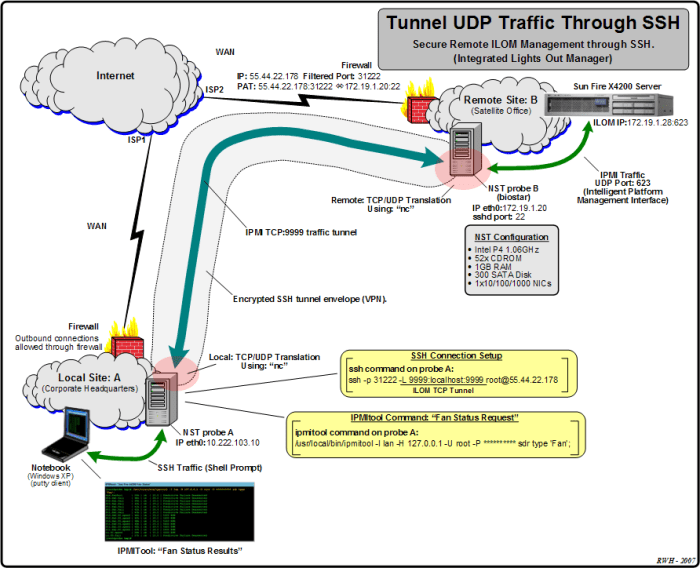
SSH over UDP offers distinct performance characteristics compared to SSH over TCP.
Latency and Throughput
UDP’s connectionless nature eliminates the need for TCP’s three-way handshake, resulting in lower latency. However, UDP lacks flow control and error correction, which can impact throughput, especially in congested networks.
Optimization for Performance
Optimizing performance for SSH over UDP involves:
- Selecting an appropriate UDP port range to avoid conflicts with other applications.
- Tuning UDP buffer sizes to match network conditions and application requirements.
- Using a reliable UDP library that provides features like fragmentation and retransmission.
Use Cases and Applications
SSH over UDP offers significant advantages in scenarios where low latency and high performance are crucial. It is particularly suitable for applications such as:
-
- -*Interactive remote access SSH over UDP provides a responsive and lag-free experience for remote desktop access, allowing users to control remote systems with minimal delay.
-*High-frequency data transfer
Applications involving real-time data streaming or frequent data updates benefit from the low latency of SSH over UDP, ensuring timely delivery of information.
-*Network monitoring and troubleshooting
SSH over UDP can be used for remote network monitoring and troubleshooting tasks, where quick response times are essential for efficient problem resolution.
Real-World Examples
Organizations that have successfully implemented SSH over UDP include:
-
- -*Google Google uses SSH over UDP for remote access to its vast network of servers, ensuring fast and reliable connectivity for its engineers.
-*Amazon Web Services (AWS)
AWS offers SSH over UDP as an option for its EC2 instances, providing low-latency remote access for cloud-based applications.
-*Microsoft Azure
Azure also supports SSH over UDP for its virtual machines, enabling seamless remote management and troubleshooting.
Alternatives to SSH over UDP
Despite its advantages, SSH over UDP has certain limitations. Let’s explore alternative protocols and techniques that offer similar functionality:
mDNS (Multicast DNS)
mDNS is a zero-configuration networking protocol that allows devices to discover each other on a local network without a central server. It operates over UDP and can be used for service discovery, hostname resolution, and other tasks. Advantages of mDNS include its simplicity, low overhead, and ease of implementation.
However, it has limited range and is not suitable for large networks or networks with complex topologies.
ZeroTier
ZeroTier is a software-defined networking (SDN) solution that creates a virtual private network (VPN) over UDP. It provides secure, low-latency connections between devices, even when they are behind firewalls or NAT devices. ZeroTier offers features such as automatic network discovery, multi-homing, and traffic encryption.
While it is more complex to set up than mDNS, it offers greater flexibility and scalability.
WireGuard
WireGuard is a modern VPN protocol that operates over UDP. It is known for its simplicity, high performance, and low overhead. WireGuard uses a modern cryptographic suite and offers strong security. It is suitable for a wide range of applications, including remote access, site-to-site VPNs, and cloud connectivity.
Choosing the Right Alternative
The choice of alternative protocol depends on the specific requirements and constraints of the network environment. mDNS is suitable for small, simple networks where service discovery is the primary requirement. ZeroTier is a good option for creating secure, private networks across complex topologies or over the internet.
WireGuard is ideal for high-performance VPN applications where security and low latency are critical.
Future Developments and Research
The field of SSH over UDP is continuously evolving, with new developments and research directions emerging. This section explores potential improvements and enhancements to the protocol, as well as areas where further research is needed to advance its adoption.
Emerging Trends
One emerging trend is the integration of SSH over UDP with other network protocols. This integration can improve performance and security, and enable new use cases. For example, SSH over UDP can be integrated with QUIC to provide a more efficient and secure transport layer.Another
emerging trend is the development of new encryption algorithms for SSH over UDP. These algorithms can provide improved security and performance, and enable the use of SSH over UDP in more sensitive applications.
Potential Improvements and Enhancements
Several potential improvements and enhancements to SSH over UDP have been identified. These include:
- Improving the performance of SSH over UDP, especially in high-latency environments.
- Developing new encryption algorithms for SSH over UDP that provide improved security and performance.
- Integrating SSH over UDP with other network protocols to improve performance and security.
Areas for Further Research
Further research is needed to advance the adoption of SSH over UDP. This research should focus on the following areas:
- Developing new use cases for SSH over UDP.
- Evaluating the security of SSH over UDP in different environments.
- Developing tools and techniques to manage and monitor SSH over UDP deployments.
By addressing these research areas, the SSH over UDP community can help to advance the adoption of this protocol and make it more widely used in the future.
Troubleshooting and Common Issues
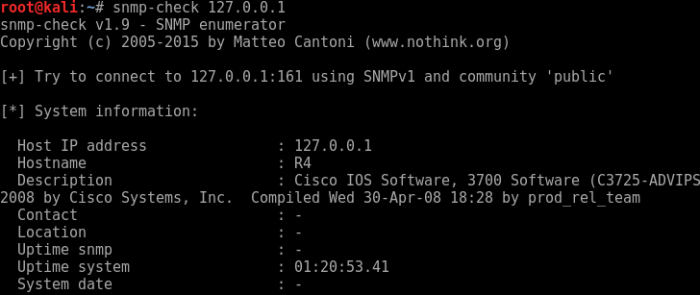
Troubleshooting SSH over UDP can involve addressing connectivity problems, authentication errors, and performance issues. Here’s a guide to help diagnose and resolve common issues:
Connectivity Problems
Unable to establish a connection or frequent connection drops can indicate network or configuration issues. Check the following:
- Ensure that both the client and server have UDP ports open and accessible.
- Verify that the client and server IP addresses are correct and reachable.
- Check for any firewalls or network security devices blocking UDP traffic.
Authentication Errors
Authentication errors occur when the client fails to provide valid credentials to the server. Consider the following:
- Confirm that the username and password or SSH key are correct.
- Check if the SSH server has any authentication restrictions, such as specific key types or IP address limitations.
- Ensure that the SSH client and server are using compatible authentication methods.
Performance Issues
Slow or unreliable performance can be caused by various factors. Investigate the following:
- Check for network congestion or latency issues.
- Adjust the UDP packet size and frequency settings to optimize performance.
- Consider using a VPN or other tunneling mechanism to improve network stability.
Common Errors and Solutions
| Error | Solution |
|---|---|
| Connection refused | Check if the UDP port is open and accessible on both the client and server. |
| Authentication failed | Verify the username, password, or SSH key. |
| Timeout | Check for network connectivity issues or adjust the SSH timeout settings. |
Best Practices and Recommendations
Implementing and using SSH over UDP securely and effectively requires careful planning and adherence to best practices. This section provides guidance on selecting appropriate cipher suites and key exchange algorithms, as well as strategies for hardening SSH over UDP deployments.
Selecting Cipher Suites and Key Exchange Algorithms
The choice of cipher suites and key exchange algorithms for SSH over UDP is critical for ensuring data confidentiality, integrity, and authenticity. Strong cipher suites provide encryption that is resistant to eavesdropping and tampering, while robust key exchange algorithms protect against man-in-the-middle attacks.
The following recommendations should be considered when selecting cipher suites and key exchange algorithms for SSH over UDP:
- Use cipher suites that support strong encryption algorithms, such as AES-256-GCM or ChaCha20-Poly1305.
- Select key exchange algorithms that provide forward secrecy, such as ECDH or Ed25519.
- Disable weak or insecure cipher suites and key exchange algorithms, such as DES or MD5.
Hardening SSH over UDP Deployments
In addition to selecting appropriate cipher suites and key exchange algorithms, there are several other measures that can be taken to harden SSH over UDP deployments. These measures include:
- Use a strong password or passphrase: The password or passphrase used to authenticate to the SSH server should be strong and complex, making it difficult for attackers to guess or brute force.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security by requiring a second factor, such as a code sent to a mobile phone, in addition to the password.
- Limit access to the SSH server: Only authorized users should be granted access to the SSH server. This can be done by using firewalls or access control lists to restrict access to specific IP addresses or networks.
- Monitor SSH logs: SSH logs should be monitored for suspicious activity, such as failed login attempts or unusual traffic patterns. This can help to detect and respond to security incidents.
Conclusion
SSH over UDP offers several advantages, including reduced latency, improved performance in constrained environments, and compatibility with legacy devices. However, it also has limitations, such as potential security risks and compatibility issues with some SSH clients and servers.Organizations considering adopting SSH over UDP should carefully weigh the advantages and limitations before making a decision.
Those with high-latency or bandwidth-constrained environments may benefit from the improved performance offered by SSH over UDP. However, organizations with stringent security requirements or those using SSH clients and servers that do not support SSH over UDP may want to consider alternative solutions.
Summary
In conclusion, SSH over UDP presents a compelling option for organizations seeking enhanced performance and reduced latency in their remote access scenarios. Its advantages, however, come with certain security implications that must be carefully considered and mitigated. By understanding the intricacies of SSH over UDP, network administrators can make informed decisions about its adoption, ensuring a secure and efficient remote access infrastructure.
As technology continues to evolve, we anticipate further developments and research in SSH over UDP, promising even greater possibilities in the future.