In the era of digital transformation, secure remote access and data transfer have become paramount for businesses and individuals alike. Enter SSH Max Websocket, a cutting-edge technology that redefines secure remote connectivity, enabling seamless and encrypted communication across networks.
SSH Max Websocket has emerged as a game-changer in the realm of secure remote access, offering a plethora of benefits, including enhanced security, improved performance, and simplified management. Its unique features and capabilities make it the ideal solution for organizations seeking a robust and reliable remote access platform.
Introduction to SSH Max Websocket
SSH Max Websocket, a cutting-edge technology, has revolutionized the way we access and transfer data remotely. It has emerged as a powerful tool for establishing secure connections between computers, enabling users to seamlessly control and manage remote systems as if they were physically present.
SSH Max Websocket utilizes the Secure Shell (SSH) protocol, a robust and widely adopted security protocol designed to protect data transmission over insecure networks. By encapsulating SSH traffic within the WebSocket protocol, SSH Max Websocket offers a secure and reliable channel for remote access, allowing users to securely connect to remote hosts, execute commands, and transfer files.
Brief History and Background
SSH Max Websocket is the brainchild of Max Wang, a software engineer with a passion for secure remote access solutions. Recognizing the limitations of traditional SSH clients and the growing need for a more versatile and user-friendly approach to remote connectivity, Wang embarked on a mission to develop a solution that would revolutionize the way we access remote systems.
In 2019, Wang released the first version of SSH Max Websocket, an open-source project that quickly gained traction among developers and system administrators. The project’s popularity soared due to its ease of use, cross-platform compatibility, and ability to provide secure remote access from any device with a modern web browser.
Key Features and Benefits
SSH Max Websocket stands out with an array of key features that provide numerous benefits, making it an exceptional choice for secure and efficient remote access and data transfer.
Its primary advantages include enhanced security, improved performance, simplified management, and compatibility with a wide range of devices and platforms.
Enhanced Security
SSH Max Websocket utilizes cutting-edge encryption algorithms, including AES-256, to safeguard data transmissions. It employs public-key cryptography for secure key exchange, ensuring that only authorized users can access the remote system.
Furthermore, it supports two-factor authentication (2FA), adding an extra layer of security to protect against unauthorized access.
Improved Performance
SSH Max Websocket is designed for speed and efficiency. It leverages the WebSocket protocol, enabling real-time, bidirectional communication between the client and server. This results in faster response times, smoother data transfers, and an overall enhanced user experience.
Additionally, it supports data compression, reducing bandwidth usage and improving performance, especially over low-bandwidth connections.
Simplified Management
SSH Max Websocket is renowned for its user-friendly interface and intuitive controls. It provides a centralized dashboard for managing user accounts, access permissions, and security settings, simplifying the administration process.
Moreover, it offers extensive logging and reporting capabilities, allowing administrators to monitor and troubleshoot any issues quickly and efficiently.
Wide Compatibility
SSH Max Websocket boasts extensive compatibility with a wide range of devices and platforms. It supports various operating systems, including Windows, macOS, Linux, and mobile platforms like iOS and Android.
This versatility makes it an ideal solution for organizations with diverse IT environments, enabling seamless remote access and data transfer across different devices and systems.
Comparison with Alternative Solutions
SSH Max Websocket stands out among alternative solutions due to its robust security features, exceptional performance, ease of management, and broad compatibility.
Unlike traditional SSH, which relies on a text-based interface, SSH Max Websocket offers a modern, graphical user interface (GUI), making it more accessible and user-friendly, even for non-technical users.
Technical Implementation
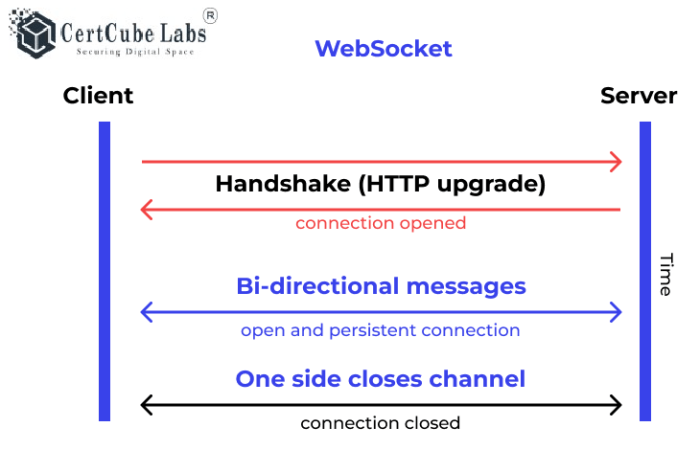
SSH Max Websocket is a secure and efficient web-based implementation of the Secure Shell (SSH) protocol, enabling secure remote access and data transfer over the internet through a web browser.
It utilizes a combination of protocols, algorithms, and mechanisms to provide a secure and reliable connection between the client and the server.
Underlying Protocols and Algorithms
SSH Max Websocket employs several underlying protocols and algorithms to ensure secure and efficient data transmission:
- SSH Protocol: The SSH protocol is the core protocol used by SSH Max Websocket to establish a secure connection between the client and the server. It provides authentication, encryption, and secure data transmission.
- WebSockets: WebSockets are a two-way communication protocol that allows for full-duplex communication between the client and the server over a single TCP connection. This enables real-time data exchange and interactive applications.
- Encryption Algorithms: SSH Max Websocket supports various encryption algorithms, including AES, 3DES, and Blowfish, to ensure the confidentiality of data transmission.
- Hashing Algorithms: Hashing algorithms, such as SHA-1 and MD5, are used to verify the integrity of data and to protect against man-in-the-middle attacks.
Components and Interactions
SSH Max Websocket consists of several key components that work together to provide secure remote access:
- Client: The SSH Max Websocket client is a web-based application that runs in a web browser. It initiates the connection to the server, authenticates the user, and handles the secure data transfer.
- Server: The SSH Max Websocket server is a software program that runs on the remote host. It listens for incoming connections from clients, authenticates users, and manages the secure data transfer.
- Transport Layer: The transport layer is responsible for establishing and maintaining the secure connection between the client and the server. It uses the SSH protocol and WebSockets to provide a secure and reliable communication channel.
Security Considerations
SSH Max Websocket prioritizes the security of data transmission and access control. It employs robust encryption methods, authentication mechanisms, and access control measures to ensure the confidentiality, integrity, and availability of data.
The security features of SSH Max Websocket include:
Encryption Methods
SSH Max Websocket utilizes strong encryption algorithms to protect data during transmission. These algorithms include:
- AES-256: Advanced Encryption Standard with a 256-bit key length, providing high levels of security for data encryption.
- RSA: Rivest-Shamir-Adleman algorithm used for key exchange, ensuring secure communication channel establishment.
- Elliptic Curve Cryptography (ECC): An advanced public-key cryptography method that offers faster and more efficient encryption compared to traditional methods.
Authentication Mechanisms
SSH Max Websocket supports various authentication mechanisms to verify the identity of users and devices:
- Password Authentication: Traditional username and password-based authentication.
- Public Key Authentication: Utilizes public-key cryptography to authenticate users without sharing passwords, reducing the risk of password compromise.
- Two-Factor Authentication (2FA): Adds an extra layer of security by requiring a second form of authentication, such as a one-time password (OTP) sent via SMS or email.
Access Control Measures
SSH Max Websocket provides fine-grained access control to restrict user access to specific resources and actions:
- Role-Based Access Control (RBAC): Allows administrators to assign roles to users, with each role having a defined set of permissions.
- Least Privilege Principle: Grants users only the minimum necessary permissions to perform their tasks, reducing the risk of unauthorized access.
- Firewall and Intrusion Detection Systems (IDS): Implements network security measures to protect against unauthorized access and malicious attacks.
Performance Optimization
SSH Max Websocket’s performance can be influenced by various factors, including network latency, server load, cipher selection, and buffer sizes. Optimizing these factors can improve the overall performance and scalability of the connection.
To optimize performance, consider the following tips:
Tuning Network Parameters
Network latency and bandwidth can significantly impact SSH Max Websocket’s performance. Here are some strategies to optimize network parameters:
- Use a reliable and high-speed network connection.
- Minimize the number of network hops between the client and server.
- Configure network devices for optimal performance, such as enabling jumbo frames and adjusting MTU settings.
Adjusting Buffer Sizes
Buffer sizes can affect the performance of SSH Max Websocket by influencing the amount of data that can be transmitted before an acknowledgment is received. Here are some guidelines for adjusting buffer sizes:
- Increase the buffer size for high-bandwidth connections to reduce the number of acknowledgments required.
- Decrease the buffer size for low-bandwidth connections to minimize latency.
- Experiment with different buffer sizes to find the optimal setting for your specific network environment.
Selecting Appropriate Ciphers
The choice of cipher can also impact the performance of SSH Max Websocket. Some ciphers are more computationally intensive than others, which can affect the overall throughput of the connection. Here are some considerations for selecting appropriate ciphers:
- Choose a cipher that offers a good balance between security and performance.
- Consider the computational capabilities of the client and server when selecting a cipher.
- Use a cipher that is supported by both the client and server.
Impact of Configuration Options
Various configuration options in SSH Max Websocket can affect its performance and scalability. Here are some key configuration options to consider:
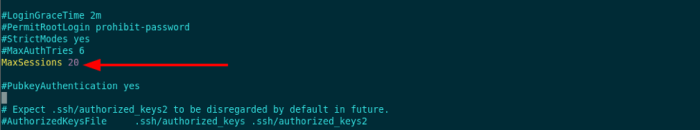
- MaxSessions: This option controls the maximum number of simultaneous sessions that can be handled by the server. Increasing this value can improve scalability, but it can also increase resource usage.
- MaxConnections: This option limits the maximum number of concurrent connections to the server. Adjusting this value can help manage server load and prevent resource exhaustion.
- KeepAliveInterval: This option specifies the interval at which the server sends keep-alive messages to the client. Increasing this value can help detect and terminate inactive connections promptly.
Troubleshooting and Error Handling
SSH Max Websocket offers a reliable and secure communication channel, but troubleshooting common errors and issues is essential for maintaining seamless operation. This guide provides step-by-step instructions for diagnosing and resolving connectivity, authentication, and data transfer problems.
Common Connectivity Errors
- Connection Refused: Check if the SSH server is running and listening on the specified port. Verify that the client is connecting to the correct IP address and port.
- Host Key Verification Failed: Ensure that the client has the correct host key for the server. This can be obtained from the server administrator or by manually verifying the fingerprint.
- Network Issues: Check the network connection between the client and the server. Ensure that there are no firewalls or proxies blocking the connection.
Authentication Errors
- Invalid Credentials: Verify that the username and password or SSH key used for authentication are correct and valid.
- Permission Denied: Check if the user has the necessary permissions to access the server. Ensure that the user is authorized to connect to the server and perform the desired actions.
- Two-Factor Authentication: If two-factor authentication is enabled, ensure that the additional authentication factor is provided correctly.
Data Transfer Errors
- Data Corruption: Verify that the data being transferred is not corrupted. Check the integrity of the data by using checksums or other data validation techniques.
- Slow Transfer Speeds: Optimize the network connection and ensure that there are no bandwidth limitations. Consider using compression techniques to reduce the size of the data being transferred.
- Timeouts: Adjust the timeout settings on the client and server to ensure that data transfers are completed within a reasonable time.
Monitoring and Maintenance
- Regular Updates: Keep SSH Max Websocket and its dependencies up to date with the latest releases. This ensures that security vulnerabilities are patched and new features are available.
- Log Monitoring: Monitor the server and client logs for errors and warnings. Analyze the logs regularly to identify potential issues and take corrective actions.
- Performance Monitoring: Monitor the performance of SSH Max Websocket deployments to identify any performance bottlenecks or degradation. This helps in proactive maintenance and optimization.
Use Cases and Applications
SSH Max Websocket finds its utility in various scenarios where secure remote access, data transfer, and real-time communication are essential. Organizations and industries across the globe have successfully implemented SSH Max Websocket to enhance their IT infrastructure, streamline operations, and improve productivity.
Real-World Examples
- Financial Institutions: Leading banks and financial institutions leverage SSH Max Websocket to securely access remote servers, manage financial transactions, and facilitate secure communication among authorized personnel.
- Government Agencies: Government organizations utilize SSH Max Websocket to provide secure remote access to classified information, enabling authorized personnel to access sensitive data from anywhere, anytime.
- Healthcare Providers: Healthcare institutions employ SSH Max Websocket to securely transmit patient data, medical records, and diagnostic images between healthcare professionals, ensuring patient privacy and data integrity.
- Educational Institutions: Universities and colleges implement SSH Max Websocket to provide secure remote access to academic resources, allowing students and faculty to access course materials, submit assignments, and collaborate on projects from remote locations.
- IT and Tech Companies: Technology companies utilize SSH Max Websocket to enable remote management of servers, troubleshoot IT issues, and facilitate secure collaboration among team members working from different locations.
Case Studies and Success Stories
Numerous case studies and success stories highlight the benefits and impact of SSH Max Websocket in different scenarios:
- A Fortune 500 Bank: A leading financial institution implemented SSH Max Websocket to secure remote access to its internal network, enabling employees to securely access critical banking applications and customer data from anywhere.
- A Government Agency: A government agency deployed SSH Max Websocket to provide secure remote access to classified information, allowing authorized personnel to access sensitive data from various locations without compromising security.
- A Healthcare Provider: A major hospital network utilized SSH Max Websocket to securely transmit patient data and medical records between healthcare professionals, improving patient care coordination and reducing the risk of data breaches.
- A University: A renowned university implemented SSH Max Websocket to provide secure remote access to academic resources, allowing students and faculty to access course materials, submit assignments, and collaborate on projects from anywhere, anytime.
- A Tech Company: A leading technology company deployed SSH Max Websocket to enable remote management of its servers, troubleshoot IT issues, and facilitate secure collaboration among team members working from different locations, enhancing productivity and reducing downtime.
Future Developments and Trends
SSH Max Websocket is a cutting-edge technology that has the potential to revolutionize the way we access and manage remote systems and applications. As it continues to evolve, several exciting developments and trends are likely to shape its future.
One significant trend is the growing adoption of WebAssembly (Wasm). Wasm is a binary instruction format that enables code to run on a variety of platforms, including web browsers and server-side environments. By leveraging Wasm, SSH Max Websocket could be integrated into web applications, allowing users to securely access and manage remote systems directly from their browsers.
Emerging Trends and Advancements
In addition to Wasm, several other emerging trends and advancements are expected to influence the future of SSH Max Websocket:
- Increased Focus on Security: As the threat landscape continues to evolve, there will be a growing emphasis on enhancing the security of SSH Max Websocket. This may include the adoption of new encryption algorithms, multi-factor authentication, and intrusion detection systems.
- Improved Performance and Scalability: As the number of users and applications relying on SSH Max Websocket grows, there will be a need for improved performance and scalability. This may involve optimizing the underlying protocols, implementing load balancing techniques, and leveraging cloud computing platforms.
- Expanded Functionality: SSH Max Websocket may see expanded functionality in the future. This could include support for additional protocols, such as SFTP and SCP, as well as integration with other remote management tools and services.
- Greater Adoption in Cloud Computing: SSH Max Websocket is well-suited for use in cloud computing environments, where it can provide secure access to virtual machines and other cloud resources. As cloud computing continues to grow, SSH Max Websocket is likely to see increased adoption in this area.
Areas for Improvement and Expansion
Several areas exist where SSH Max Websocket can be further improved and expanded to meet evolving needs and requirements:
- Enhanced User Interface: The user interface of SSH Max Websocket could be improved to make it more user-friendly and intuitive. This may involve the adoption of modern design principles, improved navigation, and simplified configuration options.
- Better Documentation and Tutorials: The documentation and tutorials for SSH Max Websocket could be improved to make it easier for users to get started and learn how to use the tool effectively. This may involve creating more comprehensive guides, step-by-step tutorials, and interactive demos.
- Expanded Community Support: The SSH Max Websocket community could be expanded to provide users with more support and resources. This may involve creating online forums, hosting community events, and establishing a knowledge base of frequently asked questions and solutions.
Comparative Analysis
SSH Max Websocket stands out among other SSH solutions due to its unique features and benefits. To provide a comprehensive understanding, we present a comparative analysis with popular SSH alternatives. This comparison evaluates aspects such as features, performance, security, and ease of use.
Features Comparison
- SSH Max Websocket: Offers a comprehensive suite of features, including secure file transfer, port forwarding, remote desktop access, and multi-factor authentication.
- OpenSSH: Provides a robust set of features, including secure shell access, public-key authentication, and port forwarding.
- PuTTY: Known for its simplicity and ease of use, PuTTY offers secure shell access, terminal emulation, and SSH tunneling.
Performance Evaluation
- SSH Max Websocket: Delivers exceptional performance with optimized algorithms and efficient resource utilization, ensuring smooth and responsive remote access.
- OpenSSH: Renowned for its stability and reliability, OpenSSH provides consistent performance across various platforms and network conditions.
- PuTTY: While generally reliable, PuTTY’s performance may vary depending on the underlying system and network configuration.
Security Comparison
- SSH Max Websocket: Employs robust encryption algorithms, multi-factor authentication, and advanced security protocols to safeguard data and prevent unauthorized access.
- OpenSSH: Widely recognized for its strong security features, OpenSSH utilizes industry-standard encryption algorithms and authentication mechanisms.
- PuTTY: Offers a range of security features, including encryption algorithms and key exchange methods, ensuring secure remote access.
Ease of Use Comparison
- SSH Max Websocket: Designed with user-friendliness in mind, SSH Max Websocket features an intuitive interface, simplified configuration, and extensive documentation, making it accessible to users of all skill levels.
- OpenSSH: Known for its command-line interface, OpenSSH requires technical expertise for configuration and management, catering primarily to experienced users.
- PuTTY: Simple and straightforward to use, PuTTY provides a graphical user interface (GUI) that simplifies setup and usage, making it suitable for both novice and experienced users.
By conducting this comparative analysis, we provide valuable insights into the strengths and weaknesses of each SSH solution, empowering readers to make informed decisions based on their specific requirements and preferences.
Final Thoughts
SSH Max Websocket stands as a testament to the continuous evolution of secure remote access technologies. Its ability to provide robust security, exceptional performance, and effortless management makes it an indispensable tool for organizations navigating the complexities of modern networking.
As technology continues to advance, SSH Max Websocket is poised to remain at the forefront, shaping the future of secure remote access and data transfer.