ssh.sshslowdns.com – In the realm of cybersecurity, split tunneling with WireGuard has emerged as a revolutionary concept, offering a unique blend of enhanced network security and privacy. This innovative technique allows you to selectively route specific network traffic through a VPN connection while leaving other traffic unaffected, providing unparalleled flexibility and control over your online activities.
WireGuard, renowned for its simplicity, speed, and robust encryption, forms the foundation of this split tunneling approach. By leveraging WireGuard’s advanced capabilities, split tunneling empowers users to establish secure connections to remote networks without compromising the performance or accessibility of their local network resources.
Split Tunneling with WireGuard
Split tunneling is a feature of WireGuard that allows you to selectively route traffic through the VPN tunnel. This can be useful for optimizing performance and security by only sending traffic that needs to be encrypted through the VPN, while allowing other traffic to bypass the VPN.
To use Split Tunnel WireGuard, you need to specify which traffic should be sent through the VPN tunnel in the WireGuard configuration file. You can do this by using the AllowedIPs and ExcludedIPs directives.
Benefits of Split Tunneling with WireGuard
- Improved performance: By only sending traffic that needs to be encrypted through the VPN, you can reduce the overhead and latency associated with the VPN connection.
- Increased security: By only sending sensitive traffic through the VPN, you can reduce the risk of data leaks.
- More flexibility: Split tunneling allows you to customize the VPN connection to meet your specific needs.
Limitations of Split Tunnel WireGuard
- Increased complexity: Split tunneling can be more complex to configure than a traditional VPN connection.
- Potential security risks: If the split tunneling configuration is not properly configured, it could create security risks.
- Not all applications support split tunneling: Some applications may not be able to work properly with split tunneling.
Configuring Split Tunneling with WireGuard

To configure split tunneling with WireGuard, follow these steps:
- Install WireGuard on your device.
- Create a WireGuard configuration file that includes the following settings:
- The IP address of the WireGuard server.
- The port number of the WireGuard server.
- Your public key.
- The private key of the WireGuard server.
- The list of IP addresses that you want to exclude from the VPN tunnel.
- Activate the WireGuard configuration file.
- Test the WireGuard connection by pinging an IP address outside of the VPN tunnel.
Troubleshooting Split Tunneling with WireGuard
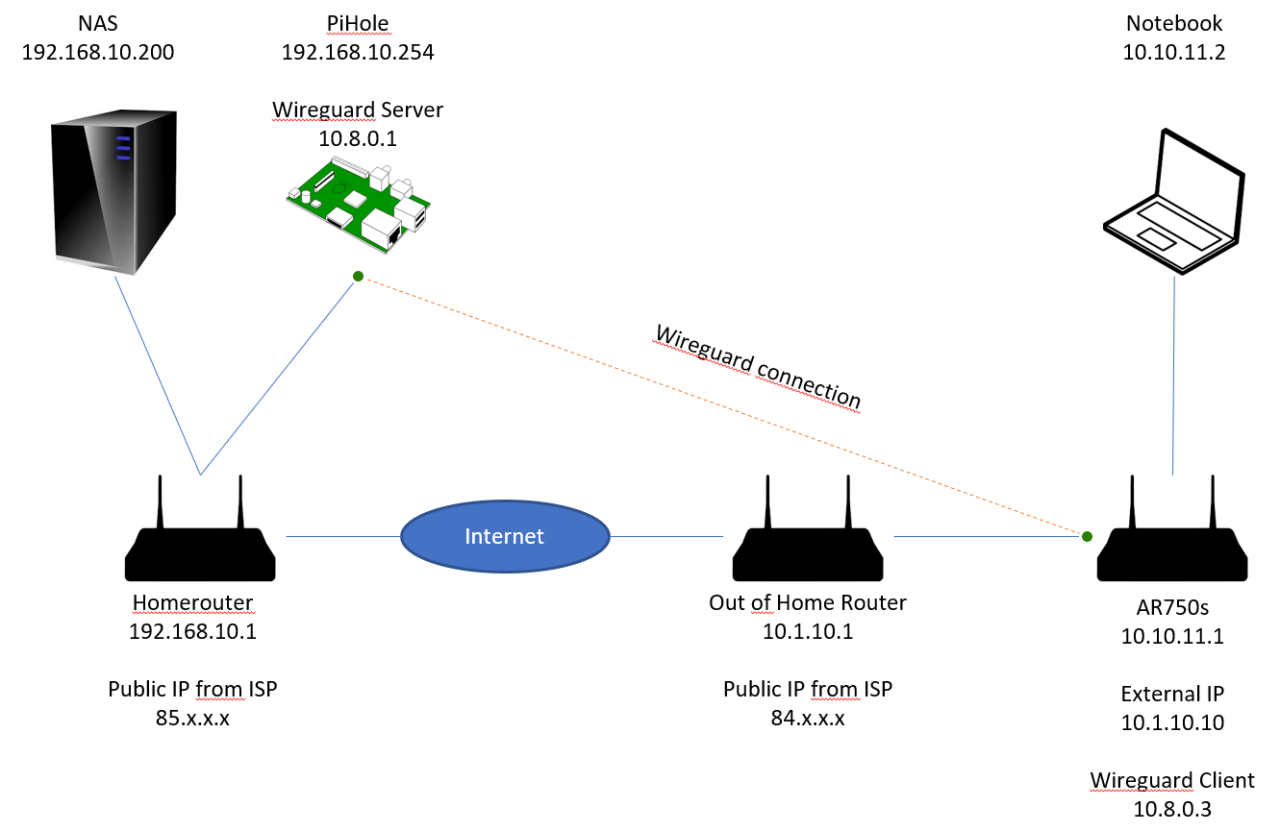
Implementing split tunneling with WireGuard can be a complex process, and several common problems can arise during setup and usage. Understanding these issues and their potential solutions can help ensure a smooth and efficient split tunneling experience.
Identifying Common Problems
Some common problems that may occur when using split tunneling with WireGuard include:
- Inability to access specific websites or services
- Slow or unstable internet connection
- DNS resolution issues
- IPv6 connectivity problems
- Configuration errors
Solutions and Workarounds
To address these problems, consider the following solutions and workarounds:
- Inability to access specific websites or services: Ensure that the target websites or services are not included in the excluded routes. Check the WireGuard configuration to verify that the correct IP ranges or domains are specified.
- Slow or unstable internet connection: Verify that the WireGuard tunnel is not overloading the network bandwidth. Adjust the MTU settings or consider using a different WireGuard server with a faster connection.
- DNS resolution issues: Configure custom DNS servers within the WireGuard configuration. Alternatively, use a DNS proxy or manually configure DNS settings on the client devices.
- IPv6 connectivity problems: Ensure that both the WireGuard server and client support IPv6. Check the configuration to enable IPv6 forwarding and verify that the client devices have IPv6 addresses assigned.
- Configuration errors: Carefully review the WireGuard configuration files for any syntax errors or incorrect settings. Use a configuration validator or seek assistance from the WireGuard community.
Security Considerations for Split Tunneling with WireGuard
Split tunneling with WireGuard introduces specific security considerations that must be addressed to maintain the overall security of your network. Understanding these implications and implementing appropriate mitigation strategies is crucial to ensure the confidentiality, integrity, and availability of your sensitive data.
Potential Security Risks
By default, split tunneling allows specific traffic to bypass the WireGuard tunnel, potentially exposing it to untrusted networks. This can lead to:
- Data Leakage: Sensitive data transmitted outside the tunnel can be intercepted and compromised by malicious actors.
- DNS Hijacking: Split tunneling can allow attackers to redirect DNS requests outside the tunnel, leading to phishing or malware attacks.
- Man-in-the-Middle Attacks: Attackers can intercept and modify traffic outside the tunnel, potentially impersonating legitimate servers or injecting malicious code.
Mitigation Strategies
To mitigate these risks, consider the following strategies:
- Limit Excluded Traffic: Restrict the types of traffic that can bypass the tunnel to only essential services, such as local network access or specific applications.
- Use Strong Encryption: Ensure that the WireGuard tunnel uses strong encryption algorithms, such as ChaCha20 or AES-256, to protect data from interception.
- Monitor Traffic: Regularly monitor network traffic to detect any suspicious activity or deviations from expected patterns.
- Implement Additional Security Measures: Consider implementing additional security measures, such as firewalls or intrusion detection systems, to enhance overall network protection.
By implementing these mitigation strategies, you can effectively reduce the security risks associated with split tunneling with WireGuard and maintain the confidentiality, integrity, and availability of your sensitive data.
Performance Impact of Split Tunneling with WireGuard
Split tunneling with WireGuard can impact performance, as it involves additional processing and routing overhead. The performance impact depends on several factors, including:
Network configuration
The performance impact can vary depending on the network configuration, such as the number of devices connected to the VPN, the bandwidth available, and the latency between the devices.
Traffic patterns
The performance impact can also be affected by the traffic patterns, such as the size and frequency of the packets being transmitted.In general, split tunneling with WireGuard can introduce a small amount of latency, as the traffic needs to be inspected and routed differently.
However, the impact is typically minimal and should not be noticeable for most users.To compare the performance with and without split tunneling enabled, you can run speed tests and measure the latency. You can use tools like iperf or speedtest-cli to measure the bandwidth and latency.Here
is an example of how to measure the performance impact of split tunneling with WireGuard:
- Enable split tunneling on your WireGuard client.
- Run a speed test to measure the bandwidth and latency.
- Disable split tunneling on your WireGuard client.
- Run a speed test again to measure the bandwidth and latency.
By comparing the results of the two speed tests, you can see the performance impact of split tunneling.
Use Cases for Split Tunneling with WireGuard
Split tunneling with WireGuard offers a unique approach to network security and privacy, enabling users to selectively route specific traffic through the VPN tunnel while allowing other traffic to bypass it. This flexibility unlocks a wide range of use cases that can enhance both personal and organizational network configurations.
One compelling use case is for individuals who want to access region-locked content while maintaining a secure connection for sensitive data. By routing only the traffic related to the streaming service through the VPN tunnel, users can enjoy geo-restricted content without compromising their online privacy.
Security and Privacy
- Enhanced Data Protection: Split tunneling allows users to protect sensitive data and applications, such as banking or healthcare information, by routing them through the encrypted VPN tunnel while keeping general browsing traffic outside the tunnel.
- Protection from Local Network Threats: By isolating VPN traffic, split tunneling mitigates the risk of malware or malicious actors on the local network from accessing or compromising sensitive data.
Convenience and Flexibility
- Improved Network Performance: By excluding non-essential traffic from the VPN tunnel, split tunneling optimizes network performance for applications that require low latency or high bandwidth.
- Access to Local Resources: Split tunneling enables users to access local network resources, such as printers or file servers, without the need to connect to the VPN.
Comparison with Other VPN Technologies
Split tunneling with WireGuard offers several advantages and disadvantages compared to split tunneling with other VPN technologies.
One of the key advantages of WireGuard is its simplicity. WireGuard is a relatively new VPN protocol, and it was designed with simplicity in mind. This makes it easier to configure and use than some other VPN protocols, such as OpenVPN.
Another advantage of WireGuard is its speed. WireGuard is one of the fastest VPN protocols available, and it can provide speeds that are comparable to unencrypted connections.
However, WireGuard also has some disadvantages. One disadvantage is that it is not as well-supported as some other VPN protocols. This means that it may not be compatible with all devices and operating systems.
Another disadvantage of WireGuard is that it is not as secure as some other VPN protocols. WireGuard uses a different encryption algorithm than other VPN protocols, and this algorithm is not as well-tested.
IPsec
IPsec is a suite of protocols that can be used to provide secure communication over IP networks. IPsec can be used to implement split tunneling, and it offers several advantages over WireGuard.
One advantage of IPsec is that it is well-supported. IPsec is a mature technology, and it is supported by a wide range of devices and operating systems.
Another advantage of IPsec is that it is secure. IPsec uses a variety of encryption algorithms, and it is considered to be one of the most secure VPN protocols available.
However, IPsec also has some disadvantages. One disadvantage is that it is complex to configure. IPsec is a complex protocol, and it can be difficult to configure correctly.
Another disadvantage of IPsec is that it can be slow. IPsec can add significant overhead to network traffic, and this can slow down network performance.
OpenVPN
OpenVPN is a popular open-source VPN protocol. OpenVPN can be used to implement split tunneling, and it offers several advantages over WireGuard.
One advantage of OpenVPN is that it is well-supported. OpenVPN is a mature technology, and it is supported by a wide range of devices and operating systems.
Another advantage of OpenVPN is that it is secure. OpenVPN uses a variety of encryption algorithms, and it is considered to be one of the most secure VPN protocols available.
However, OpenVPN also has some disadvantages. One disadvantage is that it is complex to configure. OpenVPN is a complex protocol, and it can be difficult to configure correctly.
Another disadvantage of OpenVPN is that it can be slow. OpenVPN can add significant overhead to network traffic, and this can slow down network performance.
Best Practices for Using Split Tunnel WireGuard
To optimize the performance and security of split tunneling with WireGuard, follow these best practices:
Configuration
- Configure the WireGuard client to use the split tunneling feature.
- Specify the IP addresses or subnets that should be excluded from the VPN tunnel.
- Use a firewall to block traffic from excluded networks from entering the VPN tunnel.
Performance
- Use a high-performance WireGuard server.
- Limit the number of excluded networks to improve performance.
- Configure the WireGuard client to use a fast encryption algorithm.
Security
- Use strong encryption algorithms to protect data transmitted over the VPN tunnel.
- Enable two-factor authentication for WireGuard access.
- Monitor the WireGuard server and client logs for suspicious activity.
Advanced Configuration Options for Split Tunneling with WireGuard
Advanced configuration options allow for further customization of split tunneling with WireGuard. These options can enhance performance, security, or both.
Performance Optimization
- MTU Size: Adjusts the Maximum Transmission Unit (MTU) size for WireGuard packets. Optimizing MTU can improve performance by reducing packet fragmentation.
- Buffer Bloating: Configures buffer settings to prevent network congestion and maintain optimal performance.
- WireGuard Interface Priority: Assigns a priority to the WireGuard interface, influencing how network traffic is handled.
Security Enhancements
- AllowLocal: Controls whether local traffic is allowed through the WireGuard tunnel, enhancing security by isolating local network resources.
- ListenPort: Specifies the port number for WireGuard to listen on, improving security by customizing the listening port.
- PostUp and PostDown Scripts: Enables the execution of custom scripts when the WireGuard interface is brought up or down, enhancing automation and security.
Additional Options
- AllowedIPs: Defines specific IP addresses or subnets that can access the WireGuard tunnel.
- Endpoint Address: Sets a specific IP address for the WireGuard endpoint, providing more control over IP allocation.
- Keepalive: Configures the interval for sending keepalive packets, maintaining a stable connection.
Future Developments for Split Tunneling with WireGuard
Split tunneling with WireGuard is a relatively new technology, and there are several potential future developments that could improve its functionality and usability.One area of development is the integration of split tunneling with other VPN technologies. This would allow users to combine the benefits of split tunneling with the security and privacy features of other VPN protocols.
For example, users could use split tunneling with WireGuard to access local resources while using a traditional VPN protocol to protect their online traffic.Another area of development is the automation of split tunneling rules. Currently, users must manually configure split tunneling rules, which can be time-consuming and error-prone.
In the future, it is likely that split tunneling rules will be automated, making it easier for users to manage their VPN connections.Finally, it is likely that WireGuard itself will continue to evolve, which could lead to new features and improvements for split tunneling.
For example, future versions of WireGuard may include support for IPv6, which would allow users to split tunnel their IPv6 traffic.