In the realm of cybersecurity, split tunneling emerges as a game-changer, enabling a secure and efficient way to access both public and private networks simultaneously. When combined with the cutting-edge WireGuard protocol, this powerful technique unlocks unparalleled levels of protection and performance.
Split tunnel WireGuard empowers users to selectively route specific traffic through an encrypted VPN tunnel while allowing other traffic to flow directly through their local internet connection. This granular control provides a unique balance of security and convenience, catering to the diverse needs of individuals and organizations alike.
Split Tunneling Overview

Split tunneling is a networking technique that allows specific network traffic to bypass a virtual private network (VPN) while other traffic is routed through the VPN.
The purpose of split tunneling is to provide more flexibility and control over network traffic. For example, a user may want to access local network resources while also using a VPN to protect their internet traffic from snooping or censorship.
Benefits of Split Tunneling
- Improved performance for local network access
- Reduced VPN overhead
- Increased flexibility and control over network traffic
Limitations of Split Tunneling
- Increased security risks
- More complex to configure
- May not be supported by all VPN providers
WireGuard Overview
WireGuard is a modern VPN protocol that offers a unique combination of speed, security, and ease of use. It is designed to be more efficient and secure than traditional VPN protocols like OpenVPN and IPsec.
Features and Benefits of WireGuard
- High speed: WireGuard uses a modern cryptographic algorithm called ChaCha20 that is significantly faster than the algorithms used by other VPN protocols.
- Strong security: WireGuard uses state-of-the-art cryptography to protect your data from eavesdropping and other attacks.
- Easy to use: WireGuard is designed to be easy to set up and use, even for non-technical users.
How WireGuard Differs from Other VPN Protocols
WireGuard differs from other VPN protocols in several key ways:
- Simplicity: WireGuard is a much simpler protocol than other VPN protocols. This makes it easier to implement and audit, and it also reduces the risk of security vulnerabilities.
- Speed: WireGuard is significantly faster than other VPN protocols. This is due to its use of a more efficient cryptographic algorithm and its streamlined design.
- Security: WireGuard uses state-of-the-art cryptography to protect your data from eavesdropping and other attacks. This makes it one of the most secure VPN protocols available.
Split Tunnel WireGuard Configuration
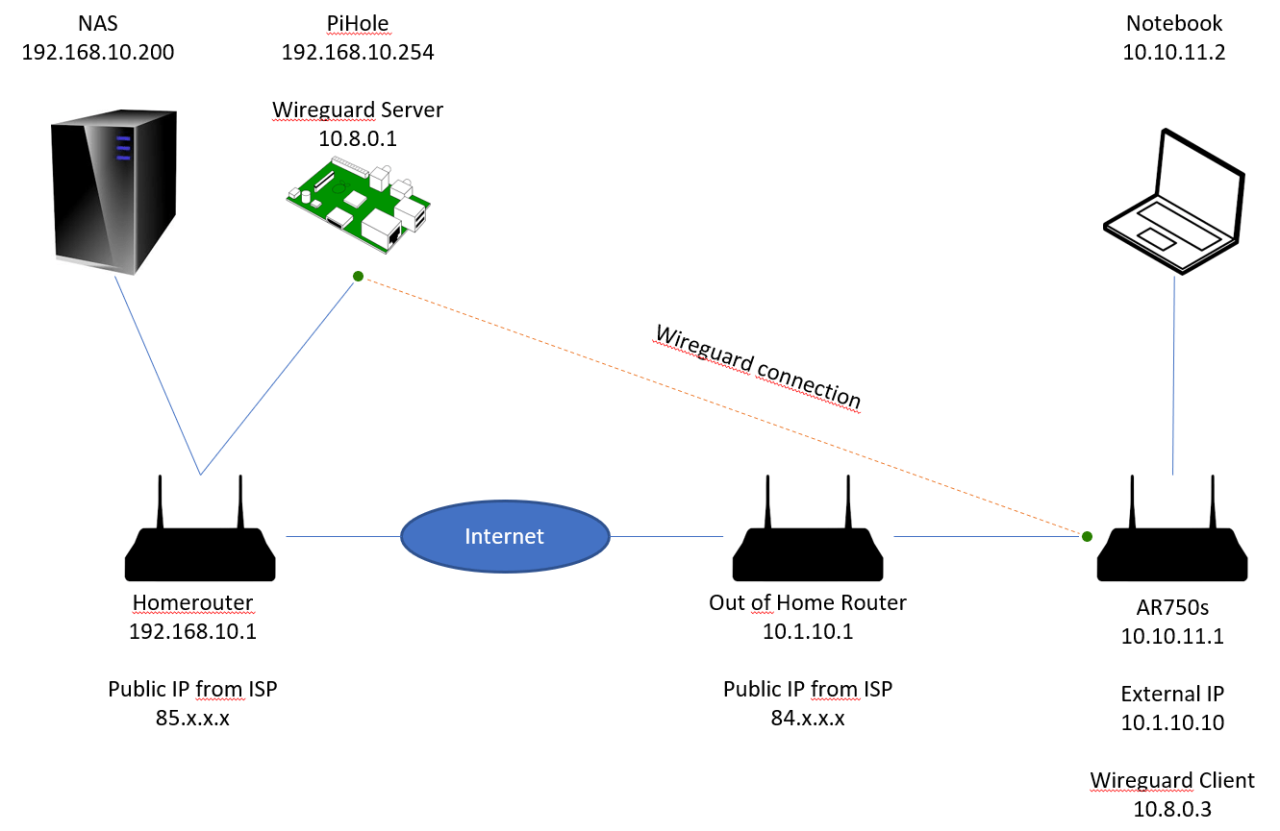
Configuring split tunnel WireGuard involves setting up a WireGuard tunnel and specifying which traffic should be routed through it. The steps vary slightly depending on the platform, but the general process is as follows:
On Linux, you can use the following commands to set up a split tunnel WireGuard interface:
- Create a WireGuard interface:
- wg-quick up wg0
- Add a rule to the iptables to route specific traffic through the WireGuard interface:
- iptables
-t mangle
-A OUTPUT
-o wg0
-j MARK
–set-mark 1 - iptables
-t mangle
-A OUTPUT
-m mark
–mark 1
-j ACCEPT
On Windows, you can use the following steps to set up a split tunnel WireGuard interface:
- Install the WireGuard client.
- Create a WireGuard configuration file.
- Import the configuration file into the WireGuard client.
- Enable the “Split Tunneling” option in the WireGuard client.
- Specify the IP addresses or subnets that should be routed through the WireGuard tunnel.
On macOS, you can use the following steps to set up a split tunnel WireGuard interface:
- Install the WireGuard client.
- Create a WireGuard configuration file.
- Import the configuration file into the WireGuard client.
- Enable the “Split Tunneling” option in the WireGuard client.
- Specify the IP addresses or subnets that should be routed through the WireGuard tunnel.
Advantages of Split Tunnel WireGuard
Split tunnel WireGuard offers several advantages over traditional VPN configurations:
Improved performance: By selectively routing only specific traffic through the VPN tunnel, split tunnel WireGuard reduces the overall network load and improves internet speeds for non-VPN-bound traffic. This is particularly beneficial for bandwidth-intensive applications or when accessing local network resources.
Enhanced security: Split tunnel WireGuard allows users to maintain a secure connection to the VPN while accessing local network resources without exposing them to the VPN tunnel. This reduces the risk of data breaches or unauthorized access to sensitive information on the local network.
Enhanced Control and Flexibility
Granular control: Split tunnel WireGuard provides granular control over which traffic is routed through the VPN tunnel, allowing users to tailor the VPN configuration to their specific needs. This flexibility enables users to optimize performance and security based on the type of traffic and the level of protection required.
Reduced Complexity
Simplified configuration: Split tunnel WireGuard simplifies VPN configuration by eliminating the need for complex routing rules or additional network infrastructure. This makes it easier to deploy and manage VPN connections, reducing the administrative overhead.
Disadvantages of Split Tunnel WireGuard
Split tunnel WireGuard, while offering advantages, also has some potential disadvantages that should be considered before implementing it.
Security Risks
One potential disadvantage is that split tunnel WireGuard may introduce security risks if not configured properly. By allowing certain traffic to bypass the VPN tunnel, it creates a potential entry point for attackers to access the internal network. If the excluded traffic includes sensitive data or applications, it could be vulnerable to interception or manipulation.
Performance Issues
Another disadvantage is that split tunnel WireGuard can potentially impact network performance. By excluding certain traffic from the VPN tunnel, it can lead to increased latency and reduced bandwidth for the excluded traffic. This can be a concern for applications that require high bandwidth or low latency, such as video conferencing or online gaming.
Use Cases for Split Tunnel WireGuard
Split tunnel WireGuard offers numerous benefits for businesses and individuals, enabling them to securely access specific resources while maintaining direct internet connectivity for other traffic.
Enhanced Security for Remote Access
Split tunnel WireGuard can enhance security for remote employees by providing a secure tunnel for accessing company resources, such as internal servers or applications, while allowing them to access the internet directly for personal use. This setup reduces the risk of data breaches or malware infections by isolating business traffic from personal traffic.
Improved Performance for Specific Applications
Split tunnel WireGuard can improve performance for specific applications by directing traffic through the VPN tunnel only when necessary. For example, a business may use WireGuard to route traffic for a CRM system through the VPN tunnel while allowing employees to access other websites and applications directly over the internet.
This approach ensures that the CRM system traffic is encrypted and protected, while maintaining optimal performance for other applications.
Cost Savings for Internet Connectivity
Split tunnel WireGuard can help businesses save on internet connectivity costs by allowing employees to use their personal internet connections for non-business traffic. This approach reduces the need for expensive business-grade internet connections, as only a portion of the traffic is routed through the VPN tunnel.
Increased Flexibility for Mobile Workers
Split tunnel WireGuard provides increased flexibility for mobile workers who frequently connect to different Wi-Fi networks. By using split tunneling, they can securely access company resources on public Wi-Fi networks while maintaining direct internet access for personal use. This flexibility allows mobile workers to stay connected and productive regardless of their location.
Comparison of Split Tunnel WireGuard to Other VPN Protocols
Split tunnel WireGuard offers advantages over other VPN protocols like OpenVPN and IPSec in terms of speed, security, and ease of use. However, it also has some limitations.
Security
WireGuard is considered more secure than OpenVPN and IPSec due to its modern cryptography and simpler codebase. It uses the ChaCha20 cipher and Poly1305 authenticator, which are both considered to be very secure. OpenVPN and IPSec, on the other hand, use older encryption algorithms that may be more vulnerable to attack.
Speed
WireGuard is significantly faster than OpenVPN and IPSec. This is because it uses a more efficient tunneling protocol that reduces overhead. In tests, WireGuard has been shown to be up to 10 times faster than OpenVPN.
Ease of Use
WireGuard is much easier to configure than OpenVPN and IPSec. It has a simple configuration file that is easy to understand and edit. OpenVPN and IPSec, on the other hand, have more complex configuration files that can be difficult to set up correctly.
Limitations
One of the main limitations of split tunnel WireGuard is that it is not as widely supported as OpenVPN and IPSec. This means that it may not be compatible with all devices and operating systems. Additionally, split tunnel WireGuard does not support all of the features that are available in OpenVPN and IPSec, such as server-side NAT traversal and multi-hop connections.Overall,
split tunnel WireGuard is a good choice for users who want a fast, secure, and easy-to-use VPN protocol. However, it is important to be aware of its limitations before making a decision.
Best Practices for Using Split Tunnel WireGuard
To ensure secure and efficient usage of split tunnel WireGuard, adhering to certain best practices is crucial. These practices encompass optimizing settings, employing effective troubleshooting techniques, and implementing security measures to safeguard your network.
Configuration Optimization
Proper configuration of WireGuard is essential for optimal performance. Consider the following tips:
- Choose an appropriate MTU size for your network to prevent fragmentation and ensure efficient data transfer.
- Enable KeepAlive to maintain a stable connection and prevent unexpected drops.
- Configure DNS settings to use a reputable and secure DNS provider for reliable and secure domain resolution.
Troubleshooting
Troubleshooting common issues can help maintain a seamless WireGuard experience. Here are some helpful approaches:
- Check firewall settings to ensure WireGuard traffic is allowed through.
- Examine routing tables to verify proper routing of traffic through the VPN tunnel.
- Inspect WireGuard logs for error messages and other diagnostic information.
Security Considerations
Security is paramount when using WireGuard. Implement these measures to protect your network:
- Use strong encryption algorithms, such as AES-256, to safeguard data transmitted over the VPN tunnel.
- Employ two-factor authentication (2FA) for added security when accessing the VPN.
- Regularly update WireGuard software to patch any vulnerabilities and ensure the latest security features are implemented.
Troubleshooting Split Tunnel WireGuard
Split tunnel WireGuard troubleshooting involves addressing connection and performance issues.
Common Connection Problems
- Interface Misconfiguration: Ensure the WireGuard interface is properly configured with the correct IP addresses, subnets, and routes.
- Firewall Blocking: Check if firewalls are blocking WireGuard traffic on the client or server side.
- DNS Issues: Verify that DNS settings are correct and that the client can resolve domain names.
Performance Optimization
- MTU Size: Adjust the MTU size to match the underlying network to improve performance.
- Cipher Selection: Choose an appropriate cipher balance between security and performance.
- Network Congestion: Identify and address network congestion that may affect WireGuard performance.
Advanced Troubleshooting
- Packet Capture Analysis: Use packet capture tools to analyze network traffic and identify issues.
- Kernel Log Examination: Review kernel logs for WireGuard-related errors or warnings.
- Community Support: Engage with the WireGuard community for assistance and troubleshooting tips.
Advanced Split Tunnel WireGuard Configuration
Split tunnel WireGuard offers advanced configuration options for tailored use cases. These settings allow for granular control over traffic routing, ensuring optimal performance and security.
Customizing WireGuard settings involves modifying the configuration file. By adjusting parameters such as allowed IP addresses, DNS settings, and firewall rules, you can achieve specific network configurations.
Customizing Allowed IP Addresses
By specifying allowed IP addresses, you can restrict WireGuard traffic to specific destinations. This is useful for scenarios where you want to exclude certain websites or services from the VPN tunnel.
To configure allowed IP addresses, add the following lines to your WireGuard configuration file:
AllowedIPs = 192.168.1.0/24AllowedIPs = 8.8.8.8/32
In this example, traffic is allowed to and from the 192.168.1.0/24 subnet and the IP address 8.8.8.8.
Closure
As we delve into the intricacies of split tunnel WireGuard, we will uncover its numerous advantages, potential drawbacks, and best practices for secure and efficient deployment. By harnessing the power of this innovative technology, you can elevate your cybersecurity posture, enhance network performance, and unlock a world of secure and seamless connectivity.