In the realm of secure remote communication, SSH (Secure Shell) plays a pivotal role. SSH protocol identification is a crucial aspect of establishing a secure connection, but its absence can raise concerns. This article delves into the causes, implications, and troubleshooting techniques for missing SSH protocol identification, ensuring seamless and secure server communication.
SSH protocol identification serves as a beacon of authenticity, verifying the server’s identity and ensuring that the connection is not compromised. Its absence can leave servers vulnerable to malicious attacks, highlighting the importance of understanding and addressing this issue.
Server Response Identification
Secure Shell (SSH) is a secure remote login and remote command execution protocol that provides a secure channel between two hosts over an insecure network.
SSH protocol identification is a mechanism used by SSH servers to identify themselves to clients. When a client connects to an SSH server, the server sends a response that includes its SSH protocol version and other information. This information helps the client to identify the server and to establish a secure connection.
Importance of SSH Protocol Identification
SSH protocol identification is important for several reasons:
- It allows clients to identify the SSH server and to establish a secure connection.
- It helps to prevent man-in-the-middle attacks, where an attacker impersonates a legitimate SSH server in order to intercept and decrypt client traffic.
- It can be used to troubleshoot SSH connectivity issues.
Causes of Missing SSH Protocol Identification
The absence of SSH protocol identification in a server response can arise due to several reasons. Understanding these causes is crucial for maintaining secure communication channels.
Malformed Response
- Corrupted or truncated packets: Network issues or software malfunctions can lead to the corruption or truncation of packets during transmission. This can result in incomplete or missing SSH protocol identification information in the server response.
- Protocol mismatch: Incompatibility between the SSH client and server versions can cause the server to send an unexpected or unsupported response. This can result in the absence of SSH protocol identification or an error message indicating protocol mismatch.
Security Vulnerabilities
- Man-in-the-middle attacks: Adversaries can intercept and manipulate network traffic, including SSH connections. They can remove or alter the SSH protocol identification to impersonate the server or eavesdrop on the communication.
- Misconfigured servers: Incorrect server configurations or outdated software can lead to vulnerabilities that allow attackers to bypass or disable SSH protocol identification mechanisms.
Implications of Missing SSH Protocol Identification
The absence of SSH protocol identification poses significant security risks:
- Compromised authentication: Without proper protocol identification, it becomes difficult to verify the authenticity of the server and ensure secure authentication.
- Increased vulnerability to attacks: Missing SSH protocol identification can make the connection susceptible to man-in-the-middle attacks and other security breaches.
- Impaired troubleshooting: The lack of SSH protocol identification information can hinder troubleshooting efforts in case of connection issues or security incidents.
Troubleshooting Techniques
If you encounter issues with missing SSH protocol identification, it is essential to identify the underlying cause to resolve the problem effectively. Here are some troubleshooting techniques to guide you:
Check SSH Client Configuration
Verify the SSH client configuration to ensure that the protocol identification is enabled. Check the SSH client’s configuration file (e.g., ~/.ssh/config) and look for settings related to protocol identification. If necessary, modify the settings to enable protocol identification.
Examine Server Configuration
Inspect the server configuration to determine if protocol identification is disabled. Access the server’s SSH configuration file (e.g., /etc/ssh/sshd_config) and search for settings related to protocol identification. Ensure that the Protocol field is set to 2, which enables protocol identification.
Network Analysis
Analyze the network traffic to identify any potential issues that may be blocking the transmission of protocol identification information. Use tools like Wireshark or tcpdump to capture and inspect the network packets exchanged during the SSH connection establishment process. Look for any abnormalities or errors that may indicate a problem with protocol identification.
Firewall Rules
Check the firewall rules on both the client and server systems to ensure that they allow the transmission of protocol identification information. Verify that the necessary ports (e.g., port 22 for SSH) are open and accessible, and that the firewall rules do not block the exchange of protocol identification data.
Update SSH Software
Ensure that both the SSH client and server software are up-to-date. Outdated software versions may have bugs or vulnerabilities that can affect protocol identification. Update the software to the latest stable release to address any potential issues.
Impact on Security
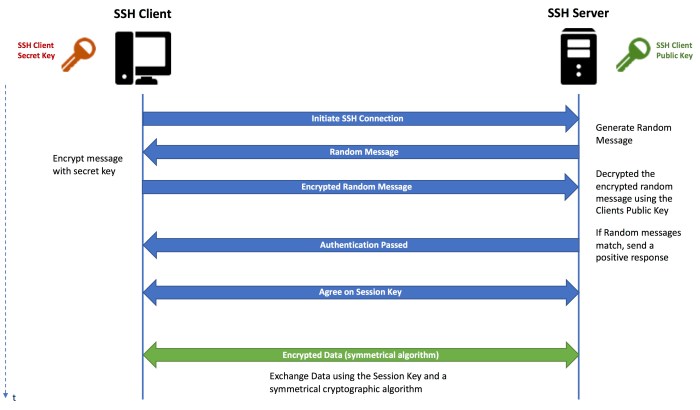
The absence of SSH protocol identification in server responses poses significant security risks, leaving systems vulnerable to a range of attacks.
Firstly, it allows attackers to impersonate legitimate SSH servers, potentially tricking users into connecting to malicious servers that can steal credentials or compromise sensitive data.
Exploitation of Protocol Vulnerabilities
Without proper protocol identification, attackers can exploit vulnerabilities in older or less secure SSH versions. They may use these vulnerabilities to gain unauthorized access to systems, elevate privileges, or launch other malicious activities.
Man-in-the-Middle Attacks
The lack of SSH protocol identification creates opportunities for man-in-the-middle attacks. Attackers can intercept and modify SSH traffic, impersonating both the client and server to steal credentials or redirect connections to malicious destinations.
Mitigation Strategies
To effectively mitigate the risks associated with missing SSH protocol identification, it is crucial to implement robust mitigation strategies that enhance server security.
One effective strategy is to enforce SSH protocol version 2 (SSHv2) on all servers. SSHv2 includes mandatory protocol identification, making it easier to detect and prevent unauthorized access attempts. Additionally, SSHv2 provides stronger encryption algorithms and improved key exchange mechanisms, further enhancing server security.
Disable SSHv1
SSHv1 is an outdated protocol that lacks essential security features, including mandatory protocol identification. By disabling SSHv1 on servers, organizations can eliminate the risk of unauthorized access attempts exploiting this vulnerability.
Implement Intrusion Detection Systems (IDS)
Intrusion detection systems (IDS) can monitor network traffic and identify suspicious activities, including attempts to exploit missing SSH protocol identification. By deploying IDS, organizations can detect and respond to unauthorized access attempts in real-time, mitigating the potential impact of a security breach.
Regular Security Audits
Regular security audits are essential for identifying vulnerabilities, including missing SSH protocol identification. By conducting thorough security audits, organizations can proactively identify and address potential security risks, ensuring that their servers are adequately protected against unauthorized access.
Alternative Authentication Methods

When SSH protocol identification is missing, alternative authentication methods can be used to establish a secure connection. These methods vary in their security and ease of use, and it is important to understand the advantages and disadvantages of each to make an informed decision.
Some of the most common alternative authentication methods include:
- Password authentication: This is the simplest and most widely used authentication method. However, it is also the least secure, as passwords can be easily stolen or guessed.
- Public-key authentication: This method uses a pair of cryptographic keys, one public and one private. The public key is stored on the server, while the private key is kept secret by the client. When a client attempts to connect to the server, the server sends the client a challenge. The client then uses its private key to decrypt the challenge and send it back to the server. If the decrypted challenge matches the original challenge, the client is authenticated.
- Kerberos authentication: This method uses a trusted third-party authentication server to authenticate clients. When a client attempts to connect to the server, the client sends a request to the authentication server. The authentication server then checks the client’s credentials and, if they are valid, issues a ticket-granting ticket (TGT) to the client. The client can then use the TGT to obtain a service ticket from the authentication server. The service ticket can then be used to authenticate the client to the server.
Best Practices for SSH Server Configuration
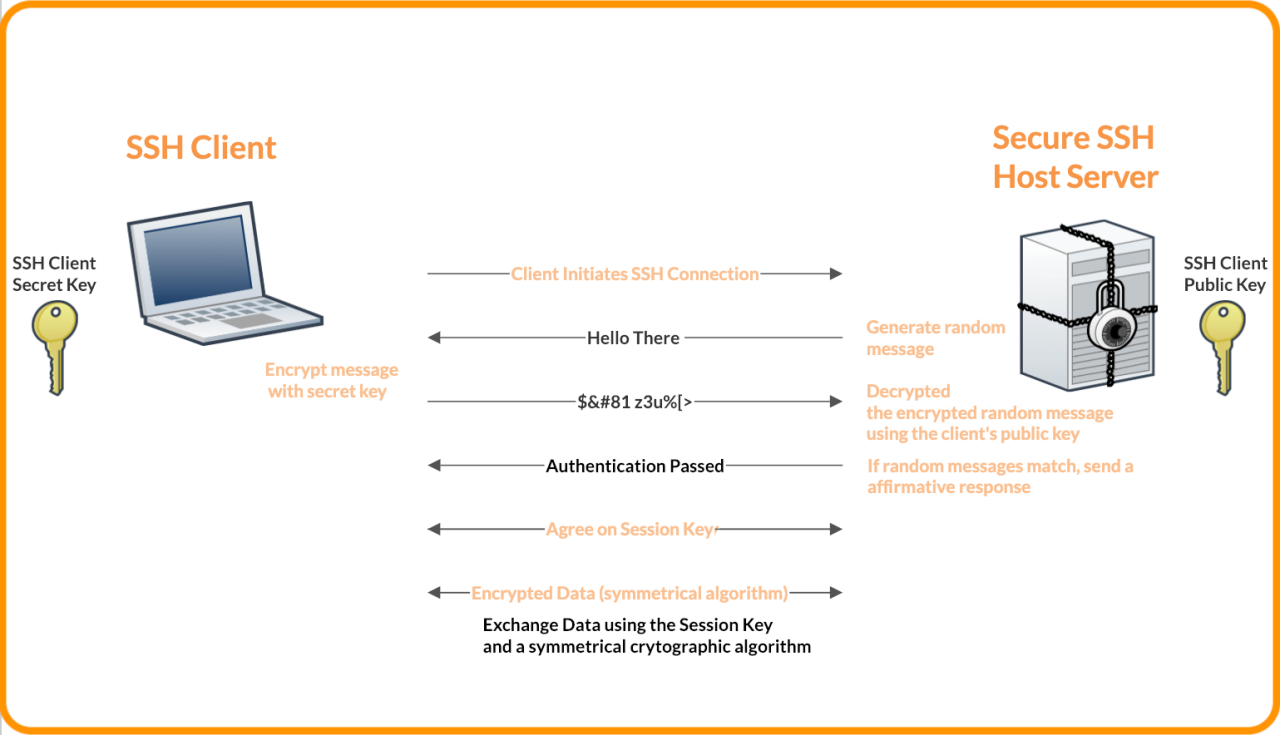
To ensure proper SSH protocol identification, follow these best practices when configuring SSH servers:
Enable SSH protocol version 2 (SSHv2): SSHv2 provides stronger encryption and authentication mechanisms than SSHv1, and it includes support for protocol identification. Configure your SSH server to use SSHv2 by default.
Use strong encryption algorithms
- Configure your SSH server to use strong encryption algorithms, such as AES-256-CBC or ChaCha20-Poly1305, to protect data transmitted over the SSH connection.
- Avoid using weak encryption algorithms, such as DES or 3DES, as they are vulnerable to attack.
Disable weak authentication methods
- Disable weak authentication methods, such as password-based authentication, as they are susceptible to brute-force attacks.
- Instead, use strong authentication methods, such as public-key authentication or two-factor authentication, to protect against unauthorized access.
Limit access to the SSH port
- Limit access to the SSH port (port 22) to only authorized users or networks.
- Use a firewall to block access to the SSH port from untrusted sources.
Enable SSH key exchange algorithms
- Enable SSH key exchange algorithms, such as Diffie-Hellman or Elliptic Curve Diffie-Hellman (ECDH), to establish a secure key exchange between the client and server.
- These algorithms provide forward secrecy, ensuring that compromised session keys cannot be used to decrypt past or future sessions.
Use a secure shell (SSH) protocol identification banner
- Configure your SSH server to display a secure shell (SSH) protocol identification banner upon connection.
- This banner should clearly identify the SSH server software and version, and it should warn users that unauthorized access is prohibited.
Regularly update SSH software
- Regularly update your SSH server software to the latest version.
- Updates often include security patches that address vulnerabilities that could allow attackers to bypass protocol identification or gain unauthorized access to the server.
Tools for Identifying SSH Protocol
To identify and analyze SSH protocol identification, various tools and techniques are available. These tools enable administrators and security professionals to troubleshoot and resolve issues related to missing SSH protocol identification.
One of the primary tools for identifying SSH protocol identification is a packet analyzer. Packet analyzers, such as Wireshark or tcpdump, capture and analyze network traffic. They can be used to examine the initial handshake between an SSH client and server, which includes the protocol identification.
By analyzing the captured packets, administrators can determine if the SSH protocol identification is present and correct.
OpenSSH
OpenSSH, an open-source implementation of the SSH protocol, provides a command-line utility called ‘ssh’ that can be used to identify SSH protocol identification. The ‘ssh’ command includes a ‘-v’ option, which enables verbose logging. When the ‘-v’ option is used, the ‘ssh’ command will output detailed information about the SSH connection, including the protocol identification.
SSH Protocol Fingerprinting
SSH protocol fingerprinting is another technique used to identify SSH protocol identification. SSH protocol fingerprinting involves analyzing the unique characteristics of an SSH server’s response to a connection request. By comparing the fingerprint of a server’s response to known SSH protocol implementations, administrators can determine the specific SSH protocol version and implementation being used.
Real-World Case Studies
Missing SSH protocol identification is a security issue that has been encountered in real-world scenarios, leading to vulnerabilities and breaches. Here are some case studies and lessons learned:
In 2016, a major cloud provider experienced a security incident where an attacker exploited a vulnerability in their SSH server configuration. The server was missing SSH protocol identification, allowing the attacker to masquerade as a legitimate SSH client and gain unauthorized access to sensitive data.
Lessons Learned
- The importance of proper SSH server configuration, including ensuring that SSH protocol identification is enabled.
- The need for continuous security monitoring and vulnerability management to identify and address potential security issues promptly.
- The value of implementing defense-in-depth strategies to mitigate the impact of security breaches.
Future Developments
As the digital landscape continues to evolve, the SSH protocol is expected to undergo further advancements and enhancements to meet the evolving security demands of modern communication.
One anticipated development is the increased adoption of quantum-resistant cryptography in SSH. Quantum computers pose a significant threat to traditional encryption algorithms, and SSH is likely to embrace quantum-safe algorithms to safeguard communications against future quantum attacks.
Enhancements in Authentication
Future versions of SSH may incorporate more sophisticated authentication mechanisms, such as multi-factor authentication or biometric identification, to strengthen the security of server access. This will help prevent unauthorized access and mitigate the risks associated with compromised passwords.
Final Conclusion
In conclusion, server response missing SSH protocol identification warrants prompt attention. By understanding the causes and implications, implementing effective troubleshooting techniques, and adopting mitigation strategies, organizations can enhance their server security and maintain seamless communication. The future holds promising developments in SSH protocol identification, further bolstering the security landscape.