When establishing a secure connection to a remote server via SSH, the server’s response plays a pivotal role in authenticating the connection. A crucial aspect of this response is the inclusion of the SSH protocol identification string. However, in certain instances, this identification may be absent, leading to connection issues and security concerns.
This article delves into the causes of this omission and provides comprehensive troubleshooting steps to resolve it.
The SSH protocol identification string serves as a unique identifier for the SSH server, enabling clients to verify the authenticity of the server and establish a secure connection. The absence of this identification can indicate various underlying issues, ranging from misconfigurations to potential security breaches.
SSH Protocol Identification
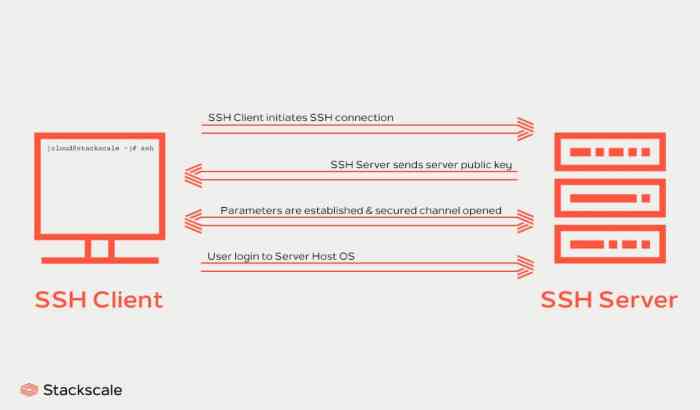
The SSH protocol identification string is a sequence of characters that identifies the SSH protocol version and the SSH server implementation. It is sent by the SSH server to the SSH client at the beginning of the SSH connection.
The SSH protocol identification string has the following format:
SSH-2.0-OpenSSH_8.4
The first field is the SSH protocol version. The second field is the SSH server implementation. The third field is the SSH server version.
The SSH protocol identification string is used by the SSH client to determine the SSH protocol version and the SSH server implementation. This information is used by the SSH client to negotiate the SSH connection parameters.
Purpose and Significance
The SSH protocol identification string is used to identify the SSH protocol version and the SSH server implementation. This information is used by the SSH client to negotiate the SSH connection parameters.
The SSH protocol identification string is also used by SSH clients to detect SSH servers that are vulnerable to security vulnerabilities. For example, the SSH protocol identification string can be used to detect SSH servers that are vulnerable to the Heartbleed vulnerability.
Examples of SSH Protocol Identification Strings
- SSH-2.0-OpenSSH_8.4
- SSH-2.0-Dropbear_2020.82
- SSH-2.0-PuTTY_0.78
Causes of Missing SSH Protocol Identification
The absence of SSH protocol identification in a server response can result from various factors, including:
- Misconfiguration: The SSH server may be incorrectly configured, leading to the omission of the protocol identification.
- Firewall Blocking: A firewall or network security device may be blocking the SSH protocol identification, preventing it from reaching the client.
- Network Issues: Network latency or packet loss can disrupt the transmission of the SSH protocol identification, resulting in its absence.
The implications of missing SSH protocol identification include:
- Security Concerns: Without the protocol identification, it becomes difficult to determine the authenticity and version of the SSH server, potentially exposing the system to security vulnerabilities.
- Troubleshooting Difficulties: The absence of protocol identification makes it challenging to troubleshoot SSH connectivity issues, as it provides valuable information for debugging.
Scenarios of Missing SSH Protocol Identification
Examples of scenarios where SSH protocol identification may be absent include:
- A newly installed SSH server that has not been properly configured.
- A network environment where a firewall is blocking SSH traffic, including the protocol identification.
- A congested network where packet loss occurs, resulting in the loss of the protocol identification.
Troubleshooting Missing SSH Protocol Identification
If you encounter the error “SSH Protocol Identification Missing,” it’s crucial to troubleshoot the issue promptly to establish a secure SSH connection. This error indicates that the SSH server cannot verify the client’s identity using the SSH protocol.
To troubleshoot this issue, follow these steps:
Verify SSH Protocol Identification
- Check if the SSH client is using the correct SSH protocol version. SSH version 2 is the most commonly used, so ensure your client supports it.
- Verify that the SSH server is configured to accept SSH protocol version 2. You can check this in the server’s SSH configuration file.
Resolve Missing SSH Protocol Identification
- If the SSH client and server are using different SSH protocol versions, upgrade or downgrade the client to match the server’s version.
- If the SSH server is not configured to accept SSH protocol version 2, edit the server’s SSH configuration file to enable it.
- Ensure that the SSH client and server are using the same encryption algorithms. Check the configuration files of both the client and server to verify this.
- If the issue persists, check for any firewalls or network configurations that may be blocking the SSH connection.
Alternative Identification Methods
SSH servers can be identified using alternative methods when protocol identification is unavailable. These methods provide alternative ways to distinguish SSH servers from other services running on the same port.
Advantages of Alternative Identification Methods:
- Increased security: Reliance on protocol identification can be a security risk, as attackers can spoof SSH protocol identification.
- Improved compatibility: Some SSH servers may not support protocol identification, making alternative methods necessary.
Disadvantages of Alternative Identification Methods:
- Less reliable: Alternative identification methods may be less reliable than protocol identification, as they rely on other factors that can vary.
- Increased complexity: Implementing and configuring alternative identification methods can be more complex than using protocol identification.
Banner Grabbing
Banner grabbing involves sending a request to the SSH server and analyzing the response banner. SSH servers typically display a banner containing information such as the SSH version, server software, and operating system. By comparing the banner to known SSH server banners, the server can be identified.
Port Knocking
Port knocking is a technique where a specific sequence of port connections is used to identify a hidden SSH server. The SSH server listens for this sequence on a non-standard port and only responds when the correct sequence is received.
This provides an additional layer of security by hiding the SSH server from unauthorized access.
Fingerprinting
SSH fingerprinting involves collecting a unique set of characteristics from the SSH server, such as the supported encryption algorithms, key exchange methods, and packet sizes. By comparing the fingerprint to a database of known SSH server fingerprints, the server can be identified.
Best Practices
Establishing best practices is crucial for ensuring the presence of SSH protocol identification in server responses. These practices should be implemented and followed diligently to maintain consistency and security.
Guidelines for Implementation
Implement the following guidelines to ensure effective best practices:
- Configure SSH Servers: Ensure that SSH servers are configured to send the SSH protocol identification string in their responses. This can be achieved by setting the “Protocol” in the SSH configuration file.
- Use SSH Clients that Support Protocol Identification: Utilize SSH clients that support and expect the SSH protocol identification string in server responses. This ensures compatibility and proper handling of server responses.
- Monitor and Audit SSH Connections: Regularly monitor and audit SSH connections to verify the presence of the SSH protocol identification string. This helps identify any deviations or potential security issues.
Examples of Best Practices in Action
- Secure Shell (SSH) Protocol Identification: In SSH, the server responds with an identification string that includes the SSH protocol version, such as “SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.3”. This identification string helps clients verify the server’s authenticity and ensures secure communication.
- Telnet Protocol Identification: When connecting to a Telnet server, the server responds with an identification string that typically includes the Telnet protocol version, such as “Telnetd 2.7.1”. This identification string allows clients to identify the server and establish a Telnet session.
Related Protocols
SSH operates alongside other protocols, each serving specific purposes and potentially influencing SSH protocol identification.
These related protocols include:
- Telnet: A legacy protocol for remote terminal access, Telnet transmits data in clear text, making it less secure than SSH.
- FTP: File Transfer Protocol allows for file transfers between systems, but lacks the encryption and authentication features of SSH.
- SCP: Secure Copy Protocol, built on top of SSH, provides secure file transfers using SSH encryption.
- SFTP: SSH File Transfer Protocol, also leveraging SSH, offers a more secure and interactive file transfer mechanism.
Impact on SSH Protocol Identification
The presence of related protocols can affect SSH protocol identification in the following ways:
- Port Conflicts: If SSH and other protocols share the same port (e.g., 22), the initial connection attempt may not be able to identify the specific protocol.
- Protocol Negotiation: When multiple protocols are available on a port, the client and server negotiate to establish the appropriate protocol. This negotiation can impact the SSH protocol identification process.
- Protocol Hijacking: Malicious actors may attempt to hijack SSH connections by impersonating other protocols. This can lead to confusion and security breaches.
Historical Context

The SSH protocol identification has undergone significant evolution since its inception, driven by advancements in cryptography, security best practices, and the need to address evolving threats.
Initially, SSH relied on simple text-based identification, which was susceptible to eavesdropping and man-in-the-middle attacks. As the protocol matured, more robust identification mechanisms were introduced, including:
Key Exchange Algorithms
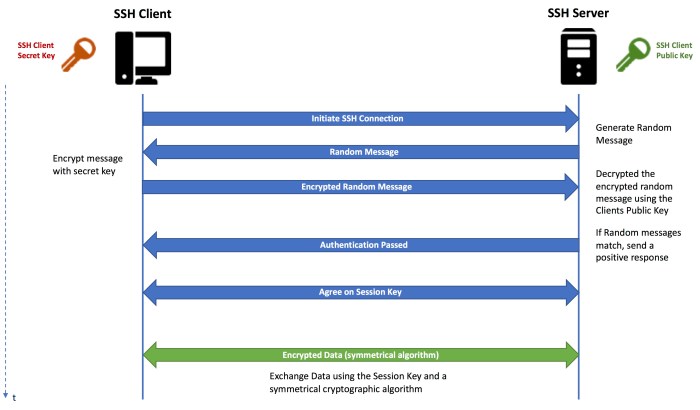
- Diffie-Hellman Key Exchange: Introduced in SSH-1, it provided a secure method for establishing a shared secret key between two parties.
- RSA Key Exchange: Added in SSH-2, it allowed for authentication using public-key cryptography, enhancing security.
- Elliptic Curve Diffie-Hellman (ECDH) Key Exchange: Introduced in SSH-2, it offered improved performance and security over Diffie-Hellman.
Authentication Methods
- Password Authentication: The traditional method of authentication, where a user provides a password to establish their identity.
- Public-Key Authentication: Introduced in SSH-2, it allows users to authenticate using a public-private key pair, enhancing security and convenience.
- Certificate-Based Authentication: Added in SSH-2, it enables authentication using digital certificates issued by trusted authorities.
Future Directions
The future of SSH protocol identification holds exciting prospects, driven by ongoing advancements in technology and the ever-evolving cybersecurity landscape. Emerging trends and innovations promise to enhance security, efficiency, and usability.
One key area of focus is the integration of artificial intelligence (AI) and machine learning (ML) algorithms. These technologies can analyze vast amounts of data to identify patterns and anomalies, enabling more accurate and proactive detection of potential threats. By leveraging AI/ML, SSH protocol identification can be made more robust and resilient against sophisticated attacks.
Enhanced Encryption Standards
The adoption of stronger encryption algorithms is another important trend. As computing power continues to increase, traditional encryption methods become more susceptible to brute-force attacks. The development and implementation of new encryption standards, such as quantum-resistant algorithms, will play a crucial role in safeguarding SSH connections against future threats.
Improved User Experience
Simplifying and streamlining the user experience is also a priority. Automated processes and user-friendly interfaces can make SSH protocol identification more accessible and less time-consuming. Additionally, the integration of mobile devices and cloud-based platforms can enhance the flexibility and convenience of SSH access.
Zero-Trust Architecture
The adoption of zero-trust architecture principles is gaining traction in the cybersecurity realm. This approach assumes that all users and devices are untrusted until they are explicitly verified. By incorporating zero-trust principles into SSH protocol identification, organizations can implement more granular access controls and reduce the risk of unauthorized access.
Summary
Understanding the causes and resolutions associated with missing SSH protocol identification is essential for maintaining secure remote connections. By implementing the best practices Artikeld in this article, system administrators can ensure the presence of SSH protocol identification in server responses, mitigating security risks and ensuring seamless SSH connectivity.