In the realm of networking, site-to-site VPNs have emerged as a crucial technology for connecting remote networks securely. Among the various VPN solutions available, pfSense and WireGuard stand out as powerful and reliable options. This guide will delve into the intricacies of pfSense WireGuard site-to-site VPNs, providing a comprehensive overview of their configuration, troubleshooting, optimization, and security considerations.
pfSense, an open-source firewall and router distribution, offers a robust platform for implementing WireGuard, a modern and efficient VPN protocol. Together, they provide a highly secure and flexible solution for establishing secure connections between geographically dispersed networks.
Introduction
Site-to-site VPNs (Virtual Private Networks) are crucial in modern networking, enabling secure and private communication between multiple networks. They establish encrypted tunnels over the internet, allowing geographically dispersed sites to connect as if they were on the same local network.
pfSense and WireGuard are renowned open-source VPN solutions that offer reliable and efficient site-to-site connectivity. pfSense is a feature-rich firewall and router distribution, while WireGuard is a cutting-edge VPN protocol known for its speed, simplicity, and security.
pfSense and WireGuard
pfSense provides a robust platform for managing site-to-site VPNs. Its user-friendly interface and extensive configuration options make it suitable for both small businesses and large enterprises. WireGuard, on the other hand, is a state-of-the-art VPN protocol that offers superior performance and reduced overhead compared to traditional protocols.
Configuring pfSense WireGuard Site-to-Site VPN
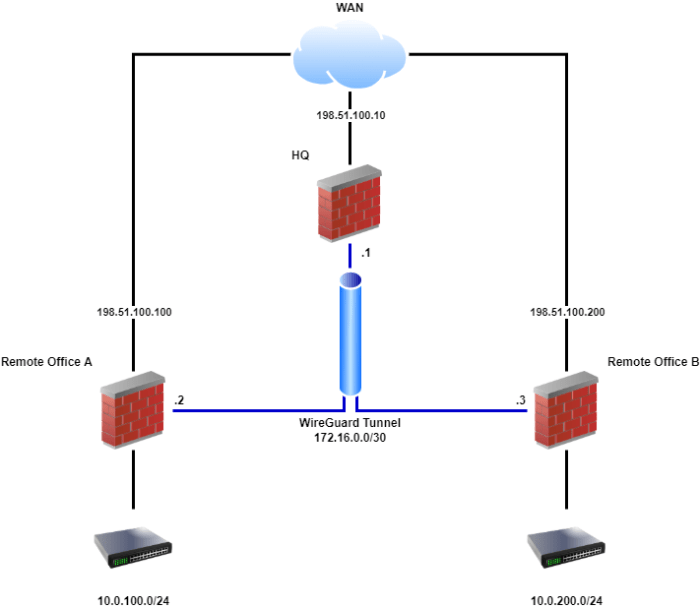
Creating a New WireGuard Interface
To establish a WireGuard site-to-site VPN, you need to create a new WireGuard interface on each pfSense firewall involved. Navigate to
- *Interfaces >
- *Assignments, click
- *Add, select
- *WireGuard, and enter a descriptive name for the interface.
Generating and Exchanging Public Keys
Next, generate public keys for each firewall. On the first firewall, go to
- *WireGuard >
- *Interfaces, click on the newly created interface, and click
- *Generate. Copy the generated public key. On the second firewall, repeat the process and copy its public key. Exchange these public keys between the two firewalls.
Configuring the WireGuard Tunnel Settings
Finally, configure the WireGuard tunnel settings. On the first firewall, go to
-
- *WireGuard >
- *Peers, click
-*Add Peer, and enter the following details
- Name: A descriptive name for the peer
- Public Key: Paste the public key of the second firewall
- Allowed IPs: Specify the IP address range or individual IP addresses that the second firewall is allowed to access
Repeat the same steps on the second firewall, using the public key of the first firewall. Click
*Save on both firewalls to activate the VPN connection.
Troubleshooting pfSense WireGuard Site-to-Site VPN

Troubleshooting pfSense WireGuard site-to-site VPNs involves identifying common issues during setup, resolving connectivity problems, and monitoring and debugging the VPN connection.
Common Issues and Solutions
Common issues during setup include incorrect configuration, firewall blocking, and routing problems. To resolve these, verify the configuration settings, check firewall rules, and ensure proper routing between the sites.
Connectivity Problems
Connectivity problems can arise due to issues such as incorrect IP addresses, mismatched keys, or network connectivity issues. To troubleshoot, check the IP addresses and keys, and verify network connectivity.
Monitoring and Debugging
Monitoring and debugging the VPN connection involves using tools like the pfSense log viewer, WireGuard status page, and packet captures. These tools help identify errors, connection issues, and performance problems.
Advanced pfSense WireGuard Site-to-Site VPN Configuration
In addition to the basic configuration, pfSense WireGuard site-to-site VPNs offer advanced features for enhanced performance and reliability.
This section explores these advanced configurations, including multiple tunnels for redundancy, load balancing, and failover mechanisms.
Configuring Multiple WireGuard Tunnels for Redundancy
Configuring multiple WireGuard tunnels between two sites provides redundancy and increased availability. If one tunnel fails, traffic can automatically failover to another active tunnel.
- Create multiple WireGuard interfaces on each pfSense firewall.
- Configure each interface with unique IP addresses and subnets.
- Assign each interface to a different WireGuard peer.
- Enable “Keepalive” to detect and recover from connection failures.
Implementing Load Balancing Across Multiple Tunnels
Load balancing distributes traffic across multiple WireGuard tunnels, improving performance and reducing latency. This is especially beneficial for high-bandwidth applications.
- Enable “Load Balancing” in the WireGuard interface settings.
- Configure the “Weight” parameter to distribute traffic based on tunnel capacity.
- Use the “Active Probing” option to monitor tunnel health and automatically adjust traffic distribution.
Setting Up Failover Mechanisms for Increased Reliability
Failover mechanisms ensure that traffic is automatically routed to a backup tunnel if the primary tunnel fails. This provides high availability and prevents disruptions.
- Configure a “Gateway” option in the WireGuard interface settings.
- Set the “Gateway” to the IP address of the backup tunnel.
- Enable “Failover” to automatically switch to the backup tunnel if the primary tunnel fails.
Performance Optimization for pfSense WireGuard Site-to-Site VPN
Optimizing the performance of your pfSense WireGuard Site-to-Site VPN can significantly enhance data transfer speeds and overall network efficiency. Here are some key strategies to consider:
Optimizing MTU Settings for Maximum Throughput
The Maximum Transmission Unit (MTU) defines the largest packet size that can be transmitted over a network. Optimizing MTU settings ensures that packets are not fragmented, reducing overhead and improving throughput. To determine the optimal MTU, consider the following steps:
- Configure the MTU to the largest possible value supported by the underlying network infrastructure.
- Use a tool like “ping
s” to test different MTU values and identify the highest value that does not result in packet fragmentation.
Enabling Hardware Acceleration for Improved Performance
Hardware acceleration can significantly improve VPN performance by offloading encryption and decryption tasks to dedicated hardware.
If your pfSense system supports hardware acceleration, enable it in the WireGuard settings to leverage its capabilities.
Configuring Traffic Shaping Rules to Prioritize VPN Traffic
Traffic shaping allows you to prioritize VPN traffic over other network traffic, ensuring that VPN connections receive the necessary bandwidth for optimal performance. To configure traffic shaping rules:
- Create a new traffic shaping rule in the pfSense firewall settings.
- Set the source and destination addresses to match your VPN subnets.
- Assign a higher priority to VPN traffic compared to other traffic classes.
Security Considerations for pfSense WireGuard Site-to-Site VPN
Implementing a pfSense WireGuard site-to-site VPN requires careful attention to security measures to ensure the confidentiality, integrity, and availability of data transmitted over the VPN connection.
Implement Strong Encryption Algorithms
WireGuard utilizes robust encryption algorithms such as ChaCha20, Curve25519, and BLAKE2s to safeguard data in transit. These algorithms provide a high level of protection against eavesdropping and unauthorized access.
Configure Firewall Rules
Firewall rules should be configured on both ends of the VPN tunnel to restrict access to the VPN only to authorized users and devices. This helps prevent unauthorized entities from gaining access to the network.
Enable Two-Factor Authentication
To enhance security further, two-factor authentication (2FA) can be enabled. 2FA requires users to provide an additional form of authentication, such as a one-time password or a hardware token, in addition to their password. This makes it more difficult for unauthorized individuals to gain access to the VPN, even if they have obtained the user’s password.
Case Studies and Examples
WireGuard’s simplicity and performance make it an ideal solution for various site-to-site VPN deployments. Here are some real-world examples:
-
- -*Remote Branch Office Connectivity
pfSense WireGuard can securely connect remote branch offices to the main office, enabling seamless access to resources and applications.
- -*Remote Branch Office Connectivity
-*Cloud Connectivity
Businesses can establish secure site-to-site VPNs between their on-premises infrastructure and cloud environments, such as AWS or Azure.
-*Disaster Recovery
WireGuard can facilitate secure data replication between primary and disaster recovery sites, ensuring business continuity in the event of an outage.
Benefits of WireGuard in Different Scenarios
WireGuard offers several advantages in different scenarios:
-
- -*High Performance
WireGuard’s efficient and modern design results in significantly faster speeds compared to traditional VPN protocols.
- -*High Performance
-*Ease of Configuration
WireGuard’s simple configuration process simplifies setup and management, reducing administrative overhead.
-*Improved Security
WireGuard utilizes modern cryptography and secure key exchange mechanisms, providing robust protection against cyber threats.
-*Reduced Overhead
WireGuard’s low overhead makes it suitable for resource-constrained environments, such as embedded devices or low-bandwidth connections.
Comparison with Other VPN Solutions
pfSense WireGuard stands out among site-to-site VPN solutions due to its exceptional performance, ease of use, and security features.
However, it’s essential to compare it with other options to understand its advantages and disadvantages.
Other popular site-to-site VPN solutions include OpenVPN, IPsec, and L2TP/IPsec. Let’s delve into the key differences between these solutions and pfSense WireGuard:
Performance
- pfSense WireGuard excels in performance, offering significantly faster speeds than other VPN solutions. This advantage is particularly noticeable in high-bandwidth applications, making it ideal for real-time communication and data transfer.
- OpenVPN, while slower than WireGuard, still provides reasonable performance for most use cases. IPsec and L2TP/IPsec tend to be slower and more resource-intensive, which may impact performance in certain scenarios.
Ease of Use
- pfSense WireGuard is renowned for its user-friendly interface and simplified configuration process. Even users with limited technical knowledge can quickly set up and manage a WireGuard VPN.
- OpenVPN is also relatively easy to configure, but it may require more advanced technical skills compared to WireGuard. IPsec and L2TP/IPsec have more complex configurations, which may be challenging for non-technical users.
Security
- pfSense WireGuard employs state-of-the-art encryption algorithms and protocols to ensure robust security. It supports modern ciphers and key exchange mechanisms, providing protection against eavesdropping and man-in-the-middle attacks.
- OpenVPN and IPsec are also secure VPN solutions, offering various encryption options and security protocols. L2TP/IPsec, however, may be less secure due to its reliance on older protocols.
Cost
- pfSense WireGuard is open source and free to use, making it a cost-effective solution for organizations of all sizes.
- OpenVPN and IPsec are also open source and free, while L2TP/IPsec may require additional licensing fees depending on the implementation.
Conclusion
pfSense WireGuard stands out as a superior site-to-site VPN solution due to its exceptional performance, ease of use, robust security, and cost-effectiveness. While other solutions may offer certain advantages in specific scenarios, pfSense WireGuard remains the top choice for organizations seeking a comprehensive and reliable VPN solution.
Best Practices for pfSense WireGuard Site-to-Site VPN
Establishing best practices for pfSense WireGuard Site-to-Site VPN is crucial to ensure secure, efficient, and reliable VPN configurations. By adhering to these guidelines, network administrators can optimize the performance and security of their VPN deployments.
To maintain the integrity and effectiveness of pfSense WireGuard Site-to-Site VPN connections, ongoing management and monitoring are essential. This includes regular updates, proactive troubleshooting, and performance optimizations.
Key Management and Security
- Use strong and unique keys for both the preshared key and private keys.
- Rotate keys regularly to prevent unauthorized access.
- Configure firewall rules to restrict access to the VPN server only from authorized IP addresses.
Monitoring and Troubleshooting
Regularly monitor VPN connections for performance issues and potential security breaches.
- Use pfSense’s built-in monitoring tools to track connection status, bandwidth usage, and error logs.
- Implement proactive monitoring systems to receive alerts for any anomalies or suspicious activity.
- Maintain detailed documentation of VPN configurations and troubleshooting steps for quick resolution of issues.
Performance Optimization
Optimize VPN performance to ensure smooth and reliable data transfer.
- Use hardware-accelerated encryption (e.g., AES-NI) if available.
- Tune MTU settings to match the underlying network infrastructure.
- Consider using a VPN load balancer to distribute traffic across multiple VPN servers.
Conclusion
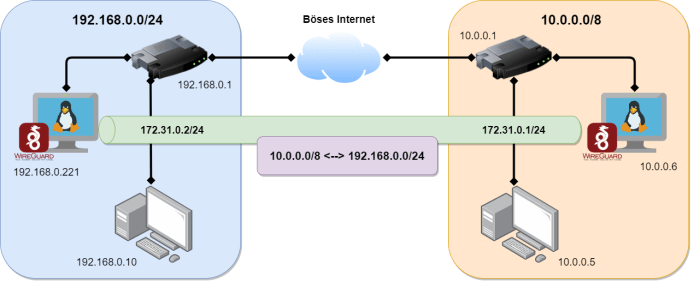
pfSense WireGuard offers a robust and versatile solution for site-to-site VPNs. It combines high performance, strong security, and ease of management.
For further assistance and resources, you can consult the following:
- pfSense WireGuard documentation: https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/index.html
- pfSense community forum: https://forum.netgate.com/
- WireGuard website: https://www.wireguard.com/
Last Point
In conclusion, pfSense WireGuard site-to-site VPNs offer a compelling solution for organizations seeking to connect their networks securely and efficiently. Its ease of configuration, advanced features, and robust security capabilities make it an ideal choice for businesses of all sizes.
By leveraging the power of pfSense and WireGuard, network administrators can establish reliable and secure connections that facilitate seamless communication and collaboration across remote locations.