In the realm of secure data transmission, payload SSH websocket has emerged as a game-changer. This innovative technology seamlessly combines the versatility of websockets with the robust security of SSH, offering a plethora of benefits for modern communication. In this comprehensive exploration, we will delve into the intricacies of payload SSH websocket, uncovering its technical nuances, security considerations, performance optimization techniques, and industry applications.
Payload SSH websocket has revolutionized the way data is transmitted over the internet. Its ability to establish secure, bidirectional communication channels has opened up new possibilities for real-time data exchange, remote access, and secure file transfer. By leveraging the power of websockets, payload SSH websocket enables full-duplex communication, allowing data to flow simultaneously in both directions.
Overview of Payload SSH Websocket
Payload SSH Websocket combines the versatility of websockets with the secure communication capabilities of SSH. It establishes an encrypted tunnel between a client and a server, enabling the transmission of arbitrary data, including SSH commands and responses, over a websocket connection.
This allows for remote command execution, file transfer, and interactive terminal sessions through a web browser or compatible client.
Benefits of Payload SSH Websocket
The primary advantage of payload SSH websocket lies in its ability to bypass restrictive network configurations, such as firewalls or proxy servers, that may block traditional SSH connections. Additionally, it facilitates seamless integration with web-based applications and enables remote access to SSH-enabled devices from a wider range of platforms, including mobile devices and thin clients.
Drawbacks of Payload SSH Websocket
While payload SSH websocket offers significant benefits, it also comes with certain drawbacks. The primary concern is its reliance on websockets, which may not be supported by all browsers or networks. Furthermore, the use of websockets introduces additional complexity and potential security risks associated with this technology.
Real-World Examples of Payload SSH Websocket Applications
Payload SSH websocket finds practical applications in various scenarios, including:
- Remote administration and management of servers and network devices from a web browser.
- Secure file transfer between devices over the internet.
- Web-based SSH terminals for accessing remote systems and executing commands.
- Integration with web applications to provide secure remote access functionality.
Technical Implementation
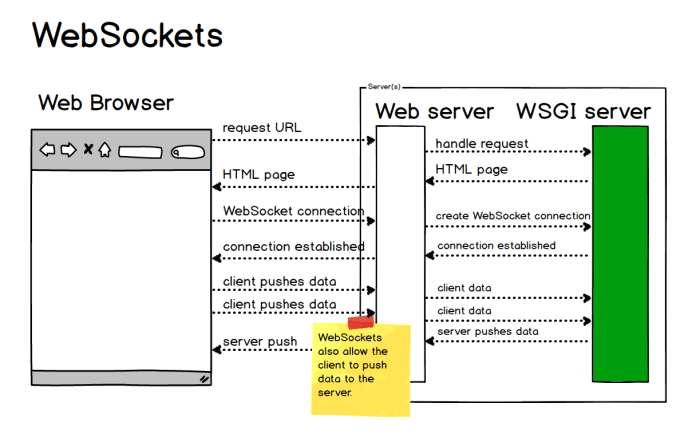
Payload SSH Websocket establishes a secure and encrypted connection between a client and a server, allowing for the secure transmission of data over a WebSocket protocol. The technical architecture of Payload SSH Websocket consists of several key components:
- Client: The client initiates the connection to the server and sends requests for data or commands.
- Server: The server receives requests from the client, processes them, and sends responses back to the client.
- WebSocket Protocol: The WebSocket protocol is used for establishing and maintaining the connection between the client and the server. It provides a full-duplex communication channel over a single TCP connection.
- SSH Encryption: SSH encryption is used to secure the data transmitted between the client and the server. It ensures that the data remains confidential and protected from unauthorized access.
The process of establishing a Payload SSH Websocket connection involves several steps:
- Client Initiation: The client initiates the connection by sending a WebSocket request to the server.
- Server Response: The server accepts the request and sends a response, establishing the WebSocket connection.
- SSH Negotiation: The client and the server negotiate the SSH parameters, such as the encryption algorithms and key exchange methods, to establish a secure channel.
- Data Transmission: Once the SSH connection is established, the client and the server can exchange data securely using the WebSocket protocol.
- Connection Termination: Either the client or the server can terminate the connection by sending a WebSocket close frame.
Payload SSH Websocket uses various mechanisms for data transmission and reception:
- WebSocket Frames: Data is transmitted and received in the form of WebSocket frames. Each frame consists of a header and a payload.
- Binary Data: Data is transmitted in binary format, allowing for efficient and reliable transmission.
- Encryption: All data transmitted over the WebSocket connection is encrypted using SSH encryption algorithms, ensuring the confidentiality and integrity of the data.
Security Considerations
Payload SSH websocket communication introduces potential security vulnerabilities that require careful attention and mitigation strategies. These vulnerabilities stem from the inherent characteristics of websockets and SSH protocols.
Identifying Potential Vulnerabilities
Websockets, by design, operate over a single TCP connection, making them susceptible to various attacks, including:
- Cross-Site WebSocket Hijacking (XSSW): Attackers can exploit vulnerabilities in web applications to inject malicious JavaScript code, enabling them to hijack websocket connections and gain unauthorized access to sensitive data.
- Man-in-the-Middle (MITM) Attacks: Adversaries can intercept and modify websocket traffic, impersonating legitimate parties and potentially stealing sensitive information or injecting malicious code.
- Replay Attacks: Attackers can capture and replay websocket messages, potentially leading to unauthorized access or manipulation of data.
SSH, being a powerful remote access protocol, also presents security risks:
- Brute-Force Attacks: Attackers can attempt to guess SSH credentials through repeated login attempts, potentially gaining unauthorized access to systems.
- Phishing Attacks: Malicious actors can create fake websites or emails designed to trick users into revealing their SSH credentials, leading to account compromise.
- SSH Key Compromise: If an attacker gains access to an SSH private key, they can impersonate the legitimate user and access protected systems.
Mitigating Vulnerabilities
To mitigate these vulnerabilities and ensure secure payload SSH websocket communication, several strategies can be employed:
- Use Strong Authentication: Implement robust authentication mechanisms, such as two-factor authentication (2FA), to protect against unauthorized access and brute-force attacks.
- Encrypt Data: Employ encryption techniques to protect data transmitted over the websocket connection, ensuring confidentiality and integrity.
- Implement Access Control: Establish granular access control policies to restrict access to sensitive data and resources based on user roles and permissions.
- Monitor and Audit: Continuously monitor websocket traffic and SSH logs for suspicious activities, enabling timely detection and response to security incidents.
Best Practices for Secure Connections
To further enhance the security of payload SSH websocket connections, consider the following best practices:
- Use Secure Websocket Libraries: Opt for well-maintained and secure websocket libraries that adhere to industry standards and best practices.
- Configure Firewalls: Implement firewall rules to restrict access to websocket ports and SSH servers, limiting exposure to unauthorized entities.
- Educate Users: Provide security awareness training to users, emphasizing the importance of strong passwords, avoiding phishing scams, and reporting suspicious activities.
By implementing these security measures and best practices, organizations can significantly reduce the risk of attacks and ensure the secure transmission of data over payload SSH websocket connections.
Performance Optimization
The performance of a payload SSH websocket connection can be affected by several factors, including the network latency, the size of the payload, the frequency of messages, and the efficiency of the websocket implementation. To optimize the performance of a payload SSH websocket connection, it is important to consider the following techniques:
Payload Size
The size of the payload is a significant factor that can affect the performance of a payload SSH websocket connection. Larger payloads require more time to transmit and process, which can lead to increased latency and reduced throughput. To optimize performance, it is important to keep the payload size as small as possible.
This can be achieved by compressing the payload or by breaking it into smaller chunks before sending it over the websocket connection.
Message Frequency
The frequency of messages sent over a payload SSH websocket connection can also affect performance. Sending too many messages in a short period of time can overwhelm the network and lead to congestion. To optimize performance, it is important to limit the frequency of messages sent over the websocket connection.
This can be achieved by batching messages together or by using a rate-limiting algorithm.
Websocket Implementation
The efficiency of the websocket implementation can also have a significant impact on the performance of a payload SSH websocket connection. Some websocket implementations are more efficient than others, and choosing the right implementation can help to improve performance. When selecting a websocket implementation, it is important to consider factors such as the performance, scalability, and security of the implementation.
Selecting the Appropriate Implementation
When selecting a payload SSH websocket implementation, it is important to consider the specific performance requirements of the application. For applications that require high throughput and low latency, it is important to choose an implementation that is optimized for performance.
For applications that require high security, it is important to choose an implementation that includes strong security features.
Troubleshooting and Debugging
Encountering issues or errors when utilizing Payload SSH Websocket? This section aims to equip you with the necessary knowledge and resources to effectively troubleshoot and debug these challenges, ensuring seamless and efficient operation.
Common Issues and Errors
Before delving into the debugging process, let’s first identify some common issues and errors that you might encounter when using Payload SSH Websocket:
- Connection Refused: This error typically indicates that the Payload SSH Websocket server is not running or is not listening on the specified port.
- Authentication Failure: If you encounter this error, it suggests that the provided credentials (username and password) are incorrect or do not have the necessary permissions to establish a connection.
- Command Execution Errors: These errors can arise due to various reasons, such as invalid commands, insufficient permissions, or syntax errors.
- Data Transmission Issues: Problems with data transmission can occur due to network connectivity issues, firewall restrictions, or incorrect data encoding.
- Unexpected Disconnections: Sudden disconnections may result from unstable network connections, server-side issues, or client-side errors.
Troubleshooting and Debugging Steps
To effectively troubleshoot and debug Payload SSH Websocket connections, follow these step-by-step instructions:
- Verify Server Status: Ensure that the Payload SSH Websocket server is running and listening on the correct port. Check the server logs for any error messages or indications of connectivity issues.
- Review Credentials: Double-check the username and password used for authentication. Make sure that the user account has the appropriate permissions to establish a Payload SSH Websocket connection.
- Examine Commands: If you encounter command execution errors, carefully review the commands you are sending to the server. Ensure that they are syntactically correct and that the user account has the necessary permissions to execute them.
- Inspect Data Encoding: Verify that the data you are transmitting and receiving is properly encoded. Common encoding formats include Base64, Hexadecimal, and Binary.
- Analyze Network Connectivity: Check the network connection between the client and the server. Ensure that there are no firewalls or other network devices blocking the communication.
- Utilize Debugging Tools: Various tools can assist in debugging Payload SSH Websocket connections. For instance, you can use packet sniffers to monitor network traffic and identify potential issues.
Resources and Tools
In addition to the aforementioned steps, here are some valuable resources and tools that can aid in diagnosing and resolving Payload SSH Websocket problems:
- Payload SSH Websocket Documentation: Refer to the official documentation for detailed information on using and troubleshooting Payload SSH Websocket.
- Online Forums and Communities: Engage with Payload SSH Websocket users and experts in online forums and communities to seek assistance and share experiences.
- Network Analysis Tools: Utilize network analysis tools such as Wireshark or tcpdump to monitor and analyze network traffic.
- Payload SSH Websocket Debuggers: Specialized debuggers specifically designed for Payload SSH Websocket can provide detailed insights into the connection and data transmission process.
Comparison with Alternatives
Payload SSH websocket stands out among other similar technologies, offering unique advantages and use cases. To gain a comprehensive understanding, let’s compare it with SSH tunneling and reverse SSH tunneling, highlighting their strengths and weaknesses.
SSH Tunneling
SSH tunneling establishes a secure channel over an insecure network, allowing data transmission between two hosts. Its key advantages include:
- Security: Encrypts data, protecting it from eavesdropping and manipulation.
- Port Forwarding: Forwards traffic from a local port to a remote server, enabling access to restricted resources.
- Authentication: Utilizes SSH authentication mechanisms, ensuring secure access control.
However, SSH tunneling also has some limitations:
- Limited Connectivity: Relies on a single SSH connection, potentially restricting simultaneous connections.
- Configuration Complexity: Setting up SSH tunneling can be complex, requiring technical expertise.
Reverse SSH Tunneling
Reverse SSH tunneling operates in the opposite direction of SSH tunneling. It allows a remote host to initiate a connection to a local host, typically used for accessing local resources from a remote location. Its advantages include:
- Remote Access: Enables secure access to local resources from remote locations, bypassing firewalls and network restrictions.
- Port Forwarding: Similar to SSH tunneling, it allows forwarding traffic from a remote port to a local server.
However, reverse SSH tunneling also has some drawbacks:
- Security Considerations: Requires careful configuration to prevent unauthorized access to the local network.
- Limited Use Cases: Primarily suited for specific scenarios where remote access to local resources is necessary.
Selecting the Most Suitable Technology
The choice among payload SSH websocket, SSH tunneling, and reverse SSH tunneling depends on specific use cases and requirements:
- Payload SSH Websocket: Ideal for scenarios requiring real-time, bidirectional data transfer over websockets, especially for applications involving frequent updates or streaming data.
- SSH Tunneling: Suitable for establishing secure connections between two hosts, enabling secure data transmission and port forwarding.
- Reverse SSH Tunneling: Best suited for situations where remote access to local resources is necessary, such as accessing local files or applications from a remote location.
By understanding the strengths and weaknesses of each technology, system administrators and developers can make informed decisions, selecting the most appropriate solution for their specific requirements.
Advanced Techniques
Payload SSH websocket offers advanced techniques to enhance its functionality and performance. These techniques include multiplexing, compression, and encryption.
Multiplexing
Multiplexing allows multiple SSH connections to be established over a single websocket connection. This improves efficiency by reducing the number of connections and optimizing bandwidth utilization.
- Benefits:
- Increased efficiency
- Reduced latency
- Improved bandwidth utilization
- Drawbacks:
- Increased complexity
- Potential security risks
- Implementation:
- Use a websocket library that supports multiplexing, such as Autobahn or SockJS.
- Configure the SSH server to allow multiplexing.
Compression
Compression reduces the size of data transmitted over the websocket connection. This can improve performance, especially for large data transfers.
- Benefits:
- Reduced bandwidth usage
- Improved performance
- Drawbacks:
- Increased CPU usage
- Potential security risks
- Implementation:
- Use a websocket library that supports compression, such as zlib or WebSocket++.
- Configure the SSH server to allow compression.
Encryption
Encryption protects data transmitted over the websocket connection from eavesdropping. This is essential for securing sensitive data, such as passwords or financial information.
- Benefits:
- Improved security
- Protection against eavesdropping
- Drawbacks:
- Increased CPU usage
- Potential performance impact
- Implementation:
- Use a websocket library that supports encryption, such as Secure WebSockets or WebSocket++.
- Configure the SSH server to allow encryption.
Industry Use Cases
Payload SSH websocket finds applications in diverse industries, offering secure and efficient data transmission over SSH channels. These industries include IT, finance, and healthcare, among others.
In the IT industry, payload SSH websocket enables secure remote access to servers, network devices, and virtual machines. This allows system administrators and IT professionals to perform maintenance, troubleshooting, and configuration tasks remotely, enhancing efficiency and reducing downtime.
Finance
In the finance industry, payload SSH websocket facilitates secure communication between financial institutions, enabling secure data exchange and transaction processing. This technology enhances the security of financial transactions and helps prevent unauthorized access to sensitive financial data.
Healthcare
In the healthcare industry, payload SSH websocket enables secure communication between healthcare providers, patients, and medical devices. This technology facilitates the secure transmission of patient data, medical images, and other sensitive information, ensuring patient privacy and data security.
Future Applications
Payload SSH websocket is poised to find applications in various emerging technologies, including:
- Internet of Things (IoT): Payload SSH websocket can secure communication between IoT devices and cloud platforms, enabling secure data transmission and remote management.
- Edge Computing: Payload SSH websocket can facilitate secure communication between edge devices and central servers, enabling efficient data transmission and processing at the edge.
- Blockchain: Payload SSH websocket can secure communication between blockchain nodes, enabling secure and transparent transactions.
Future Developments
The realm of payload SSH websocket technology is continuously evolving, driven by advancements in networking protocols, security mechanisms, and emerging use cases. These developments hold the potential to revolutionize the way payload SSH websocket is utilized, expanding its applications and enhancing its capabilities.
One significant trend is the integration of artificial intelligence (AI) and machine learning (ML) algorithms into payload SSH websocket solutions. These technologies can automate tasks such as threat detection, anomaly identification, and real-time traffic analysis, enabling more efficient and proactive security monitoring.
Enhanced Security Protocols
The future of payload SSH websocket is likely to witness the adoption of more robust and sophisticated security protocols. These advancements may include the implementation of quantum-safe cryptography algorithms, which are designed to protect against attacks that exploit the vulnerabilities of classical cryptographic methods.
Additionally, there may be increased emphasis on zero-trust architectures, where every access request is evaluated independently, regardless of the user’s or device’s previous authentication status.
Integration with Emerging Technologies
Payload SSH websocket technology is poised to converge with other emerging technologies, such as blockchain and distributed ledger technology (DLT). This integration can facilitate secure data sharing, transparent audit trails, and decentralized authentication mechanisms. Moreover, the combination of payload SSH websocket with Internet of Things (IoT) devices can enable remote monitoring and management of IoT devices in a secure and efficient manner.
Improved Performance and Scalability
Ongoing developments in payload SSH websocket technology are focused on enhancing performance and scalability. These advancements may include the utilization of faster networking protocols, optimized routing algorithms, and load balancing techniques. Additionally, the adoption of cloud-based and distributed architectures can help distribute the load and improve the overall scalability of payload SSH websocket solutions.
Conclusion
In conclusion, payload SSH websocket has emerged as a transformative technology that redefines the way we communicate and exchange data in modern networks. Its unique ability to establish secure, bidirectional communication channels over websockets has revolutionized the field of secure data transmission.
The key strength of payload SSH websocket lies in its ability to seamlessly integrate with existing web applications and infrastructure, making it accessible to a wide range of users. Its support for various protocols and its compatibility with diverse platforms further enhance its versatility and adaptability.
Future Outlook
As we look towards the future, payload SSH websocket technology is poised for continued growth and innovation. The increasing adoption of cloud computing, the Internet of Things (IoT), and edge computing is driving the demand for secure and reliable data transmission methods, making payload SSH websocket an ideal solution for these emerging technologies.
Moreover, the ongoing advancements in encryption algorithms and security protocols promise to further enhance the security and privacy of payload SSH websocket communication. This will make it even more attractive for applications that handle sensitive data or require stringent security measures.
Closure
In conclusion, payload SSH websocket stands as a testament to the ingenuity of modern communication technology. Its unique blend of security, efficiency, and versatility has made it an indispensable tool for businesses and individuals alike. As we continue to witness advancements in this field, the future of payload SSH websocket appears incredibly promising, with potential applications in areas such as the Internet of Things (IoT), cloud computing, and blockchain technology.