ssh.sshslowdns.com – In the realm of cybersecurity, OPNsense stands as a formidable open-source firewall and routing platform. Among its many capabilities, WireGuard split tunneling has emerged as a game-changer, offering unparalleled control over network traffic and enhanced security. This comprehensive guide will delve into the intricacies of OPNsense WireGuard split tunneling, empowering you with the knowledge to harness its full potential.
WireGuard split tunneling empowers you to selectively route specific traffic through a VPN while allowing other traffic to bypass the VPN connection. This granular control provides a unique blend of security and flexibility, enabling you to safeguard sensitive data while maintaining seamless access to local resources and the broader internet.
Overview of OpenSense WireGuard Split Tunnel
WireGuard is a modern VPN protocol that provides fast, secure, and easy-to-use VPN connections. OpenSense is a popular open-source firewall and router distribution that can be used to implement WireGuard split tunneling.
Split tunneling is a VPN configuration that allows you to route only certain traffic through the VPN tunnel, while other traffic is sent directly over the local network connection. This can be useful for improving performance and reducing latency for applications that do not require VPN protection, such as local network file sharing or printing.
Advantages of Using OpenSense for WireGuard Split Tunneling
- OpenSense is a powerful and flexible firewall and router distribution that provides a wide range of features and options.
- OpenSense is open source and free to use, making it a cost-effective solution for implementing WireGuard split tunneling.
- OpenSense has a large and active community of users and developers, which provides support and resources for troubleshooting and configuration.
Configuration and Setup

To set up WireGuard split tunneling on OpenSense, follow these steps:
In the OpenSense web interface, navigate to VPN > WireGuard > Tunnels.
Click on the “Add” button to create a new WireGuard tunnel.
Interface
- Select the interface to which the WireGuard tunnel will be bound. This is typically the WAN interface.
- Enter a name for the tunnel.
- Select the “Split Tunnel” checkbox to enable split tunneling.
Peer
- Enter the public IP address of the WireGuard server.
- Enter the port number of the WireGuard server.
- Generate a new private key for the tunnel.
- Enter the public key of the WireGuard server.
Allowed IPs
- Enter the allowed IP addresses for the split tunnel. This can be a single IP address, a range of IP addresses, or a subnet.
Advanced Settings
- Configure additional settings such as MTU, keepalive, and DNS settings.
Click on the “Save” button to create the WireGuard tunnel.
Advanced Configuration
OpenSense WireGuard split tunneling offers advanced configuration options to tailor the functionality to your specific needs. These options include rule-based routing and traffic shaping, allowing for granular control over network traffic.
Rule-based routing enables you to specify which traffic should be routed through the WireGuard tunnel and which should remain on the local network. This is achieved by creating rules that define the source, destination, and protocol of the traffic. Traffic shaping, on the other hand, allows you to control the bandwidth and latency of the WireGuard tunnel, ensuring optimal performance for critical applications.
Troubleshooting Common Issues
Troubleshooting common issues related to advanced configuration requires a systematic approach. Start by verifying the configuration settings, including the rules and traffic shaping parameters. Ensure that the rules are properly defined and that the traffic shaping limits are reasonable. Additionally, check the WireGuard logs for any error messages or warnings that may indicate a problem.
Security Considerations
WireGuard split tunneling introduces potential security risks that need to be carefully addressed. Understanding these risks and implementing appropriate mitigation measures is crucial for maintaining a secure network environment.One of the main concerns is the exposure of internal network traffic to the public internet when using split tunneling.
This can create a pathway for unauthorized access to sensitive data or systems within the internal network. To mitigate this risk, it is essential to implement strong firewall rules on the WireGuard interface to restrict access to only authorized devices and services.Another
potential security risk is the possibility of DNS leaks. When using split tunneling, DNS queries for internal domains may be inadvertently sent through the public internet instead of the VPN tunnel. This can reveal the internal network structure and potentially expose sensitive information.
To prevent DNS leaks, it is recommended to configure the WireGuard client to use a DNS server within the internal network or to implement a DNS leak prevention mechanism on the firewall.Finally, it is important to consider the security of the WireGuard server itself.
The server should be properly configured with strong encryption and authentication mechanisms to prevent unauthorized access and ensure the confidentiality and integrity of the VPN traffic.
Performance Optimization
Enhancing the performance of WireGuard split tunneling on OpenSense involves fine-tuning various settings and parameters. By optimizing these configurations, you can maximize the efficiency and speed of your network connection.
One crucial aspect is selecting the appropriate cipher algorithm. WireGuard offers several options, including ChaCha20, AES-256-GCM, and BLAKE2s. ChaCha20 generally provides the best performance, while AES-256-GCM offers a higher level of security. Choose the cipher that best suits your specific requirements.
MTU Settings
Optimizing the Maximum Transmission Unit (MTU) can significantly improve performance. MTU defines the maximum size of data packets that can be transmitted over the network. A larger MTU allows for fewer fragmented packets, resulting in faster data transfer. However, an excessively large MTU can lead to packet fragmentation, reducing performance.
Determine the optimal MTU size by experimenting with different values or using an MTU discovery tool.
Buffer Bloating Mitigation
Buffer bloating occurs when the network buffer becomes overwhelmed, leading to latency and performance degradation. To mitigate this, adjust the buffer size and flow control settings. Increasing the buffer size can accommodate more packets, while enabling flow control prevents excessive buffering.
Fine-tune these parameters to strike a balance between latency and throughput.
Use Cases and Applications
OpenSense WireGuard split tunneling offers a range of practical applications in various scenarios. Understanding these use cases can help you leverage its capabilities effectively.
One key benefit of split tunneling is the ability to selectively route specific traffic through the VPN tunnel while allowing other traffic to access the internet directly. This feature enables greater flexibility and control over your network connections.
Enhanced Privacy and Security
- Split tunneling allows you to protect sensitive traffic, such as financial transactions or business communications, by routing it through the VPN tunnel, while maintaining access to local network resources and services.
- By separating sensitive traffic from regular internet traffic, you can minimize the risk of data breaches and unauthorized access to your private information.
Improved Performance and Efficiency
- Split tunneling can enhance internet performance by directing traffic that does not require VPN protection directly to the internet. This reduces the load on the VPN server and improves overall network responsiveness.
- By selectively routing traffic through the VPN, you can optimize bandwidth usage and avoid unnecessary overhead, resulting in faster internet speeds and improved user experience.
Compliance and Regulatory Adherence
- Split tunneling can help organizations comply with data protection regulations and industry standards by allowing them to selectively route traffic subject to compliance requirements through the VPN tunnel.
- This ensures that sensitive data is protected and complies with regulations, while allowing access to other resources without violating compliance requirements.
Advantages and Disadvantages
While split tunneling offers several advantages, it also has some potential drawbacks to consider:
- Advantages: Enhanced privacy and security, improved performance, compliance adherence.
- Disadvantages: Potential for configuration complexity, increased administrative overhead, possible performance impact on VPN tunnel.
Comparison with Other Solutions
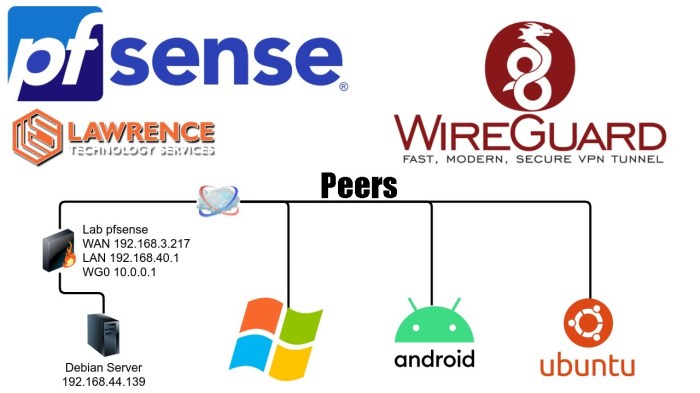
OpenSense WireGuard split tunneling stands out among other split tunneling solutions due to its exceptional features and advantages.
Unlike many solutions that rely on complex configurations, OpenSense WireGuard split tunneling offers a user-friendly interface and straightforward setup. It integrates seamlessly with the OpenSense firewall, providing a comprehensive and centralized security solution.
Unique Features
-
- Seamless Integration: Integrates seamlessly with OpenSense firewall, providing a centralized security solution.
- Easy Configuration: User-friendly interface and straightforward setup, making it accessible to users of all technical levels.
- Advanced Security: Supports strong encryption algorithms and modern security protocols, ensuring data privacy and protection.
li> Flexible Routing: Allows granular control over traffic routing, enabling customized split tunneling configurations.
Troubleshooting
OpenSense WireGuard split tunneling is a complex configuration, and issues can arise during setup or operation.
Here’s a troubleshooting guide to help resolve common problems:
Initial Setup
- Ensure the WireGuard interface is created and enabled.
- Check that the correct IP addresses and ports are configured for both the server and client.
- Verify that the firewall rules allow traffic to and from the WireGuard interface.
Connectivity Issues
- Check if the client can ping the server’s IP address.
- Ensure the client has a valid IP address assigned by the WireGuard server.
- Verify that the client’s firewall is not blocking traffic to the WireGuard interface.
Split Tunneling
- Ensure the split tunneling rules are correctly configured in OpenSense.
- Check that the client’s routing table is configured to send traffic through the WireGuard interface as desired.
- Verify that the client’s DNS settings are configured to use the DNS server specified in the WireGuard configuration.
Performance Issues
- Check the CPU and memory usage of the OpenSense firewall.
- Monitor the network traffic on the WireGuard interface to identify any bottlenecks.
- Consider using a faster encryption algorithm or increasing the MTU size.
Other Issues
- Check the OpenSense logs for any error messages related to WireGuard.
- Consult the WireGuard documentation for additional troubleshooting tips.
FAQs and Best Practices
This section addresses frequently asked questions and provides best practices for implementing and managing OpenSense WireGuard split tunneling effectively.
Best Practices
To ensure optimal performance and security, follow these best practices when setting up and managing WireGuard split tunneling:
- Choose the right devices: Use devices that support WireGuard natively or have a compatible kernel module.
- Configure the firewall rules: Allow traffic from the WireGuard interface to the internal network and block traffic from the internal network to the WireGuard interface.
- Use strong encryption: Select a strong encryption algorithm (e.g., AES-256-GCM) to protect data in transit.
- Monitor and maintain: Regularly monitor the WireGuard tunnel’s status and perform updates as needed to ensure its continued functionality and security.
FAQs
Here are some common questions and answers related to OpenSense WireGuard split tunneling:
- What is the difference between full and split tunneling?
- Full tunneling routes all traffic through the VPN, while split tunneling only routes specific traffic through the VPN.
- Why should I use split tunneling?
- Split tunneling allows you to access local resources (e.g., printers, network shares) while still protecting your internet traffic.
- How do I configure split tunneling in OpenSense?
- See the “Configuration and Setup” section for detailed instructions on configuring split tunneling in OpenSense.
Future Developments and Outlook
OpenSense WireGuard split tunneling is a rapidly evolving technology, with new developments and improvements emerging regularly. Here are some potential future developments to watch for:
Enhanced Security Features
– Integration with advanced encryption algorithms, such as AES-256-GCM, to provide even stronger protection against eavesdropping and data breaches. – Implementation of multi-factor authentication (MFA) for added security when connecting to the VPN.
– Development of new security protocols and standards to further enhance the security of WireGuard connections.
Improved Performance
– Optimization of the WireGuard protocol to reduce latency and improve overall performance, especially for high-bandwidth applications. – Integration with hardware acceleration technologies to enhance the performance of VPN connections on devices with limited resources.
– Development of new features to improve the efficiency of split tunneling, such as dynamic routing and adaptive bandwidth allocation.
Increased Usability
– Development of user-friendly interfaces and wizards to make it easier for non-technical users to set up and manage WireGuard split tunnels. – Integration with popular operating systems and devices to provide seamless connectivity across different platforms.
– Implementation of features such as auto-reconnect and kill switches to improve the reliability and usability of VPN connections.
Emerging Trends
– Increased adoption of WireGuard split tunneling in enterprise environments due to its security, performance, and flexibility advantages. – Integration with cloud computing platforms to provide secure and scalable VPN solutions for remote workers and distributed teams.
– Development of new use cases for WireGuard split tunneling, such as secure access to IoT devices and remote troubleshooting.