In the realm of secure networking, OPNsense and WireGuard emerge as formidable tools, offering a myriad of benefits. One such feature is split tunneling, a game-changer in the world of virtual private networks (VPNs). This innovative technique allows you to selectively route traffic through a VPN tunnel while maintaining direct access to local resources.
Join us as we delve into the fascinating world of OPNsense WireGuard split tunneling, exploring its advantages, configuration, optimization, and more.
As we embark on this journey, we will uncover the secrets of split tunneling, empowering you with the knowledge to enhance your network security, privacy, and performance. Get ready to witness the transformative power of this cutting-edge technology.
Introduction

OpenSense is a free and open-source firewall and routing platform that provides a wide range of features for network security and management. WireGuard is a modern VPN protocol that offers high performance, security, and ease of use. Split tunneling is a VPN feature that allows you to selectively route specific traffic through the VPN tunnel while allowing other traffic to bypass the tunnel and go directly to the internet.
In this guide, we will show you how to set up split tunneling with OpenSense and WireGuard. We will assume that you have already installed and configured OpenSense and WireGuard on your device.
Configuring Split Tunneling
- Navigate to the “Firewall” menu in OpenSense and select the “Rules” tab.
- Click on the “Add” button to create a new firewall rule.
- In the “Action” field, select “Pass”.
- In the “Interface” field, select the WireGuard interface that you want to use for split tunneling.
- In the “Source” field, select the network that you want to allow to bypass the VPN tunnel.
- In the “Destination” field, select “Any”.
- Click on the “Save” button to save the new firewall rule.
You have now successfully configured split tunneling with OpenSense and WireGuard. Traffic from the specified network will now bypass the VPN tunnel and go directly to the internet, while all other traffic will be routed through the VPN tunnel.
Benefits of Split Tunneling with OpenSense and WireGuard
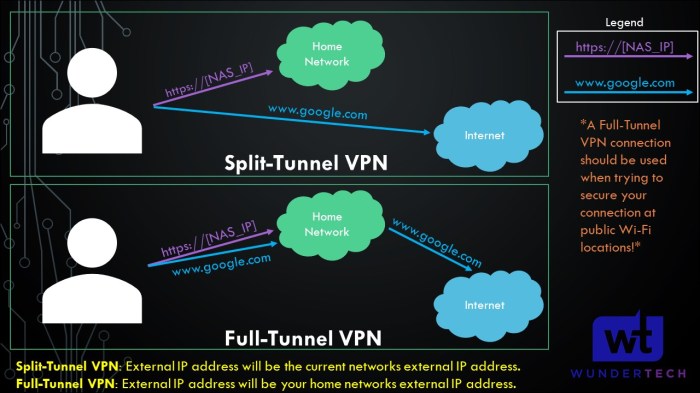
Split tunneling offers significant advantages when used with OpenSense and WireGuard. It enhances performance, security, and privacy, providing a more efficient and secure networking experience.
Improved Performance
Split tunneling reduces the load on the VPN tunnel by directing only specific traffic through the VPN connection. This improves overall network performance, as non-essential traffic is handled by the local internet connection, freeing up bandwidth for VPN-protected traffic.
Enhanced Security
By limiting the traffic that flows through the VPN tunnel, split tunneling reduces the potential attack surface and exposure to threats. Only the traffic that requires VPN protection is encrypted and routed through the VPN, minimizing the risk of data breaches and unauthorized access.
Increased Privacy
Split tunneling allows users to access local resources and services without exposing them to the VPN. This enhances privacy by preventing the VPN provider from monitoring or logging user activity on the local network. It also prevents other users on the VPN network from snooping on local traffic.
Configuring Split Tunneling with OpenSense and WireGuard
This section provides a step-by-step guide on how to configure split tunneling with OpenSense and WireGuard. We will also discuss some important configuration options and troubleshooting tips.
Before you begin, make sure you have a working WireGuard setup on your OpenSense firewall. You can follow the instructions in the previous section to set up WireGuard on OpenSense.
Step-by-Step Guide
- Navigate to the “Firewall” tab in the OpenSense web interface and click on “Rules” in the left-hand menu.
- Click on the “Add” button to create a new firewall rule.
- In the “Action” field, select “Pass”.
- In the “Interface” field, select the WireGuard interface that you want to use for split tunneling.
- In the “Source” field, select the network that you want to exclude from the VPN tunnel.
- In the “Destination” field, select “Any”.
- Click on the “Save” button to create the new firewall rule.
Configuration Options
There are a few important configuration options that you can use to customize your split tunneling setup.
- Allowed IPs: This option allows you to specify a list of IP addresses that will be excluded from the VPN tunnel. This is useful if you want to access certain local resources while connected to the VPN.
- Excluded Networks: This option allows you to specify a list of networks that will be excluded from the VPN tunnel. This is useful if you want to route all traffic from a certain network through the VPN tunnel.
Troubleshooting Tips
If you are having trouble getting split tunneling to work, here are a few troubleshooting tips:
- Make sure that you have created a firewall rule that allows traffic from the excluded network to pass through the WireGuard interface.
- Make sure that the WireGuard interface is up and running.
- Check the WireGuard configuration files to make sure that the AllowedIPs and ExcludedNetworks options are set correctly.
Optimizing Split Tunneling Performance
To ensure optimal performance of your split tunneling configuration, several optimizations can be implemented. These optimizations aim to minimize latency, maximize throughput, and enhance the overall user experience.
Key areas for optimization include identifying and excluding local traffic, configuring optimal MTU settings, and monitoring and adjusting performance metrics.
Identifying and Excluding Local Traffic
Excluding local traffic from being routed through the VPN tunnel can significantly improve performance. Local traffic, such as communication between devices on the same LAN, does not need to traverse the VPN and can be handled more efficiently by the local network.
To exclude local traffic, you can configure your WireGuard interface to use a different subnet than your local network. This ensures that traffic destined for local IP addresses will not be routed through the VPN.
Configuring MTU Settings
The Maximum Transmission Unit (MTU) is a critical setting that affects the performance of your VPN connection. MTU defines the maximum size of a single packet that can be transmitted over the network.
For optimal performance, the MTU should be set to the lowest common denominator of all the network interfaces involved in the VPN connection. This ensures that packets are not fragmented, which can introduce latency and performance issues.
Monitoring and Adjusting Performance
Regularly monitoring the performance of your split tunneling configuration is essential to ensure optimal operation. You can use various tools and metrics to monitor latency, throughput, and packet loss.
If you observe any performance degradation, you can adjust the configuration settings, such as MTU, encryption algorithms, or routing policies, to optimize performance.
Security Considerations for Split Tunneling
Split tunneling introduces additional security considerations that must be carefully addressed to maintain a robust security posture.
Potential risks and vulnerabilities associated with split tunneling include:
- Data leakage: If the split tunnel configuration is not properly configured, sensitive data from the local network may be inadvertently routed through the VPN, exposing it to potential eavesdropping or interception.
- Malware propagation: Malware on the local network may be able to bypass security measures by tunneling through the VPN, potentially infecting remote systems.
- Unauthorized access: If the VPN is compromised, attackers may be able to gain access to the local network through the split tunnel, bypassing perimeter security controls.
Best Practices for Mitigating Risks
To mitigate these risks, it is essential to implement best practices for split tunneling security, including:
- Carefully define split tunnel rules: Clearly define which traffic should be routed through the VPN and which should be excluded. Avoid broad or permissive rules that could inadvertently expose sensitive data.
- Use strong encryption: Employ robust encryption algorithms, such as AES-256, to protect data in transit through the VPN.
- Implement multi-factor authentication (MFA): Require MFA for VPN access to prevent unauthorized access even if credentials are compromised.
- Monitor and log VPN activity: Regularly monitor VPN logs for suspicious activity and investigate any anomalies promptly.
- Educate users: Train users on the importance of split tunneling security and provide guidelines for safe usage.
Monitoring and Logging for Security
Effective security for split tunneling requires robust monitoring and logging capabilities. This includes:
- VPN logs: Monitor VPN logs for suspicious activity, such as failed login attempts, unusual traffic patterns, or unauthorized access.
- Firewall logs: Monitor firewall logs to detect any unauthorized traffic passing through the split tunnel.
- Intrusion detection/prevention system (IDS/IPS): Deploy an IDS/IPS to detect and block malicious traffic that may attempt to exploit split tunneling vulnerabilities.
- Regular security audits: Conduct regular security audits to assess the effectiveness of split tunneling security measures and identify any potential weaknesses.
Advanced Split Tunneling Techniques
Advanced split tunneling techniques extend the capabilities of basic split tunneling by providing more granular control and flexibility.
These techniques allow you to configure multiple split tunnels, use routing tables for precise traffic management, and implement load balancing for optimal performance.
Configuring Multiple Split Tunnels
Configuring multiple split tunnels allows you to create separate tunnels for different sets of traffic.
For example, you could have one tunnel for business traffic and another for personal traffic, ensuring that each type of traffic is routed appropriately.
Using Routing Tables for Granular Control
Routing tables provide a powerful way to control how traffic is routed through your network.
By using routing tables, you can specify which traffic should be sent through the VPN tunnel and which traffic should be sent directly to the internet.
Implementing Load Balancing
Load balancing distributes traffic across multiple VPN tunnels, improving performance and reliability.
By implementing load balancing, you can ensure that traffic is always routed through the most efficient tunnel, reducing latency and improving overall network performance.
Troubleshooting Split Tunneling Issues
Troubleshooting split tunneling issues requires a systematic approach to identify and resolve the underlying cause. Common errors and solutions include:
- Incorrect network configuration: Ensure that the network settings, including IP addresses, subnet masks, and gateway configurations, are correct.
- Firewall rules: Verify that the firewall rules allow traffic to flow as expected through the VPN tunnel and the local network.
- Routing issues: Check the routing table to ensure that traffic is being routed correctly through the VPN tunnel and the local network.
- DNS settings: Ensure that the DNS settings are configured correctly to resolve hostnames to the appropriate IP addresses.
Debugging Techniques
Debugging techniques can help identify the root cause of split tunneling issues:
- Packet captures: Capturing network packets can provide insights into the traffic flow and identify any issues.
- Log analysis: Reviewing logs from the VPN server, firewall, and other relevant components can provide valuable information.
- Testing: Testing the split tunneling configuration with different devices and network scenarios can help identify potential issues.
Advanced Troubleshooting Methods
Advanced troubleshooting methods may be necessary to resolve complex split tunneling issues:
- Kernel debugging: Analyzing the kernel logs can provide detailed information about the VPN tunnel and network operations.
- Network analysis tools: Using tools like Wireshark or tcpdump can provide deep insights into network traffic and identify potential issues.
- Vendor support: Contacting the vendor of the VPN server or firewall for support can provide access to specialized knowledge and troubleshooting resources.
Examples of Split Tunneling Use Cases
Split tunneling offers a versatile approach to network security, providing numerous use cases for both individuals and organizations. Here are a few prominent examples:
Secure Remote Access
Split tunneling allows remote users to securely access internal corporate resources while maintaining access to the public internet. This is particularly beneficial for employees working from home or traveling, as it enables them to access company applications and data without exposing their entire network traffic to potential threats.
Improving Internet Performance
Split tunneling can optimize internet performance by selectively routing traffic through the VPN tunnel. By excluding specific websites or services from the VPN, users can enjoy faster speeds and reduced latency for these applications. This is especially useful for streaming media, online gaming, or accessing geo-restricted content.
Enhancing Privacy and Anonymity
Split tunneling provides an additional layer of privacy and anonymity by encrypting only the traffic that requires protection. This means that users can browse the internet without their ISP or other third parties monitoring their activities. It also helps prevent data leaks and tracking, making it ideal for privacy-conscious individuals.
Comparison with Other Split Tunneling Solutions
OpenSense stands out among other split tunneling solutions due to its open-source nature, flexibility, and cost-effectiveness. Let’s compare it with both open-source alternatives and commercial VPNs.
OpenSense vs. Other Open-Source Solutions
OpenSense is a popular open-source firewall and router distribution that provides advanced networking features, including split tunneling. It offers greater flexibility and customization options compared to other open-source solutions. Pros of OpenSense:
- Wide range of supported platforms and hardware
- Extensive documentation and community support
- Customizable and extendable with plugins and packages
Cons of OpenSense:
- Requires technical expertise for configuration
- Limited support for certain advanced features found in commercial VPNs
OpenSense vs. Commercial VPNs
Commercial VPNs typically offer a more user-friendly experience and a wider range of features compared to OpenSense. However, they come with subscription costs and may have limitations on customization. Pros of Commercial VPNs:
- Easy to set up and use with dedicated apps
- Comprehensive feature set, including advanced encryption and security protocols
- Customer support and regular updates
Cons of Commercial VPNs:
- Subscription costs can add up over time
- Limited customization options
- Potential privacy concerns with third-party providers
Ultimately, the best choice depends on specific requirements and preferences. OpenSense is ideal for users seeking advanced control and flexibility, while commercial VPNs offer a more user-friendly experience and comprehensive feature set.
Conclusion
Split tunneling with OpenSense and WireGuard offers numerous benefits, including improved security, reduced bandwidth consumption, and increased flexibility. It enables organizations to implement secure remote access solutions while maintaining control over network traffic. As remote work and cloud adoption continue to grow, split tunneling is expected to play an increasingly important role in network security and efficiency.
Future Trends and Advancements
The future of split tunneling with OpenSense and WireGuard holds several exciting possibilities. Advancements in encryption and authentication protocols will further enhance the security of split tunneling connections. Integration with other network security tools, such as firewalls and intrusion detection systems, will provide more comprehensive protection.
Additionally, the development of new split tunneling techniques will enable more granular control over network traffic, allowing organizations to optimize performance and security based on specific requirements.
Last Word
Our exploration of OPNsense WireGuard split tunneling concludes with a profound appreciation for its transformative capabilities. This technology has revolutionized the way we manage network traffic, offering a perfect blend of security, privacy, and performance. As we move forward, we eagerly anticipate the future advancements in split tunneling, which promise to further enhance our digital experiences.
Embrace the power of OPNsense WireGuard split tunneling and unlock a world of secure and optimized networking possibilities.