Welcome to the comprehensive guide to Linux Mint SSH Server! In this guide, we will delve into the world of secure remote access and management, empowering you to unlock the full potential of your Linux Mint system. SSH, or Secure Shell, is a powerful tool that allows you to securely connect to your Linux Mint server from anywhere in the world, enabling you to perform a wide range of tasks, from file management to system administration.
Throughout this guide, we will explore the key features and benefits of Linux Mint SSH Server, providing you with step-by-step instructions for installation and configuration. We will also delve into advanced topics such as SSH key management, troubleshooting, and best practices, ensuring that you have a secure and efficient SSH setup.
Whether you are a seasoned system administrator or just starting your journey into remote server management, this guide will provide you with the knowledge and skills you need to master Linux Mint SSH Server.
Overview of Linux Mint SSH Server
Linux Mint SSH Server is a powerful and versatile tool that allows you to securely connect to your Linux Mint system from remote locations. It provides a secure and encrypted connection, enabling you to manage your system, transfer files, and run commands as if you were physically present at the console.
Key features of Linux Mint SSH Server include:
- Strong encryption algorithms for secure data transmission
- Support for public-key authentication for added security
- Ability to create and manage multiple user accounts
- Advanced configuration options for fine-tuning the server’s behavior
- Compatibility with a wide range of SSH clients
Benefits of Using Linux Mint SSH Server
Using Linux Mint SSH Server offers numerous benefits, including:
- Secure remote access to your system from anywhere with an internet connection
- Centralized management of multiple Linux Mint systems from a single location
- Automated tasks and scripts execution on remote systems
- File transfer and synchronization between local and remote systems
- Troubleshooting and debugging of remote systems without the need for physical access
Installation and Configuration
Setting up an SSH server on Linux Mint involves installing the necessary software and configuring it to meet your security and access requirements. This process includes creating users, assigning permissions, and optimizing settings for enhanced security.
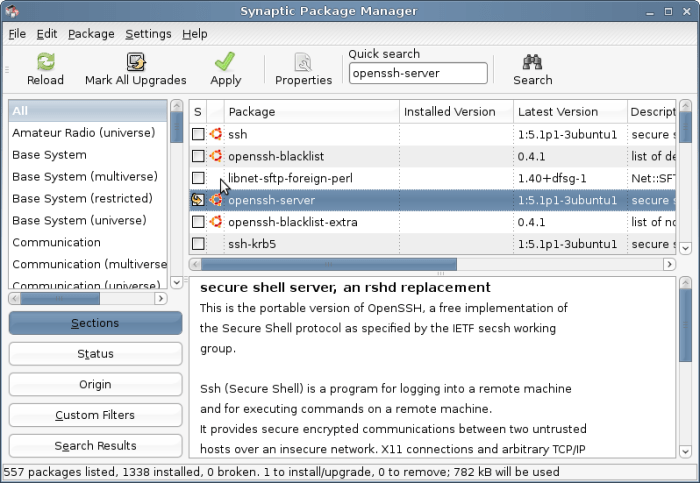
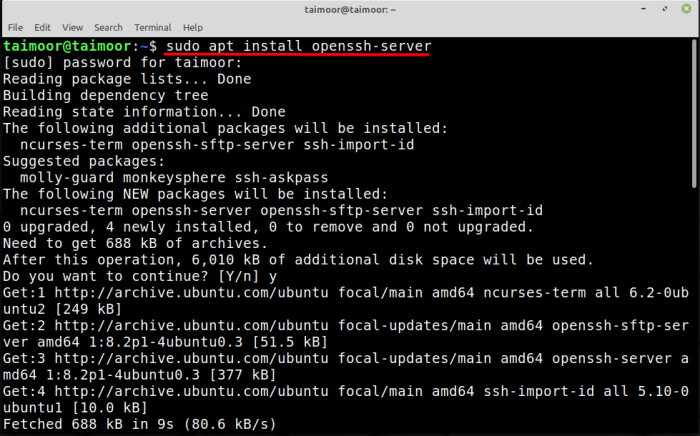
Installing the SSH Server
To install the SSH server on Linux Mint, open a terminal window and execute the following command:
sudo apt-get install openssh-server
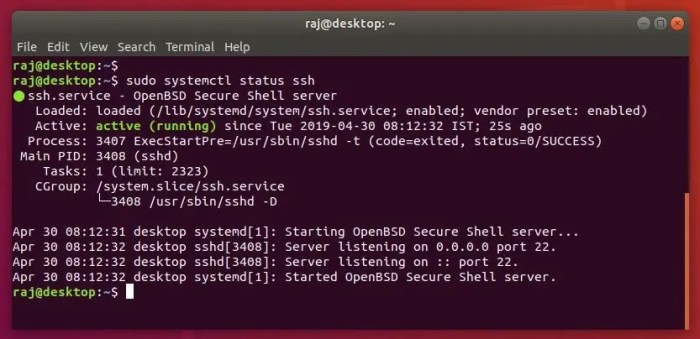
Once the installation is complete, you can start the SSH server using the command:
sudo systemctl start ssh
Configuring the SSH Server
The SSH server configuration file is located at /etc/ssh/sshd_config. To edit this file, use a text editor such as nano or vi:
sudo nano /etc/ssh/sshd_config
Within the configuration file, you can adjust various settings, including:
- Port number: Change the default SSH port (22) for enhanced security.
- User permissions: Specify which users are allowed to access the SSH server.
- Password authentication: Disable password authentication and enforce key-based authentication for improved security.
- Key exchange algorithms: Configure the algorithms used for key exchange to ensure strong encryption.
Security Considerations
SSH offers a secure remote access channel, but maintaining its security is crucial. Understanding potential risks and implementing best practices ensures the server’s integrity.
Best Practices
- Strong Passwords: Enforce complex passwords to prevent unauthorized access.
- Disable Root Login: Restrict direct root login to minimize the impact of potential exploits.
- Two-Factor Authentication: Implement additional security layers by requiring a second authentication factor, such as a security key or code sent to a mobile device.
Common Attacks and Mitigation Strategies
SSH is targeted by various attacks, including:
- Brute Force Attacks: Use strong passwords and implement rate-limiting to prevent automated login attempts.
- Man-in-the-Middle Attacks: Use SSH key authentication to verify server identity and prevent attackers from intercepting communications.
- Denial-of-Service Attacks: Implement fail2ban or other security measures to block repeated failed login attempts and prevent attackers from overwhelming the server.
Remote Access and Management
Remote access and management are crucial aspects of administering Linux Mint servers. SSH provides a secure and versatile means of connecting to a server from remote locations.
To connect to a Linux Mint SSH server, you can use various clients such as PuTTY (Windows), Terminal (macOS), or SSH (Linux). Simply enter the server’s IP address or hostname, followed by the SSH port (default: 22), and provide your username and password.
Once connected, you can manage files, run programs, and troubleshoot issues on the server remotely. For example, you can use commands like “ls” to list files, “cd” to change directories, and “sudo apt update” to update the system.
Advanced Techniques for Remote Administration
SSH offers advanced techniques for remote administration, such as port forwarding and tunneling.
- Port Forwarding: Allows you to redirect traffic from one port on your local machine to a different port on the remote server. This is useful for accessing services running on the server that may not be accessible from the internet.
- Tunneling: Creates a secure encrypted channel between your local machine and the remote server. This is useful for securely accessing applications or services on the server that may not support SSH directly.
SSH Key Management
SSH keys are an essential component of secure SSH authentication. They provide a more secure alternative to passwords by using public-key cryptography.
When using SSH keys, a pair of keys is generated: a public key and a private key. The public key is stored on the server, while the private key is kept secret by the user. When a user attempts to connect to the server, the server compares the user’s public key with the stored public key.
If the keys match, the user is authenticated.
Advantages of Using SSH Keys
- More secure than passwords
- Cannot be brute-forced
- Can be used for automated tasks
Disadvantages of Using SSH Keys
- More complex to set up
- Requires careful management of private keys
- Can be compromised if the private key is stolen
Troubleshooting SSH Issues
SSH connections can occasionally encounter problems. Understanding common issues and troubleshooting techniques is crucial for maintaining secure and reliable SSH access.
Identifying Common Problems
- Connection refused: The SSH server is not running or is not listening on the specified port.
- Authentication failed: Incorrect username, password, or SSH key.
- Permission denied: The user does not have permission to access the remote system.
- Timeout: The SSH connection timed out due to network issues or server overload.
Troubleshooting Steps
- Verify that the SSH server is running and listening on the correct port using the command:
netstat
antp | grep sshd
- Check the SSH configuration file (/etc/ssh/sshd_config) for errors and ensure that the port and IP address are correctly configured.
- Verify that the user has the necessary permissions to access the remote system.Use the command:
ls
ld /home/username
- Check the SSH logs (/var/log/auth.log) for error messages and potential security threats.
Analyzing SSH Logs
SSH logs provide valuable insights into connection attempts, errors, and security events.
To analyze the logs, use the command: grep sshd /var/log/auth.log
Common error messages include:
- Failed password for [username] from [IP address]
- Invalid user [username]
- Permission denied (publickey)
These messages can help identify failed login attempts, unauthorized access, and potential security breaches.
Advanced SSH Configuration
Advanced SSH configuration allows for customization of the SSH server to meet specific needs. It involves setting up SSH tunnels, configuring SFTP, and enabling X11 forwarding.SSH configuration files, typically located in /etc/ssh/sshd_config , provide options for customizing the SSH server.
Each option can be set to a specific value to modify the server’s behavior.
SSH Tunnels
SSH tunnels establish secure connections between two remote hosts through an SSH server. They can be used to forward traffic from one port on the client to a different port on the server, allowing access to otherwise inaccessible resources.
SFTP Configuration
SFTP (SSH File Transfer Protocol) allows secure file transfers over SSH. It can be configured to restrict access to specific directories or users, and to enforce file permissions.
X11 Forwarding
X11 forwarding enables the display of graphical applications running on a remote server on the local client. This allows for remote access to graphical user interfaces (GUIs).
SSH Best Practices
Secure Shell (SSH) is a robust protocol for remote access and management of systems. Implementing best practices enhances SSH security and efficiency. This section explores industry-recommended guidelines for optimizing SSH usage.
By adhering to these best practices, organizations can minimize security risks, improve performance, and ensure the integrity of their SSH infrastructure.
Disable Root Login
Restricting root login via SSH adds an extra layer of security. It prevents attackers from directly accessing the system with elevated privileges. Instead, create a non-privileged user account and grant necessary permissions for administrative tasks.
Use Strong Passwords and SSH Keys
Implement strong password policies and encourage the use of SSH keys for authentication. SSH keys provide a more secure alternative to passwords, as they are cryptographically generated and stored on the client system, eliminating the risk of password interception.
Enable Two-Factor Authentication (2FA)
Consider implementing 2FA for SSH access. This adds an additional layer of security by requiring users to provide a second form of authentication, such as a one-time password or a security token.
Keep Software Updated
Regularly update the SSH server and client software to address security vulnerabilities. Software updates often include patches for known exploits, ensuring that the system remains protected against the latest threats.
Monitor SSH Logs
Enable SSH logging and regularly review the logs for suspicious activity. Monitoring logs helps detect unauthorized access attempts, failed logins, and other potential security incidents.
Restrict Access to SSH Port
Restrict access to the SSH port (default port 22) to trusted IP addresses or subnets. This limits the exposure of the SSH service to unauthorized users and reduces the risk of brute-force attacks.
Use SSH Tunneling for Secure Data Transfer
Leverage SSH tunneling to securely transfer data over untrusted networks. SSH tunneling encrypts the data stream, ensuring confidentiality and integrity during transmission.
Disable Unnecessary Services
Disable any unnecessary services or protocols on the SSH server to minimize the attack surface. This includes disabling services like X11 forwarding, which can be exploited for malicious purposes.
SSH in Virtual Environments
SSH (Secure Shell) plays a crucial role in virtual environments, such as Docker and Vagrant, by providing a secure and efficient way to manage and access virtual machines.
Using SSH in virtual environments offers several benefits. It allows for remote access to the virtual machine, enabling administrators to manage and troubleshoot systems from any location. Additionally, SSH provides a secure channel for transferring files and data between the host and virtual machine.
Docker
In Docker, SSH can be enabled by adding the -p flag to the docker run command. This flag maps a port on the host machine to a port within the container, allowing SSH connections to be established.
docker run -p 22:22
Vagrant
In Vagrant, SSH is configured through the Vagrantfile . The config.ssh block allows administrators to specify the SSH port and other settings for the virtual machine.
Vagrant.configure("2") do |config|
config.vm.network "private_network", ip: "192.168.33.10"
config.vm.provision "shell", inline: <<-SHELL echo "Hello, Vagrant!" > /tmp/vagrant-provisioned
SHELL
end
SSH for System Administration
SSH is a powerful tool that can be used for a variety of system administration tasks, including software installation, configuration management, and remote monitoring.
It provides a secure and efficient way to access and manage remote systems, making it an invaluable tool for system administrators.
There are many benefits to using SSH for system administration. First, it allows administrators to access remote systems from anywhere with an internet connection. This can be especially useful for managing systems that are located in different physical locations or that are not easily accessible.
Second, SSH provides a secure way to access remote systems. All data transmitted over an SSH connection is encrypted, making it difficult for unauthorized users to intercept or eavesdrop on the connection.
Third, SSH is an efficient way to manage remote systems. It uses a command-line interface that allows administrators to quickly and easily execute commands on remote systems.
Use Cases
- Software installation: SSH can be used to install software on remote systems. This can be useful for installing updates, patches, or new applications.
- Configuration management: SSH can be used to manage the configuration of remote systems. This can include changing system settings, creating or modifying user accounts, and installing or removing software packages.
- Remote monitoring: SSH can be used to monitor the status of remote systems. This can include checking system logs, monitoring system performance, and receiving alerts when errors occur.
Final Conclusion
Congratulations on completing this comprehensive guide to Linux Mint SSH Server! By now, you should have a solid understanding of how to install, configure, and use SSH securely and efficiently. Remember to stay updated on the latest security patches and best practices to ensure the ongoing security of your SSH server.
We encourage you to continue exploring the advanced features and capabilities of SSH, as it is a versatile tool that can greatly enhance your remote server management experience. Thank you for choosing Linux Mint SSH Server, and we wish you all the best in your future endeavors.