Secure Shell (SSH), a cornerstone of secure remote access and data transfer, has captivated the world of networking. As we delve into the intricacies of SSH, a fundamental question arises: what network layer protocol does it employ? Is it the reliable TCP or the connectionless UDP? Embark on this journey as we unravel the mysteries surrounding SSH’s transport layer, exploring its intricacies and implications.
SSH, a versatile protocol, has revolutionized the way we manage and secure remote systems. Its ability to establish encrypted connections over insecure networks has made it indispensable for system administrators, network engineers, and anyone seeking secure remote access. Understanding the underlying network layer protocol used by SSH is crucial for optimizing performance, troubleshooting connectivity issues, and mitigating potential security risks.
SSH Connection Protocol
SSH (Secure Shell) is a secure network protocol used for remote login and command execution over an unsecured network. It provides a secure channel over an insecure network, allowing users to access and manage remote systems without compromising sensitive information.
SSH is widely used in various applications, including:
- Remote server management
- Secure file transfer
- Port forwarding
- Secure shell access
Key Features and Benefits
SSH offers several key features and benefits that make it a valuable tool for secure remote access:
- Strong encryption: SSH uses strong encryption algorithms to protect data in transit, preventing unauthorized access or eavesdropping.
- Authentication and authorization: SSH provides robust authentication and authorization mechanisms, ensuring that only authorized users can access remote systems.
- Confidentiality: SSH ensures the confidentiality of data by encrypting all communication, preventing unauthorized parties from accessing sensitive information.
- Integrity: SSH protects the integrity of data by ensuring that it is not modified or corrupted during transmission.
- Cross-platform compatibility: SSH is supported on a wide range of platforms, including Windows, macOS, Linux, and Unix systems, allowing for seamless remote access across different operating systems.
Network Layer Protocols
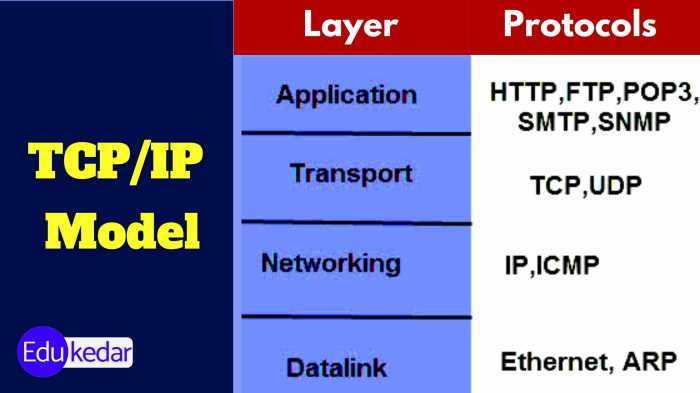
Network layer protocols provide a reliable and efficient means of transmitting data between devices on a network. The two most common network layer protocols are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP (Transmission Control Protocol)
TCP is a connection-oriented protocol, which means that it establishes a virtual circuit between the sender and receiver before transmitting data. This ensures that data is transmitted reliably and in the correct order.
- TCP uses a three-way handshake to establish a connection.
- TCP provides flow control and error correction mechanisms to ensure reliable data transmission.
- TCP is used for applications that require reliable data transmission, such as web browsing and email.
UDP (User Datagram Protocol)
UDP is a connectionless protocol, which means that it does not establish a virtual circuit before transmitting data. This makes UDP faster and more efficient than TCP, but it also makes it less reliable.
- UDP does not use a three-way handshake to establish a connection.
- UDP does not provide flow control or error correction mechanisms.
- UDP is used for applications that do not require reliable data transmission, such as online gaming and video streaming.
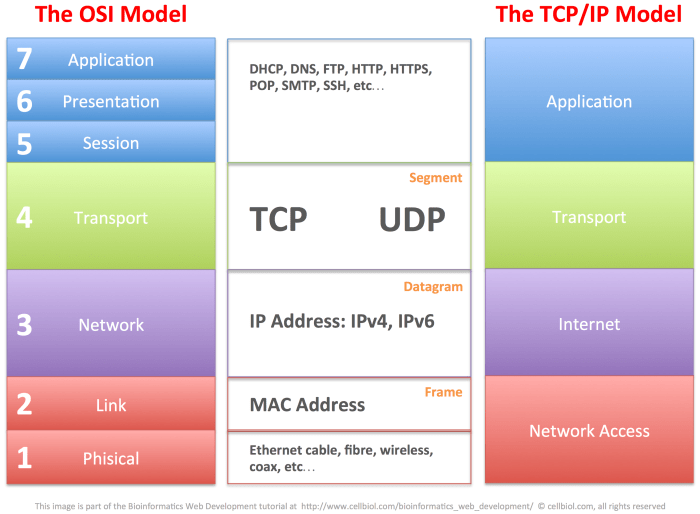
SSH Transport Layer
SSH utilizes the Transport Layer Security (TLS) protocol for secure data transmission. TLS, formerly known as Secure Sockets Layer (SSL), operates at the transport layer of the TCP/IP model, ensuring data privacy, integrity, and authenticity during communication.
Evidence supporting the use of TLS in SSH includes:
- OpenSSH, a widely adopted SSH implementation, explicitly states that it uses TLS for encryption and authentication.
- Network traffic analysis tools, such as Wireshark, can capture and decode SSH connections, revealing the use of TLS.
SSH Port Usage
SSH primarily utilizes a specific port number for establishing secure connections. Additionally, it may employ other ports for specific purposes.
Default Port
The default port associated with SSH is 22. This port is widely recognized and used by default for SSH connections, providing a standardized and well-known access point for remote logins.
Additional Ports
In certain scenarios, SSH may utilize additional ports beyond the default port 22. These ports are typically used for specific purposes, such as:
- Port 2222: Sometimes used as an alternative port for SSH connections, particularly when the default port 22 is blocked or unavailable.
- Port 443: SSH can be configured to operate over port 443, which is commonly used for HTTPS traffic. This allows SSH connections to blend in with regular web traffic, potentially evading detection in restrictive environments.
SSH Encryption
SSH utilizes a combination of encryption algorithms to protect data transmission, ensuring the confidentiality and integrity of communications. The algorithms employed vary depending on the SSH version and configuration.
SSH establishes a secure channel through a combination of symmetric and asymmetric encryption. Asymmetric encryption, using algorithms like RSA or DSA, is used for key exchange, while symmetric encryption, using algorithms like AES or 3DES, is used to encrypt the actual data transmitted.
Key Exchange
Key exchange is a crucial step in SSH encryption. It involves establishing a shared secret key between the client and server without transmitting it directly over the network. SSH supports multiple key exchange algorithms, including:
- Diffie-Hellman
- RSA
- ECDH
Data Encryption
Once the shared secret key is established, SSH uses symmetric encryption algorithms to encrypt the data transmitted. These algorithms include:
- AES (Advanced Encryption Standard)
- 3DES (Triple Data Encryption Standard)
- Twofish
- Blowfish
SSH also employs message authentication codes (MACs) to ensure the integrity of data transmission. MACs, such as HMAC-SHA1 or HMAC-SHA256, are used to verify that the received data has not been tampered with.
SSH Authentication
SSH supports various authentication methods, providing flexibility and security for user access. These methods include:
-
- -*Password Authentication Users provide a password to establish their identity. While simple, it’s susceptible to brute-force attacks.
-*Public-Key Authentication
Users generate a pair of cryptographic keys, one public and one private. The public key is shared with the SSH server, while the private key is kept secret. When a user connects, the server sends a challenge, which is encrypted using the public key.
Only the user with the corresponding private key can decrypt the challenge and prove their identity.
-*Keyboard-Interactive Authentication
The server prompts the user for additional information, such as a one-time password or answers to security questions. This method is often used as a second-factor authentication mechanism.
-*Host-Based Authentication
Users can configure SSH to allow connections from specific hosts or networks. This method is suitable for trusted environments and automated processes.
SSH manages user access and authorization through the use of authorized_keys files and user-specific configuration settings.
The authorized_keys file contains the public keys of authorized users, and SSH checks this file to determine if a user is allowed to connect. Additionally, SSH can be configured to restrict access based on factors such as IP address, username, and time of day.
SSH Tunneling
SSH tunneling, also known as port forwarding, is a technique that allows you to establish a secure connection between two networks or hosts over an insecure network.
It involves creating an encrypted SSH tunnel through which data can be transmitted securely, even if the underlying network is not secure.
SSH Tunneling Use Cases
- Securely accessing remote resources: SSH tunneling can be used to securely access resources on a remote network, such as a file server or database, from a client machine over an insecure network like the internet.
- Bypassing firewalls: SSH tunneling can be used to bypass firewalls or other network restrictions by creating a secure tunnel through the firewall.
- Securely connecting to applications: SSH tunneling can be used to securely connect to applications that are not natively supported by SSH, such as web servers or email clients.
SSH Security Considerations
SSH is generally considered secure, but like any protocol, it has potential vulnerabilities. It’s essential to understand these vulnerabilities and implement best practices to mitigate risks.
Potential Vulnerabilities
-
- -*Weak Passwords Weak passwords are easily compromised, allowing attackers to gain unauthorized access.
-*Unpatched Software
Outdated SSH software may contain vulnerabilities that can be exploited.
-*Man-in-the-Middle Attacks
Attackers can intercept and modify SSH traffic, impersonating the server or client.
-*Brute Force Attacks
Attackers can attempt to guess passwords through repeated login attempts.
-*Buffer Overflow Attacks
Sending excessive data to an SSH server can cause a buffer overflow, leading to arbitrary code execution.
Best Practices for Mitigation
-
- -*Use Strong Passwords Implement strong password policies and consider using two-factor authentication.
-*Keep Software Updated
Regularly patch SSH software to address known vulnerabilities.
-*Use Key-Based Authentication
Use public-key cryptography instead of passwords for more secure authentication.
-*Limit Access
Restrict SSH access to only authorized users and IP addresses.
-*Disable Unused Services
Disable SSH services that are not required, such as remote X11 forwarding.
-*Monitor Logs
Regularly monitor SSH logs for suspicious activity and investigate any anomalies promptly.
SSH Management Tools
SSH management tools are essential for administrators to effectively manage SSH servers and ensure their security. These tools provide a comprehensive range of features to monitor, configure, and troubleshoot SSH servers, enabling administrators to maintain optimal performance and mitigate potential threats.
OpenSSH
OpenSSH is a widely used and open-source SSH management tool that provides a suite of utilities for managing SSH servers and clients. It includes commands such as ssh, sshd, scp, and sftp, which allow administrators to perform various tasks, including:
- Managing SSH server configuration
- Creating and managing SSH keys
- Securely transferring files over SSH
- Interactive shell access to remote systems
Paramiko
Paramiko is a Python library that provides a comprehensive set of tools for interacting with SSH servers. It enables developers to write Python scripts to automate SSH tasks, such as:
- Connecting to SSH servers
- Executing commands remotely
- Transferring files securely
- Managing SSH keys
SSHGuard
SSHGuard is an SSH brute-force protection tool that helps prevent unauthorized access to SSH servers. It monitors SSH login attempts and automatically blocks IP addresses that exhibit suspicious behavior, such as repeated failed login attempts.
Fail2ban
Fail2ban is a general-purpose intrusion detection and prevention system that can be used to protect SSH servers from brute-force attacks. It monitors log files for failed login attempts and automatically bans IP addresses that exceed a predefined threshold.
Bastille
Bastille is a hardening tool that can be used to secure SSH servers by applying a set of security best practices. It automates the process of configuring SSH servers to mitigate common vulnerabilities, such as disabling root login and enforcing strong password policies.
SSH Configuration
SSH configuration plays a crucial role in enhancing security and optimizing performance. It allows administrators to customize various parameters to suit specific environments and security requirements.
Key SSH configuration parameters include:
- Port: Specifies the TCP port on which the SSH server listens for incoming connections. The default port is 22, but it’s recommended to change it to a non-standard port for added security.
- Protocol: Determines the version of the SSH protocol to be used. SSHv2 is the preferred version due to its enhanced security features.
- Ciphers: Defines the encryption algorithms used to protect data transmitted over the SSH connection. Strong ciphers, such as AES-256, provide high levels of encryption.
- MAC algorithms: Specifies the algorithms used to ensure the integrity of data transmitted over the SSH connection. Strong MAC algorithms, such as HMAC-SHA256, prevent data tampering.
- Key exchange algorithms: Determines the algorithms used to establish a secure key exchange between the client and server. Strong key exchange algorithms, such as Diffie-Hellman, provide high levels of security.
- Authentication methods: Specifies the methods used to authenticate users to the SSH server. Password-based authentication is common, but it’s recommended to use more secure methods such as public key authentication or two-factor authentication.
- Logging level: Determines the amount of information logged by the SSH server. Verbose logging can provide valuable insights for troubleshooting and security analysis.
Optimizing SSH configuration for different environments requires careful consideration of security requirements, performance needs, and the specific use cases involved. Here are some general guidelines:
- For high-security environments: Use strong ciphers, MAC algorithms, and key exchange algorithms. Enable two-factor authentication and consider using a non-standard port.
- For performance-sensitive environments: Choose ciphers and MAC algorithms that balance security with performance. Consider increasing the number of parallel SSH sessions allowed.
- For specific use cases: Configure SSH parameters to meet specific requirements. For example, enable port forwarding or X11 forwarding if needed.
Regularly reviewing and updating SSH configuration is essential to maintain optimal security and performance. By understanding the key parameters and following best practices, administrators can ensure that their SSH deployments are secure and reliable.
Last Word
In conclusion, SSH’s adoption of TCP as its transport layer protocol underscores its commitment to reliable and secure data transmission. While UDP offers speed advantages, TCP’s inherent reliability and congestion control mechanisms make it the ideal choice for SSH’s critical role in remote access and data transfer.
By leveraging TCP’s strengths, SSH ensures the integrity, confidentiality, and availability of data, even in challenging network conditions.