SSH, or Secure Shell, is a network protocol that provides secure remote access to a computer system. It is widely used for managing servers, transferring files, and executing commands on remote machines. Understanding the underlying protocols used by SSH is crucial for optimizing its performance and security.
This guide will delve into the fundamental differences between TCP and UDP protocols and explore how SSH utilizes both of them. We will examine the advantages and disadvantages of each protocol in SSH and provide practical examples of their real-world applications.
By the end of this discussion, you will have a comprehensive understanding of SSH protocol usage and the role of TCP and UDP in its operation.
Protocol Overview
TCP and UDP are two distinct network protocols that serve different purposes and exhibit unique characteristics. Understanding the fundamental differences between these protocols is crucial for optimizing network performance and selecting the most appropriate protocol for specific applications.
TCP, or Transmission Control Protocol, is a connection-oriented protocol that establishes a reliable, end-to-end connection between two devices. It guarantees that data is transmitted in the correct order and that all packets are received without errors. TCP employs mechanisms like error checking, flow control, and congestion control to ensure reliable data delivery.
UDP, or User Datagram Protocol, on the other hand, is a connectionless protocol that does not establish a connection before sending data. It simply sends data packets without any guarantees of delivery or order. UDP is faster and more efficient than TCP but less reliable.
It is often used for applications where speed and low latency are more critical than reliability, such as online gaming, video streaming, and voice over IP (VoIP).
Comparison
- Connection-oriented vs. Connectionless: TCP establishes a connection before sending data, while UDP does not.
- Reliability: TCP guarantees reliable data delivery, while UDP does not.
- Speed: UDP is faster than TCP because it does not have to establish a connection or perform error checking.
- Applications: TCP is suitable for applications that require reliable data delivery, such as file transfer and web browsing, while UDP is suitable for applications that prioritize speed and low latency, such as online gaming and video streaming.
SSH Protocol
The SSH protocol, short for Secure Shell protocol, is a secure network protocol that allows for remote access and management of computer systems. It provides a secure channel over an insecure network, enabling users to securely connect to a remote computer and execute commands, transfer files, and manage system configurations.
SSH utilizes both TCP and UDP ports for different purposes. TCP port 22 is the default port used for SSH connections, providing a reliable and ordered data transmission channel for interactive sessions and file transfers. UDP port 3389 is used for X11 forwarding, allowing users to remotely display graphical applications running on the server on their local computer.
SSH Port Usage
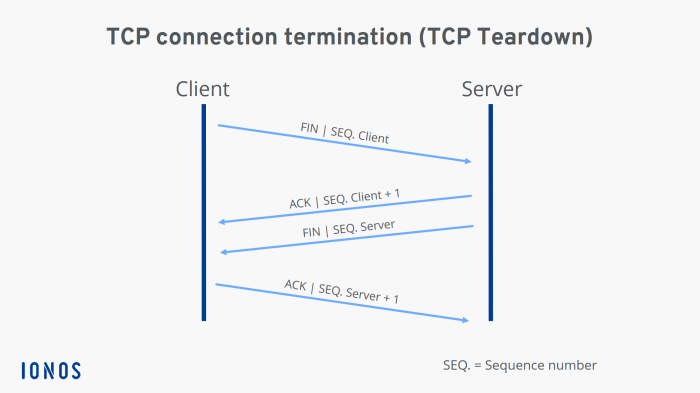
SSH utilizes both TCP and UDP ports for its operation. Each port serves a specific purpose in establishing and maintaining secure connections.
The following table Artikels the default TCP and UDP ports used by SSH:
| Port | Protocol | Purpose |
|---|---|---|
| 22 | TCP | Default port for SSH connections |
| 2222 | TCP | Alternative port for SSH connections, commonly used to bypass firewalls |
| 514 | UDP | Port for establishing UDP-based SSH connections |
| 515 | UDP | Port for receiving UDP-based SSH traffic |
The default port for SSH connections is TCP port 22. This port is widely recognized and used by most SSH clients and servers. However, it is possible to configure SSH to use alternative ports, such as port 2222, to enhance security or bypass firewall restrictions.
UDP ports 514 and 515 are used for UDP-based SSH connections. UDP is a connectionless protocol that offers faster connection establishment compared to TCP. However, UDP connections are less reliable and may not be suitable for all SSH applications.
TCP vs. UDP in SSH
SSH, or Secure Shell, is a network protocol that provides secure remote access to a computer. It can be used for a variety of purposes, such as managing servers, transferring files, and running commands remotely.
SSH uses two different transport protocols: TCP and UDP. TCP is a reliable, connection-oriented protocol that guarantees that data is delivered in the correct order and without errors. UDP is an unreliable, connectionless protocol that does not guarantee that data will be delivered in the correct order or without errors.
However, UDP is faster than TCP and is often used for applications that require real-time data transfer, such as streaming video or audio.
Advantages and Disadvantages of TCP and UDP in SSH
- Advantages of TCP
- Reliable: TCP guarantees that data is delivered in the correct order and without errors.
- Connection-oriented: TCP establishes a connection between the client and server before any data is transferred. This allows for more efficient and secure data transfer.
- Disadvantages of TCP
- Slower: TCP is slower than UDP because it has to establish a connection before any data can be transferred.
- More overhead: TCP has more overhead than UDP because it has to maintain a connection between the client and server.
- Advantages of UDP
- Faster: UDP is faster than TCP because it does not have to establish a connection before any data can be transferred.
- Less overhead: UDP has less overhead than TCP because it does not have to maintain a connection between the client and server.
- Disadvantages of UDP
- Unreliable: UDP does not guarantee that data will be delivered in the correct order or without errors.
- Connectionless: UDP does not establish a connection between the client and server before any data is transferred. This can make it more difficult to troubleshoot problems.
When to Use TCP and UDP in SSH
TCP is the best choice for SSH when you need reliable data transfer. This is important for applications that require high levels of security, such as financial transactions or remote management of critical systems.
UDP is the best choice for SSH when you need fast data transfer. This is important for applications that require real-time data transfer, such as streaming video or audio.
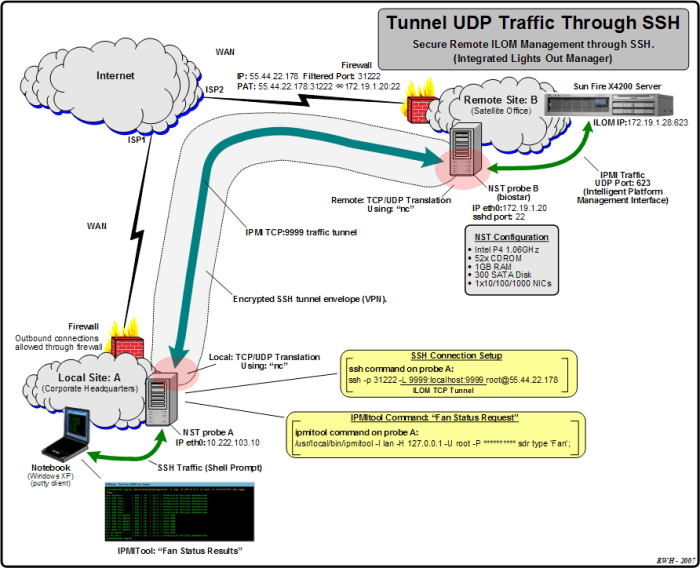
SSH Tunneling
SSH tunneling is a technique that allows you to create a secure, encrypted connection between two remote hosts over an insecure network. This is achieved by creating an SSH tunnel, which is a virtual network interface that encapsulates the traffic between the two hosts within an SSH connection.SSH
tunneling can be used to accomplish a variety of tasks, such as:*
-*Securely accessing remote resources
SSH tunneling can be used to securely access remote resources, such as files, databases, and applications, over an insecure network.
-
- -*Bypassing firewalls
SSH tunneling can be used to bypass firewalls that block certain types of traffic.
- -*Bypassing firewalls
-*Creating private networks
SSH tunneling can be used to create private networks between two or more hosts that are not directly connected.
TCP and UDP in SSH Tunneling
SSH tunneling can be used with both TCP and UDP traffic.
TCP is a connection-oriented protocol, which means that it establishes a connection between two hosts before any data is transmitted. UDP is a connectionless protocol, which means that it does not establish a connection before sending data.TCP is typically used for applications that require reliable data transmission, such as file transfers and remote desktop connections.
UDP is typically used for applications that do not require reliable data transmission, such as streaming media and online gaming.When using SSH tunneling with TCP, the SSH client and server establish a TCP connection before any data is transmitted. The SSH client then creates a virtual network interface that encapsulates the TCP traffic within the SSH connection.
The SSH server then forwards the TCP traffic to the remote host.When using SSH tunneling with UDP, the SSH client and server do not establish a TCP connection before any data is transmitted. Instead, the SSH client creates a virtual network interface that encapsulates the UDP traffic within the SSH connection.
The SSH server then forwards the UDP traffic to the remote host.
Security Considerations
When evaluating the security implications of SSH over TCP and UDP, it’s crucial to understand the inherent characteristics of each protocol.
TCP
TCP, a connection-oriented protocol, establishes a reliable communication channel before data transfer. This reliability comes with overhead, making it less suitable for applications requiring real-time or low-latency data transmission.
In the context of SSH, TCP provides a secure and stable connection, making it ideal for interactive sessions and file transfers. However, its connection-oriented nature introduces potential vulnerabilities, such as:
- Connection hijacking: An attacker may intercept and take control of an established TCP connection.
- Denial-of-service (DoS) attacks: An attacker can flood a TCP server with connection requests, overwhelming its resources and preventing legitimate connections.
UDP
UDP, a connectionless protocol, operates without establishing a prior connection. It prioritizes speed and efficiency over reliability, making it suitable for applications that require low latency and can tolerate occasional data loss.
In the context of SSH, UDP can provide faster connection establishment and data transfer, but it also introduces different security considerations:
- Spoofing: An attacker can impersonate a legitimate SSH server by sending UDP packets with a forged source IP address.
- Eavesdropping: UDP packets are sent in plaintext, making them vulnerable to eavesdropping by attackers.
Performance Comparison
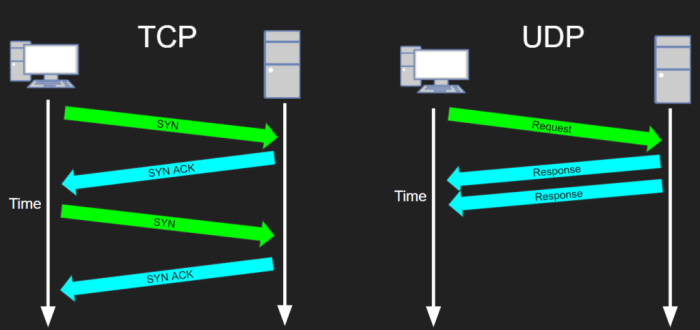
TCP and UDP exhibit distinct performance characteristics in SSH. TCP, with its connection-oriented nature, ensures reliable data transmission by establishing a virtual circuit between the client and server. This mechanism introduces additional overhead and latency, making TCP less suitable for applications requiring real-time performance.
UDP, on the other hand, is a connectionless protocol, offering higher speed and lower latency due to its simplified data transmission process. However, UDP’s lack of error correction and flow control mechanisms can lead to data loss or corruption in unstable network conditions.
Latency
TCP typically introduces higher latency compared to UDP. The connection establishment and teardown processes, along with the need for acknowledgment and retransmission mechanisms, contribute to the increased latency in TCP.
Bandwidth Utilization
TCP efficiently utilizes bandwidth by dynamically adjusting the transmission rate based on network conditions. UDP, lacking flow control mechanisms, may send data at a rate exceeding the network’s capacity, leading to packet loss and reduced effective bandwidth.
Packet Loss
TCP’s error correction and retransmission mechanisms effectively handle packet loss, ensuring reliable data delivery. UDP, however, does not provide any inherent packet recovery mechanisms, making it more susceptible to data loss in unstable network conditions.
Real-World Applications
SSH finds widespread use in various real-world scenarios, leveraging both TCP and UDP protocols.
SSH with TCP
TCP’s reliability and error correction make it ideal for applications requiring secure data transfer. SSH over TCP is commonly employed in:
- Secure remote administration: Accessing and managing servers remotely, often for configuration, maintenance, and troubleshooting.
- File transfer: Securely transferring files between remote hosts, often using protocols like SCP (Secure Copy) and SFTP (SSH File Transfer Protocol).
- Port forwarding: Tunneling specific ports or applications through an SSH connection, enabling secure access to otherwise inaccessible services.
SSH with UDP
UDP’s speed and low overhead make it suitable for applications where latency is critical. SSH over UDP is often used in:
- Interactive remote sessions: Providing real-time interactive access to remote servers, such as for troubleshooting or command execution.
- Secure voice and video conferencing: Establishing secure communication channels for voice and video calls over SSH.
- Remote gaming: Enabling secure multiplayer gaming sessions over SSH, reducing latency and improving gameplay.
Each protocol has its advantages and challenges, making the choice between TCP and UDP dependent on the specific application and performance requirements.
Best Practices
When choosing between TCP and UDP for SSH, consider the specific requirements of your application. TCP provides reliable, in-order delivery of data, making it suitable for interactive sessions and file transfers. UDP, on the other hand, offers lower latency and overhead, making it a good choice for applications that require real-time performance.To
optimize SSH performance and security, follow these best practices:
- Use strong encryption algorithms such as AES-256 or ChaCha20.
- Disable unused SSH services and protocols to reduce the attack surface.
- Limit access to SSH servers using firewalls and access control lists.
- Regularly update SSH software to patch security vulnerabilities.
- Monitor SSH logs for suspicious activity and investigate any potential threats.
Troubleshooting
When working with SSH over TCP or UDP, various issues can arise. Here are some common troubleshooting scenarios and their potential solutions:
Connection Issues
If you encounter difficulties establishing an SSH connection, consider the following:
- Check firewall settings: Ensure that your firewall is not blocking the SSH port (default: 22 for TCP and 2222 for UDP).
- Verify IP address: Make sure you are connecting to the correct IP address of the remote host.
- Check SSH service: Confirm that the SSH service is running on the remote host.
Authentication Issues
If you are unable to authenticate to the remote host via SSH, consider the following:
- Correct credentials: Ensure that you are using the correct username and password or SSH key.
- Two-factor authentication: If two-factor authentication is enabled, provide the necessary verification code.
- Check user permissions: Verify that the user account you are using has the necessary permissions to log in to the remote host.
SSH Tunneling Issues
If you experience problems setting up or using SSH tunneling, consider the following:
- Firewall rules: Make sure that firewall rules are configured to allow traffic through the tunnel.
- Port forwarding: Check if the correct ports are being forwarded on both the client and server sides.
- Local and remote ports: Verify that the local and remote ports specified in the SSH tunnel configuration are correct.
Performance Issues
If you encounter performance issues with SSH, consider the following:
- Network bandwidth: Ensure that the network bandwidth is sufficient to support the required data transfer.
- SSH cipher: Try experimenting with different SSH ciphers to find one that offers a balance between security and performance.
- Compression: Enable SSH compression to reduce the size of data packets and improve performance over high-latency connections.
Other Issues
Other potential issues with SSH include:
- Host key mismatch: Verify the host key fingerprint to ensure that you are connecting to the intended host.
- SSH version compatibility: Make sure that both the client and server are using compatible SSH versions.
- Resource exhaustion: Check for resource exhaustion issues on the remote host, such as high CPU or memory usage.
Conclusion
In summary, SSH is a versatile protocol that leverages both TCP and UDP to provide secure and efficient remote access. TCP offers reliable and ordered data transmission, while UDP enables faster and more lightweight communication. The choice between TCP and UDP depends on the specific requirements of the SSH application and the underlying network conditions.
By understanding the characteristics and usage of each protocol, system administrators and network engineers can optimize SSH performance, enhance security, and troubleshoot potential issues effectively.