SSH.SSHSlowdns.com – In the realm of secure and efficient data transfer, SSH (Secure Shell) and UDP (User Datagram Protocol) emerge as formidable allies. SSH UDP, a combination of these two protocols, offers an exceptional solution for transmitting data swiftly and securely over networks.
SSH, renowned for its robust encryption, establishes a secure channel for data transmission. UDP, known for its speed and low overhead, ensures lightning-fast delivery. By harnessing the strengths of both protocols, SSH UDP empowers users with a powerful tool for secure and expedited data transfer.
Introduction
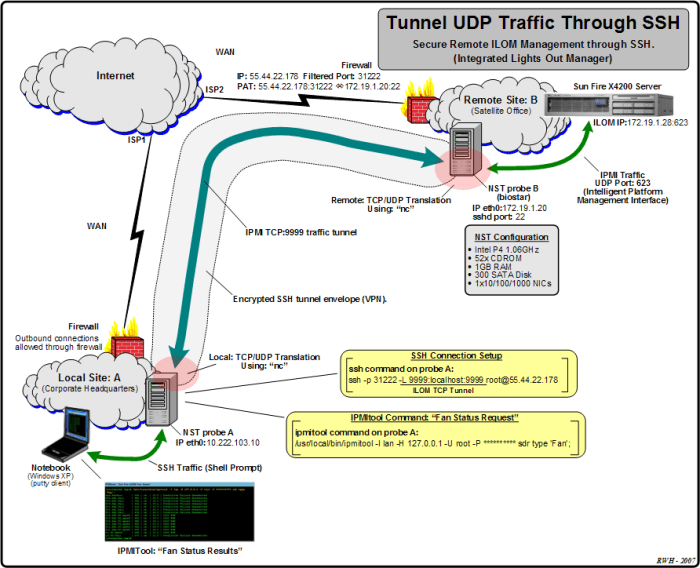
SSH (Secure Shell) is a network protocol that provides a secure way to access a remote computer. It uses strong encryption to protect data from eavesdropping and tampering.
UDP (User Datagram Protocol) is a transport protocol that is used for sending data over a network. It is a connectionless protocol, which means that it does not require a connection to be established before data can be sent.
SSH over UDP
SSH over UDP is a combination of the SSH and UDP protocols. It provides the security of SSH with the speed and efficiency of UDP.
- Speed: UDP is a faster protocol than TCP, which is the protocol that is typically used with SSH. This makes SSH over UDP ideal for applications that require high speed, such as remote desktop sharing and video conferencing.
- Efficiency: UDP is a more efficient protocol than TCP. This makes SSH over UDP ideal for applications that require low latency, such as online gaming and real-time data transmission.
Methods of Establishing Free SSH UDP
Establishing a free SSH UDP connection involves setting up a server and connecting to it. Here are the steps to set up a free SSH UDP server:
- Install an SSH server: Choose an SSH server software, such as OpenSSH, and install it on the server machine.
- Configure the SSH server: Edit the SSH server configuration file to enable UDP port forwarding. Typically, this involves adding the “-u” flag to the SSH command.
- Start the SSH server: Once configured, start the SSH server using the appropriate command, usually “sshd”.
To connect to a free SSH UDP server, you can use a variety of methods:
- SSH client: Use an SSH client, such as PuTTY or OpenSSH, to connect to the server using the UDP port.
- UDP proxy: Set up a UDP proxy on the client machine to forward UDP traffic to the SSH server.
- SOCKS proxy: Use a SOCKS proxy to tunnel UDP traffic through an SSH connection.
Security Considerations
SSH UDP connections offer certain advantages, but it’s crucial to be aware of the potential security risks involved.
One major concern is that UDP is a connectionless protocol, which means it doesn’t establish a persistent connection between the client and server. This makes it easier for attackers to intercept and eavesdrop on data transmitted over the connection.
Best Practices
- Use strong encryption: Employ robust encryption algorithms like AES-256 or ChaCha20 to protect data transmitted over the SSH UDP connection.
- Enable IP filtering: Configure firewalls to restrict access to the SSH UDP port from only trusted IP addresses.
- Disable unnecessary services: Turn off any unused services or ports on the server to minimize potential attack vectors.
- Regularly update software: Keep SSH and operating system software up to date to patch security vulnerabilities.
- Monitor logs: Regularly review SSH logs for suspicious activity and take appropriate action if any anomalies are detected.
Use Cases for Free SSH UDP
Free SSH UDP offers several advantages over traditional SSH connections, making it suitable for various use cases. These scenarios highlight the benefits and drawbacks of using SSH UDP.
One of the primary advantages of SSH UDP is its speed and efficiency. UDP is a connectionless protocol, which means it does not require a three-way handshake like TCP. This makes SSH UDP ideal for applications that require fast and reliable data transfer, such as online gaming, streaming media, and VoIP.
Remote Access and Management
SSH UDP can be used for remote access and management of servers and other network devices. It provides a secure and efficient way to connect to remote systems and perform administrative tasks, such as file transfer, command execution, and system monitoring.
SSH UDP is particularly useful in situations where speed and reliability are critical, such as when managing remote servers in high-latency environments.
Tunneling
SSH UDP can be used to create secure tunnels through firewalls and other network restrictions. This allows users to access blocked websites and services, or to connect to remote networks securely. SSH UDP tunneling is often used for bypassing censorship, accessing geo-restricted content, and establishing secure connections over untrusted networks.
Network Monitoring and Troubleshooting
SSH UDP can be used for network monitoring and troubleshooting purposes. It allows users to remotely monitor network traffic, identify performance issues, and troubleshoot connectivity problems. SSH UDP is particularly useful for monitoring remote networks and devices that are not easily accessible through other means.
Disadvantages of SSH UDP
While SSH UDP offers several advantages, it also has some disadvantages that should be considered before using it. One of the main drawbacks of SSH UDP is its lack of reliability compared to TCP. UDP is a connectionless protocol, which means it does not guarantee that data will be delivered or received in the correct order.
This can be a problem for applications that require reliable data transfer, such as file transfers or database operations.
Another disadvantage of SSH UDP is its increased vulnerability to security attacks. UDP packets are not encrypted by default, which makes them susceptible to eavesdropping and other attacks. To ensure security, SSH UDP should be used in conjunction with encryption mechanisms such as IPSec or TLS.
Alternatives to Free SSH UDP
Free SSH UDP is a popular solution for secure remote access, but it’s not the only option. Several alternatives offer different features and benefits, catering to specific needs.
Let’s explore some notable alternatives to Free SSH UDP:
OpenSSH
- Open source and widely used SSH implementation
- Supports a wide range of authentication methods and encryption algorithms
- Offers strong security and stability
- Feature-rich with support for port forwarding, X11 forwarding, and more
WireGuard
- Modern and high-performance VPN protocol
- Uses state-of-the-art cryptography for secure communication
- Lightweight and easy to configure
- Supports UDP-based connections, providing low latency and fast speeds
Tailscale
- Managed VPN service with a focus on ease of use
- Provides automatic device discovery and connection management
- Offers strong security with end-to-end encryption
- Supports multiple devices and platforms, including mobile devices
ZeroTier
- Virtual LAN service that creates a private network over the internet
- Uses a software-defined networking approach for flexible and scalable connectivity
- Provides low latency and high bandwidth
- Supports a wide range of devices and operating systems
Open Source Tools for SSH UDP
SSH UDP connections can be managed using several open-source tools and libraries. These tools provide various features and capabilities, enabling users to establish, maintain, and secure SSH UDP connections.
OpenSSH
OpenSSH is a widely used open-source suite of tools for secure remote login and file transfer. It includes support for SSH UDP, allowing users to create and manage SSH UDP connections. OpenSSH provides features such as strong encryption, authentication mechanisms, and port forwarding.
Stunnel
Stunnel is an open-source tool that provides TLS/SSL encryption for network connections. It can be used to establish SSH UDP connections over an encrypted tunnel, enhancing the security of the connection. Stunnel supports various encryption algorithms and protocols, allowing users to customize the level of security based on their requirements.
ProxyChains
ProxyChains is an open-source tool that allows users to redirect network traffic through a chain of proxies. It can be used to establish SSH UDP connections through a proxy server, providing anonymity and bypassing network restrictions. ProxyChains supports various proxy protocols and allows users to configure multiple proxy servers for redundancy and load balancing.
PuTTY
PuTTY is a free and open-source SSH and Telnet client for Windows platforms. It includes support for SSH UDP, allowing users to create and manage SSH UDP connections from Windows machines. PuTTY provides features such as session management, key management, and port forwarding, making it a convenient tool for managing SSH UDP connections.
Performance Considerations
SSH UDP exhibits unique performance characteristics that differentiate it from other protocols. Understanding these characteristics and implementing optimization techniques can significantly enhance the efficiency and responsiveness of SSH UDP connections.
One key aspect to consider is the inherent overhead associated with UDP. Unlike TCP, UDP does not establish a reliable connection, resulting in potential packet loss and retransmissions. However, this overhead can be mitigated by utilizing larger UDP packets, which reduce the number of packets required for data transfer and minimize the impact of packet loss.
Packet Size Optimization
Optimizing the packet size for SSH UDP is crucial for maximizing performance. Larger packets can accommodate more data, reducing the number of packets transmitted and improving overall throughput. However, excessively large packets may fragment during transmission, leading to reduced efficiency.
Experimenting with different packet sizes can help determine the optimal balance between packet size and fragmentation.
Troubleshooting SSH UDP Issues
Identifying and resolving common SSH UDP issues can enhance the stability and reliability of your SSH UDP connections. Let’s explore some troubleshooting techniques:
Common Issues and Solutions
- Connection Refused: Verify that the SSH UDP port (default 53) is open on both the client and server firewalls.
- Timeout Errors: Adjust the timeout settings in your SSH client configuration to account for network latency or high traffic.
- Data Corruption: Enable error checking mechanisms in your SSH configuration to detect and correct data transmission errors.
Additional Troubleshooting Steps
- Check Firewall Settings: Ensure that the SSH UDP port is allowed through all relevant firewalls.
- Test Connectivity: Use tools like “nmap” or “netcat” to test if the SSH UDP port is accessible from both the client and server.
- Review SSH Configuration: Verify that the SSH configuration on both the client and server is correct, including the UDP port setting.
- Examine Network Logs: Analyze network logs to identify any errors or connection issues related to SSH UDP.
Example Use Cases
Free SSH UDP finds applications in various scenarios, offering benefits such as secure data transfer, remote access, and network tunneling.
However, it’s crucial to consider the challenges associated with UDP, such as potential packet loss and lack of inherent reliability.
Secure Data Transfer
SSH UDP can be employed to securely transfer sensitive data between remote locations. By encrypting the data, it protects against unauthorized access and eavesdropping.
Remote Access
Free SSH UDP enables secure remote access to servers and devices, allowing administrators to perform tasks such as configuration, troubleshooting, and file management from any location with an internet connection.
Network Tunneling
SSH UDP can establish secure tunnels through firewalls and other network restrictions, allowing traffic to bypass these barriers and reach its intended destination.
Future Developments
The future of free SSH UDP is promising, with advancements in technology expected to enhance its capabilities and expand its applications.
One emerging trend is the integration of artificial intelligence (AI) and machine learning (ML) into SSH UDP. AI algorithms can automate tasks, improve security, and optimize performance. For instance, AI can detect and block malicious traffic, reducing the risk of attacks.
Quantum Computing
Quantum computing is another potential game-changer. Quantum computers can perform complex calculations much faster than traditional computers, enabling faster and more efficient encryption and decryption processes.