ssh.sshslowdns.com – Secure Shell (SSH) has become an indispensable tool for system administrators and users alike, providing a secure and encrypted channel for remote access, file transfer, and command execution. In this comprehensive guide, we delve into the world of Fedora SSH server, exploring its features, configuration, security best practices, and troubleshooting techniques.
Whether you’re a seasoned Linux enthusiast or just starting your journey with SSH, this guide will equip you with the knowledge and skills to harness the power of Fedora SSH server.
Fedora SSH server, a robust and versatile implementation of the SSH protocol, offers a wide range of capabilities, including secure remote login, file transfer using SFTP and SCP, port forwarding, and much more. Its flexibility and ease of use make it an ideal choice for system administrators seeking a reliable and secure remote access solution.
SSH Server Overview
SSH, or Secure Shell, is a network protocol that allows secure remote login and command execution over an unsecured network. It provides a secure channel for transmitting data between two computers, enabling users to access and manage remote systems as if they were physically present.
SSH servers are essential components of secure remote administration and management, providing a range of benefits, including:
Encrypted communication
SSH encrypts all data transmitted between the client and server, protecting sensitive information from eavesdropping and unauthorized access.
Strong authentication
SSH supports various authentication methods, including passwords, public-key cryptography, and two-factor authentication, ensuring only authorized users can access the remote system.
Remote command execution
SSH allows users to execute commands on remote systems as if they were present locally, providing convenient and efficient system management.
Port forwarding
SSH supports port forwarding, allowing users to securely access services running on the remote system from their local machine, even if those services are not directly accessible from the internet.
File transfer
SSH supports secure file transfer capabilities, enabling users to securely transfer files between the client and server.SSH has evolved significantly since its inception in the early 1990s. The original SSH protocol, SSH-1, was replaced by SSH-2 in 1996, which introduced significant improvements in security, speed, and functionality.
SSH-2 is the current standard for secure remote access and is widely supported by various operating systems and applications.
Fedora SSH Server Installation

Installing an SSH server on a Fedora system is a straightforward process that can be completed in a few steps. This guide will provide detailed instructions on how to install and configure the SSH server, as well as troubleshooting tips for common issues.
Before proceeding with the installation, ensure that your system is up-to-date by running the following command:
sudo dnf update Step 1: Install the SSH Server
To install the SSH server on Fedora, use the following command:
sudo dnf install openssh-server This command will install the SSH server and its dependencies.
Step 2: Start the SSH Server
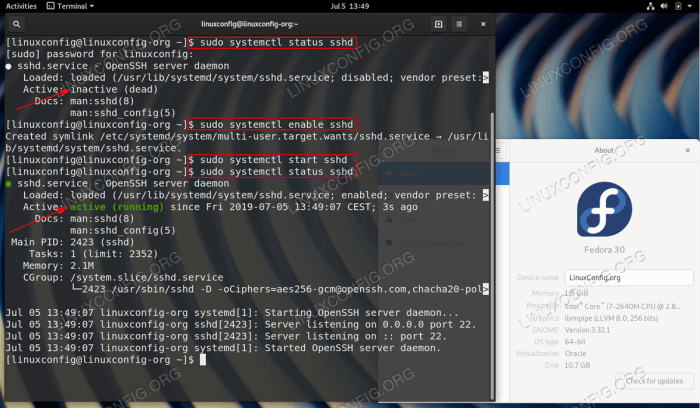
Once the SSH server is installed, you can start it using the following command:
sudo systemctl start sshd You can check if the SSH server is running by using the following command:
sudo systemctl status sshd Step 3: Configure the SSH Server
The SSH server configuration file is located at /etc/ssh/sshd_config. You can edit this file using your preferred text editor. Some common configuration options include:
- Port: The port on which the SSH server listens for incoming connections. The default port is 22.
- PermitRootLogin: Specifies whether root login is allowed. The default is no.
- PasswordAuthentication: Specifies whether password authentication is allowed. The default is yes.
- ChallengeResponseAuthentication: Specifies whether challenge-response authentication is allowed. The default is no.
Step 4: Troubleshooting
If you encounter any issues while installing or configuring the SSH server, you can check the following:
- Firewall: Ensure that the firewall is not blocking the SSH port.
- SELinux: If SELinux is enabled, you may need to adjust the SELinux policy to allow SSH traffic.
- Log files: Check the SSH server log files for any error messages.
SSH Server Configuration
The SSH server offers a wide range of configuration options that allow you to tailor it to meet your specific security, performance, and access control requirements.
To configure the SSH server, edit the configuration file located at /etc/ssh/sshd_config. The file contains a series of directives, each of which controls a specific aspect of the server’s behavior.
Security Settings
The following directives can be used to enhance the security of your SSH server:
- PasswordAuthentication: Disable password-based authentication to prevent brute-force attacks.
- ChallengeResponseAuthentication: Disable challenge-response authentication to prevent eavesdropping.
- UsePAM: Enable Pluggable Authentication Modules (PAM) to use system-wide authentication mechanisms.
- PermitRootLogin: Restrict root login via SSH to prevent unauthorized access.
Performance Settings
The following directives can be used to optimize the performance of your SSH server:
- MaxSessions: Set the maximum number of simultaneous SSH sessions allowed per user.
- MaxAuthTries: Set the maximum number of authentication attempts allowed before the connection is terminated.
- Ciphers: Specify the encryption algorithms to be used for SSH connections.
- Compression: Enable or disable compression to reduce network bandwidth usage.
Access Control Settings
The following directives can be used to control access to your SSH server:
- AllowUsers: Specify the users who are allowed to connect to the server.
- DenyUsers: Specify the users who are not allowed to connect to the server.
- AllowGroups: Specify the groups whose members are allowed to connect to the server.
- DenyGroups: Specify the groups whose members are not allowed to connect to the server.
SSH Server Security
SSH server security is paramount for protecting remote access to systems and data. Best practices include:
- Restricting access to authorized users
- Using strong passwords or SSH keys
- Disabling root login
- Enabling two-factor authentication
- Implementing fail2ban to block repeated failed login attempts
SSH Server Logging and Monitoring
Logging and monitoring SSH server activity is crucial for security and troubleshooting purposes. It allows administrators to detect suspicious activities, identify security breaches, and track server usage.
Logging Options
Fedora SSH server offers several logging options, including:
-
- -*Syslog
Logs SSH activity to the system’s syslog facility, providing a central location for logging from various system components.
- -*Syslog
-*Authpriv
Logs SSH authentication attempts, including successful and failed logins, in the /var/log/auth.log file.
-*sshd
Logs SSH server-specific events, such as connection attempts, command executions, and error messages, in the /var/log/secure file.
To configure logging options, edit the /etc/ssh/sshd_config file and adjust the following parameters:
-
- -*SyslogFacility
Specifies the syslog facility to which SSH activity should be logged.
- -*SyslogFacility
-*LogLevel
Sets the verbosity of SSH logging, with options ranging from VERBOSE to QUIET.
Monitoring Tools
Various tools are available for monitoring SSH server activity:
-
- -*Logwatch
A log monitoring tool that parses log files and sends alerts based on predefined rules.
- -*Logwatch
-*Logstalgia
A web-based log analyzer that provides visualizations and insights into log data.
-*SSHGuard
A security tool that monitors SSH login attempts and blocks suspicious activities, such as repeated failed logins from the same IP address.
Techniques for Monitoring
Effective SSH server monitoring involves:
-
- -*Regular log reviews
Regularly checking log files for unusual activities, such as failed login attempts from unknown IP addresses or suspicious command executions.
- -*Regular log reviews
-*Use of monitoring tools
Employing tools like Logwatch or Logstalgia to automate log analysis and receive alerts on suspicious events.
-*Security audit
Periodically conducting security audits to identify potential vulnerabilities and misconfigurations in the SSH server configuration.
By implementing robust logging and monitoring practices, administrators can enhance the security and reliability of their SSH servers, ensuring that unauthorized access and malicious activities are promptly detected and mitigated.
SSH Server Access Control
SSH server access control encompasses the mechanisms used to restrict and regulate access to the server. It involves defining who can connect, under what circumstances, and with what privileges.
Access control in SSH servers is achieved through a combination of user authentication, authorization, and access permissions.
Authentication
Authentication verifies the identity of users attempting to connect to the SSH server. Common authentication methods include:
- Password-based authentication: Requires users to provide a password to access the server.
- Public-key authentication: Uses cryptographic key pairs to verify user identities. A private key is stored on the client, while the corresponding public key is stored on the server.
Authorization
Authorization determines what actions a user is permitted to perform after successful authentication. Authorization can be configured through:
- Group memberships: Assigning users to groups and granting permissions to those groups.
- Access control lists (ACLs): Specifying specific permissions for individual users or groups on specific files or directories.
Access Permissions
Access permissions define the level of access that users have to the server. These permissions include:
- Read: Ability to view and copy files.
- Write: Ability to create, modify, and delete files.
- Execute: Ability to run commands on the server.
SSH Server Key Management

SSH keys play a crucial role in securing SSH connections. They are used for server authentication and encryption, ensuring the integrity and confidentiality of data transmitted over the SSH channel.
To establish SSH key-based authentication, you must generate an SSH key pair on the client machine. This pair consists of a public key and a private key. The public key is shared with the SSH server, while the private key is kept secret on the client machine.
Generating and Managing SSH Keys
To generate an SSH key pair, use the following command on the client machine:
ssh-keygen
- t rsa
- b 4096
This command generates a 4096-bit RSA key pair. You can specify a different key type (-t) or key size (-b) as needed.
The generated keys are stored in the ~/.ssh directory on the client machine. The public key is named id_rsa.pub, while the private key is named id_rsa.
Distributing SSH Keys
To use SSH key-based authentication, you need to distribute your public key to the SSH server. This can be done manually or using an SSH key management tool.
To manually distribute your public key, copy the id_rsa.pub file to the ~/.ssh/authorized_keys file on the SSH server.
Configuring SSH Key-Based Authentication
To configure SSH key-based authentication on the SSH server, add the following lines to the /etc/ssh/sshd_config file:
PasswordAuthentication noChallengeResponseAuthentication noUsePAM noPubkeyAuthentication yes
These settings disable password-based authentication and enable public key authentication.
Restart the SSH server to apply the changes:
systemctl restart sshd
SSH Server Port Forwarding
SSH port forwarding allows you to establish a secure tunnel through an SSH connection, enabling you to access remote services securely over an untrusted network. It provides a secure and encrypted channel for data transmission, ensuring the privacy and integrity of your communications.Port
forwarding is particularly useful when you need to access services running on a private network from a remote location. For example, you can use port forwarding to access your home network’s file server or web server from a public Wi-Fi hotspot.
Local Port Forwarding
Local port forwarding allows you to access a service on a remote server by creating a tunnel from a local port on your client machine to a specific port on the remote server. This is useful when you want to access a service that is not accessible directly from the internet, such as a database or an internal web application.To
configure local port forwarding, use the following syntax:“`ssh
-L local_port
remote_host:remote_port user@remote_server“`For example, to create a tunnel from local port 8080 to port 80 on the remote server example.com, you would use the following command:“`ssh
-L 8080
example.com:80 [email protected]“`
Remote Port Forwarding
Remote port forwarding allows you to access a service on your local machine from a remote server. This is useful when you want to expose a service on your local machine to the internet, such as a web server or an SSH server.To
configure remote port forwarding, use the following syntax:“`ssh
-R remote_port
localhost:local_port user@remote_server“`For example, to create a tunnel from port 80 on the remote server example.com to port 8080 on your local machine, you would use the following command:“`ssh
-R 80
localhost:8080 [email protected]“`
SSH Server Troubleshooting
Troubleshooting SSH server problems involves identifying the root cause and implementing appropriate solutions. This guide provides a structured approach to diagnosing and resolving common SSH server issues.
Common Issues
Common SSH server issues include:
- Connectivity problems: SSH server not responding or unreachable.
- Authentication failures: Invalid credentials or permission issues.
- Configuration errors: Incorrect settings or misconfigurations.
Troubleshooting Guide
- Verify connectivity: Check if the SSH server is running and listening on the correct port using netstat or ss commands.
- Examine logs: Review the SSH server logs (usually /var/log/auth.log or /var/log/secure) for error messages or warnings.
- Check firewall settings: Ensure that the firewall is not blocking incoming SSH connections.
- Validate authentication methods: Verify that the SSH server is configured to use the appropriate authentication methods (e.g., password, public key).
- Review SSH configuration: Check the SSH configuration file (/etc/ssh/sshd_config) for any misconfigurations or missing settings.
- Test with different clients: Try connecting to the SSH server using different SSH clients to rule out client-specific issues.
- Use debug mode: Enable debug mode in the SSH configuration to generate more detailed logs for analysis.
Tips for Debugging
- Use verbose logging (-v option) to display detailed connection and authentication information.
- Enable packet capture (e.g., using tcpdump) to monitor SSH traffic and identify potential network issues.
- Consult online resources and forums for known issues and solutions.
SSH Server Best Practices
To ensure a secure and efficient SSH server, it’s crucial to follow industry best practices. These practices encompass server configuration, management, and optimization techniques.
Adhering to these best practices will enhance the security and reliability of your SSH server, protecting against unauthorized access, data breaches, and service disruptions.
Server Configuration
Configure your SSH server with robust security measures, including: