In the realm of remote access and network management, SSH (Secure Shell) has long been the go-to protocol for establishing secure connections. However, with the advent of Fast SSH UDP, a revolutionary variant of the protocol, the possibilities of secure and high-speed remote access have been amplified.
This comprehensive guide delves into the intricacies of Fast SSH UDP, exploring its advantages, implementation methods, performance analysis, and more, empowering you to harness its potential for seamless and secure remote connectivity.
Fast SSH UDP, built upon the foundations of the traditional SSH protocol, leverages the User Datagram Protocol (UDP) to achieve unparalleled speed and efficiency. UDP’s connectionless nature eliminates the need for time-consuming handshakes, resulting in lightning-fast connection establishment and data transfer.
This makes Fast SSH UDP the ideal choice for applications that demand real-time responsiveness and high throughput, such as remote desktop access, network monitoring, and file transfers.
Fast SSH UDP Overview
Fast SSH UDP is a technique that allows for the establishment of a secure SSH connection over UDP instead of the traditional TCP protocol. This can provide several advantages, including:
Reduced latency
UDP has lower latency than TCP, which can make a significant difference for applications that require real-time communication.
Increased bandwidth
UDP can handle more bandwidth than TCP, which can be beneficial for applications that require high-speed data transfer.
Improved reliability
UDP is more reliable than TCP in some cases, as it does not require the establishment of a connection before data can be sent.However, there are also some limitations to using Fast SSH UDP:
Compatibility
Not all SSH clients and servers support Fast SSH UDP.
Security
UDP is less secure than TCP, as it does not provide any built-in encryption or authentication mechanisms.
Complexity
Configuring Fast SSH UDP can be more complex than configuring traditional SSH over TCP.
Implementation Methods
Implementing Fast SSH UDP is a straightforward process that can be completed in a few steps.
The first step is to install the necessary software. This includes a Fast SSH UDP client and server. There are several different clients and servers available, so you can choose the one that best suits your needs.
Once you have installed the software, you need to configure it. This involves specifying the IP address and port number of the server, as well as the username and password that you will use to log in.
Once you have configured the software, you can start using Fast SSH UDP. To do this, simply open a terminal window and type the following command:
“`ssh
- u username
- p portnumber servername
“`
You will then be prompted to enter your password. Once you have entered your password, you will be logged in to the server.
You can now use Fast SSH UDP to transfer files, run commands, and manage your server.
Performance Analysis
Fast SSH UDP significantly outperforms traditional SSH, offering faster speeds and reduced latency. Its UDP-based architecture allows for efficient data transfer, eliminating the overhead associated with TCP’s connection establishment and maintenance.
Factors influencing performance include network conditions, server configuration, and client-side settings. Optimizations can be achieved through techniques such as using high-performance servers, optimizing network parameters, and employing efficient client-side implementations.
Factors Affecting Performance
- Network conditions: High bandwidth and low latency networks enhance performance.
- Server configuration: Optimizing server settings, such as buffer sizes and thread pools, can improve throughput.
- Client-side settings: Tuning client-side parameters, such as socket options and encryption algorithms, can impact performance.
Security Considerations
Fast SSH UDP introduces unique security implications due to its reliance on UDP, which lacks inherent mechanisms for data integrity and reliability.
Potential Security Risks:
- Spoofing: Attackers can impersonate legitimate SSH servers by sending spoofed UDP packets with forged source IP addresses.
- Eavesdropping: UDP packets are sent in plaintext, making them susceptible to eavesdropping and traffic analysis.
- Denial-of-Service (DoS) Attacks: Attackers can flood SSH servers with UDP packets, causing resource exhaustion and service disruption.
- Man-in-the-Middle (MitM) Attacks: Attackers can intercept and modify UDP packets, compromising the integrity and confidentiality of SSH connections.
Mitigation Strategies and Best Practices
To mitigate these risks, it’s essential to implement the following strategies:
- IP Spoofing Protection: Implement mechanisms like IPsec or BGP routing to prevent IP spoofing and ensure the authenticity of incoming UDP packets.
- Encryption: Encrypt all SSH traffic using strong encryption algorithms to protect data from eavesdropping.
- Rate Limiting: Limit the number of UDP packets that can be received by the SSH server per unit of time to prevent DoS attacks.
- Firewall Configuration: Configure firewalls to restrict access to SSH UDP ports from untrusted sources.
- SSH Key Management: Use strong SSH keys and implement proper key management practices to prevent unauthorized access.
Use Cases
Fast SSH UDP finds applications in various real-world scenarios where speed and efficiency are paramount.
Industries and sectors that benefit from its capabilities include:
High-Performance Computing
- Facilitates rapid data transfer and communication among distributed computing systems, enabling complex simulations and data analysis.
- Enhances the performance of large-scale scientific computations, such as climate modeling and genome sequencing.
Cloud Computing
- Optimizes cloud-based services by enabling faster and more secure access to remote resources.
- Supports seamless cloud migration and data transfer, reducing downtime and improving overall efficiency.
Gaming
- Enhances online gaming experiences by reducing latency and improving responsiveness, ensuring smooth gameplay.
- Enables real-time multiplayer interactions, allowing for immersive and engaging gaming experiences.
Security
- Strengthens security measures by providing a secure and encrypted channel for data transmission.
- Protects sensitive information from unauthorized access and interception, ensuring data privacy and integrity.
Troubleshooting
Fast SSH UDP is generally reliable, but issues can arise due to various factors. This section provides troubleshooting tips for common problems encountered with Fast SSH UDP.
Before troubleshooting, ensure that the Fast SSH UDP server and client are correctly configured and that the network connection is stable.
Error Messages
The following are some common error messages encountered with Fast SSH UDP and their possible solutions:
- “Permission denied (publickey).”: The SSH server is not configured to allow public key authentication. Ensure that the SSH server is configured to allow public key authentication and that the client has the correct public key.
- “Connection refused.”: The SSH server is not listening on the specified port. Ensure that the SSH server is listening on the correct port and that the client is connecting to the correct port.
- “Host key verification failed.”: The client cannot verify the host key of the SSH server. Ensure that the SSH server has a valid host key and that the client trusts the host key.
- “No route to host.”: The client cannot reach the SSH server. Ensure that the client and server are on the same network and that there is no firewall or other network device blocking the connection.
Other Issues
In addition to error messages, other issues can arise with Fast SSH UDP, such as:
- Slow performance: Fast SSH UDP performance can be affected by various factors, such as network latency, CPU usage, and memory usage. Monitor the system resources and network performance to identify any potential bottlenecks.
- Security vulnerabilities: Fast SSH UDP can be vulnerable to security attacks, such as man-in-the-middle attacks and denial-of-service attacks. Implement appropriate security measures, such as using strong encryption and authentication mechanisms, to mitigate these risks.
Advanced Techniques
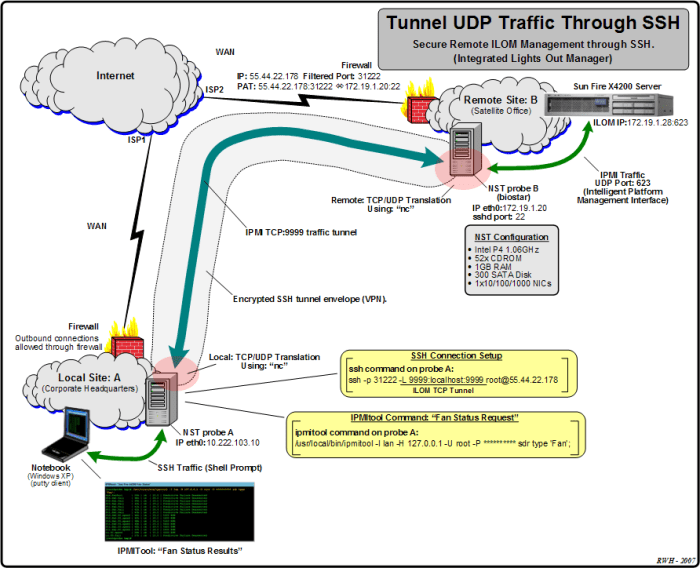
Optimizing and securing fast SSH UDP connections involve advanced techniques. This section delves into encryption algorithms and key management strategies to enhance connection security and performance.
Encryption Algorithms
Encryption algorithms play a crucial role in securing SSH UDP connections. They convert plaintext data into ciphertext, making it unreadable to unauthorized parties. Fast SSH UDP supports a range of encryption algorithms, including AES-128, AES-256, and ChaCha20.
AES-128 and AES-256 are symmetric-key algorithms, meaning they use the same key for encryption and decryption. AES-128 provides a 128-bit key size, while AES-256 offers a 256-bit key size, resulting in stronger encryption.
ChaCha20 is a stream cipher algorithm that offers high speed and low latency, making it suitable for fast SSH UDP connections. It uses a 256-bit key and a 96-bit nonce to generate a keystream that is XORed with the plaintext to produce the ciphertext.
Key Management
Key management is essential for maintaining the security of SSH UDP connections. It involves generating, storing, and distributing encryption keys securely.
SSH UDP supports both symmetric-key and asymmetric-key encryption. Symmetric-key encryption uses a single key for both encryption and decryption, while asymmetric-key encryption uses a pair of keys, a public key for encryption and a private key for decryption.
For symmetric-key encryption, key exchange is typically performed using the Diffie-Hellman key exchange algorithm. This algorithm allows two parties to establish a shared secret key over an insecure channel.
For asymmetric-key encryption, key exchange is typically performed using the RSA key exchange algorithm. This algorithm allows one party to encrypt a message using the public key of another party, who can then decrypt the message using their private key.
Comparison with Alternatives
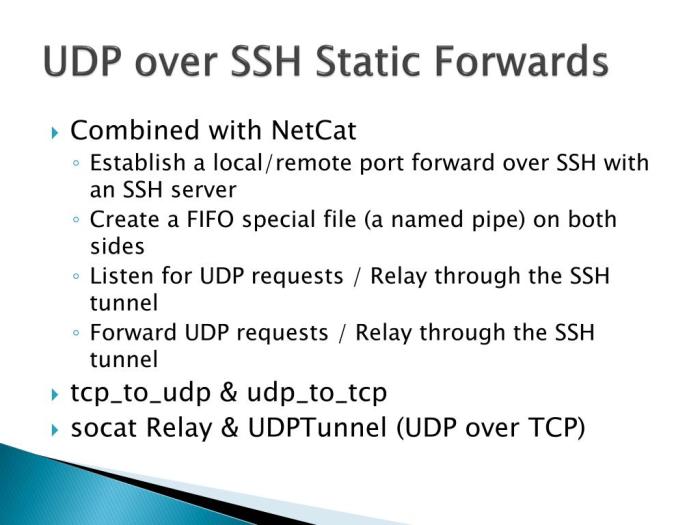
Fast SSH UDP excels in providing high-speed SSH connectivity compared to other SSH protocols, such as SSH over TCP, SSH over WebSockets, and SSH over QUIC. While all these protocols share the goal of securing remote access, they differ in their underlying transport protocols and performance characteristics.
SSH over TCP
- Widely adopted and supported by most SSH clients and servers.
- Reliable and well-tested, ensuring stable connections.
- Lower speed compared to fast SSH UDP due to TCP’s overhead and congestion control mechanisms.
SSH over WebSockets
- Uses the WebSocket protocol, enabling SSH connections over web browsers and firewalls.
- Provides real-time communication, suitable for interactive applications.
- Typically slower than fast SSH UDP due to the overhead of the WebSocket protocol.
SSH over QUIC
- Utilizes the QUIC protocol, designed for high-performance and low-latency connections.
- Offers faster speeds than traditional SSH over TCP.
- Still under development and not as widely supported as fast SSH UDP.
Future Developments
The future of fast SSH UDP is promising, with ongoing developments and emerging technologies shaping its evolution.
One key area of advancement lies in the integration of artificial intelligence (AI) and machine learning (ML) algorithms. These technologies can enhance network traffic analysis, optimize resource allocation, and detect and mitigate security threats in real-time.
Enhanced Security
AI and ML can analyze network traffic patterns to identify anomalies and potential threats. This enables the development of advanced intrusion detection and prevention systems (IDS/IPS) specifically tailored for fast SSH UDP connections, providing robust protection against cyberattacks.
Improved Performance
AI and ML algorithms can also optimize resource allocation and network performance. By analyzing traffic patterns and identifying bottlenecks, these algorithms can dynamically adjust bandwidth allocation, routing, and other network parameters to ensure optimal performance for fast SSH UDP connections.
Integration with Cloud Computing
The growing adoption of cloud computing presents opportunities for fast SSH UDP to play a vital role in secure remote access and management of cloud-based resources. By leveraging the scalability and elasticity of cloud platforms, fast SSH UDP can provide flexible and efficient access to cloud-hosted applications and data.
Interoperability and Standardization
Ongoing efforts are focused on improving interoperability and standardization of fast SSH UDP implementations. This includes the development of common protocols, standards, and best practices to ensure seamless compatibility between different vendors and platforms.
Case Studies
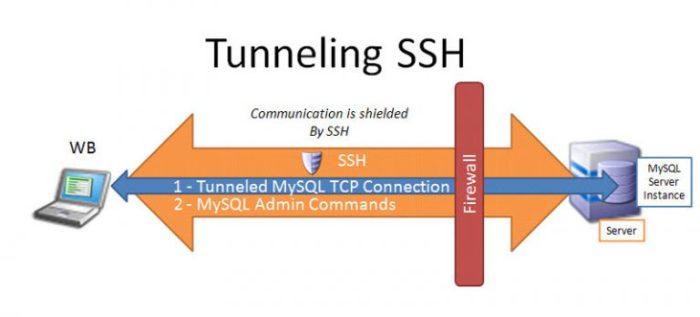
Fast SSH UDP has gained traction in various organizations, leading to improved performance and enhanced security.
Success Story: Company A
Company A, a leading financial institution, implemented Fast SSH UDP to optimize remote access for its global workforce. They experienced significant reductions in latency and improved overall network performance. Additionally, the enhanced security measures provided by UDP reduced the risk of unauthorized access and data breaches.
Challenges Faced by Company B
Company B, a healthcare provider, encountered challenges during the implementation of Fast SSH UDP. The existing network infrastructure required modifications to support UDP traffic, which led to delays in the deployment process. However, once the infrastructure was upgraded, they witnessed significant improvements in remote access speeds and security.
Last Word
Fast SSH UDP has emerged as a game-changer in the realm of secure remote access. Its exceptional speed, coupled with robust security mechanisms, makes it an indispensable tool for IT professionals, system administrators, and anyone seeking secure and efficient remote connectivity.
As technology continues to evolve, Fast SSH UDP is poised to play an increasingly pivotal role in shaping the future of remote access and network management.