Secure Shell (SSH) is a versatile protocol that enables secure communication over unsecured networks. Its primary role is to establish encrypted connections between two remote hosts, facilitating secure data transfer, remote command execution, and secure remote login. One crucial aspect of SSH is its reliance on transport protocols, which play a vital role in ensuring the secure transmission of data.
In this guide, we will delve into the intricacies of SSH, exploring the transport protocols it utilizes, comparing TCP and UDP, and examining the implications for SSH’s functionality and security.
SSH operates at the transport layer of the TCP/IP model, utilizing both TCP and UDP protocols to establish and maintain secure connections. Understanding the characteristics and distinctions between TCP and UDP is essential for grasping the behavior and capabilities of SSH.
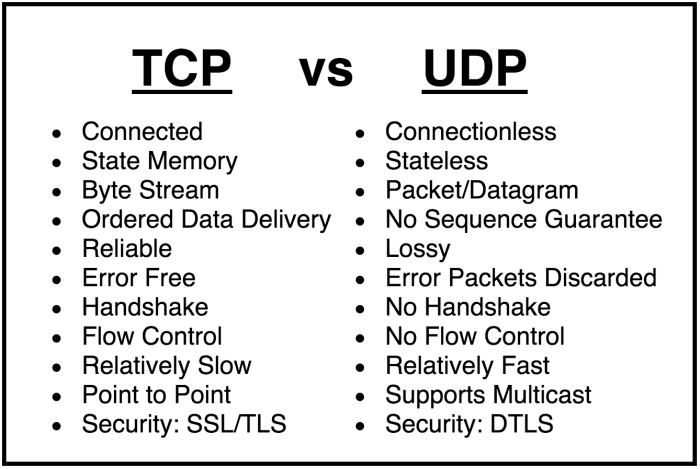
TCP, a connection-oriented protocol, provides reliable, in-order data delivery with error correction and flow control mechanisms. UDP, on the other hand, is a connectionless protocol, offering faster, more lightweight data transmission but sacrificing reliability and error handling.
SSH Protocol Overview
SSH (Secure Shell) is a network protocol that provides secure remote access and command execution over an insecure network. It allows users to securely log in to remote machines, execute commands, and transfer files over an encrypted connection. SSH is widely used for system administration, remote management, and secure file transfer.The
SSH protocol has evolved over time, with different versions introducing new features and security enhancements. The most common versions of SSH are:
SSH Versions
- SSH-1: The original version of SSH, released in 1995. It has been deprecated due to security vulnerabilities.
- SSH-2: The current version of SSH, released in 2006. It addresses the security issues of SSH-1 and provides stronger encryption algorithms.
- SSH-3: A newer version of SSH, still under development. It aims to improve performance and security further.
TCP vs. UDP in Network Protocols
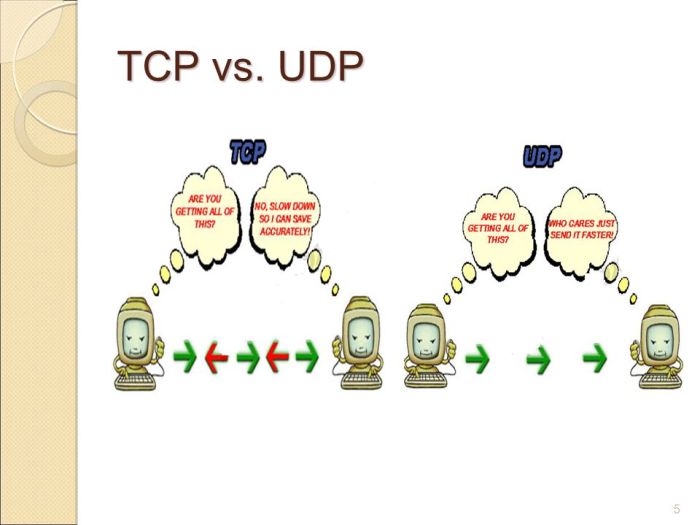
TCP and UDP are two fundamental protocols in the Transmission Control Protocol/Internet Protocol (TCP/IP) suite, each with distinct characteristics and use cases.TCP (Transmission Control Protocol) is a connection-oriented protocol that establishes a virtual circuit between two endpoints before data transmission.
It ensures reliable delivery of data, with error correction and flow control mechanisms. TCP is commonly used for applications that require high reliability, such as web browsing, email, and file transfers.UDP (User Datagram Protocol), on the other hand, is a connectionless protocol that sends data without establishing a prior connection.
It is a faster and simpler protocol than TCP, but it does not provide error correction or flow control. UDP is often used for applications that require real-time performance, such as online gaming, video streaming, and voice over IP (VoIP).
Advantages and Disadvantages of TCP and UDP
TCP*
-*Advantages
Reliable data delivery
Error correction and flow control
Congestion control
*
-*Disadvantages
Higher overhead due to connection establishment and maintenance
Slower performance compared to UDP
UDP*
-*Advantages
Fast and efficient
Low overhead
Real-time performance
*
-*Disadvantages
No error correction or flow control
Can lead to data loss or corruption
The choice between TCP and UDP depends on the specific requirements of the application. For applications that require high reliability and data integrity, TCP is the preferred choice. For applications that prioritize speed and real-time performance, UDP is more suitable.
SSH Transport Layer
The transport layer is a crucial component of the SSH protocol, responsible for establishing and maintaining a secure connection between the client and the server. It provides a reliable and ordered channel for exchanging data and ensures the integrity and confidentiality of the transmitted information.
SSH primarily utilizes two transport protocols:
TCP (Transmission Control Protocol)
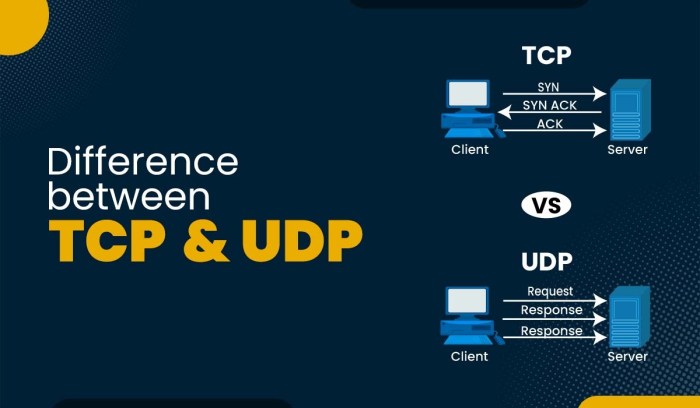
TCP is a connection-oriented protocol that establishes a reliable, ordered, and error-checked connection between the two endpoints. It ensures that data packets are delivered in the correct order, without errors, and without loss. TCP is the preferred transport protocol for SSH, as it provides a stable and secure foundation for the higher-level SSH protocols.
UDP (User Datagram Protocol)
UDP is a connectionless protocol that sends data packets without establishing a connection. It is faster than TCP but less reliable, as it does not guarantee the delivery or ordering of packets. SSH can use UDP for specific applications where speed is critical and reliability is less important, such as for port forwarding.
SSH Encryption
SSH relies on robust encryption mechanisms to protect the integrity and confidentiality of transmitted data. These mechanisms safeguard sensitive information, such as passwords and commands, from unauthorized access and interception.
SSH supports a wide range of encryption algorithms, providing flexibility in choosing the appropriate level of security for specific use cases. The most commonly used algorithms include:
Symmetric Encryption
- AES-256: A highly secure and widely adopted symmetric encryption algorithm, known for its speed and reliability.
- 3DES: A triple DES algorithm that offers enhanced security by applying DES encryption three times to the same data.
- Blowfish: A fast and efficient symmetric encryption algorithm that is suitable for high-performance applications.
Asymmetric Encryption
- RSA: A widely used asymmetric encryption algorithm that is employed for key exchange and digital signatures.
- DSA: A digital signature algorithm that is commonly used for authentication purposes.
SSH Authentication
SSH supports various authentication methods to verify the identity of the user attempting to establish a secure connection. Each method offers varying levels of security and ease of use.
Password Authentication
The simplest authentication method is password authentication, where the user enters a password to prove their identity. While convenient, it is also the least secure method as passwords can be easily compromised through brute force attacks or phishing scams.
Public Key Authentication
Public key authentication is a more secure method that utilizes a pair of cryptographic keys: a public key and a private key. The public key is shared with the server, while the private key is kept secret by the user.
When a user attempts to connect, the server sends a challenge that can only be decrypted using the private key. This method is more secure than password authentication as it does not require the user to transmit their password over the network.
Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring users to provide two different authentication factors. This can include a password and a one-time code generated by a mobile device or a hardware token. 2FA significantly reduces the risk of unauthorized access, even if one factor is compromised.
Kerberos Authentication
Kerberos is a network authentication protocol that allows users to access network services without having to enter their passwords multiple times. In SSH, Kerberos authentication can be used to simplify the login process and improve security by leveraging a trusted third-party authentication server.
Security Considerations
When selecting an authentication method, it is important to consider the security implications of each method and the level of protection required for the specific use case. Password authentication is suitable for low-risk scenarios, while public key authentication and 2FA are recommended for more sensitive applications.
SSH Tunneling
SSH tunneling is a technique that allows you to establish a secure connection between two remote hosts over an untrusted network.
This is achieved by creating an encrypted tunnel over the SSH connection, through which data can be securely transmitted.
Types of SSH Tunneling
SSH supports different types of tunneling, including:
- Local Port Forwarding: Allows you to forward a local port on your client machine to a remote port on the server.
- Remote Port Forwarding: Allows you to forward a remote port on the server to a local port on your client machine.
- Dynamic Port Forwarding: Allows you to dynamically forward ports on the client machine to random ports on the server.
SSH Port Forwarding
SSH port forwarding is a technique that allows you to securely access a service running on a remote server through an SSH connection. It creates a secure tunnel between your local computer and the remote server, allowing you to redirect network traffic from your local machine to the remote server.
There are two main types of port forwarding supported by SSH:
Local Port Forwarding
Local port forwarding allows you to access a service running on a remote server as if it were running on your local machine. This is useful when you want to access a service that is not publicly accessible or is behind a firewall.
Remote Port Forwarding
Remote port forwarding allows you to access a service running on your local machine from a remote server. This is useful when you want to expose a service running on your local machine to the internet without having to open up a firewall port.
SSH Configuration
SSH offers a range of configuration options to tailor its behavior to specific needs. Understanding and customizing these settings is crucial for securing and optimizing SSH connections.
Best practices for securing SSH configurations include using strong encryption algorithms, disabling insecure protocols, setting up proper user authentication mechanisms, and implementing security measures like fail2ban to prevent brute-force attacks.
Configuration Options
- Port Number: Change the default SSH port (22) to reduce the risk of automated attacks.
- Encryption Algorithms: Specify preferred encryption algorithms for data and key exchange, such as AES-256-CBC and ECDH-SHA2-NISTP384.
- Authentication Methods: Configure SSH to support strong authentication methods like public-key authentication and two-factor authentication.
- Protocol Versions: Disable insecure SSH protocol versions like SSHv1 and enable SSHv2 for improved security.
- Logging and Auditing: Enable SSH logging to monitor connection attempts and detect suspicious activities.
Securing SSH Configurations
- Use Strong Encryption: Implement robust encryption algorithms like AES-256-CBC and ECDH-SHA2-NISTP384 to protect data in transit.
- Disable Insecure Protocols: SSHv1 is vulnerable to attacks; disable it and use SSHv2 or later for secure connections.
- Configure Strong Authentication: Require public-key authentication and two-factor authentication to prevent unauthorized access.
- Limit Login Attempts: Use tools like fail2ban to limit login attempts and block IP addresses after a certain number of failed attempts.
- Monitor Logs: Regularly review SSH logs to identify suspicious activities, such as failed login attempts or unusual traffic patterns.
SSH Vulnerabilities
SSH, like any software, is not immune to vulnerabilities. Several common vulnerabilities have been identified over the years, including:
- Buffer overflow vulnerabilities: These vulnerabilities allow attackers to execute arbitrary code on the SSH server by sending specially crafted packets that cause the server to allocate more memory than it should.
- Authentication bypass vulnerabilities: These vulnerabilities allow attackers to bypass the SSH authentication process and gain access to the server without providing valid credentials.
- Man-in-the-middle attacks: These attacks allow attackers to intercept and modify SSH traffic, allowing them to eavesdrop on communications or impersonate the server or client.
To mitigate these vulnerabilities, it is important to keep SSH software up to date, use strong passwords or SSH keys, and implement additional security measures such as two-factor authentication or intrusion detection systems.
Mitigation Strategies
Several strategies can be employed to mitigate the risks associated with SSH vulnerabilities:
- Use strong passwords or SSH keys: Using strong passwords or SSH keys makes it more difficult for attackers to guess or brute-force their way into the server.
- Implement two-factor authentication: Two-factor authentication requires users to provide two forms of authentication, such as a password and a one-time code sent to their phone, making it more difficult for attackers to gain access to the server even if they have the user’s password.
- Use intrusion detection systems: Intrusion detection systems can help to detect and block unauthorized access attempts to the SSH server.
- Keep SSH software up to date: Software vendors regularly release updates to address security vulnerabilities. It is important to keep SSH software up to date to protect against the latest threats.
By implementing these mitigation strategies, organizations can significantly reduce the risk of SSH vulnerabilities being exploited by attackers.
SSH Tools and Utilities
SSH provides a versatile suite of tools and utilities to facilitate secure remote access and management tasks. These tools offer a range of functionalities, from basic connectivity testing to advanced network management and troubleshooting.
The most commonly used SSH tools include:
SSH Tool: ssh
- Establishes an encrypted SSH connection to a remote server.
- Allows for secure remote command execution, file transfer, and port forwarding.
SSH Tool: scp
- Securely copies files between local and remote hosts.
- Utilizes SSH encryption to protect data during file transfer.
SSH Tool: sftp
- Provides an interactive file transfer interface over an SSH connection.
- Supports file browsing, editing, and management on remote servers.
SSH Tool: ssh-keygen
- Generates SSH key pairs for authentication.
- Creates public and private keys to enhance security and simplify login.
SSH Tool: ssh-copy-id
- Copies the public SSH key to a remote server.
- Allows for passwordless authentication to the server.
SSH Tool: ssh-agent
- Manages SSH keys and provides secure authentication.
- Stores keys in memory and automatically unlocks them when needed.
Last Recap
SSH’s versatility and robust security features make it a cornerstone of secure remote access and data transfer. Its ability to leverage both TCP and UDP protocols ensures that it can adapt to diverse network environments and application requirements. By comprehending the nuances of SSH’s transport layer, we gain a deeper appreciation for its design and the critical role it plays in safeguarding our communications in today’s digital landscape.