SSH.SSHSlowdns.com – In the realm of secure network communication, SSH (Secure Shell) reigns supreme, enabling remote access and data transfer with robust encryption. While traditionally operating over TCP, SSH can also leverage UDP (User Datagram Protocol) for enhanced performance and flexibility. This guide delves into the intricacies of creating SSH UDP custom configurations, empowering you to optimize your network security and efficiency.
SSH over UDP offers distinct advantages over its TCP counterpart, including lower latency, higher throughput, and reduced overhead. However, customizing SSH UDP configurations requires careful consideration of various parameters and potential security implications. This guide will equip you with the knowledge and techniques to create and manage SSH UDP custom configurations that meet your specific network requirements.
Understanding SSH UDP Custom
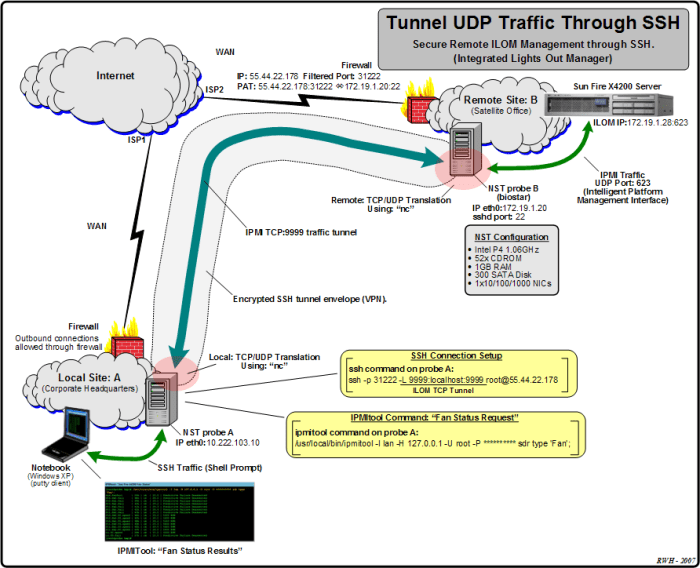
SSH (Secure Shell) is a versatile network protocol that allows for secure remote access to a computer system. Traditionally, SSH operates over TCP (Transmission Control Protocol), which ensures reliable and ordered data delivery. However, SSH can also be configured to use UDP (User Datagram Protocol), offering distinct advantages and use cases.
SSH over UDP differs from SSH over TCP in several key aspects. UDP is a connectionless protocol, meaning it does not establish a persistent connection between the client and server. Instead, each data packet is transmitted independently, without the need for acknowledgment or retransmission.
This results in lower overhead and faster response times, making SSH over UDP ideal for applications that require real-time or low-latency communication.
Key Benefits of SSH over UDP
- Faster response times: UDP’s connectionless nature eliminates the need for connection establishment and acknowledgment, reducing latency.
- Lower overhead: UDP packets are smaller than TCP packets, as they do not include headers for connection management.
- Improved performance for real-time applications: UDP’s fast and low-latency nature makes it suitable for applications such as video conferencing, remote desktop, and online gaming.
Potential Use Cases for SSH over UDP
SSH over UDP is particularly beneficial in scenarios where low latency and fast response times are critical, such as:
- Interactive remote desktop sessions
- Real-time data monitoring and control
- Streaming multimedia content
- Online gaming
Creating an SSH UDP Custom Configuration
Creating an SSH UDP custom configuration involves specifying the desired behavior and parameters for SSH UDP connections. By customizing the configuration, you can tailor the SSH UDP functionality to meet specific requirements and optimize performance.
To create an SSH UDP custom configuration, follow these steps:
- Open the SSH configuration file, typically located at /etc/ssh/sshd_config.
- Add or modify the following parameters as needed:
- Port: Specifies the UDP port to listen on. The default is 22.
- AddressFamily: Specifies the address family to use. The default is “inet” (IPv4) or “inet6” (IPv6).
- ListenAddress: Specifies the IP address to listen on. The default is “0.0.0.0” (IPv4) or “::” (IPv6), which listens on all available addresses.
- UDPForward: Specifies whether to allow UDP port forwarding. The default is “no”.
- PermitTunnel: Specifies whether to allow TCP port forwarding over UDP. The default is “no”.
- Save the changes and restart the SSH service.
The impact of different configuration options on SSH performance can be significant. For example, choosing an appropriate port number can avoid conflicts with other services running on the same system. Specifying a specific IP address for ListenAddress can improve security by restricting SSH access to only authorized networks.
Enabling UDPForward and PermitTunnel can enhance connectivity options but may also introduce security risks, so it’s crucial to consider the specific requirements and security implications before making these changes.
Testing and Troubleshooting SSH UDP Custom Configuration
Testing SSH UDP custom configurations involves establishing a connection between a client and server using the configured parameters. Use the ssh command with theu option to specify the UDP protocol. If the connection is successful, verify the functionality of the configuration by transferring files or executing commands.
Troubleshooting Tips
* Ensure that both client and server have the SSH UDP custom configuration applied.
- Verify that the UDP port specified in the configuration is open on both systems.
- Check for firewall rules that may be blocking UDP traffic.
- Examine the SSH log files on both systems for any error messages or warnings.
- Consider using a network analyzer to capture and analyze UDP traffic for troubleshooting purposes.
Best Practices for Monitoring and Maintaining
* Regularly review SSH UDP custom configurations to ensure they remain up-to-date and secure.
- Implement monitoring tools to track SSH UDP traffic and identify any anomalies.
- Perform periodic security audits to assess the overall health of the SSH UDP configuration and identify potential vulnerabilities.
- Consider using automated tools for configuration management and backup to ensure consistency and recoverability.
Performance Considerations for SSH UDP Custom
SSH UDP Custom can have performance implications compared to traditional SSH over TCP.
Latency
SSH UDP Custom generally has lower latency than SSH over TCP, as UDP does not require handshakes or acknowledgments. This can be beneficial for applications that require real-time communication, such as remote desktop or audio/video streaming.
Throughput
SSH UDP Custom can have higher throughput than SSH over TCP, especially in high-bandwidth environments. UDP does not have the same overhead as TCP, which can result in faster data transfer rates.
Reliability
SSH UDP Custom is less reliable than SSH over TCP, as UDP does not guarantee delivery of packets. This can be a concern for applications that require reliable data transfer, such as file transfers or remote system administration.
Factors Affecting SSH UDP Performance
Several factors can affect the performance of SSH UDP Custom, including:
Network conditions
The performance of SSH UDP Custom can be affected by network latency, packet loss, and congestion.
Application requirements
The performance requirements of the application using SSH UDP Custom will impact its performance.
Server configuration
The configuration of the SSH server can affect the performance of SSH UDP Custom.
Security Implications of SSH UDP Custom
SSH UDP Custom offers performance benefits, but it’s essential to consider its potential security risks. Using UDP eliminates TCP’s built-in mechanisms, increasing the risk of data loss, spoofing, and denial-of-service (DoS) attacks.
Mitigation Strategies
To mitigate these risks, implement the following measures:
Strong encryption
Use strong encryption algorithms like AES-256 to protect data in transit.
Firewall rules
Implement strict firewall rules to limit access to the SSH UDP Custom port and block unauthorized connections.
Intrusion detection systems (IDS)
Deploy IDS to detect and block malicious traffic targeting the SSH UDP Custom service.
Regular security audits
Conduct regular security audits to identify and address any vulnerabilities.
Use Cases for SSH UDP Custom
SSH over UDP custom configurations offer unique advantages in specific scenarios where performance and resource utilization are critical. Let’s explore some real-world examples:
Industrial Automation and Control Systems
In industrial settings, SSH over UDP custom configurations can facilitate secure remote access and control of equipment. The low latency and bandwidth efficiency of UDP enable real-time monitoring and control, even in environments with limited network resources.
Remote Desktop Access
For remote desktop access, SSH over UDP custom configurations provide a lightweight and responsive connection. The reduced overhead and faster response times make it ideal for applications that require high interactivity, such as graphical user interfaces or video conferencing.
Network Monitoring and Management
Network administrators can leverage SSH over UDP custom configurations for efficient and scalable network monitoring. The low overhead allows for frequent data collection and real-time monitoring, even across large networks with limited bandwidth.
Advantages of Using SSH over UDP in these Scenarios
* Low latency: UDP’s connectionless nature minimizes latency, enabling faster response times.
Bandwidth efficiency
UDP’s smaller packet size and reduced overhead conserve bandwidth.
Scalability
The lightweight nature of UDP allows for efficient handling of multiple connections.
Limitations of Using SSH over UDP in these Scenarios
* Reliability: UDP is a connectionless protocol, so it does not guarantee delivery or order of packets.
Security
UDP’s lack of inherent encryption may require additional security measures.
Industries and Applications that Benefit from SSH over UDP Custom
Industries that prioritize real-time communication, remote access, and network efficiency may benefit from SSH over UDP custom configurations. These include:* Manufacturing and industrial automation
- IT and network management
- Remote desktop and application access
- Healthcare and medical devices
- Transportation and logistics
Advanced SSH UDP Custom Techniques
Optimizing SSH UDP Custom Configurations
To enhance the performance and efficiency of SSH UDP custom configurations, consider the following techniques:
- Fine-tuning UDP buffer sizes: Experiment with different buffer sizes to find the optimal balance between performance and resource utilization.
- Using custom SSH clients and servers: Leverage specialized SSH clients and servers designed for UDP connections to maximize performance and reliability.
- Employing multiple UDP ports: Utilize multiple UDP ports to distribute traffic and improve overall throughput.
Specific Applications and Protocols
SSH UDP custom can be tailored to support specific applications or protocols:
- Secure tunneling for VoIP: Establish secure tunnels for VoIP traffic, ensuring privacy and protection against eavesdropping.
- Remote access to graphical applications: Enable remote access to graphical applications using X11 forwarding over SSH UDP custom.
- Custom data transfer protocols: Develop and deploy custom data transfer protocols that leverage SSH UDP custom for secure and efficient data exchange.
SSH UDP Custom in Cloud and Virtualization Environments
SSH UDP Custom in cloud and virtualization environments provides benefits like improved performance, reduced latency, and efficient resource utilization. However, it also presents challenges such as security concerns and configuration complexities.
Considerations for Using SSH UDP Custom
*
-*Security Implications
UDP is a connectionless protocol, making it more susceptible to eavesdropping and spoofing attacks.
-
- -*Configuration Complexity
Configuring SSH UDP Custom requires additional steps compared to TCP-based SSH, potentially leading to misconfigurations.
- -*Configuration Complexity
-*Resource Utilization
UDP connections can consume less bandwidth and system resources compared to TCP connections.
Challenges and Benefits
Challenges:*
-*Security Risks
UDP’s lack of connection tracking can increase the risk of unauthorized access.
-*Configuration Management
Maintaining consistent SSH UDP Custom configurations across multiple cloud instances can be complex.
Benefits:*
-*Improved Performance
UDP’s low overhead and connectionless nature can enhance SSH performance, especially in high-latency environments.
-
- -*Reduced Latency
UDP’s connectionless nature eliminates the need for handshaking, reducing latency.
- -*Reduced Latency
-*Resource Efficiency
UDP connections consume less bandwidth and system resources, making them suitable for resource-constrained environments.
Best Practices for Cloud Management
*
-*Centralized Configuration Management
Use a centralized tool or platform to manage SSH UDP Custom configurations across multiple cloud instances.
-
- -*Security Hardening
Implement strong security measures such as firewalls, intrusion detection systems, and regular security audits.
- -*Security Hardening
-*Monitoring and Logging
Establish robust monitoring and logging mechanisms to detect and respond to potential security incidents.
SSH UDP Custom and Automation
Automating the creation and management of SSH UDP custom configurations enhances efficiency and reduces human error.
Automation tools streamline the process, ensuring consistent and accurate configurations across multiple systems.
Benefits of Automation
-
- -*Reduced Configuration Time
Automating configuration tasks eliminates manual effort, saving time and resources.
- -*Reduced Configuration Time
-*Improved Consistency
Automation ensures that configurations are applied uniformly across systems, minimizing errors and maintaining consistency.
-*Centralized Management
Automation tools provide a central platform to manage SSH UDP custom configurations, simplifying administration and monitoring.
Automation Tools and Scripts
Several automation tools and scripts can be utilized for SSH UDP custom configuration management:
-
- -*Ansible
A popular configuration management tool that allows for automated deployment and management of SSH UDP custom configurations.
- -*Ansible
-*Puppet
Another configuration management tool that provides declarative language for defining and enforcing SSH UDP custom configurations.
-*Custom Scripts
System administrators can develop their own scripts using languages like Python or Bash to automate SSH UDP custom configuration tasks.
Future Trends in SSH UDP Custom
SSH UDP custom technology continues to evolve, driven by advancements in networking and security.
Several emerging trends and advancements are shaping the future of SSH over UDP:
-
- -*Increased Adoption of Cloud and Virtualization
The growing adoption of cloud and virtualization environments is driving the demand for SSH UDP custom solutions that can provide secure and efficient remote access to virtual machines and cloud resources.
- -*Increased Adoption of Cloud and Virtualization
-*Integration with Software-Defined Networking (SDN)
SSH UDP custom is increasingly being integrated with SDN technologies, enabling dynamic and automated management of network resources. This integration allows for more flexible and efficient deployment and management of SSH UDP custom configurations.
-*Enhanced Security Features
Future developments in SSH UDP custom are expected to focus on enhancing security features, such as support for stronger encryption algorithms, multi-factor authentication, and intrusion detection and prevention mechanisms.
-*Improved Performance and Scalability
Ongoing advancements in hardware and software technologies are expected to lead to improvements in the performance and scalability of SSH UDP custom solutions. This will enable support for larger and more complex deployments.
-*New Use Cases and Applications
SSH over UDP is expected to find new use cases and applications in areas such as IoT, edge computing, and secure remote access to industrial control systems.