In the realm of secure and efficient VPN solutions, WireGuard emerges as a cutting-edge technology. With its lightning-fast speeds, streamlined configuration, and robust security features, WireGuard has gained immense popularity among network engineers and security professionals alike. This comprehensive guide will delve into the intricacies of WireGuard configuration, providing a step-by-step approach to harness its full potential and establish secure VPN connections.
Through a detailed exploration of WireGuard’s configuration file structure, interface and peer settings, firewall configurations, and advanced options, this guide will empower you to customize and optimize WireGuard for a wide range of use cases. Whether you seek remote access, site-to-site VPNs, or secure cloud connectivity, this guide will equip you with the knowledge and skills to configure WireGuard seamlessly.
WireGuard Configuration File Overview
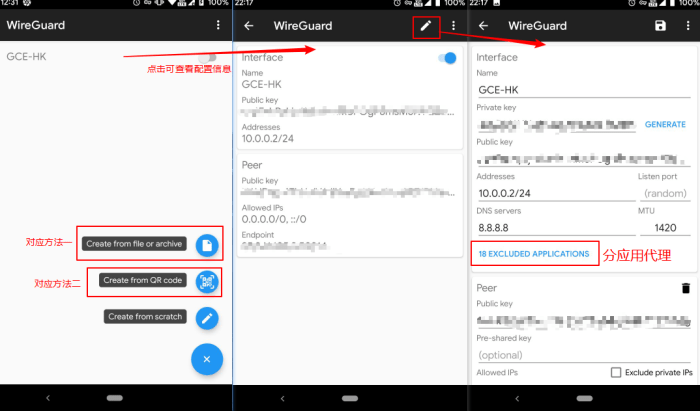
A WireGuard configuration file defines the settings and parameters for a WireGuard interface. It is typically stored in the /etc/wireguard/wg0.conf file on Linux systems.
The configuration file is structured into sections, each with a specific purpose. The main sections include:
- [Interface]: Defines the settings for the WireGuard interface, such as the IP address, subnet mask, and listen port.
- [Peer]: Defines the settings for a remote peer, including its public key, IP address, and allowed IP addresses.
- [ListenPort]: Specifies the port on which the WireGuard interface will listen for incoming connections.
- [PrivateKey]: Specifies the private key for the WireGuard interface.
- [Address]: Specifies the IP address assigned to the WireGuard interface.
- [DNS]: Specifies the DNS servers to be used by the WireGuard interface.
- [MTU]: Specifies the maximum transmission unit (MTU) for the WireGuard interface.
Here is an example of a simple WireGuard configuration file:
[Interface]PrivateKey = /etc/wireguard/wg0.keyAddress = 10.0.0.1/24ListenPort = 51820[Peer]PublicKey = /etc/wireguard/peer1.pubAllowedIPs = 10.0.0.2/32
Interface Configuration
The interface configuration in a WireGuard configuration file defines the network interface that will be used by WireGuard. It specifies the IP address, DNS servers, and routing settings for the interface.
To configure the interface, use the following settings in the configuration file:
Address
The Address setting specifies the IP address of the WireGuard interface. It can be a single IP address or a range of IP addresses.
For example, to specify a single IP address, use the following syntax:
Address = 10.0.0.1/24
To specify a range of IP addresses, use the following syntax:
Address = 10.0.0.0/24-10.0.0.255
DNS
The DNS setting specifies the DNS servers that will be used by the WireGuard interface. It can be a single DNS server or a list of DNS servers.
For example, to specify a single DNS server, use the following syntax:
DNS = 8.8.8.8
To specify a list of DNS servers, use the following syntax:
DNS = 8.8.8.8, 8.8.4.4
Routing
The Routing setting specifies the routing table that will be used by the WireGuard interface. It can be a single routing table or a list of routing tables.
For example, to specify a single routing table, use the following syntax:
Routing = 10.0.0.0/24
To specify a list of routing tables, use the following syntax:
Routing = 10.0.0.0/24, 192.168.0.0/24
Peer Configuration
Configuring peers is crucial in establishing secure connections within a WireGuard network. It involves defining the settings for each device that will communicate with others. Let’s delve into the key aspects of peer configuration.
Public Key
Each peer requires a public key to identify itself and authenticate its communication. The public key is generated during the initial setup of WireGuard and is shared with other peers to establish a secure channel.
Endpoint
The endpoint specifies the IP address and port combination where the peer is reachable. It allows devices to connect to each other by establishing a secure tunnel over the specified endpoint.
Allowed IP Addresses
To restrict communication to specific IP addresses or networks, allowed IP addresses can be configured for each peer. This ensures that only authorized devices can communicate with each other within the WireGuard network.
Example Peer Configuration
Here’s an example peer configuration for connecting to a remote server:
[Peer] PublicKey = AllowedIPs = Endpoint = :
This configuration allows the local device to establish a secure connection with the remote server, using the specified public key, IP address, and port.
Firewall Configuration
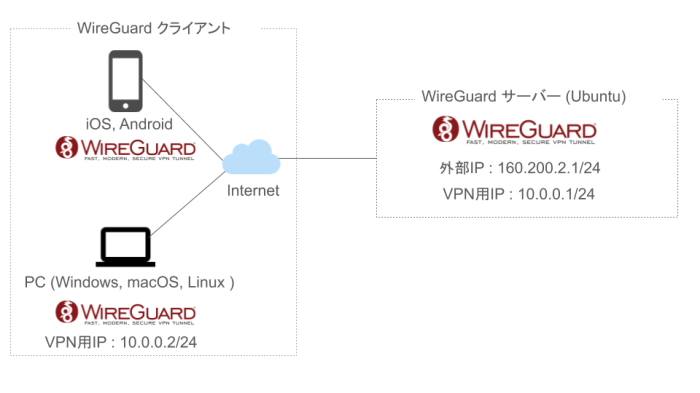
WireGuard incorporates firewall capabilities to manage network access, enhancing security and granular control over traffic flow.
The firewall settings within the WireGuard configuration file allow administrators to specify which ports and IP addresses are allowed or blocked for incoming and outgoing connections.
Allowed and Blocked Ports
- AllowedPorts: Restricts incoming connections to specific ports. Only traffic destined for these ports will be accepted.
- BlockedPorts: Prohibits incoming connections to specified ports. Traffic targeting these ports will be dropped.
Allowed and Blocked IP Addresses
- AllowedIPs: Grants access to specific IP addresses or subnets. Only connections originating from these addresses will be allowed.
- BlockedIPs: Denies access to specific IP addresses or subnets. Connections from these addresses will be blocked.
Example Firewall Configurations
Basic Firewall:
[Firewall] AllowedIPs = 192.168.1.0/24 BlockedPorts = 25, 110
Advanced Firewall:
[Firewall] AllowedIPs = 192.168.1.0/24, 10.0.0.0/16 AllowedPorts = 80, 443 BlockedIPs = 127.0.0.1, 8.8.8.8
Advanced Configuration
WireGuard offers various advanced configuration options to tailor its functionality to specific needs. These options provide granular control over various aspects of the VPN connection.
Keepalive Settings
Keepalive settings ensure that the VPN tunnel remains active and responsive even during periods of inactivity. WireGuard supports two keepalive mechanisms:
– Keepalive Interval: Sets the time interval between sending keepalive packets. – Keepalive Timeout: Specifies the maximum time allowed for a keepalive response before the connection is considered inactive.
Configuring these settings helps maintain a stable connection and prevent unnecessary tunnel dropouts.
MTU Settings
The Maximum Transmission Unit (MTU) determines the maximum size of data packets that can be transmitted over the VPN tunnel. By default, WireGuard sets the MTU to 1420 bytes. However, adjusting the MTU can improve performance in certain network environments.
A lower MTU may be necessary if the network path experiences fragmentation issues. A higher MTU can increase throughput if the network supports larger packets.
PreSharedKey (PSK) Authentication
PreSharedKey (PSK) authentication provides an alternative to public key cryptography for establishing a secure connection. With PSK, both peers share a secret key that is used to generate encryption keys.
PSK authentication is suitable for scenarios where public key infrastructure (PKI) is not feasible or preferred. It simplifies the setup process and reduces the computational overhead associated with public key cryptography.
Troubleshooting
WireGuard is generally stable and easy to configure, but errors and issues can still occur. Identifying and resolving these problems is crucial for maintaining a secure and functional WireGuard connection.
Common Errors
Some common errors that may arise include:
– Connection timeout – Permission denied – Invalid endpoint address – Duplicate IP address
Troubleshooting Techniques
To troubleshoot WireGuard issues, consider the following techniques:
– Check firewall settings: Ensure that WireGuard traffic is allowed through your firewall. – Verify IP addresses: Confirm that the IP addresses used in the configuration are correct and reachable. – Inspect logs: Examine WireGuard logs for error messages that may indicate the root cause of the issue.
– Test connectivity: Use tools like ping or traceroute to test connectivity between the WireGuard peers. – Disable other VPNs: Deactivate any other active VPN connections, as they may interfere with WireGuard. – Reinstall WireGuard: If all else fails, consider reinstalling WireGuard to resolve any potential configuration issues.
Advanced Troubleshooting
For more complex troubleshooting, consider the following advanced techniques:
– Use Wireshark: Capture and analyze network traffic using Wireshark to identify potential issues. – Consult documentation: Refer to the official WireGuard documentation for detailed troubleshooting guidance. – Seek community support: Join online forums or communities dedicated to WireGuard to connect with other users and seek assistance.
Best Practices
To ensure optimal performance, security, and reliability when configuring WireGuard, it is essential to adhere to recommended best practices. These guidelines encompass considerations for different use cases, ensuring that your WireGuard setup meets your specific requirements.
When configuring WireGuard, prioritize security by employing strong encryption algorithms and robust authentication mechanisms. Additionally, implement proper firewall rules to restrict unauthorized access and enhance network protection.
Performance Considerations
To optimize WireGuard performance, consider the following recommendations:
- Choose an appropriate MTU (Maximum Transmission Unit) size to match your network infrastructure, minimizing packet fragmentation and improving throughput.
- Utilize modern and efficient encryption algorithms, such as ChaCha20 or BLAKE2, to reduce computational overhead and enhance performance.
- Configure WireGuard on high-performance hardware with sufficient processing power and network bandwidth to handle the expected traffic load.
Reliability Enhancements
To enhance WireGuard reliability, consider the following best practices:
- Implement keepalive mechanisms to maintain active connections and detect network interruptions promptly.
- Configure redundant tunnels to provide failover capabilities in case of primary tunnel failures.
- Monitor WireGuard performance and logs regularly to identify and resolve any potential issues proactively.
Comparison with Other VPN Technologies
WireGuard is a modern and highly efficient VPN technology that offers several advantages over traditional VPN protocols such as OpenVPN and IPSec. Let’s compare these technologies and discuss their key strengths and weaknesses.
OpenVPN
OpenVPN is an open-source and widely used VPN protocol known for its security and flexibility. It utilizes OpenSSL for encryption and provides a wide range of configuration options.Advantages:
-
- -*Strong encryption
OpenVPN supports various encryption algorithms, including AES-256, which provides robust protection against eavesdropping.
- -*Strong encryption
-*Flexible configuration
OpenVPN allows for extensive customization of settings, making it suitable for complex network environments.
-*Widely supported
OpenVPN is compatible with a broad range of platforms and devices, including routers, mobile phones, and servers.
Disadvantages:
-
- -*Performance overhead
OpenVPN can be resource-intensive, especially on low-powered devices, due to its complex encryption algorithms.
- -*Performance overhead
-*Complex setup
Configuring OpenVPN can be challenging, especially for users with limited technical expertise.
IPSec
IPSec (Internet Protocol Security) is a suite of protocols that provides secure communication at the IP layer. It is commonly used for VPN connections between networks and remote users.Advantages:
-
- -*Native support
IPSec is natively supported by most operating systems and network devices, making it easy to implement and manage.
- -*Native support
-*Scalability
IPSec can handle large-scale VPN deployments with thousands of concurrent connections.
-*Interoperability
IPSec is widely interoperable with various VPN gateways and devices, ensuring compatibility in multi-vendor environments.
Disadvantages:
-
- -*Less secure
IPSec has been subject to several security vulnerabilities in the past, making it less secure than newer VPN protocols like WireGuard.
- -*Less secure
-*Limited configuration options
IPSec offers fewer configuration options compared to OpenVPN, which may limit its suitability for complex network requirements.
Choosing the Best VPN Technology
The choice of VPN technology depends on specific requirements and use cases.
-
- -*Security and privacy
WireGuard offers the highest level of security and privacy due to its modern encryption algorithms and streamlined design.
- -*Security and privacy
-*Performance
WireGuard is significantly faster than OpenVPN and IPSec, making it ideal for high-speed connections and latency-sensitive applications.
-*Ease of use
WireGuard is designed to be simple to configure and manage, even for non-technical users.
-*Compatibility
WireGuard is still relatively new compared to OpenVPN and IPSec, so its compatibility with certain devices and platforms may be limited.
In general, WireGuard is the recommended choice for most users who prioritize security, performance, and ease of use.
OpenVPN remains a solid option for users who require extensive configuration options and wide platform support. IPSec is best suited for large-scale VPN deployments where interoperability and native support are essential.
Use Cases
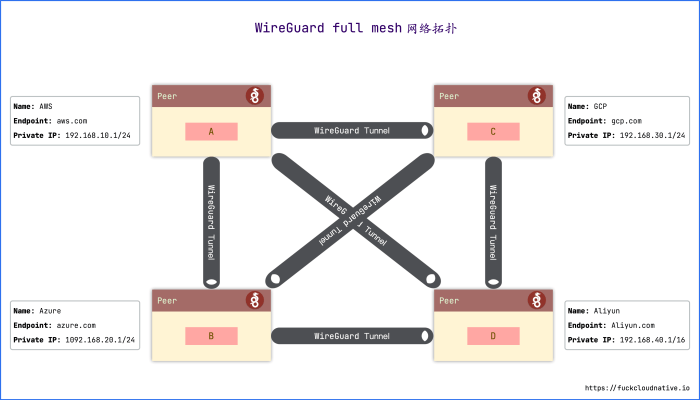
WireGuard is a versatile VPN technology that finds application in various scenarios. Its ease of use, high performance, and strong security features make it suitable for a wide range of use cases.
Remote Access
WireGuard is ideal for providing secure remote access to corporate networks. Employees can connect to their office network from anywhere with an internet connection, allowing them to access internal resources and applications securely.
Site-to-Site VPNs
WireGuard can establish secure connections between multiple sites or branch offices. This enables seamless communication and resource sharing among geographically dispersed locations.
Cloud Connectivity
WireGuard facilitates secure connectivity to cloud services, such as AWS or Azure. Organizations can establish encrypted tunnels to their cloud environments, allowing for secure data transfer and remote management.
Integration with Other Tools
WireGuard’s flexibility allows it to integrate seamlessly with a wide range of other tools and technologies, enhancing its capabilities and expanding its use cases.
The benefits of using WireGuard with these tools include simplified management, automated deployment, and enhanced security.
Network Management Systems
WireGuard can be integrated with network management systems (NMS) to provide centralized control and visibility over VPN connections. NMS tools allow administrators to monitor the health and performance of WireGuard tunnels, manage user access, and troubleshoot issues.
Container Orchestration Platforms
WireGuard integrates seamlessly with container orchestration platforms like Docker and Kubernetes. This integration enables the automatic deployment and management of WireGuard tunnels within containerized environments. By using WireGuard with container orchestration platforms, administrators can establish secure and dynamic VPN connections between containers and other resources.
Cloud Providers
WireGuard is supported by major cloud providers such as AWS, Azure, and GCP. This integration allows users to easily set up and manage WireGuard tunnels within their cloud environments. Cloud providers offer managed WireGuard services that simplify deployment, configuration, and maintenance.
Conclusion
Mastering WireGuard configuration unlocks a world of possibilities for secure and efficient network connectivity. By leveraging the insights and best practices Artikeld in this guide, you can confidently deploy WireGuard solutions that meet your specific requirements. Embrace the power of WireGuard and elevate your network security and performance to new heights.