Welcome to the realm of WireGuard, a cutting-edge VPN technology that has revolutionized secure networking. Its simplicity, speed, and robust security features have made it the go-to choice for individuals and organizations seeking unparalleled online protection. This comprehensive guide will equip you with the knowledge and skills to master WireGuard configuration, empowering you to establish secure and efficient VPN connections.
WireGuard’s user-friendly interface and straightforward configuration process make it accessible to both technical enthusiasts and everyday users. With its advanced encryption algorithms and flexible routing options, WireGuard ensures the privacy and integrity of your data, enabling you to navigate the digital landscape with confidence.
WireGuard Configuration Overview

WireGuard is a modern and versatile VPN (Virtual Private Network) protocol that offers a secure and efficient way to establish encrypted connections over the internet. It features a streamlined configuration process compared to other VPN protocols, making it an attractive choice for both personal and professional use.To
set up a WireGuard connection, you need to configure a few key elements:
-
- -*Public and private keys Each device participating in the WireGuard connection needs to have a unique pair of public and private keys. These keys are used to encrypt and decrypt data transmitted over the connection.
-*Peer configuration
Each device needs to know the public key and IP address of the other devices it wants to connect to. This information is typically specified in a configuration file.
-*Firewall rules
Firewall rules are required to allow traffic through the WireGuard interface and forward it to the appropriate devices.
Once these elements are configured, devices can establish secure and encrypted connections using the WireGuard protocol.
Configuring WireGuard Interfaces
To establish secure connections between devices using WireGuard, you need to configure WireGuard interfaces on each device. Here’s a step-by-step guide for different platforms:
Before starting, ensure you have installed WireGuard on your device.
Linux
- Create a new WireGuard interface using the command:
sudo wg setconf wg0 /path/to/interface.conf - Edit the interface configuration file
/path/to/interface.confto specify the necessary parameters (e.g., IP address, private and public keys, peers). - Activate the interface by running:
sudo wg-quick up wg0
Windows
- Open PowerShell as administrator and run:
Set-ExecutionPolicy Bypass- Scope Process
- Force
- Install WireGuard using the command:
choco install wireguard-tun - Create a new WireGuard interface using:
wg genkey | wg set wg0 privatekey - Generate a public key using:
wg pubkey - Edit the interface configuration file
%ProgramData%\WireGuard\wg0.confto configure the interface. - Activate the interface by running:
wg-quick up wg0
macOS
- Install WireGuard using Homebrew:
brew install wireguard-go - Create a new WireGuard interface using:
wg genkey | wg set wg0 privatekey - Generate a public key using:
wg pubkey - Edit the interface configuration file
/etc/wireguard/wg0.conf - Activate the interface by running:
sudo wg-quick up wg0
Configuring WireGuard Peers
To establish secure connections between WireGuard peers, you need to configure them appropriately.
This involves exchanging public keys and specifying allowed IP addresses.
Peer Configuration Options
- Public Keys: Each WireGuard peer has a public key that identifies it. Peers exchange public keys to establish a secure connection.
- Allowed IPs: You can specify which IP addresses are allowed to connect to a particular peer. This helps prevent unauthorized access.
Configuring WireGuard Routing
WireGuard routing allows you to direct traffic through the VPN tunnel, ensuring secure and efficient data transmission. By configuring specific routes, you can control which traffic is routed through the VPN and which remains on the local network.
WireGuard supports both static and dynamic routing. Static routes are manually configured and provide a specific path for traffic to follow. Dynamic routing, on the other hand, uses routing protocols to automatically discover and update routes based on network conditions.
Static Routes
Static routes are useful for directing traffic to specific destinations, such as a remote server or a private subnet. To configure a static route, use the following syntax in your WireGuard configuration file:
[Peer] AllowedIPs = 192.168.10.0/24 Route = 10.0.0.0/24
In this example, traffic destined for the subnet 10.0.0.0/24 will be routed through the WireGuard tunnel.
Policy-Based Routing
Policy-based routing allows you to apply routing rules based on specific criteria, such as source or destination IP address, port number, or protocol. This provides greater flexibility and control over how traffic is routed.
To configure policy-based routing, use the following syntax:
[Peer] AllowedIPs = 192.168.10.0/24 Route = 10.0.0.0/24 Table = 100
In this example, traffic matching the criteria will be routed through the WireGuard tunnel and assigned to routing table 100.
Configuring WireGuard Firewall Rules
Configuring firewall rules is crucial for controlling the flow of traffic through a WireGuard tunnel. By implementing firewall rules, you can restrict access to specific ports, block certain types of traffic, and enhance the security of your network.
Firewall Rule Syntax
WireGuard firewall rules follow a specific syntax that includes the following elements:
- Table: The table to which the rule applies (e.g., filter, nat)
- Chain: The chain within the table (e.g., INPUT, OUTPUT)
- Rule Number: A unique identifier for the rule
- Source: The source IP address or range
- Destination: The destination IP address or range
- Protocol: The protocol to which the rule applies (e.g., TCP, UDP)
- Port: The port number or range (e.g., 80, 443)
- Action: The action to take when the rule matches (e.g., ACCEPT, DROP)
Troubleshooting WireGuard Connections
Troubleshooting WireGuard connections can be challenging, but it is essential to ensure that your network is functioning properly. Here are some common issues that you may encounter and tips for resolving them.
One common issue is that the WireGuard interface may not be active. To fix this, check if the interface is up and running using the command “wg show”. If the interface is not up, you can try restarting the WireGuard service or rebooting the system.
Peer Connectivity Issues
Another common issue is that you may not be able to connect to your WireGuard peers. This can be caused by several factors, such as incorrect peer configuration, firewall rules blocking traffic, or network connectivity issues.
- Verify that the peer’s public key is correct in your configuration.
- Check if the firewall is blocking WireGuard traffic. You can disable the firewall temporarily to test if this is the issue.
- Ensure that there is no network connectivity issues between the two peers.
Optimizing WireGuard Performance
To enhance WireGuard’s performance, various techniques can be employed. These include selecting appropriate MTU sizes and encryption algorithms, as well as monitoring performance metrics to identify potential bottlenecks.
Choosing the Right MTU
The MTU (Maximum Transmission Unit) defines the maximum packet size that can be transmitted over a network interface. Selecting an optimal MTU size is crucial for minimizing fragmentation and improving performance. Larger MTU sizes can reduce the number of packets transmitted, while smaller MTU sizes can prevent fragmentation but introduce overhead.
Finding the optimal MTU size requires experimentation and consideration of factors such as the network infrastructure and packet size distribution.
Encryption Algorithm Selection
WireGuard supports multiple encryption algorithms, including ChaCha20, AES-GCM, and BLAKE2s. The choice of encryption algorithm can impact performance. ChaCha20 is typically faster than AES-GCM, while AES-GCM offers stronger security. Selecting the appropriate algorithm involves balancing performance and security requirements.
Monitoring WireGuard Performance
Monitoring WireGuard performance is essential for identifying potential bottlenecks and ensuring optimal operation. Metrics such as connection speed, latency, and packet loss can be monitored using tools like WireGuard’s built-in monitoring utilities or third-party network monitoring tools. Regular monitoring allows for proactive identification and resolution of performance issues.
Advanced WireGuard Configuration
WireGuard’s versatility extends beyond basic configurations, offering advanced options for complex networking scenarios. This section delves into advanced WireGuard configurations, empowering users to explore multiple interfaces, configure NAT, and establish mesh networks.
Multiple Interfaces
WireGuard supports multiple interfaces on a single host, allowing for flexible network configurations. Each interface can have its own IP address, encryption keys, and routing rules, enabling isolation and customization of network traffic.
NAT Configuration
Network Address Translation (NAT) allows WireGuard to connect devices on private networks to the public internet. By configuring NAT rules, users can establish outbound connections while maintaining privacy and security for internal network resources.
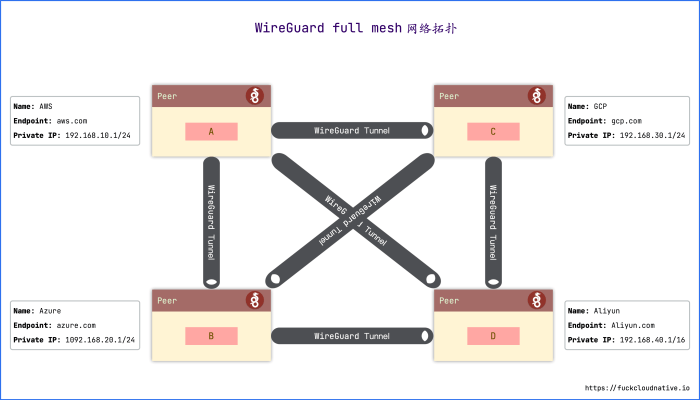
Mesh Networks
WireGuard facilitates the creation of mesh networks, where multiple devices connect directly to each other without a central server. This topology enhances network resilience and scalability, as each device acts as both a client and a server, distributing traffic and reducing single points of failure.
WireGuard Security Considerations
WireGuard is a secure VPN protocol that provides strong encryption and privacy. However, it is important to be aware of the security implications of using WireGuard and to take steps to secure your connections.One of the most important things to do is to use strong encryption.
WireGuard supports a variety of encryption algorithms, including ChaCha20, AES-GCM, and Curve25519. It is recommended to use the strongest encryption algorithm that is supported by your devices.Another important security measure is to implement proper firewall rules. WireGuard allows you to control which traffic is allowed to pass through the VPN tunnel.
By default, all traffic is allowed, but you can restrict traffic to specific IP addresses or ports. This can help to protect your network from unauthorized access.
Best Practices for Securing WireGuard Connections
Here are some best practices for securing WireGuard connections:
- Use strong encryption algorithms.
- Implement proper firewall rules.
- Use a strong password for your WireGuard key.
- Keep your WireGuard software up to date.
- Monitor your WireGuard connections for suspicious activity.
By following these best practices, you can help to ensure that your WireGuard connections are secure and private.
WireGuard Use Cases
WireGuard is a versatile VPN solution with a wide range of applications. It offers secure and efficient networking for various scenarios, including:
- Remote access: WireGuard allows users to securely connect to their home or office networks from anywhere with an internet connection. It provides a fast and reliable way to access files, applications, and resources on the remote network.
- Secure networking: WireGuard can be used to create secure private networks between multiple devices or locations. It is particularly useful for businesses and organizations that need to connect their remote offices, data centers, or employees’ devices securely.
- Load balancing: WireGuard can be configured for load balancing, distributing network traffic across multiple servers or network interfaces. This helps improve performance and reliability, ensuring that applications and services remain accessible even during high traffic periods.
Case Studies and Testimonials
Numerous users and organizations have successfully implemented WireGuard, experiencing significant benefits in terms of security, performance, and ease of use. Here are a few case studies and testimonials:
“WireGuard has been a game-changer for our remote access needs. It provides a secure and reliable connection that allows our employees to access their work resources from anywhere, anytime.”
IT Manager, Fortune 500 Company
“We have been using WireGuard to connect our multiple offices and data centers. It has significantly improved our network performance and reduced latency, allowing us to collaborate more efficiently.”
Network Engineer, Large Enterprise
Summary
By embracing the power of WireGuard, you unlock a world of possibilities. Whether you seek to protect your online activities, establish secure remote access, or optimize your network performance, WireGuard empowers you to achieve your goals. Its versatility and adaptability make it the ideal solution for a wide range of scenarios, from personal use to enterprise-grade deployments.
Embrace the future of VPN technology with WireGuard and experience the unparalleled benefits of secure and seamless networking.