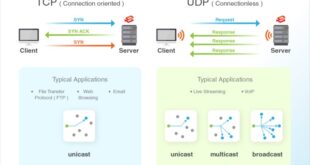
Secure Shell (SSH) is a powerful protocol that enables secure remote access and data transfer over insecure networks. At the heart of SSH lies the concept of ports, specifically TCP port 22, which plays a crucial role in establishing SSH connections. However, the choice between TCP and UDP for SSH …
Read More »SSH Server
SSH UDP Server: A Guide to Configuration, Security, and Performance Optimization
In the realm of secure remote access, SSH UDP servers have emerged as a versatile and efficient solution. Leveraging the User Datagram Protocol (UDP), these servers offer a unique combination of speed, flexibility, and enhanced security. This comprehensive guide delves into the intricacies of SSH UDP servers, exploring their functionality, …
Read More »SSH over UDP: A Comprehensive Guide to Enhance Performance and Security
In the realm of secure remote access, SSH (Secure Shell) stands tall as a ubiquitous protocol. While traditionally implemented over TCP, SSH over UDP has emerged as an alternative offering unique advantages and considerations. This guide delves into the intricacies of SSH over UDP, exploring its benefits, drawbacks, implementation, security …
Read More »SSH Tunneling with UDP: A Comprehensive Guide to Securing Your Connections
In the realm of cybersecurity, SSH tunneling has emerged as a powerful tool for establishing secure connections over insecure networks. By leveraging UDP, a connectionless protocol, SSH tunneling offers unique advantages in terms of performance, reliability, and versatility. This comprehensive guide delves into the intricacies of SSH tunneling with UDP, …
Read More »SSH UDP Custom Port Forwarding: A Comprehensive Guide for Secure Remote Access
In the realm of secure remote access, SSH UDP custom port forwarding stands out as a versatile and powerful tool. This technique allows users to establish secure connections to remote servers, bypass firewalls, and tunnel traffic over unreliable networks, all while maintaining the utmost confidentiality and integrity. This comprehensive guide …
Read More »Creating an SSH Tunnel over UDP: A Comprehensive Guide
In the realm of network security, the ability to establish secure and reliable remote connections is paramount. SSH (Secure Shell) has emerged as a ubiquitous protocol for encrypted communication, while UDP (User Datagram Protocol) offers a lightweight and efficient transport layer. By combining these technologies, we can create SSH tunnels …
Read More »Mastering Termux SSH: A Comprehensive Guide to Secure Remote Access
In the realm of mobile computing, Termux SSH emerges as a powerful tool, unlocking a world of possibilities for Android users. This comprehensive guide will delve into the depths of Termux SSH, empowering you to establish secure connections to remote servers, execute commands, and harness its advanced features. Termux, an …
Read More »Understanding SSH UDP or TCP: A Comprehensive Guide
In the realm of secure remote access, SSH (Secure Shell) reigns supreme. This versatile protocol allows for secure data transfer and remote command execution, empowering users with unparalleled control over their systems. At the heart of SSH lies a fundamental choice: UDP (User Datagram Protocol) or TCP (Transmission Control Protocol). …
Read More »SSH: UDP or TCP? Unraveling the Network Layer Protocol
Secure Shell (SSH), a cornerstone of secure remote access and data transfer, has captivated the world of networking. As we delve into the intricacies of SSH, a fundamental question arises: what network layer protocol does it employ? Is it the reliable TCP or the connectionless UDP? Embark on this journey …
Read More »SSH UDP Account: A Comprehensive Guide to Secure Remote Access
In the realm of cybersecurity, SSH (Secure Shell) has emerged as a cornerstone technology for secure remote access and data transfer. Its versatility and robust security features have made it an indispensable tool for system administrators, developers, and anyone seeking to establish secure connections over untrusted networks. This comprehensive guide …
Read More »