ssh.sshslowdns.com – In the realm of network security, the Secure Shell (SSH) protocol reigns supreme, providing a robust and encrypted channel for remote access and data transfer. SSH UDP, a variant of SSH that utilizes the User Datagram Protocol (UDP), offers a unique set of advantages and challenges. This comprehensive …
Read More »SSH Server
Unlock Secure Remote Access with SSH UDP Gratis
In the realm of secure remote access, SSH UDP stands out as a powerful protocol that offers a unique blend of speed, efficiency, and security. Unlike its TCP counterpart, SSH UDP utilizes a connectionless transport layer, enabling lightning-fast data transmission and minimizing latency. In this comprehensive guide, we will delve …
Read More »Fast SSH UDP: A Comprehensive Guide to High-Speed Secure Shell
In the realm of remote access and network management, SSH (Secure Shell) has long been the go-to protocol for establishing secure connections. However, with the advent of Fast SSH UDP, a revolutionary variant of the protocol, the possibilities of secure and high-speed remote access have been amplified. This comprehensive guide …
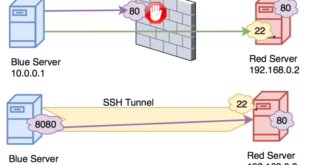
Read More »SSH UDP Tunneling: A Comprehensive Guide to Secure and Efficient Data Transmission
In the realm of secure and efficient data transmission, SSH UDP tunneling emerges as a powerful tool that enables seamless communication across networks. This technique harnesses the capabilities of the Secure Shell (SSH) protocol to establish encrypted tunnels, allowing users to bypass firewalls, access remote resources, and optimize network performance. …
Read More »Understanding SSH UDP Request: A Comprehensive Guide
In the realm of secure remote access, SSH UDP requests play a crucial role. SSH (Secure Shell) is a widely used protocol for establishing encrypted connections over insecure networks, and its UDP (User Datagram Protocol) variant offers unique advantages for specific use cases. This comprehensive guide will delve into the …
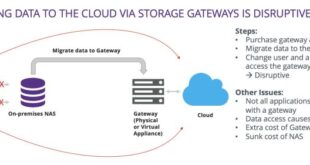
Read More »SSH Store UDP: Enhancing Data Security and Transfer
In the realm of secure data storage and transmission, SSH Store UDP emerges as a formidable technology that seamlessly integrates the robust capabilities of SSH with the efficiency of UDP. SSH Store UDP has revolutionized the way businesses and individuals safeguard and share sensitive information, offering unparalleled security and performance. …
Read More »SSH UDP Premium: Unlocking Secure and Efficient Remote Access
In the realm of remote access and secure communication, SSH (Secure Shell) stands as a cornerstone technology. As organizations and individuals embrace the benefits of remote work and cloud computing, SSH has become an indispensable tool for establishing secure connections over the internet. This comprehensive guide delves into the world …
Read More »Unleashing the Power of UDP SSH Accounts: A Comprehensive Guide
In the realm of secure remote access, UDP SSH accounts have emerged as a game-changer, offering a unique blend of speed, efficiency, and enhanced security. Unlike traditional SSH connections that utilize TCP, UDP SSH leverages the User Datagram Protocol, opening up a world of possibilities for seamless data transfer and …
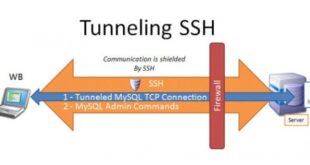
Read More »Securing SSH UDP Connections: A Comprehensive Guide for Enhanced Security
SSH (Secure Shell) is a critical tool for secure remote access and management of systems. While TCP is the default transport protocol for SSH, UDP (User Datagram Protocol) can also be used, offering certain advantages. This comprehensive guide delves into the world of SSH UDP, exploring its purpose, vulnerabilities, best …
Read More »UDP Custom SSH: Enhancing Security and Performance in Network Communications
In the realm of network security, SSH (Secure Shell) has long been a trusted protocol for establishing secure remote connections. However, with the increasing demand for faster and more efficient network protocols, UDP (User Datagram Protocol) custom SSH has emerged as a promising alternative to traditional SSH. UDP custom SSH …
Read More »