In the realm of secure remote server access, SSH (Secure Shell) reigns supreme. Central to SSH’s robust security is the public key authentication mechanism, which relies on a public key to verify the identity of a connecting client. However, if this public key is too small, it can pose a …
Read More »SSH Server
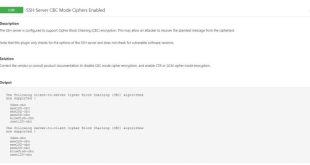
SSH Server CBC Mode Ciphers Enabled: Enhancing Security and Protecting Connections
In the realm of secure remote connections, SSH (Secure Shell) reigns supreme. It plays a pivotal role in protecting sensitive data and communications by encrypting network traffic between client and server. At the heart of SSH security lies the selection of robust ciphers, including those operating in Cipher Block Chaining …
Read More »Mastering Kpym Telnet SSH Server: A Comprehensive Guide
In the realm of secure remote access, kpym telnet ssh server stands out as a formidable tool. This versatile server empowers users with the ability to establish secure connections to remote hosts, facilitating efficient management and troubleshooting tasks. In this comprehensive guide, we delve into the intricacies of kpym telnet …
Read More »The Ultimate Guide to Setting Up and Securing a Termux SSH Server
Welcome to the world of secure and remote access with Termux SSH Server! This comprehensive guide will empower you to establish a robust SSH server on your Termux environment, enabling you to manage your devices and access your data from anywhere in the world. Whether you’re a seasoned IT professional …
Read More »A Comprehensive Guide to Installing and Configuring an SSH Server on Linux Mint
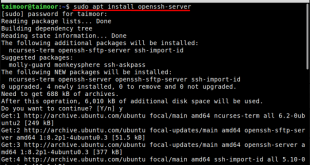
Secure Shell (SSH) is an essential tool for remote server management, providing a secure and encrypted channel for accessing and controlling systems over a network. In this guide, we will delve into the intricacies of installing and configuring an SSH server on Linux Mint, empowering you to harness the full …
Read More »Server Response Omission of SSH Protocol Identification: Causes and Resolutions
When establishing a secure connection to a remote server via SSH, the server’s response plays a pivotal role in authenticating the connection. A crucial aspect of this response is the inclusion of the SSH protocol identification string. However, in certain instances, this identification may be absent, leading to connection issues …
Read More »Mastering Linux Mint SSH Server: A Comprehensive Guide to Secure Remote Access
In the realm of Linux operating systems, Linux Mint stands out as a user-friendly and powerful distribution. Its versatility extends to the world of secure remote access, where the SSH server plays a crucial role. This comprehensive guide will delve into the intricacies of the Linux Mint SSH server, empowering …
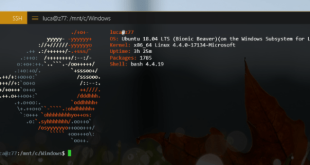
Read More »WSL SSH Server: A Comprehensive Guide to Remote Access on Windows
In the realm of computing, the Windows Subsystem for Linux (WSL) has emerged as a game-changer, enabling users to seamlessly run Linux distributions within the Windows operating system. One of the most powerful features of WSL is its SSH server, which allows for secure remote access to your WSL environment …
Read More »SSH UDP Server: A Comprehensive Guide to Secure and High-Performance Remote Access
In the realm of secure remote access, SSH (Secure Shell) has long been a trusted protocol. Its TCP-based implementation has proven reliable, but for applications demanding low latency and high performance, SSH over UDP (User Datagram Protocol) emerges as a compelling alternative. This guide delves into the intricacies of SSH …
Read More »SSH Server Weak Key Exchange Algorithms: A Guide to Prevention and Mitigation
Secure Shell (SSH) is a vital protocol for remote server management and secure data transfer. However, the security of SSH deployments can be compromised if weak key exchange algorithms are supported. This article explores the risks associated with weak key exchange algorithms in SSH, provides guidance on identifying vulnerable servers, …
Read More »