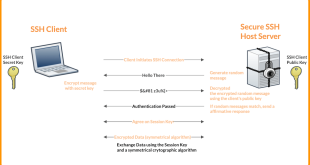
In the realm of web server security, SSH (Secure Shell) stands as a cornerstone, providing a secure channel for remote access and management. Configuring SSH effectively is paramount, and one crucial aspect is selecting the appropriate port number. This decision involves balancing security considerations, ease of use, and potential performance …
Read More »SSH Server
WSL SSH Server: Unleashing the Power of Secure Remote Access in Windows
In the realm of computing, seamless remote access to Linux environments has become a cornerstone of modern productivity and collaboration. Windows Subsystem for Linux (WSL) has revolutionized this landscape by enabling Linux distributions to run natively on Windows, opening up a world of possibilities for developers, system administrators, and enthusiasts …
Read More »Unveiling the Enigmatic World of SSH Server CBC Mode Ciphers: A Comprehensive Exploration
In the realm of secure communication, the SSH protocol stands as a cornerstone, enabling encrypted connections between devices across networks. Delving into the intricacies of SSH server configuration, we encounter a crucial aspect: the selection of encryption ciphers. Among these ciphers, CBC mode emerges as a prominent choice, offering a …
Read More »SSH Server Security: Addressing Weak Key Exchange Algorithms
In the realm of cybersecurity, the Secure Shell (SSH) protocol plays a pivotal role in establishing secure remote connections. However, the effectiveness of SSH connections hinges on the robustness of the underlying key exchange algorithms. Weak key exchange algorithms can compromise the integrity of SSH connections, exposing systems to a …
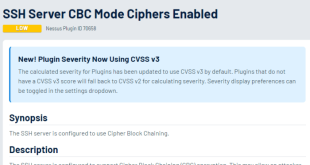
Read More »SSH Server CBC Mode Ciphers Enabled: Enhancing Security and Performance
In the realm of secure remote access, SSH (Secure Shell) stands as a pivotal protocol. To further bolster its security posture, enabling CBC (Cipher Block Chaining) mode ciphers on SSH servers has emerged as a crucial practice. This article delves into the intricacies of SSH server CBC mode ciphers, exploring …
Read More »Enable SSH on Windows Server 2008: A Comprehensive Guide
Secure Shell (SSH) is an essential tool for managing remote servers securely. By enabling SSH on Windows Server 2008, administrators can connect to and control their servers from anywhere with an internet connection. This guide will provide a comprehensive overview of the process, including prerequisites, configuration, management, and troubleshooting. SSH …
Read More »SSH Server Public Key Too Small: Understanding and Resolving the Issue
In the realm of secure remote server access, SSH (Secure Shell) reigns supreme. Central to its security is the public key authentication mechanism, which hinges on the size of the public key. When an SSH server encounters a “Public Key Too Small” error, it raises concerns about the strength of …
Read More »Troubleshooting ‘Server Response Does Not Contain SSH Protocol Identification’
In the realm of secure remote communication, SSH (Secure Shell) plays a pivotal role. SSH protocol identification is a crucial aspect of establishing a secure connection, but its absence can raise concerns. This article delves into the causes, implications, and troubleshooting techniques for missing SSH protocol identification, ensuring seamless and …
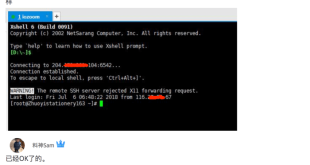
Read More »Troubleshooting the Remote SSH Server’s Rejection of X11 Forwarding Requests
X11 forwarding, a feature of the SSH protocol, enables users to securely access and interact with graphical applications running on a remote server from their local machine. However, sometimes, the remote SSH server may reject X11 forwarding requests, preventing users from accessing remote graphical applications. This comprehensive guide will delve …
Read More »Troubleshooting SSH Connectivity Issues: The Gshant User’s Remote Server Connection Attempt
In the realm of remote server management, SSH (Secure Shell) plays a pivotal role, enabling secure and efficient access to systems across networks. However, when a user encounters difficulties establishing an SSH connection, a methodical troubleshooting approach is crucial to identify and resolve the underlying issue. This comprehensive guide will …
Read More »