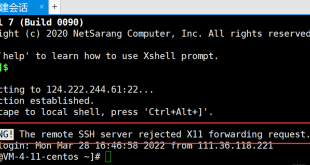
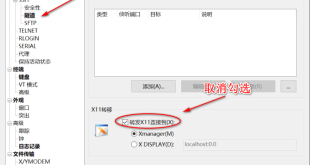
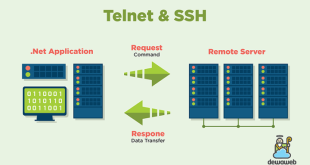
X11 forwarding is a useful feature that allows you to access graphical applications running on a remote server from your local machine. However, sometimes you may encounter the error “the remote ssh server rejected x11 forwarding request”. This can be a frustrating issue, but it is usually easy to resolve. …
Read More »SSH Server
The Remote SSH Server Rejected X11 Forwarding Request: A Comprehensive Guide
When working with remote servers, X11 forwarding is a powerful tool that allows you to seamlessly display graphical applications on your local machine. However, sometimes you may encounter the frustrating error message “the remote ssh server rejected x11 forwarding request.” This guide will delve into the causes of this error, …
Read More »SSH UDP Server: Enhancing Security and Performance in Network Communications
In the realm of secure network communications, the SSH UDP server stands out as a powerful tool. By leveraging the User Datagram Protocol (UDP), SSH UDP servers offer a unique combination of security and performance enhancements that cater to diverse use cases. Unlike its TCP counterpart, SSH UDP operates on …
Read More »SSH Server Security: Mitigating Risks from Weak Key Exchange Algorithms
In the realm of secure remote access, SSH servers play a critical role. However, vulnerabilities stemming from weak key exchange algorithms can compromise the integrity of these servers, posing significant security risks. Understanding and addressing these vulnerabilities is essential for safeguarding sensitive data and maintaining network security. This comprehensive guide …
Read More »SSH Server Public Key Too Small: Risks and Mitigation Strategies
In the realm of secure remote access, the SSH protocol reigns supreme. At its core lies the public key infrastructure, where a key’s size plays a pivotal role. In this article, we delve into the critical implications of using an SSH server public key that is too small, exploring the …
Read More »The Ultimate Guide to Linux Mint SSH Server
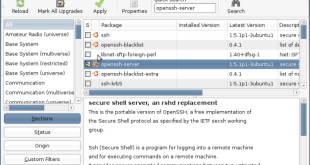
Welcome to the comprehensive guide to Linux Mint SSH Server! In this guide, we will delve into the world of secure remote access and management, empowering you to unlock the full potential of your Linux Mint system. SSH, or Secure Shell, is a powerful tool that allows you to securely …
Read More »Kpym Telnet/SSH Server: A Comprehensive Guide for Secure Remote Access
In the realm of secure remote access, the Kpym Telnet/SSH server stands as a formidable solution, offering a robust suite of features and unparalleled security measures. This guide delves into the intricacies of Kpym, exploring its capabilities, security considerations, and practical applications, empowering you with the knowledge to harness its …
Read More »How to Check if SSH Server is Running on Ubuntu: A Comprehensive Guide
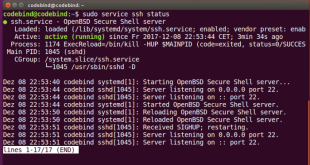
Secure Shell (SSH) is a vital protocol for remote server management and secure file transfer. Ensuring that the SSH server is running smoothly is crucial for maintaining system accessibility and security. This guide will provide a comprehensive overview of how to check if the SSH server is running on Ubuntu, …
Read More »Secure Your Linux Mint System with SSH: A Comprehensive Guide
In the realm of system administration, secure remote access is paramount. SSH, the Secure Shell protocol, stands as a cornerstone of secure remote connectivity, enabling system administrators and users alike to securely manage and access systems over a network. In this comprehensive guide, we delve into the intricacies of installing …
Read More »Unveiling the Mystery: Delving into the Enigma of Server Response Without SSH Protocol Identification
In the realm of secure communication, SSH protocol identification stands as a cornerstone, ensuring the integrity and confidentiality of data exchange. Yet, occasionally, a perplexing phenomenon arises—a server’s response devoid of SSH protocol identification. This anomaly can disrupt communication, leaving users bewildered and seeking answers. Embark on an enlightening journey …
Read More »