In the realm of secure remote access, SSH UDP Premium emerges as a game-changer, offering an unparalleled combination of enhanced security and blazing-fast performance. This innovative protocol leverages the power of UDP to deliver a robust and reliable connection, ensuring seamless access to critical systems and resources. SSH UDP Premium …
Read More »SSH Server
Does SSH Use TCP or UDP? A Comprehensive Guide
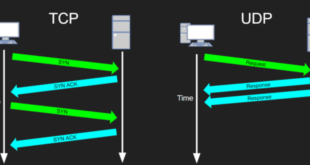
Secure Shell (SSH) is a versatile protocol that enables secure communication over unsecured networks. Its primary role is to establish encrypted connections between two remote hosts, facilitating secure data transfer, remote command execution, and secure remote login. One crucial aspect of SSH is its reliance on transport protocols, which play …
Read More »UDP SSH: A Comprehensive Guide to Enhance Network Performance and Security
In the realm of network connectivity, the advent of UDP SSH (User Datagram Protocol Secure Shell) has revolutionized secure remote access. UDP SSH harnesses the power of UDP, a connectionless protocol, to establish secure communication channels with remarkable speed and efficiency, making it an ideal solution for applications demanding real-time …
Read More »Is SSH TCP or UDP? A Comprehensive Guide to Protocol Usage in SSH
SSH, or Secure Shell, is a network protocol that provides secure remote access to a computer system. It is widely used for managing servers, transferring files, and executing commands on remote machines. Understanding the underlying protocols used by SSH is crucial for optimizing its performance and security. This guide will …
Read More »SSH UDP Custom: A Comprehensive Guide to Enhanced Connectivity
In the realm of secure remote access, SSH (Secure Shell) stands as a pillar of reliability. However, by harnessing the power of custom UDP ports, you can unlock a new dimension of SSH connectivity, enhancing security, performance, and flexibility. This guide will delve into the intricacies of SSH UDP custom …
Read More »SSH over TCP or UDP: Understanding the Differences and Applications
In the realm of secure remote access, SSH (Secure Shell) stands as a cornerstone technology, facilitating encrypted communication over insecure networks. At its core, SSH leverages two primary transport protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). Understanding the distinctions between these protocols is crucial for optimizing SSH …
Read More »SSH UDP: A Secure and Versatile Remote Access Protocol
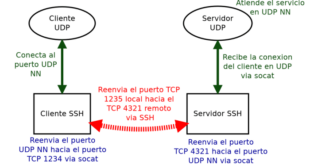
SSH UDP is a powerful protocol that offers secure remote access to servers and devices. It is a lightweight and efficient alternative to SSH TCP, making it ideal for applications that require low latency and high performance. In this comprehensive guide, we will explore the benefits, configuration, security implications, performance …
Read More »A Comprehensive Guide to Enable SSH on Windows Server 2008
In the realm of system administration, Secure Shell (SSH) reigns supreme as a secure and versatile protocol for remote server access and management. In this guide, we will embark on a journey to enable SSH on Windows Server 2008, providing you with a comprehensive understanding of the process, configuration, and …
Read More »SSH Connection Troubleshooting: Resolving “gshant user is attempting to connect to a remote ssh server” Error
Secure Shell (SSH) is a powerful tool for establishing secure remote connections, but it can sometimes encounter issues. One common error message is “gshant user is attempting to connect to a remote ssh server.” This error can be frustrating, but it can be resolved by understanding the underlying causes and …
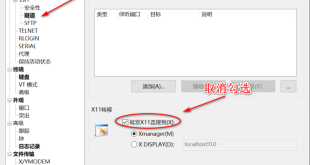
Read More »Troubleshooting “the remote ssh server rejected x11 forwarding request” Error
X11 forwarding is a useful feature that allows you to access graphical applications running on a remote server from your local machine. However, sometimes you may encounter the error “the remote ssh server rejected x11 forwarding request”. This can be a frustrating issue, but it is usually easy to resolve. …
Read More »